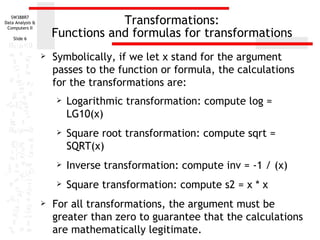
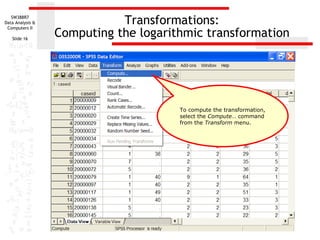
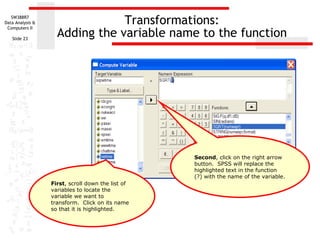
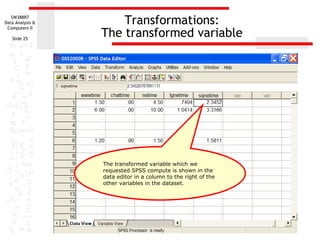
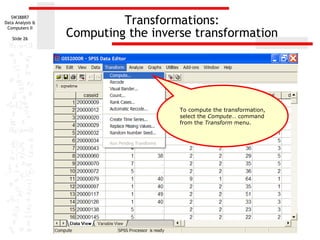
This document discusses various data transformations that can be used to satisfy assumptions of normality, homogeneity of variance, and linearity. It describes how to compute logarithmic, square root, inverse, and square transformations in SPSS. For each transformation, it provides details on specifying the target variable name, selecting the appropriate function or formula, and adding any necessary constants to the values. The purpose of these transformations is to modify non-normal, non-linear, or heteroscedastic data to better meet the assumptions of parametric statistical tests.