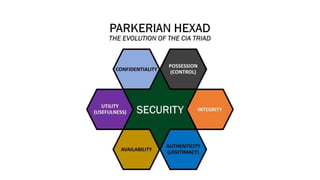
The document provides an overview of information security, emphasizing its importance in protecting sensitive data from unauthorized access and alteration. It discusses various services such as message confidentiality, integrity, authentication, and nonrepudiation, along with key concepts like the CIA triad and Parkerian hexad. Additionally, it addresses security threats, vulnerabilities, and risk management, while outlining different types of security controls necessary for a robust security strategy.