This document provides information about different types of computers and their components. It begins by defining a computer and its basic functions of input, processing, output, storage, and communication. It then describes the major components of a computer system including the input and output units, storage unit, central processing unit (CPU), arithmetic logic unit (ALU), and control unit. It further explains the differences between main memory and secondary storage. The document also classifies computers based on purpose, data handling, and functionality. It concludes by describing different types of computers based on size, including supercomputers, mainframe computers, minicomputers, and microcomputers.






















![COMPUTER &COMMUNICATION SKILLS
23rmmakaha@gmail.com
Have high print quality
They are fast and do not make noise
They are reliable because they have less moving parts
See above [non impact section]
Give three examples of impact printers &three examples of non-impact printers.
Impact printers Non impact printers
Dot matrix Laser
Daisy wheel printers Inkjet
Line printers LED
Chain printers Thermal
Magnetic
Electrostatic
Xerographic
NON-IMPACT PRINTERS
1 - LASER PRINTERS:
How it works: • These print individual pages and work in a
similar way to photocopiers.
• A drum is charged to match the image and
powdered ink (toner) sticks to the surface. The
toner is then transferred to the paper and fixed
by heat and pressure.
• A school or business printer would have a
typical speed of 10 to 20 pages per minute
(ppm).
Suitable uses: • Common wherever fast, high quality printing is required.
Disadvantages: • Non-colour laser printers are more expensive than ink-jet printers (but
the difference is narrowing).
• Colour laser printers are considerably more expensive. (but their speed
and high quality output means they are becoming more popular).
Advantages: • They are quiet and fast and produce high quality printouts.
• Running cost are low because although toner cartridges are expensive
to replace, they last a long time.
Laser printer - A type of printer that utilizes a laser beam to produce an image on a drum. The
light of the laser alters the electrical charge on the drum wherever it hits. The drum is then rolled
through a reservoir of toner, which is picked up by the charged portions of the drum. Finally, the
toner is transferred to the paper through a combination of heat and pressure.
Advantages
-Monochrome or four color
-High-quality print
-Capable of printing an almost unlimited variety of fonts
-Quiet operation
Disadvantages
-Color laser printerstend to be about five to ten times as expensive as](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-23-320.jpg)







![COMPUTER &COMMUNICATION SKILLS
31rmmakaha@gmail.com
DISK CARE
1) Do not expose them to sun or a hot environment.
2) Keep them away from moisture or water.
3) Keep them away from magnetic fields i.e. Phones, tops of some monitors, magnetized
items etc..
4) Do not touch the actual tape.
5) Keep them away from dust.
6) Do not place heavy objects on them.
7) Write on a floppy disk label only with a felt-tip pen, or write before sticking the label
8) Avoid using rubber bands, paper clips and erasers on floppy disks
HARDWARE CARE
1) Make sure there is enough space for the machines to breathe. (Fresh air is necessary
to make the fan keep the electronics cool).
2) Do not block air vents with books.
3) Keep the computer dry.
4) House the machine in a dust free environment e.g. 1ST
floor carpeted-room (Carpets
suck dust) and, use a vacuum cleaner to clean the carpet. (Dust is the biggest killer of
hard drives).
5) Do not expose the machine to extreme temperatures.
6) Properly shut down the machine before turn-off.
7) Pull the plug out of socket when there is thunder and lightning.
8) Do not move the system when the computer is on. The hard drive can be damaged.
9) Use of UPS- Uninterruptible Power Supply in case of power failures,
10) Use of Surge Protectors against too high voltages.
NECESSARY CONDITIONS FOR AN IDEAL COMPUTER ROOM ENVIRONMENT.
1. Cleanliness [books, manuals not encouraged] because they bring dust & caught fire
easily.
2. Air conditioners, which control the room and dehumidates it.
3. It should be dust free; dust is the biggest “killer” of hard drives.
4. No carpets, they caught fire more easily.
5. You are not allowed to eat, smoke or drink in the computer room.
6. No magnetic material should be in the computer room.
7. The computer room should be located in such a way that computers are not exposed
to direct sunlight or hot environments, use curtains if otherwise.
8. The computer room should be fitted with burglar bars, alarm systems, or guarded
24hours to ensure security.
9. The computer room should have surge protectors or suppressors to guard against
electrical faults and high voltages.
10. The computer room should have UPS [uninterrupted power supply] in case of power
failures, which may be fatal.
11. Computer room should be well ventilated, to allow for air circulation,
12. Foreign media, such as floppy diskettes, flash disks should not be allowed in order
to minimize virus spread.
13. Always switch off machines if not in use.
14. Avoid overloading circuits.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-31-320.jpg)














![COMPUTER &COMMUNICATION SKILLS
46rmmakaha@gmail.com
NECESSARY CONDITIONS FOR AN IDEAL COMPUTER ROOM ENVIRONMENT.
1. Cleanliness [books, manuals not encouraged] because they bring dust & caught fire easily.
2. Air conditioners, which control the room and dehumidates it.
3. It should be dust free; dust is the biggest “killer” of hard drives.
4. No carpets, they caught fire more easily.
5. You are not allowed to eat, smoke or drink in the computer room.
6. No magnetic material should be in the computer room.
7. The computer room should be located in such a way that computers are not exposed to direct
sunlight or hot environments, use curtains if otherwise.
8. The computer room should be fitted with burglar bars, alarm systems, or guarded 24hours to
ensure security.
9. The computer room should have surge protectors or suppressors to guard against electrical faults
and high voltages.
10. The computer room should have UPS [uninterrupted power supply] in case of power failures,
which may be fatal.
11. Computer room should be well ventilated, to allow for air circulation,
12. Foreign media, such as floppy diskettes, flash disks should not be allowed in order to minimize
virus spread.
13. Always switch off machines if not in use.
14. Avoid overloading circuits.
15. All cabling and wiring should not be exposed; it should be covered and should not criss cross the
room.
16. Leave enough space between computers and the walls.
17. Do not use chalk the computer room , dry wipe markers are encouraged.
DATA SECURITY /PROTECTION
Data Security/Protection
Refers to keeping data safe from various hazards or dangers like natural hazards,
deliberate corruption or destruction of software & hardware by malicious or terrorist acts,
illegal access to data by hackers [people who break into the system] & accidental
destruction of data by hardware or software failure [operator error].
MEASURES TO ENSURE DATA SECURITY
1. DATA ENCRYPTION/DECRYPTION
Data is coded before transmission over a WAN & decrypted only if you have the key & code to
decrypt the data on the receiving end. The process of transforming a message in ordinary language i.e.
plain text to produce what is called cipher text which is then send along a communication line/link.
The receiving computer uses another transformation to decode the message.
Decryption
• The process of converting encrypted content back into its original form, often the process of
converting cipher text to plaintext. Decryption is the opposite of encryption.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-46-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
47rmmakaha@gmail.com
Encryption
• Any procedure used in cryptography to convert plaintext into cipher text in order to prevent
anyone except the intended recipient from reading that data. There are many types of data
encryption, and they are the basis of network security. Common types include Data Encryption
Standard and public-key encryption.
Cipher text
• Data that has been transformed by encryption so that its semantic information content (ie, its
meaning) is no longer intelligible or directly available.
2. FIREWALL-
a firewall is a software program designed to prevent unauthorized access to a PC or network
through a connection to the Internet. It works by monitoring all data sent to and from the PC
and comparing the data with a set of user-defined security criteria. Any data that does not
meet that criteria is blocked. Firewalls also process encrypted data. They verify the validity of
the user. User would require access to the firewall before they can transmit data. Latest
firewalls also have the ability to detect virus software in packets of data that is sent through
the network. Firewalls disallow data transmission if it detects strains of virus on the data
being transmitted.
3. USERNAMES & PASSWORDS-
Passwords restrict only authorized personnel/users to have access to the data or computer
rooms [cards]. Passwords bring in an aspect of accountability, if a file is deleted, the person
with the password will be reported as the culprit through logging. Passwords can be
forgotten. Widely used by companies to protect their equipment & data
4. AUTHORIZED ENTRY TO COMPUTER INSTALLATIONS-
Most installations have card readers, voice recognition systems or keypads on the doors that
prohibit entry to unauthorized personnel.
5. Backing-up files on external disks periodically.
6. Keeping backup copies of files in a different location and making about 3 generations of
backup.
7. Saving work frequently
8. Avoiding viruses.
9. Restricting access to the computer room. Access could be only through codes, voice
recognition etc.
10. Installing fire alarms.
11. Lining computer rooms with fire resistant material.
12. Placing the computer room in upper floors of a building to avoid burglaries.
13. Having a security guard 24 hours a day.
Summary - Keeping data secure
Measures that can be taken to keep data safe include:
• Making regular back-ups of files. (Back up copies should be stored safely in fireproof
safes or in another building.)
• Protecting yourself against viruses by running anti-virus software.
• Using a system of passwords so that access to data is restricted.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-47-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
48rmmakaha@gmail.com
• Safe storage of important files stored on removable disks - eg locked away in a fireproof
and waterproof safe.
• Allowing only authorized staff into certain computer areas, eg by controlling entry to
these areas by means of ID cards or magnetic swipe cards.
• Always logging off or turning terminals off and if possible locking them.
• Avoiding accidentally deletion of files by write-protecting disks.
• Using data encryption techniques to code data so that it makes no apparent sense
MAJOR THREATS TO INFORMATION SYSTEMS/COMPUTERS
Key threats to data security
• Data can be lost or damaged during a system crash - especially one affecting the hard
disk.
• Data can become corrupt as a result of faulty disks or disk drives, or power failures.
• Data can be lost by accidentally deleting or overwriting files.
• Data can be lost or become corrupted by computer viruses.
• Data can be hacked into by unauthorized users and deleted or altered.
• Data can be destroyed by terrorist activities, war, bombs and fire.
• Data can be deleted or altered by unpleasant employees wishing to make money or seek
revenge on their employers.
Explain 5 major threats to information systems; for each threat describe its impact and
preventative measure you would adopt to prevent it..
THREAT IMPACT CONTROL
Hardware failure • You are grounded
• You cannot access the system
• Data is incorrectly/
incompletely processed
• Have spares in the warehouse.
• Do regular servicing
• Have a disaster plan
• Run hardware diagnostics frequently
Electrical faults • Loss of data
• Disk crushes
• Damage to hardware
• Have standby generators
• Install UPS [uninterrupted power
supply]
• Install Surge suppressors/ protectors
Software failures • Operations are grounded • Buy software from reputable vendors.
• Do regular back ups
• Software diagnostics
Natural disasters/ physical threats • Absolute destruction • Relocate backups to other areas free
from disasters
Viruses • Deletion & corruption of files
• Reformatting of documents
• System may fail to work
• Install a reliable anti-virus software
• Never download unknown e-mail
attachments
• Scan unknown diskettes
Hackers, Computer crime • Security is breached
• Security is bypassed
• Destruction of files
• Data is stolen
• Change passwords regularly
• Employ a security guard
• Install a firewall
• Prevent unauthorized access to
computer facilities.
War and Terrorist activity
Human error](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-48-320.jpg)

![COMPUTER &COMMUNICATION SKILLS
50rmmakaha@gmail.com
malicious codes written with an aim to harm a computer system and destroy information. Writing
computer viruses is a criminal activity as virus infections can crash computer systems, thereby
destroying great amounts of critical data.
Cyberstalking: The use of communication technology, mainly the Internet, to torture other
individuals is known as cyberstalking. False accusations, transmission of threats and damage to
data and equipment fall under the class of cyberstalking activities. Cyberstalkers often target the
users by means of chat rooms, online forums and social networking websites to gather user
information and harass the users on the basis of the information gathered. Obscene emails,
abusive phone calls and other such serious effects of cyberstalking have made it a type of
computer crime.
Identity Theft: This is one of the most serious frauds as it involves stealing money and obtaining
other benefits through the use of a false identity. It is the act of pretending to be someone else by
using someone else's identity as one's own. Financial identity theft involves the use of a false
identity to obtain goods and services and a commercial identity theft is the using of someone
else’s business name or credit card details for commercial purposes. Identity cloning is the use of
another user's information to pose as a false user. Illegal migration, terrorism and blackmail are
often made possible by means of identity theft.
The different types of computer crimes involve an illegal exploitation of the computer and
communication technology for criminal activities. While the advancing technology has served as
a boon to mankind, the destructively directed human intellects are all set to turn technology into a
curse. However, crimes are sure to end, as it is truth that always triumphs!
1. Intellectual crime – cracking into a computer system with the sole aim of transferring or
stealing funds, e.g. Salami slicing which is the activity of obtaining or stealing money
repeatedly in extremely small quantities over a period of time
2. Destruction of property
3. Software piracy
4. Deliberate circumvention of computer security systems or unauthorized access to or
modification of computer programs and data; i.e. hacking which attempts to bypass the
security mechanism of a computer system or network
5. Theft of computer hardware and software or taking away software without the owner’s
consent
6. Making and distributing pornography
MEASURES TO COUNTER OR COMBAT COMPUTER CRIME [COMPUTER
SECURITY]
Careful vetting of employees
Separation of duties
Use of passwords
Security manager software-to monitor attempts to access the system whether
successful or not.
Educating staff
Prevention of unauthorized access to the computer operations room
Data Encryption/Decryption](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-50-320.jpg)




![COMPUTER &COMMUNICATION SKILLS
55rmmakaha@gmail.com
Use of network files/direct connection/through networks.
Software piracy [buying software from unauthorized agents]. Pirated software.
Booting a PC from an infected medium.
Executing an infected program.
Opening an infected file.
Shareware.
Viruses may be sent by opening email attachments,
clicking on spam,
visiting corrupt websites and links online,
• Opening spreadsheets or even the original method—infected disks.
• But the Internet is now the superhighway for virus transmission.
Sharing of storage media
• Through e-mail attachments
• Networks – if your computer is connected to a home network or if your work computer is
part of network, you may find yourself with an infection through no fault of your own.
There isn’t much you can do to stop these kinds of infections, short of having your
network administrator ensure that everyone’s antivirus software is up to date so that the
invading bug can be removed as quickly as possible.
• Internet downloads including software piracy
• Rogue Websites. It is depressing to know that you may become infected with spyware or
a virus by doing nothing more than simply visiting a website, but it is true. Many adult
websites, gambling websites and other less than trustworthy websites will attempt to
automatically access your computer when you visit them. They often install adware bugs
that will cause a flurry of pop ups to appear on your screen. This adware will often allow
for other programs with even more nefarious purposes to be installed and before you
know it, your computer will be swamped. To stop these rogue websites, adjust the
settings on your antivirus software and firewall so that no outside connections can be
made and no programs can be installed without your express permission.
CHARACTERISTICS and ATTRIBUTES OF COMPUTER VIRUSES
The demonstrated characteristics of computer viruses include several remarkable items, including
size, versatility, propagation, effectiveness, functionality, and persistence.
1) Size.The sizes of the program code required for computer viruses has been demonstrated to
be surprisingly small. This has facilitated the ability of these programs to attach themselves to
other applications and escape notice for long periods of time.
2) Versatility.computer viruses have appeared with the ability to generically attack a wide
variety of applications. Many do not even require information about the program they are
infecting.
3) Propagation. Once a computer virus has infected a program, while this program is running,
the virus is able to spread to other programs and files accessible to the computer system. The
ability to propagate is essential to a virus program.
4) Effectiveness. Many of thecomputer viruses that have received widespread publicity have
had far-reaching and catastrophic effects on their victims. These have included total loss of
data, programs, and even the operating systems.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-55-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
56rmmakaha@gmail.com
5) Functionality. A wide variety of functions has been demonstrated in virus programs. Some
virus programs merely spread themselves to applications without otherwise attacking data
files, program functions, or operating systems activities. Other virus programs are
programmed to damage or delete files and systems. The effectiveness of these programs is
enhanced through the use of several phases of operation, in which the virus propagates
through a system or lies dormant until triggered by a specified event. This allows the virus
program increased time to spread before the victim system's user becomes aware of its
presence.
6) Persistence. Even after the virus program has been detected, recovery of data, programs, and
even system operation has been difficult and time consuming. In many cases, especially in
networked operations, eradication of viruses has been complicated by the ability of the virus
program to repeatedly spread and reoccur through the networked system from a single
infected copy.
Attributes of computer viruses
o Auto replicating [self replicating].
o Attaches itself to a program or file
o It infects as it travels
o Reproduces itself
o Distribute itself
o Copies itself
o Duplicate copies of itself
o It spreads
o It is software
o It can destroy
o It hides
DESTRUCTIVE EFFECTS OF COMPUTER VIRUSES
o Cause damage to data
o Extract data from machines for spying or theft
o Slow machine performance
o Corrupt data
o Damage software, hardware and files
o Damage the computer by damaging programs
o Reformatting of the hard disk
o Deletion of files
Top 15 ANTIVIRUS TOOLS/PACKAGES/SOFTWARE
15. ESET NOD32 Antivirus 8
14. Webroot Internet Security Plus 2015
13. Panda Global Protection 2015
12. G-Data Internet Security 2015
11. McAfee LiveSafe 2015
10. AVG Free Antivirus 2016
9. Avast Free Antivirus 2015
8. Panda Free Antivirus 2016](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-56-320.jpg)





![COMPUTER &COMMUNICATION SKILLS
63rmmakaha@gmail.com
Single user
Modes of operation/ Operating system techniques
Computers can operate in many different ways requiring different and complex operating
systems.
Real time processing
When the computer has to react within a guaranteed time to an input, a real time
operating system is used. For example, the engine management system within a car
uses a real time operating system in order to react to all the things going on within the
engine. A real time operating system does not necessarily have to be fast. It simply
has to be quick enough to respond to inputs in a predictable way. Embedded
computers often contain an RTOS as many are used to control something.
Computers operating in real time are often dedicated to the control of systems such
as industrial processes, planes and space flights. Another example of real time
processing is computer games. For example, when an action is selected in a game, the
data is fed back to the computer and the systems updated.
Multi-programming
Multi-programming is a method of operating such that several programs appear to be
running at once.
The jobs are usually given priorities. The operating system switches jobs in and out
of processor time according to priority. For example, while one job is being allocated
printer time, another will be being processed in memory. The processor is so fast
that it seems that many jobs are being processed at the same time.
Multi-tasking
This isn't just about running more than one application at the same time. Multi-
tasking allows multiple tasks to run concurrently, taking turns using the resources of
the computer.
This can mean running a couple of applications, sending a document to the printer
and downloading a web page.
However, operating systems are not truly multi-tasking - in order to do this, you
would need parallel processors, which are now appearing on personal computers.
Multiprocessing
An operating system technique which can manage multiple instruction processors,
assigning each to operate upon a different instruction stream (program or job)
concurrently.
Multiprocessing is the use of two or more central processing units (CPUs) within a
single computer system. The term also refers to the ability of a system to support more
than one processor and/or the ability to allocate tasks between them.[1]
There are many
variations on this basic theme, and the definition of multiprocessing can vary with
context, mostly as a function of how CPUs are defined (multiple cores on one die,
multiple chips in one package, multiple packages in one system unit, etc.).
Multiprocessing sometimes refers to the execution of multiple concurrent software
processes in a system as opposed to a single process at any one instant. However, the
terms multitasking or multiprogramming are more appropriate to describe this concept,
which is implemented mostly in software, whereas multiprocessing is more appropriate to
describe the use of multiple hardware CPUs. A system can be both multiprocessing and
multiprogramming, only one of the two, or neither of the two.
Multi-access or multi-user
A multi-access (or multi-user) system is one where a number of users are able to use the
same system together.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-63-320.jpg)






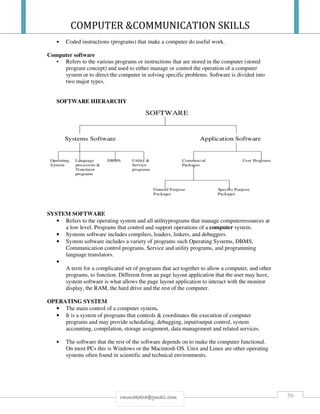
![COMPUTER &COMMUNICATION SKILLS
70rmmakaha@gmail.com
Programs that help users develop information system programs
and procedures and prepare user programs for computer
processing.
Major development programs are language translators,
programming tools and CASE [computer-aided software
engineering] packages.
APPLICATION PACKAGES/SOFTWARE
Are programs that are or were developed to solve specific user problems?
Word processors and spreadsheets fall into this category.
Software application packages can be custom built or they can be bought off the shelf.
# APPLICATION
SOFTWARE
DESCRIPTION EXAMPLES
1 Word processing
software
• A word processor is used to produce documents such as letters, memos and reports.
The latest versions of word processing software contain many features and can also
be used for "desktop publishing" to create newsletters, brochures, business cards,
signs and more. The latest word processing software will allow you to easily type
into columns, add pictures and charts to your page, create custom borders, and
experiment with a variety of type faces (fonts) in a wide range of sizes. You can even
combine different fonts on the same page.
• Word processing software offers many exciting formatting and editing features to
make your work easier. You can easily check the spelling of a word or the entire
document. The built in thesaurus will help you find an alternate word to use. Blocks
of text can be easily moved, copied or erased.
• Use this kind of tool to create worksheets, type letters, type papers, etc, e.g. MS
Word, WordPerfect,....
• Ms word,
Word
perfect,
Word star,
• Ms works
word
processor
,WordPro
2 Spreadsheet
software
• A spreadsheet is used to manage, analyze and present numeric information. Some
common uses of spreadsheet software are financial reports, personal finances and
business finances. Spreadsheet programs can also create a chart from the numeric
data.
• The working screen is laid out in rows and columns, much like a ledger. The
information is typed into a "cell." A cell is the intersection of a row and a column.
The cell can contain a number, a word or phrase (generally used to identify what the
number represents, such as a column or row heading), or a math function or formula.
• Spreadsheets allow you to use simple math expressions such as add, subtract,
multiply or divide, or advanced math such as the type of calculations performed by
architects, engineers, economists and scientists. Spreadsheets also have a special
group of built-in formulas, called functions, that let you perform calculations without
having to type long, complex formulas. Functions are grouped into categories, such
as financial, statistical, engineering, logical, math and trigonometry, database and list
management, date and time, and information.
• One of the reasons many people use a computer for their spreadsheet projects is
because it is easy to change your information once it has been entered. If you change
a number, the spreadsheet will automatically recalculate the results. You can also
take advantage of this feature to perform a "what-if" analysis. For example, you input
the data for a small business venture you are considering and the spreadsheet
calculates your net profit for the first year of business. If you are not pleased with the
result, you can change a few numbers to see how the change would affect the
outcome.
• Use this kind of tool to compute number-intensive problems such as budgeting,
forecasting, etc. A spreadsheet will plot nice graphs very easily, e.g. MS Excel,
Quattro Pro, Lotus 1-2-3,
• Ms Excel,
Lotus 1-2-3
3 Database
management
software
• Allows user to prepare reports based on data found in different records. DBMS is an
important managerial decision support tool for managers at all levels of the
organization. A database is an organised store of information, for example an address
book, list of employees, list of students, customers or items of assets. Database
• Ms Access,
DbaseIV,
Oracle](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-70-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
71rmmakaha@gmail.com
package is used to store records. Data can be sorted or filtered for separate viewing.
Also Calculations and comparisons between data items can be done. Popular
database packages are: Microsoft Excel, lotus Approach, Paradox, dBase IV, Data
Ease.
• Use this software to store data such as address, membership and other text
information. A database can be used to easily sort and organize records
4 Payroll • Pay plus ,
Pay well
5 Accounting e.g. Pastel, TurboCash, QuickBooks • Pastel, Tetra
2000
6 Presentation
graphics software
• Lets users or managers prepare slides containing charts, text and images. Presentation
graphics software usually provides libraries of clip art images that can be cut and
pasted into a slide to make the slide more attractive and informative. These are
applications designed solely for designing graphs and text charts/posters and often
used to produce slides for use on overhead projectors, or presentations on computer-
projectors. They can also produce various types of charts. Examples of graphics
packages are: Microsoft PowerPoint, Lotus Freelance, Harvard Graphics and Corel
Draw, HyperStudio, Flash, Director.
• Use this software to create multimedia stacks of cards/screens that can effectively
present a lesson or a sales pitch. The user often clicks on buttons to advance to the
next screen in a sequence
• Ms
PowerPoint,
Lotus
freelance
graphs
7 Desktop Publishing • Use this software to make signs, banners, greeting cards, illustrative worksheets,
newsletters, etc
• Desktop Publishing (DTP) applications give users powerful and versatile page design
capabilities. The user can incorporate text and graphics on very exact page layouts.
These applications produce magazines, catalogues, invitation cards, business cards
and other sophisticated documents. It links up well with other applications as the user
can import text and graphics from the other applications. Examples of DTP packages
are: Microsoft Publisher, PageMaker, Ventura and Frame maker.
• Ms
publisher,
Aldus
8 Multimedia i) Internet Browsers
This software allows one to surf the Web. Often they can read email and create Web pages
too, e.g. Netscape Navigator (or Netscape Communicator), MS Internet Explorer, AOL
Browser....
ii) Email programs
These programs send and receive email, e.g. Netscape Messenger (part of Netscape
Communicator), MS Outlook Express, MS Outlook, Eudora, AOL browser (has email
built in)....
iii) Graphics Programs (pixel-based)
This software allows one to touch up photographs and create graphics from scratch, e.g
Adobe Photoshop, Paint Shop Pro, MS Paint (comes free on Windows PC's), Painter, ....
• Internet
explorer
Netscape
9 Communication • This software allows two computers with modems to communicate through audio,
video, and/or chat-based means, e.g. MS NetMeeting, AOL Instant Messenger, IRC,
ICQ, CU-SeeMe, ...
• Ms Outlook,
Ms
Exchange
10 Design e.g. AutoCad, Corel Draw • AutoCAD,
CAM
State five advantages of using a word processor (e.g. MS Word) rather than a manual
typewriter in an office [10].
Ability to correct mistakes
Ability to view documents on screen before printing
Ability to incorporate diagrams](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-71-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
72rmmakaha@gmail.com
Ability to move parts of text to other sections of the document.
Ability to save or store documents for future reference or use.
Ability to alter or change document layout.
Ability to print a lot of copies [ no retyping]
Ability to insert tables
Ability to format document [font, paragraphs, bullets etc] Spelling and grammar checker
Import files
Mail merge
WYSIWYG capability
Creation of templates
Automatic creation of index and table of contents
o ther - Good reasoning [ 2 marks each for 5 & 1 mark each for more than 5]
a) Explain what is meant by the term ‘word processing package’. [3 marks]
Is a program or set of programs used to enter, edit, format, store and print
documents. A document may be anything from a single memo to a complete
book.
An application package that involves the use of computers to manipulate text
data in order to produce office communications in the form of documents.
Any of many popular application programs designed for composing,
revising, printing, and filing written documents.
Word Processing is the efficient and effective production of written
communications at the lowest possible cost through the combined use of
systems management procedures, automated technology, and accomplished
personnel. The equipment used in word processing applications includes but
is not limited to the following: dictation and transcription equipment,
automatic repetitive typewriters, visual display text editing typewriters,
keyboard terminals, etc.
b) Give any 2 examples of a word processing package’. [2marks]
MS WORD
WORD STAR
WORD Perfect
MS WORKS WORD
c) Briefly describe any 5 important features of a word processor. [5 marks]
1) Spelling and grammar checker
2) Import files
3) Mail merge
4) WYSIWYG capability
5) Creation of templates
6) Automatic creation of index and table of contents
d) List any 10 facilities that spreadsheets offer. [10 marks]
1. Format cells, rows and columns, specifying for example, the alignment of text,
number of decimal points, height and width of a cell.
2. Copy cell contents to other locations
3. Determine the effect of several different hypothetical changes of data
4. Insert, move or delete rows and columns](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-72-320.jpg)


![COMPUTER &COMMUNICATION SKILLS
75rmmakaha@gmail.com
• DDR SDRAM (double data rate synchronous dynamic RAM) takes all the features of
ordinary SDRAM and increases the frequency bandwidth to improve system performance
and speed.
• RDRAM (Rambus dynamic RAM) is able to load a new stream of data before the
previous stream has completed, resulting in faster access speeds. The RDRAM memory
features dual-channel processing which doubles data throughput to further enhance
performance. This type of memory is optimized for high-end multimedia tasks involving
video and audio. Dual Channel RDRAM is shipped on our performance desktop systems
powered by Pentium 4 processors
• VRAM: Memory designed for storing the image to be displayed.
• CACHE RAM is a small block of high-speed memory located between the Processor
and main memory and is used to store frequently requested data and instructions. When
the processor requests data, it will check in the cache first
The computer has two types of memory chips within the system unit, known as RAM
and ROM.
ROM (Read Only Memory)
This memory chip has essential programs that start up the computer hardwired on the
microchip during the manufacture of the computer. It forms what is known as
FIRMWARE, being a halfway between hardware and software. The characteristics of
this memory are that:-
1) can be read from,
2) cannot be changed
3) is permanent
4) non-volatile (data not lost when power is turned off).
ROM
Stores instructions & data which do not change
It is written once during manufacture
It is for holding software such as MS-DOS.Windows 95, 98.XP.
It is programmed by the manufacturer and cannot be altered by the user
It is static & non volatile
It stores control routines for personal computers
VARIATIONS OF ROM
Allow users to store and in some cases to change data stored in ROM
PROM [Programmable ROM] is not programmed during manufacture but can
be programmed by the user. It is programmed according to the needs of the user
organization. If you make a mistake the ROM once programmed will became
permanent to the effect that any errors will never be corrected thus the user will
throw away any chip if errors are made.
EPROM [Erasable Programmable ROM] can be programmed and erased as
many times. This time you don’t have to worry about errors too much because
there is room for correction. The programming is done electronically. Stored data
can be lost by exposing it to Ultra Violet light over a period of minutes.
1) EEPROM [Electrically Erasable Programmable ROM] can be read, erased,
rewritten, without removing from the computer. The erasing & rewriting process
is very slow compared with reading, which limits their use. These can be erased
& programmed with electrical pulses. Can be erased in a few Milliseconds](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-75-320.jpg)


![COMPUTER &COMMUNICATION SKILLS
78rmmakaha@gmail.com
STAR TOPOLOGY
Is a network in which nodes are connected to a central component as its hub?
The central component can be a switching device like a switch or PABX [private
automatic branch exchange], a computer [minicomputer to which workstations
or PCs are connected] or just a wiring center that is a common termination point
for the nodes, called a hub.
A HUB is a component that serves as a common termination point for multiple
nodes and that can relay [store & forward] signals along the appropriate paths.
Definitions of star network on the Web:
• A network in which all terminals are connected through a single point, such as a star
coupler.
• A network topology in the form of a star. At the center of the star is a wiring hub or
concentrator, and the nodes or workstations are arranged around the central point
representing the points of the star.
Advantages of star topology
It is easy to add or remove nodes
Because each node has its own link to the central node, the star is more reliable than other
topologies.
Full utilization of resources i.e. printer, sharing of processor
Direct connection of terminals to the main processor, means that if one terminal breaks
down it won’t affect other terminals.
Disadvantages of star topology
All traffic between two nodes passes through the central node. If the central component
breaks down, the whole network is down.
The number of ports of the central component limits the number of connected nodes.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-78-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
79rmmakaha@gmail.com
A star topology requires a lot of cabling since all data path connections must be to the
central node.
There is no direct communication between or among workstations
Sharing of processor delays in the processing of jobs.
BUS/LINEAR TOPOLOGY
Describes a network in which each node is connected to a common line.
This is also sometimes called a horizontal, multidrop or multi point network.
Though it is preferable to use the last terms for connections with a
mainframe/mini computer as in the following diagram.
In a bus messages travel in both directions and do not go through the individual
nodes but every node can hear each message as it goes past.
When the signal/message reaches an end of the bus, a terminator absorbs it, to
keep it from traveling back again along the bus line, to avoid interference with
other messages already in the line.
The data/signals/messages are transmitted in packets along the bus.
Each packet is send with a receiver identification code that is an address of
destination and all computers on the network are permanently on the alert for any
messages coming to them.
Definitions of bus network on the Web:
• A single-cable LAN, in which all computers on the network are connected in series to a
single cable. On a bus network, each computer hears all of the transmissions going down
the line, and selects only those that are addressed to its location. This is the simplest and
most common LAN technology.
Advantages of Bus Network/topology
When a node breaks down, the network does not break down.
A bus uses relatively less cables compared to other topologies
Direct communication due to direct connection.
Fast processing since there is no Host computer
Once a cable has been laid down any new equipment can easily be
connected to the network by a simple tapping into the cable.
Disadvantages of Bus Network/topology
In a bus topology it is not always easy to add a node. [E.g. installation of extra tap in
thick Ethernet].](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-79-320.jpg)
![COMPUTER &COMMUNICATION SKILLS
80rmmakaha@gmail.com
Diagnosis/trouble shooting can be difficult.
Expensive to run [several processors] – Detectors.
Communication between components of the network traveling in opposite direction along
the bus can collide causing loss of transmitted information.
Because of this collision a detection system has to be present to control the re-
transmission of lost information thereby making it a more expensive option
RING NETWORK
A ring network has nodes connected in a circular way.
Each node has two neighboring nodes
Data flow is unidirectional.
A message is forwarded in one direction until it reaches the destination with
intermediate nodes acting as relay [store & forward] units.
The destination node copies the message and passes the message again to the
ring.
This message then continues to circulate around the ring back to the source.
Definitions of ring network on the Web:
• A network topology in the form of a closed loop or circle. Each node in the network is
connected to the next, and messages move in one direction around the system. When a
message arrives at a node, the node examines the address information in the message. If
the address matches the node's address, the message is accepted; otherwise the node
regenerates the signal and places the message back on the network for the next node in
the system. ...
Advantages of ring network
The message return provides the source with a form of
acknowledgement. The node removes its own message from the ring.
Little cabling needed compared to Star.
Each node acts as relay unit.
Packet collisions do not occur because information is traveling in one
direction.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-80-320.jpg)



















![COMMUNICATION
100rmmakaha@gmail.com
QUESTION
Define Communication. [2]
6. The process by which information, ideas, attitudes and emotions are exchanged between one
person and another by the use of a common system of symbols, signs and behaviour.
(Hammond S 1998:19)
7. The giving, receiving or exchange of information, opinions or ideas by writing, speech or
visual means or a combination of these three- so that the material communicated is
understood by everyone.
QUESTION
Elements of communication [10]
The elements are discussed in short below:
6. Two or more parties: communication must involve at least two parties. One party acts
as the SENDER of message and another is the RECEIVER of that message.
7. Message: The second important elements of communication are message or information
that the sender wants to communicate. Messages may take the form of feelings, wishes,
attitudes, ideas, facts, information or any other perceivable matter. The messages that a
sender wants to send, should be meaningful to the receiver.
8. Business related information: Information that the sender transmits should be related to
business. Similarly the feedback from the receiver should also be business based.
9. Media or channel: Channel of medium is a pre-requisite of communication. It is the
means of transmitting messages from sender to receiver. Communication media can be
verbal and nonverbal. The verbal media may be of oral and written. Verbal media of
communication include telephonic conversation, fax, newspaper, books, journals etc. On
the other hand, gestures, and body language, facial expression etc. Are the media of non-
verbal communication? The sender must select appropriate media for successful
communication.
10. Feedback: The final element of communication is feedback. It is the response or reaction
of the receiver regarding the sender’s message. Feedback describes how the message is
being interpreted by the receiver. It is regarded as the instrument for evaluating the
success of communication process.
11. Noise: The messages are transferred from encoder to decoder through channel. During
this process the messages may distracted or affected by physical noise like horn sounds,
thunder and crowd noise or encoded signals may distract in the channel during the
transmission process which affect the communication flow or the receiver may not
receive the correct message](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-100-320.jpg)
![COMMUNICATION
101rmmakaha@gmail.com
QUESTION
Functions of communication [10]
Some of its major functions are as follows:
1. Informing: The principal function of communication is informing messages to others. It
really is done verbally or non-verbally. Verbal messages might be either oral or written.
On the other hand, non-verbal messages can be sent via human body language, gestures,
posture etc.
2. Persuading: One more essential functionality of communication is persuading a single
party by another. In business, management persuades the employees to make certain that
employees persuade management so that management accepts their ideas, opinions and
suggestions. The business also communicates with external stakeholders to persuade
them.
3. Integrating various divisions and departments: Attainment of organizational goals
requires integration and coordination of activities performed by various individuals,
groups and departments. Management can put together and coordinate those people
divisions and departments by building a communication network for the whole
organization.
4. Creating relationships through external parties: Communication creates relationships
not just with internal parties but also with the external parties like customers, suppliers,
investors, general community and government. Communication through these external
parties could be the for survival of an organization.
5. Improving labor-management association: There’s no option to excellent labor-
management relationship for achieving organizational goals. Therefore, a significant
purpose of communication is to increase labor management relationship. Communication
helps each party to express themselves and produce an atmosphere of cooperation.
6. Helping in decision making: Management is absolutely nothing but producing decisions
for creating decision, management requirements information. The function of
communication is to supply relevant info on the management in time so that they are able
to make appropriate decisions.
7. Reducing misunderstanding: In the absence of communication, misunderstanding,
distance, conflict, controversies etc. May perhaps a rise inside the organization.
Communication helps to overcome and avoid these misunderstanding, disagreement and
controversies.
8. Solving problems: Difficulties are favorite to every business. A business faces good deal
of difficulties in its day-to-day operations. Achievement of business depends on timely
items of individual problems. Item of these problems is impossible without the need of
appropriate communication with the concerned parties.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-101-320.jpg)
![COMMUNICATION
102rmmakaha@gmail.com
QUESTION
Major forms of communication [10]
• Intrapersonal Communication
• Interpersonal/Dyadic Communication
• Extra personal
• Small Group Communication
• Public Communication
• Mass Communication
INTRAPERSONAL COMMUNICATION
Intrapersonal communication is a communication which happens yourself. Here both
Source (sender) and receiver is only one. so, the feedback works without any interruption.
Example: A person can communicate himself through pain, thinking, feelings and
emotion etc.
INTERPERSONAL COMMUNICATION (Dyadic Communication)
In Interpersonal/Dyadic communication, two persons are involved in this communication
process. Here the Source becomes a receiver and receiver become Source because of
dynamic communication process were the feedback’s are shared between Source and the
receiver.
SMALL GROUP COMMUNICATION
Small group communication takes place in a group, usually comprising five to 10
people. This form of communication serves relationship needs (like companionship,
family bonding and affection or support) as well as task-based needs, for example,
deciding on disciplinary action or resolving conflict in the workplace.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-102-320.jpg)

![COMMUNICATION
104rmmakaha@gmail.com
Communication between human beings and non-human entities is extra personal
communication. For example, when your pet dog comes to you wagging its tail as soon
as you return home from work, it is an example of extra personal communication.
Communication between human beings and non-human entities is called as extra
personal communication. For e.g. your parrot responding your greeting. In this type of
communication understanding is required between sender and receiver. Receiver
responds in sign language
QUESTION
Models of communication [10]
a. Linear model
b. Interactive model
c. Transactional model
LINEAR MODEL
The linear model views communication as a one-way or linear process in which the speaker
speaks and the listener listens.
Shannon and Weaver’s (1949) model includes noise or interference that distorts understanding
between the speaker and the listener. Figure shows a linear model of communication:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-104-320.jpg)

![COMMUNICATION
106rmmakaha@gmail.com
QUESTION
Difference between communication process and communication model [10]
QUESTION
Communication process [10]
Communication process consists of some interrelated steps or parts through which messages are
sent form sender to receiver. The process of communication begins when the sender wants to
transmit a fact, idea, opinion or other information to the receiver and ends with receiver’s
feedback to the sender.
.
The main components of communication process are
• Sender,
• Message,
• Channel,
• Receiver
• Feedback
• Noise](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-106-320.jpg)

![COMMUNICATION
108rmmakaha@gmail.com
QUESTION
The main components of communication process 10]
The main components of communication process are as follows:
1. Context - Communication is affected by the context in which it takes place. This
context may be physical, social, chronological or cultural. Every communication
proceeds with context. The sender chooses the message to communicate within a
context.
2. Sender / Encoder - Sender / Encoder is a person who sends the message. A
sender makes use of symbols (words or graphic or visual aids) to convey the
message and produce the required response. For instance - a training manager
conducting training for new batch of employees. Sender may be an individual or a
group or an organization. The views, background, approach, skills, competencies,
and knowledge of the sender have a great impact on the message. The verbal and
non verbal symbols chosen are essential in ascertaining interpretation of the
message by the recipient in the same terms as intended by the sender.
3. Message - Message is a key idea that the sender wants to communicate. It is a
sign that elicits the response of recipient. Communication process begins with
deciding about the message to be conveyed. It must be ensured that the main
objective of the message is clear.
4. Medium - Medium is a means used to exchange / transmit the message. The
sender must choose an appropriate medium for transmitting the message else the
message might not be conveyed to the desired recipients. The choice of
appropriate medium of communication is essential for making the message
effective and correctly interpreted by the recipient. This choice of communication
medium varies depending upon the features of communication. For instance -
Written medium is chosen when a message has to be conveyed to a small group of
people, while an oral medium is chosen when spontaneous feedback is required
from the recipient as misunderstandings are cleared then and there.
5. Recipient / Decoder - Recipient / Decoder is a person for whom the message is
intended / aimed / targeted. The degree to which the decoder understands the
message is dependent upon various factors such as knowledge of recipient, their
responsiveness to the message, and the reliance of encoder on decoder.
6. Feedback - Feedback is the main component of communication process as it
permits the sender to analyze the efficacy of the message. It helps the sender in
confirming the correct interpretation of message by the decoder. Feedback may be
verbal (through words) or non-verbal (in form of smiles, sighs, etc.). It may take
written form also in form of memos, reports, etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-108-320.jpg)
![COMMUNICATION
109rmmakaha@gmail.com
QUESTION
Different Types Of Noise [10]
Psychological noise
Psychological noise results from preconceived notions we bring to conversations, such as
racial stereotypes, reputations, biases, and assumptions. When we come into a
conversation with ideas about what the other person is going to say and why, we can
easily become blinded to their original message. Most of the time psychological noise is
impossible to free ourselves from, and we must simply strive to recognize that it exists
and take those distractions into account when we converse with others.
Physiological noise
Physiological noise has to do with distractions from the natural effects of the body, such
as being tired or hungry.The pains a person received will also result in physiological
noise. For instance, great anger or sadness may cause someone to lose focus on the
present moment.
Physical noise
Physical noise is any external or environmental stimulus that distracts us from receiving
the intended message sent by a communicator.Examples of physical noise include: others
talking in the background, background music, a startling noise and acknowledging
someone outside of the conversation.
Semantic noise
This is noise caused by the sender. i.e., the encoder. This type of noise occurs when
grammar or technical language is used that the receiver (the decoder) cannot understand,
or cannot understand it clearly. It occurs when the sender of the message uses a word or a
phrase that we don't know the meaning of, or which we use in a different way from the
speakers. This is usually due to the result that the encoder had failed to practice audience
analysis at first. The type of audience is the one that determine the jargon one will use.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-109-320.jpg)
![COMMUNICATION
110rmmakaha@gmail.com
QUESTION
Explain communication breakdown & communication barrier [10]
Communication Breakdown
• A lack of communication; a failure to exchange information
• A communication breakdown occurs when communication is incomprehensible to one
party or entirely absent between two people.
Communication barrier
• “Barriers to communication mean obstacles to the process of communication.
• “Communication barriers are the problems that arise at every stage of the communication
process and have the potential to create misunderstanding and confusion.
• “Communication, when it is impeded and does not reach the receiver is often somewhat
ineffective and the impediments are known as barriers.”
• Factors that inhibit the effective flow of information that communication.
• Communication barriers impede the flow of information or create problems in
understanding and acceptance of information.
QUESTION
Barriers to communication [10]
ORGANIZATIONAL BARRIERS:
The barriers that generate form within the organization are known as organizational barriers may
be of the following types:
1. Negative organizational climate: Negative attitude of top management discourages
communication initiative of the employees.
2. Absence of communication policy: Well-designed communication policy encourages
communication in the organization. In the absence of such policies, employees fail hesitate to
communicate.
3. Excessive authority layers: Excessive authority layers acts as a severe impediment to
successful communication. In the case of excessive authority impediment to successful
communication. In the case of excessive authority layers, information reaches to its final
destination passing through several hierarchical levels. As a result, information may be
distorted or lost. Excessive authority layers also causes delay in communication.
4. Filtering: Filtering implies willful distortion of information. This problem usually arise in
upward communication. In upward communication, employees tend to pass only those
messages that create positive impression about them.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-110-320.jpg)

![COMMUNICATION
112rmmakaha@gmail.com
QUESTION
Overcoming Barriers to communication [10]
• Developing flat organization structure: In modern time, organizations prefer flat
structure to tall one. Flat structure has fewer heretical levels that reduce communication
gap between superiors and subordinates. Therefore, business enterprises in any country
should design flat structure in place of the traditional tall structure.
• Specifying objective of communication: In order to overcome the problem of
ambiguity, communicator should specify the objective of communication. This will help
him to arrange the message concisely and clearly.
• Clear-cut message: Top executives should send clear orders, instructions, policies,
procedures and directions so that misunderstanding and confusion do not arise. This will
enhance the effectiveness of communication.
• Using simple language: Language creates numerous communication problems in
organization. Employees in the organization are neither equally educated nor trained.
Therefore, the communication should use simple and common words. At the same time,
they should avoid technical jargons so that everyone can understand it.
• Selecting proper media: Appropriate media should be used for effective
communication. Management should decide when to use oral medium and when to use
written medium. While selecting media, management must consider the nature of the
message, its importance and complexity.
• Encouraging feedback: Managers should encourage feedback from subordinates to
attain the objective of communication. This will help the manager to know the reaction of
subordinates and to take proper action.
• Providing communication training: Organizations can provide training to enhance
communication skills of their employees. In this regard, organizations can arrange
seminars, symposiums or institutional training programs.
• Creating congenial labor management relationship: Harmonious relationship between
labors and management is essential for successful communication. Relationship between
them affects the level of importance one party gives on the message of other. Therefore,
management and labor should cooperate with each other to create a favorable
communication climate.
• Using modern communication technologies: In order to facilitate speedy and regular
communication, organizations need to use modern communication devices.
• Encouraging informal communication: To make formal communication effective,
organizations can arrange informal channels. This will obviously promote good
relationship among the participants in the organization.
• Unbiased attitude of management: Management should be free from political, regional
and religious biasness. Their neutral attitude will bring a fair environment of
communication in the organization.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-112-320.jpg)
![COMMUNICATION
113rmmakaha@gmail.com
QUESTION
Explain the following types of communication
a) Verbal Communication
b) Nonverbal Communication [10]
VERBAL COMMUNICATION:
Verbal communication is the process of exchanged of information or message between two or
more persons through written or oral words.
Forms of verbal communication are as follows:
1. Oral communication: Oral communication is the process of communication in which
messages or information is exchanged or communicated within sender and receiver
through the word of mouth. It can be divided into two ways: a. Speaking b. Listening.
2. Written communication: Written communication is the process of communication in
which messages or information is exchanged or communicated within sender and
receiver through written form. It can be divided into two ways: a. Writing b. Reading.
NONVERBAL COMMUNICATION:
• Nonverbal communication is the expression or exchange of information or messages
without using any spoken or written word.
• Nonverbal communication is the sending or receiving of wordless messages.
• We can say that communication other than oral and written, such as gesture, body
language, posture, tone of voice or facial expressions, is called nonverbal
communication.
• Nonverbal communication helps receiver in interpreting the message received.
• Often, nonverbal signals reflects the situation more accurately than verbal messages.
Some of the forms of non-verbal communications are as follows:
1. Facial expression
2. Gestures
3. Body language
4. Proximity
5. Touch
6. Appearance
7. Silence
8. Paralinguistic
9. Eye Gaze or eye contact etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-113-320.jpg)
![COMMUNICATION
114rmmakaha@gmail.com
QUESTION
Characteristics of non-verbal communication [10]
Non-verbal communication is any information that is communicated without using words. The
important characteristics of non-verbal communication are as follows:
• No use of words: Non-verbal communication is a communication without words or
language like oral or written communication. It uses gestures, facial expressions, eye
contact, physical proximity, touching etc. for communicating with others.
• Culturally determined: Non-verbal communication is learnt in childhood, passed on to
you by your parents and others with whom you associate. Through this process of
growing up in a particular society, you adopt the taints and mannerisms of your cultural
group.
• Different meaning: Non-verbal symbols can many meanings. Cross-culture aspects give
various meanings to same expression in respect of non-verbal communication.
• Vague and imprecise: Non-verbal communication is quite vague and imprecise. Since in
this communication there is no use of words or language which expresses clear meaning
to the receiver.
• May conflict with verbal message: Non-verbal communication is so deeply rooted, so
unconscious, that you can express a verbal message and then directly contradict it with a
nonverbal message.
• Largely unconscious: Non-verbal communication is unconscious in the sense that it is
usually not planned nor rehearsed. It comes almost instantaneously.
• Shows feelings and attitudes: Facial expressions, gestures, body movements, the way
you use your eyes – all communicate your feelings and emotions to others.
• Informality: Non verbal communication does not follow any rules, formality or structure
like other communication. Most of the cases people unconsciously and habitually
engaged in non-verbal communication by moving the various parts of the body.
QUESTION
Advantages and disadvantages of non-verbal communication [10]
It has multiple advantages or functions:
1. Complementary: Non-verbal cues complement a verbal message by adding to its meaning.
You can pat someone you offended at the back as you say sorry to him or her.
2. Easy presentation: Information can be easily presented in non-verbal communication
through using visual, audio-visual and silent means of non-verbal communication.
3. Substituting: Non-verbal message may substitute for the verbal message especially if it is
blocked by noise, interruption, long distance etc. for example: gestures-finger to lips to
indicate need for quite, facial expressions- a nod instead of a yes.
4. Accenting: Often used to accent a verbal message. Verbal tone indicates the actual meaning
of the specific words.
5. Repeat: Used to repeat the verbal message (e.g. point in a direction while stating directions.)](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-114-320.jpg)

![COMMUNICATION
116rmmakaha@gmail.com
QUESTION
Differences between verbal and non-verbal communication: [10]
• Verbal communication is the expression or exchanged of information or messages
through written or oral words.
• On the other hand, non-verbal communication is the expression or exchanged of
information or messages through without using any spoken or written word. The
important differences between verbal and non-verbal communication are as follows:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-116-320.jpg)
![COMMUNICATION
117rmmakaha@gmail.com
QUESTION
• Different types of Non Verbal Cues
• Medias Or Ways Or Methods Or Kinds Of Non-Verbal Communication [10]
Non-verbal communication is the expression or exchanged of information or messages through
without using any spoken or written word. Several symbols can be used in non-verbal
communication. We will discuss here only the following types of communication that occur
without words.
A. Body language: Some parts of our body can express many indications without any sound.
Message can be transmitted with the help of our body movements which is called body language.
Body language is a form of non-verbal communication, which consists of posture, gestures, facial
expressions, eye movements etc.
1. Facial expression:
2. Gestures:
3. Posture
4. Eye Gaze or Eye contact:
5. Appearance and dress:
6. Touch:
7. Silence:
B. Space or proximity: People often refer to their need for “personal space”, which are also
important types of nonverbal communication. The physical distance between you and others
signals your level of intimacy and comfort. If someone you don’t know stand too close or touches
too often, you will probably begin to feel uncomfortable.
C. Time: Another type of non-verbal communication involves time. Thant is how we give
meaning to time communicates to other. For example, begin late in work everybody a worker can
be considered as a man of carelessness but if a manager does it; we say it is a symbol of power.
We know, time can play a vital role to reduce tension, conflict among groups. It is said that- “Kill
the time to delay the justice”.
D. Paralinguistic (Tone and volume of voice): Paralinguistic refers to vocal communication that
is separate from actual language. Paralanguage also include such vocal characteristics as rate
(speed of speaking), pitch (highness of lowness of tone), inflection, volume (loudness) and
quality (pleasing or unpleasant sound).
• Vocal characterizers (laugh, cry, yell, moan, whine, belch and yawn). These send
different message in different cultures (Japan- giggling indicates embarrassment; India-
belch indicates satisfaction)
• Vocal qualifiers (volume, pitch, rhythm, tempo and tone). Loudness indicates strength in
Arabic cultures and softness indicates weakness; indicates confidence and authority to the
Germans; indicates impoliteness to the Thai; indicates loss of control to the Japanese.
(Generally, one learns not to “shout” in Asia for nearly any reason). Gender based as well
women tend to speak higher and more softly than men.
• Vocal segregates (UN-huh, shh, uh, ooh, mmmh, hummm, eh mah, lah). Segretates
indicate formality, acceptance, assent, uncertainty.
E. Visual communication: When communication takes place by means of any visual aid, it is
known as visual communication. Such as facial expression, gesture, eye contact, signals, map,
chart, poster, slide, sign etc. for example, to indicate ‘danger’, we use red sign, to indicate ‘no
smoking’, we use an image showing a lighted cigarette with across mark on it etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-117-320.jpg)
![COMMUNICATION
118rmmakaha@gmail.com
QUESTION
Advantages and disadvantages of written communication [10]
Advantages of written communication:
• Easy to preserve: .
• Easy presentation of complex matter:
• Permanent record:
• Prevention of wastage of time and money:
• Accurate presentation:
• Use as a reference:
• Delegation of authority
• Longevity:
• Effective communication:
• Maintaining image: .
• Proper information: .
• Less distortion possibility.
• No opportunity to misinterpret:
• Controlling tool:
• Easy to verify:.
• Others: Clear understanding, Legal document, Acceptability, Reduction of risk, Creating
confidence, Easy circulation, Wide access or coverage etc.
Disadvantages of written communication
• Expensive:
• Time consuming: Written communication takes time to communicate with others. It is a time
consuming media. It costs the valuable time of both the writer and the reader.
• Useless for illiterate person: It messages receiver is illiterate, written communication is
quite impossible. This is major disadvantage written communication.
• Difficult to maintain secrecy: It is an unexpected medium to keep business secrecy. Secrecy
is not always possible to maintain through written communication. Because here needs to
discuss everything in black and white.
• Lack of flexibility: Since writing documents cannot be changed easily at any time. Lack of
flexibility is one of the most important limitations of written communication.
• Delay in response: It takes much time to get a response from the message receiver; prompt
response is not possible in case of written communication that is possible in oral
communication.
• Delay in decision making: Written communication takes much time to communicate with all
the parties concerned. So the decision maker cannot take decisions quickly.
• Cost in record keeping: It is very difficult and expensive to keep all the records in written
communication.
• Complex words: Sometimes the writer uses complex words in writing a message. It becomes
difficult to meaning out to the reader. So the objectives of the communication may lose.
• Lack of direct relation: If there is no direct relation between the writer and the reader, writer
communication cannot help to establish a direct relation between them.
• Other: Prompt feedback is impossible, Slowness, Bureaucratic attitude, Understanding
problem between boos and subordinates, lack in quick clarification and correction, formality
problem, lack of personal intimacy, etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-118-320.jpg)
![COMMUNICATION
119rmmakaha@gmail.com
QUESTION
Different types of written communication [10]
A. Media of written communication to management:
1. Special management bulletin: The bulletin which is issued for emergency matters
related to management is called special management bulletin. This kind of bulletin must
be published promptly.
2. Management news copy: The less important management issues are published in this
news copy. Generally this new copy is published weekly.
3. Formal management report: Formal management report is one of the most important
media of written communication to management. It emphasizes the upward
communication.
4. Publications: Some organizations publish special journals or publications for the high
level officer. It provides officers information about lost-reduces, safety system, decreases
of accident, improvement of quality etc.
B. Media of written communication for employees:
1. Bulletin for employees: Bulletin is published to inform the employees of emergency and
important matters within a very short time. Generally it is hanging on a notice board.
2. Newspaper: Newspaper is a wide used medium to communicate with employees.
Company’s planning, policy, procedure objectives, problems is published in it to inform
employees. Generally it is published weekly.
3. Publication of monthly paper: Some large companies publish it to inform everything to
the employees. The company’s role and plan are also stated here.
4. Letters: Letter is one of the most important media of written communication for
employees. Sometimes the higher authority sends letter to the employee without asking
any response.
5. Employee’s notebook: Sometimes the management supplies notebook to the employees
in which speech of executives, history of the organization, planning, policy, order for the
work are stated.
6. Reading rack: Necessary books for the employees can be arranged on the shelf so that
they can read and get knowledge.
7. Notice: Notice is an important medium to communicate with employees. By which the
employees are invited to attend a special meeting.
8. Internal circular: It is one of the most important media of written communication. It is
used for internal communication. When all the employees are informed at a time, internal
circular is used.
9. Complain Book: A complains book can be kept in a definite place so that the employees
can write their complaints with it.
10. Memo: Memo is a popular medium of internal written communication. The memo is a
short form of letter usually used to communicate with the employees of the same
organization.
11. Report: Report is an organized statement of facts and findings that contains information
obtained by proper inquiry and examination and evaluation of any past event relating to a
particular subject or problem that helps to decision making.
12. Other media: Salary envelope, annual financial reports or statements, Note sheets,
Question box, Essay competition etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-119-320.jpg)
![COMMUNICATION
120rmmakaha@gmail.com
QUESTION
Different types of oral communication [10]
Medias or ways or techniques or channels of oral communication
The channels or methods or oral communication may be classified broadly in two categories non
mechanical channels and mechanical channels which are described below:
A. Non mechanical channels
• Conversation: conversation means the informal discussion among the people. When one
person discusses his views, opinion to another person and exchanges their views in the
presence of both then it is called face to face conversation. It also includes the face-to-
face discussion on a particular issue. In this method both the information receiver and
sender can exchange their views freely and fairly.
• Interview: It suggests a meeting between two or more persons for the purpose of getting
a view of each other or for knowing each other. When we normally think of an interview,
we think a situation in which an employer tries to size up an applicant for a job. The
employer’s aim is to know whether the applicant can be fit for service to this organization
and the applicant’s aim is to find whether the job being offered by the organization can be
suitable to him. Its first, the speaker asks questions to the listener and then the listener
answers the question. There are three major techniques of interview. They are as follows:
o Direct questioning
o Non-directive interview and
o Guided interview
• Does speech: Speech means what the speaker says in front of the audience. It is fully
audience-oriented system. Generally the political leaders, the managers, the business man
or the workers’ leaders use this system sometimes. It can build tension or it can relax
tension. This system is practiced in public gathering at company meetings, inauguration
and seminars etc. In needs to considerable skills otherwise it is not effective.
• Group discussion: Group discussion is a popular method of oral communication.
Management arranges group discussion to take a decision on a special matter. Group
discussion is very helpful to human relation, idea getting an idea development and
training.
• Formal training courses: Effective communication can be performed through formal
training courses. It is a wide used technique of oral communication. Both the trainer and
the trainee can exchange their views directly.
• Meeting: Meeting means the formal group discussion about a specific predetermined
topic or subject. Meeting members to get together and discuss about a problem or issue or
a special matter. There are several types of meeting such as –
o Security meeting
o Minutes meeting
o Social meeting
o General meeting itself
• Counseling: Counseling is an effective medium of oral communication. Generally it
held yearly or bi-yearly. It is adopted by the higher authority for their followers.
• Committee: Committee is an organization. The committee meeting is a popular
technique of oral communication. Special decision is taken through face to face
discussion of a committee meeting.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-120-320.jpg)

![COMMUNICATION
122rmmakaha@gmail.com
QUESTION
Advantages and disadvantages of oral communication [10]
1. Time saving:
2. Cost savings:
3. More powerful: .
4. Effectiveness: With the help of variations in the tone, pitch and intensity of voice, the speaker
can convey shades of meaning. This factor also contributes to the effectiveness of oral
communication.
5. Immediate feedback:
6. More suitable:
7. A relationship develops: Oral communication is mostly carried out helps to promote friendly
relations between the parties communicating with each other.
8. Flexibility: By the demand of the situations, oral instructions can be changed easily and for
these cases maintain the formalities are not necessary. So it is very much flexible and
effective.
9. Easiness: Correction of errors: If any error is expressed at the time of oral communication.
It was possible to rectify at that time or within a very short time.
10. Informal communication: In oral communication, no need to maintain such formalities
which are needed in written communication. So it is easy and helpful to any organization.
11. Motivation: In oral communication system, top executives and sub ordinates staff can sit
face-to-face and exchange their views directly, so sub-ordinates are motivated day by day.
12. Special applications: Oral communication is more helpful in communicating messages to
groups of people at assembly meetings etc.
13. Maintaining secrecy: Interested parties of oral communication can maintain the secrecy of
messages easily.
Disadvantages of oral communication
1. No record: In oral communication, messages are difficult to record. So it is impossible to
preserve the message for future.
2. Distortion of the word: If distortion of the word occurs in oral communication, then main
goals of the organization may be filed.
3. Inaccuracy: There is very possibility of inaccurate messages to reach the destination. So, the
reverse result of expected plan may be occurred.
4. Limited use: The scope of usage of oral communication is limited. It is not suitable for
lengthy messages. It should be sued for short message.
5. Probability of omitting main subject: Sometimes, main subject may be omitted to express a
word for communicating. So, expected result may not be achieved.
6. No legal validity: there is any legal validity of the oral message. As, the oral messages are
not taped and kept records, so it can be denied easily if the situation goes against the speaker.
7. Late decision: It takes time to reach a decision. At the beginning stage, sometime is killed in
the discussion of any personal matters. Besides some time is also wasted for irrelevant
discussion. In this way decision making is delayed.
8. Less important: In oral communication, meaningless speech can mislead the main effects of
the communication. But when the information comes out in written, we take it seriously.
9. Lack of secrecy: In oral communication, the important and secret information may be
disclosed.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-122-320.jpg)
![COMMUNICATION
123rmmakaha@gmail.com
10. Creates misunderstanding: The speaker often gives message without having properly
organized it earlier. So, it is possible that he may not be able to make himself properly to
communicate with the receiver. As a result, misunderstanding May develops.
QUESTION
Explain
1. Formal Communication
2. Informal Communication [10]
1. Formal Communication
• In formal communication, certain rules, conventions and principles are followed
while communicating message.
• Formal communication occurs in formal and official style.
• Usually professional settings, corporate meetings, conferences undergoes in formal
pattern.
• In formal communication, use of slang and foul language is avoided and correct
pronunciation is required.
• Authority lines are needed to be followed in formal communication.
2. Informal Communication
o Informal communication is done using channels that are in contrast with formal
communication channels.
o It’s just a casual talk.
o It is established for societal affiliations of members in an organization and face-to-
face discussions.
o It happens among friends and family.
o In informal communication use of slang words, foul language is not restricted.
Usually.
o informal communication is done orally and using gestures.
o Informal communication, Unlike formal communication, doesn’t follow
authority lines.
o In an organization, it helps in finding out staff grievances as people express more
when talking informally.
o Informal communication helps in building relationships.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-123-320.jpg)
![COMMUNICATION
124rmmakaha@gmail.com
QUESTION
Explain
a) Horizontal Communication
b) Vertical Communication. [10]
Differences between horizontal and vertical communication [10]
Horizontal and vertical communications are the two different types of internal communication.
These two types of communications differ in the following ways:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-124-320.jpg)
![COMMUNICATION
125rmmakaha@gmail.com
QUESTION
Explain
a) Upward Communication
b) Downward Communication. [10]
Upward Communication
• When information flows form subordinated to superiors, it is called upward
communication.
• The purpose of upward communication is to provide information to the managers from
subordinates.
• Through this communication, subordinates convey their opinions, suggestions,
complaints etc. to their superiors.
• The lower-level employees initiate up-ward communication and the message ultimately
reaches to the upper-level management.
• It may take place in the form of feedback of downward communication.
The following figure represents the upward flow of information:
Downward communication
• Downward communication is the communication where information or messages flows
from the top of the organizational structure from the bottom of the organizational
structure.
• Downward communication occurs when information flows down the hierarch form
superiors to subordinates.
• This type of communication may forms such as staff meetings, company newsletter,
company policy statement, information memos, e-mail, face-to-face contact, orders,
instruction etc.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-125-320.jpg)
![COMMUNICATION
126rmmakaha@gmail.com
QUESTION
Media or ways of upward communication. [10]
The subordinates can communicate their problems, attitudes, complaints and suggestion to their
superiors through various ways. That means, there are a number ways or means or methods of
upward communication.
1. The popular written media of upward communication are discussed below:
• Report: Report is one of the most important a widely used media of upward communication.
Subordinates prepare reposts periodically or regularly on various routine issues. They also
prepare special report when need arises. Reports are then submitted to the higher authority for
supplying necessary information.
• Memo: Memo is the short form of memorandum. A memo is a short piece of writings
generally used to exchange information among the persons within the organization. Superiors
usually send information to their subordinates through memo. However, subordinates can
also write memos to convey essential information to their superiors for making decisions.
• Suggestion and complaint boxes: Some organizations install suggestion and complaint
boxes at some convenient places in the office or factory through suggestion box, management
invites the employees to submit their suggestions for improving the efficiency of
organizational operations. On the other hand, complaint box is placed to submit any
complaint of the employees regarding any aspect of their employment.
• Direct letters: Subordinates can write letters directly to their superiors at their superiors at
their own initiation or they may be asked by their superiors write about any directed matter.
• Questionnaire: Sometimes managers encourage upward communication by asking questions
to their subordinates. For this purpose, they distribute questionnaires to the employees.
Through questionnaires, management can know the attitudes, feelings and complaints of the
employees.
2. The oral media of upward communication are as follow:
• Grievance procedure: Grievance is the employee dissatisfaction over any aspect of their
employment. Grievance procedure provides the employees with a formal channel of appeal to
their superiors. In modern organizations, there is well-established procedure for handing
employee grievances that acts as a mode of upward communication.
• Joint setting of objectives: In participative organizations, superiors and subordinates sit
together for setting objectives. In this case, the superiors seek information and suggestions
from the bottom-level managers and employees.
• Employer-employee meeting: Meeting between employer and employees is a very useful
medium of upward communication. In the meeting, the superior can raise problems and seek
information, guidelines or suggestions from the subordinates.
3. Other Media: In addition to written and oral media, superiors can encourage upward
communication through the following symbolic medium.
o Open-door-policy: Open-door-policy of management inspires the employees to feel
that the manger’s doors are always open to them. Whenever they want they can enter
into the manager’s room and talk everything to the superiors without any fear or
hesitation.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-126-320.jpg)
![COMMUNICATION
127rmmakaha@gmail.com
These are the commonly used media of upward communication. However, all the media
are not suitable for every message. Selection of a particular medium in a particular
situation depends on the nature and importance of the message.
QUESTION
Media or ways of downward communication [10]
Methods of downward communication
Both written and oral methods are used in transmitting messages of downward communication.
Actually, section of media depends on the nature, urgency and importance of the message to be
communicated. The followings are the frequently used media or methods of downward
communication.
1. Oral Media or Method: Downward communication is mainly done by means of oral
media or method. Usually, the supervisors give instructions to their subordinates through
face-to-face and telephonic conversation. Beside this, managers also exchange relevant
information to their subordinates through meetings, conferences, lectures etc.
2. Written Media or Method: Organization of any size and nature sends important
information to its employees in written forms through letters, circulars, manuals,
bulletins, posters annual reports etc. generally, letters and memos communicate important
organizational directives; circulars, manuals and bulletins communicate policies and
procedures and annual report communicates organizational activities and performance at
the end of the year.
3. Other Media or Method: In addition to oral and written media or method, audio, visual
and audio-visual media are also used in downward communication. Radio, television,
poster, signal, symbol, graphs etc. some of the commonly used instruments that convey
messages to the subordinates.
QUESTION
Objectives or purpose of downward communication [10]
It is a system of communication where communication takes place form upper level to downward
or form the superior to subordinate level. The following objectives are available in downward
communication.
1. Supply information: Work style, method, responsibility, duties etc. are supplied to
subordinates by this communication system.
2. Assigning work: Through downward communication, superior assigns different works to
their subordinate.
3. Explaining policies and plan: The objective of an organization is to inform institution’s
plan, policy, program etc. to lower level by this communication system.
4. Responsibility and duty: Inter departmental duties and responsibilities are distributed by
this communication system.
5. Directing subordinates: Downward communication is directive in nature. To give
directions to the subordinates, top executives use this communication method.
6. Evaluation of performance: Top executives evaluate the performance of their
subordinate through this communication method. After evaluation of workers work, the
analyzed result is informed to others for incentive.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-127-320.jpg)

![COMMUNICATION
129rmmakaha@gmail.com
QUESTION
Explain The Term Meeting [5]
• A meeting is a group communication in action around a defined agenda, at a set time, for
an established duration.
• Meetings can be effective, ineffective, or a complete waste of time.
• If time is money and effectiveness and efficiency are your goals, then if you arrange a
meeting, lead a meeting, or participate in one, you want it to be worth your time.
• Meetings can occur face-to-face, but increasingly business and industry are turning to
teleconferencing and videoconferencing options as the technology improves, the cost to
participate is reduced, and the cost of travel including time is considered.
• Regardless how you come together as a team, group, or committee, you will need to
define your purpose in advance with an agenda.
Advantages of meetings:
In the business organizations meetings are used for a variety of purpose. There are some
advantages of meeting which are stated below:
1. Democratic process: Meeting is a democratic process of taking decision. None can
blame other for the decision because it is taken in presence of all the members.
2. Improve decision: Improve decision can be taken through meeting. Because every
matter is discussed pros and cons and nothing is left over unconsidered. Proverb says
”Two heads are better than one.”
3. Participative management: Participative management can be materialized through
meeting. Al the departmental heads and supervisors may sit together for taking decision.
4. Help in co-ordination: Meeting can help for co-coordinating the work as a whole
because all the parties or members are presented in the meeting.
5. Covey information to a large gathering: Meeting can convey information for all
departments. Besides the presented members exchange their views, idea, opinion and
feeling at a large gathering.
6. Others: Provide necessary information to a group of people, report on some incidents or
activities, create involvement and interest, formulate policies etc.
Disadvantages of meetings:
There are some limitations and disadvantages of meeting. These limitations and disadvantages are
discussed below:
1. Time consuming: Meeting takes much time to take decision
2. Costly:
3. Formalities: There are many formalities to hold on a meeting. Agenda, minutes,
regulations are needed for a valid meeting.
4. Difficult to control:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-129-320.jpg)
![COMMUNICATION
130rmmakaha@gmail.com
QUESTION
• Essentials of a valid meeting | Conditions of valid meeting
• Requirement or essentials of a valid meeting or, necessary conditions of a
valid meeting:
• Preconditions of a valid meeting: [10]
A valid meeting should have the following elements:
1. Legal objectives: Any meeting must have legal objectives. Meetings on illegal or
unethical purposes cannot be valid in the eye of law.
2. Convened by proper authority: A valid meeting should be contended by the proper
authority of the company.
3. Serving proper notice in proper time: Notice of a meeting must be served timely by
maintaining rules and regulations of the companies act.
4. Presence of authorized persons: To make a meeting valid person who is entitled to
present in a particular type of meeting should be present in the meeting.
5. Presided over by a chairman: A valid meeting should be presided over by a chairman
who will be selected by the members.
6. Specific agenda: A detail agenda should be prepared before the meeting and the meeting
should be operated by following agenda.
7. Quorum: Quorum is the minimum number of persons that must be present in the meeting
to make it valid.
QUESTION
Explain the following types of meetings.
a) Public meeting
b) Private meeting
c) Command or management meetings
d) General meetings
e) Special meetings
f) Committee meetings
g) Shareholders meeting
h) Statutory meeting:.
i) Annual general meeting:
j) Extra-ordinary general meeting:
a) Directors meeting:
b) Board meeting:
c) Special meeting:
d) Class-meeting:
e) Creditors meeting:
a) Public meeting - every member of the public is allowed (to discuss, e.g. political issues.)
a) Private meeting – Only the members of the organisation are allowed to attend the
meeting.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-130-320.jpg)

![COMMUNICATION
132rmmakaha@gmail.com
QUESTION
Duties of chairman and secretary in a meeting [10]
The chairperson: He she plays a key role in the success of the meetings: The chairperson should
therefore be tactful, diplomatic, sincere, a good communicator and above all a
respectable leader. The main function of the chairperson is to maintain order
during the meeting.
Secretary: The secretary must be well organised and attend to matters such as the venue for
the meeting, the drafting of the notice and agenda and taking down the minutes
of the meeting, The secretary should therefore, be well skilled in
communication,
Role or function or duties of chairmen of a meeting:
In all types of meetings, you have the following responsibilities as a presiding officer.
• Arranging the time and place
• Preparing and serving an agenda.
• Calling the meeting to order on time
• Making clear the purpose of the meeting
• Keeping the discussion on course
• Controlling over enthusiastic members
• Electing contributions from each member
• Creating a good atmosphere
• Summarizing the discussion form time to time
• Working to end the meeting on schedule
• Thanking to the members
Secretarial work relating to statutory meeting
1. Functions before the meeting:
• Maintaining time for statutory meeting,
• Preparing statutory statement or report,
• Drafting a notice for the meeting,
• Collecting the auditor’s certificate,
• Selection the place of the meeting,
• Preparing agenda of the meeting,
• Listing the name of members who will attend the meeting,
• Calling on board of directors meeting,
• Preparing final notice of the meeting.
• Serving the notice to the concerned members.
2. Functions at the meeting:
• Determining the quorum of the meeting,
• Stating or reading the agenda,
• Supply of the necessary explanations,
• Giving the explanations,
• Writing the rough minutes
3. Functions after the meeting:
• Preparing final minutes and resolutions,
• Submitting the statutory report
The following is expected from:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-132-320.jpg)
![COMMUNICATION
133rmmakaha@gmail.com
QUESTION
Explain the following terms
a) Notice
b) Agenda
c) Minute [10]
Notice
• A notice is a written or an oral statement that contains the particulars of holding a
meeting.
• When a circular is served among the members of the meeting to attend the meeting, it is
called a notice.
• It is letter of invitation that carries the request to the members to attend a meeting.
• A notice includes time, place, date and agenda of a meeting.
• The notice should be sent by the proper authority in due time so that the members can
attend the meeting in time.
• So, notice is formal written or formal information, notification or warning about a fact or
an invitation to the concerned person for attending the meeting.
A notice can be formal or informal.
MUTARE POLYTECHNIC
Ministry of Higher and Tertiary Education
NOTICE OF A MEETING
Notice is hereby given of a monthly academic board meeting. It is to be held in the
boardroom on the 21st
of June 2012 at 0900 hours.
The minutes of the meeting held on the 20th
of May 2012 are attached.
C Gatsi
Chairwoman
Cell: 0772 950 037
10 June 2012
Notice of a monthly meeting is given above. If you are requested to write the notice of an annual
meeting, then it is obvious that you’ll replace monthly with annual.
Agenda
• Agenda means things to be done.
• It is usually sent along with the notice of the meeting.
• It is a list of the topics to be discussed in a meeting.
• Sometimes the agenda is prepared after the circulation of the notice in order to include
the member’s opinion.
• If the subject matter of the meeting is secret, the agenda may not be circulated.
• Agenda is document that outlines the contents of a forth coming meeting.”](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-133-320.jpg)

![COMMUNICATION
135rmmakaha@gmail.com
• Minutes are the official records of the proceedings of meeting.”
• So, minutes are the brief and complete official written record of all discussion which is
held among the members of the meeting.
QUESTION
Difference between agenda and minute: [10]
Both agenda and minutes are the important documents of a meeting. But they differ from each
other in respect of the following points:](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-135-320.jpg)
![COMMUNICATION
136rmmakaha@gmail.com
QUESTION
Essential elements or factors of a valid notice: [10]
The essentials or elements or factors of a valid nonce are given below:
1. Signature: The notice must be signed by the proper authority. Only the legal authority
should serve the notice.
2. Proper time: The notice must be served in proper time. It should be circulated according
to the rules and regulations of the company or the organization.
3. Time date and place: The time, date and place of the meeting must be stated in the
notice.
4. Unconditional: There must be no condition or complexity in the notice about attending
meeting. Always a notice is unconditional.
5. Agenda: Agenda means topics to be discussed in a meeting. A valid notice should
contain the agenda of the meeting.
6. Conciseness: The notice must be short in size. It should be clear, simple and easy.
7. Proper persons: Notice should be served to the proper persons who are entitled to attend
the meeting.
8. Enclosure: An explanatory statement should be sent with the notice.
QUESTION
Importance or necessities of agenda:[10]
The necessity or importance’s of an agenda are as follows:
1. As it is circulated in advance, the members of the committee or meeting can take
preparation to discuss the topics accurately.
2. It helps to take prompt decision.
3. Since it has a set of order, it helps the chairperson to conduct the meeting smoothly.
4. It can ensure covering all the topics that will be discussed in a meeting.
5. It helps to control the unnecessary talking in the meeting.
6. It is helps to write the minutes and resolution of the meeting.
7. As it is served earlier, the members of the meeting can exchange their thought and ideas
informally before holding the meeting.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-136-320.jpg)
![COMMUNICATION
137rmmakaha@gmail.com
QUESTION
Meetings terminology [10]
Constitution: A set of rules and regulations which govern the organisation. These have
been accepted by members during the inaugural (very first) meeting. The
constitution is that which prescribes to the members how they must
behave and which decisions are legally binding.
The Quorum: A minimum of members, as prescribed by the constitution, must be
present during a meeting before a legally binding decision may be taken.
Voting on issues, therefore, presupposes that the prescribed minimum
number of members should be present (before any legally binding
decision may be made.)
The Chairperson: This person presides at the meeting. The chairperson’s duty is to
maintain order during the meeting and to control the procedure. The
chairperson's role is to run meetings in a way that encourages decisions.
The chairperson should allow fair and open discussion of matters and
stick to the agenda, so that decisions can be made. If there is no
committee, the owners corporation chairperson must be a lot owner.
The Secretary: The role of the Secretary is to support the Chair in ensuring the smooth
functioning of the Management Committee. In summary, the Secretary
is responsible for: Ensuring meetings are effectively organised and
minuted. Maintaining effective records and administration.
The Treasurer: The main duties of a treasurer are to oversee the financial
administration of the organisation, review procedures and financial
reporting, advise the board on financial strategy, and advise on
fundraising. A treasurer is in charge of the organisation’s financial
matters.
Proposal: This is a suggestion made by someone during the meeting. If a proposal
is given to be discussed before the meeting, then we call it a motion. A
motion becomes a resolution when the motion is either accepted or
rejected.
Ad hoc Committee: During a meeting, it may become clear that certain issues have to be
attended to. The appointment of members on the committee is then done
on a temporary basis: they are expected to conduct investigations into the
matters and then report back to the members at another meeting after the
completion of the investigation.
Voting: It is sometimes necessary to vote ( to reach a decision on a matter).
Voting procedures have their own terminology:
Ballot: Voting in secret, either by ballot (putting votes in a ballot- secretly- or
voting anonymously.
Deadlock: Sometimes a situation rises where equal numbers of votes are for and
against a proposal.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-137-320.jpg)



![COMMUNICATION
141rmmakaha@gmail.com
QUESTION
Enquiry/ inquiry letter [10]
INQUIRY LETTER
• Make an inquiry when you are requesting more information about a product or service.
• This type of business letter tends to include specific information such as product type, as
well as asking for further details in the form of brochures, catalogues, telephone contact,
etc.
• Making inquiries can also help you keep up on your competition!
KINDS OF INQUIRY LETTERS:
Inquiry letters fall in three categories:
1. Trade inquiry,
2. Status inquiry and
3. General inquiry
1. Trade Inquiry:-
A trade inquiry (or sales related inquiry) is written with the intention of making business deals
with the addressee. Such inquiry letters are written regarding products or services purchased or
being considered for purchase. The trade inquiries ask information about the supply of goods,
availability of goods, delivery time, leaflet or catalogue, quotations or price, method of transport,
insurance, samples and terms and discount, etc.
2. Status Inquiry:-
Status inquiry is written to know the financial position of some individual or firm usually
prospective buyer. Inquiries about the character, qualifications, experience and performance of
the applicant for job or membership may also be termed as status inquiries.
3. General Inquiries:-
General inquiry is made to get information about rules and procedures used in other
organizations, government policies, market conditions etc. General inquiry may also seek
information for private or business research. For example a firm may receive injuries for various
data from students, teachers or executives of other organizations.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-141-320.jpg)
![COMMUNICATION
142rmmakaha@gmail.com
QUESTION
John House, Washington, New York, has applied for credit purchase form Anna
Enterprise, 20, TUCSON AZ 85705 USA. In the letter, John House has mentioned the name
of Mr. Michel, Manager, Mahan Boutiques and Fabrics of Taxes, as reference.
Write business status inquiry letter on behalf of Anna Enterprise. [10]
Anna Enterprise
(Wholesaler of Quality Fabrics)
20, TUCSON AZ 85705 USA
December 07, 2013
Mr. Michel
Manager
Mahan Boutiques and Fabrics,
Texas.
Sub: Inquiring the financial status of John House, Washington, New York.
Dear Mr. Michel,
Will you please respond to the following questions about John House, Washington, New York,
which has listed your name as a credit reference on its letter for credit purchase?
1. How long John House has a credit account with your company?
2. What is the credit limit you currently extend to them?
3. What is the maximum amount of credit you have ever extended to them?
4. Has it ever been delinquent in paying his dues?
I assure you that information provided by you will be treated confidentially. If you send answers
to the above questions with December 25, 2013 will be highly appreciated. We will be highly
glad to provide you any such help in future.
Sincerely,
(Mr. Michel Jackson)
Manager, Credit Division](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-142-320.jpg)
![COMMUNICATION
143rmmakaha@gmail.com
QUESTION
Assume that you are the manager of Mr. Anna Trade International, 54, Washington, New
York. Mr. Michel Trading Agency, 302, TUCSON AZ 85705 USA has a letter to you
inquiring the financial solvency of John and company, 14/1, Taxes, Washington.
Write a positive response to this business status inquiry letter. (Favorable reply to the
inquiry letter given in specimen).[10]
Anna Trade International
54, Washington, New York
Phone: 914554656 Fax: 099-9152752568
Date: November 31, 2013
Manager
Mr. Michel Trading Agency
302, TUCSON AZ 85705
USA.
Subject: Reply to financial status inquiry of John and company, 14/1, Taxes, Washington.
Dear Sir,
Thank you for your letter of November 28, 2013. We have regular and satisfactory business
relation for long time with John and company, 14/1, Taxes, Washington about whom you have
sought information. They are doing business in this line since long ago with utmost sincerity and
honesty. Their financial capability and business goodwill are highly appreciable. Their business
dealings and payment records with us during the last several years can be held in high esteem.
You can supply them goods worth 1300$ on credit in a single consignment without any
hesitation.
We feel proud to provide information about the firm and we think our confidence on this firm
will never be misplaced. Expecting your business success.
Thanking you.
Sincerely yours.
(Mr. Jonson)](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-143-320.jpg)
![COMMUNICATION
144rmmakaha@gmail.com
QUESTION
Contents or elements of reply letter to business status inquiry letter. [10]
The particular answer business standing inquiry letter can be sometimes positive as well as
negative. Regardless of the characteristics associated with response is actually, its full of a
number of normal information as well as unique positive as well as negative view.
This items are likely to be a part of an answer to business standing inquiry letter:
• Acknowledging this notice from the inquirer. This means, acclaim with the notice
associated with request should be mentioned.
• Name, address along with points with the corporation regarding which usually
information is actually provided.
• Giving certain information as questioned through the inquirer. Data delivered should be
appropriate in addition to applicable whether it’s positive as well as negative.
• The particular replier must not fit his or her own assumptions while using the
information.
• Any affirmation producing this intention to never take any legal responsibility resulting
from long term orders while using the likely shopper.
• Requiring this enquirer to keep up secrecy with the information delivered.
• Offering warranty associated with providing additional help out with long term.
• Producing ache if the information delivered is going from the possible shopper.
• Making use of basic in addition to unambiguous words and phrases in addition to
paragraphs.
• Wanting inquirer’s business success along with thank you.
• Mentioning this name, location in addition to address with the information provider](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-144-320.jpg)
![COMMUNICATION
145rmmakaha@gmail.com
QUESTION
Quotation letter [10]
• A letter of quotation is any letter written in reference to the price of a service or product.
• This could range from a customer or client requesting or accepting a quote, to the supplier or
service provider sending the quote amount.
• Either of these letters could be headed as a letter of quotation.
• For example you would write a letter of quotation to a ventilation company explaining your
situation and requesting a quote to complete the job.
• Because money is likely to be exchanged it is important for both parties to be clear about the
service or product in question and the terms of the agreement.
Letter of Quotation Request Sample
DESU, HEAD OFFICE
9/2, Surya Kiran Building,
New Delhi (India).
25/02/2016
M/s Popular Cables,
C-12/5, Sadar Market,
Delhi (India).
Dear Sir,
You have previously supplied us cables and we should be glad if you would now quote
for the items named below, manufactured by Saru Cables. The cables we require are
listed in your Catalogue no. 24 and 38.
Catalogue No. Dimensions
No. 28...................3/2
No. 36.................3/41
No. 27.................7/20
No. 40.................1/40
Prices quoted should include packing and delivery at the above address.
While replying please state (i) discount, (ii) mode of payment, (iii) date of delivery](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-145-320.jpg)

![COMMUNICATION
147rmmakaha@gmail.com
QUESTION
Order letter [10]
• Is a document that confirms the details of a purchase of goods or services from
one party to another?
• It usually includes more information about what you are ordering, like quantity,
model number, or color, the payment terms, and the matter in which the products
are to be shipped.
• When the recipient receives this letter, they will process the order and send the
merchandise.
What are main points of a good order letter?
Mention the circumstances under which an order letter needs reply.
An order letter needs to be correct, complete and definite so that the reader may fill it exactly.
Incompleteness or errors may mean further correspondence, shipping delays, complicated billing,
repacking and reshipping and loss of business.
Therefore, a good order letter should:
1. Include full details of quantities, prices, colors, sizes etc.
2. Quote catalogue number if any.
3. State the requirements as to delivery – date, place, mode of transport etc.
4. Confirm the terms of payment agreed in preliminary negotiation.
5. Refer to the enclosure of cheque, pay order or draft or samples or colour of material if any.
Replying of Orders:
Ordinarily order letters need to reply. But replies should be written under following circumstance.
1. When a customer requests for acknowledgement in confirmation of the order.
2. When an order is incorrect incomplete or vague.
3. When an order cannot be complied with.
4. When extra time is needed to fill the order.
The letter that is written by a potential buyer to the seller requesting him to deliver goods is
known as order letter. By writing inquiry letters, buyers can collect necessary information about
the price, quality of goods and terms of sale. If the buyer finds the quoted price, quality of goods
and terms of sales satisfactory, he places an order to supply goods in his address. The seller
delivers the good according to the buyer’s order.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-147-320.jpg)
![COMMUNICATION
148rmmakaha@gmail.com
In modern time, sellers supply printed orders forms to the customers and customers place orders
by filling up those printed order blanks. In this case, the printed order sheet or blank is considered
as the order letter.
QUESTION
Factors to Be Considered In Writing Order Letter or, Contents of Order Letter [10]
• Through order letter, the potential buyers request the suppliers to deliver goods to them.
• In modern time, printed order blanks or purchase order forms supplied by the seller are
typically used for placing orders.
• However, in absence of order blanks and purchase order forms, order letters are written.
• Such letters contain three major categories of information:
• Information about the items being ordered;
• Information relating to shipping; and
• Information relating to payment.
1. Information about the items being ordered: An order letter must contain full particulars of
goods ordered. Such information include the followings:
• a. Product name
• Brand name
• Quantity
• Catalog number
• Model number
• Color
• Size
• Weight
• Unit price
2. Information relating to shipping: Shipping information is very important. In absence of
shipping information, there can arise misunderstanding between buyer and seller. Shipping
information may include the followings:
• Desired receipt date;
• Desired shipping location; and
• Mode of shipping (rail, road, or waterways).
3. Information relating to payment: Mode of payment of prices for the ordered items must be
clearly indicated. The seller will accept the order letter only when both of them come to a
common ground relation to payment of price. Payment information include the following:
• Mode of payment (cash, cheque, draft)
• Payment data
The above stated factors are usually included in order letter. However, the buyer can include any
other instruction or element if he thinks necessary.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-148-320.jpg)
![COMMUNICATION
149rmmakaha@gmail.com
QUESTION
Write an order letter [10]
Starting to Write
• Politely thank the buyer or client for their custom.
• Briefly outline the details of the transaction, such as the item model name, color
etc, the name of the buyer or client, their address if relevant, and the medium of
payment. This is essentially a summary of the order to reassure the recipient that
everything is going smoothly.
• Provide contact information so the recipient can get in touch if there’s a problem.
Letter of Order Sample
Mancini Kitchen Equipment
Troy D. Mancini
4220 Straford Park
Harold, KY 41635
Dear Mr. Mancini,
We would like to purchase twenty two (22) individual stand mixers (Model #43423), all in the
color red.
We would like you to charge this purchase to the preexisting account that we have with you,
business account #543234.
We hope to receive this order no later than Friday, November 11th, 2009. Attached to this letter
please find our preferred shipping method and receiving address.
Please confirm that you received this order by calling us at 232-231-4563 anytime during
business hours, Monday to Friday.
Thank you for your cooperation
Keller Kitchen Co.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-149-320.jpg)

![COMMUNICATION
151rmmakaha@gmail.com
QUESTION
Write a delivery letter [10]
The _______
(designation),
_______________
(company).
Subject: Acknowledgement Letter for Receiving Goods
Dear Sir,
This letter has been written to inform you, that I acknowledge the receiving of goods by
your company. The slip and invoice has been checked. All the goods are passed from the
session of checking and no defect have been found.
The number is items is proper and without any doubt. Under signatory is grateful for your
punctuality.
Warm Regards,
Name:________
Signature:_______
Designation:_______
Date:_________](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-151-320.jpg)
![COMMUNICATION
152rmmakaha@gmail.com
QUESTION
Collection letter [10]
• Letters written for realizing payments from the debtors are known as collection letters.
• The need for writing collection letters arises from credit sales.
• Selling on credit is a traditional business policy that enhances volume of sales.
• Under the credit sales policy, the sellers allow the customers a definite period for
payment of dues.
• However, sometimes the buyers make unexpected delay in paying their dues.
• Even, some custom stances, the sellers write letters reminding and requesting the
customers to pay the due bills.
• Instead of sending one letter or repeated copies of the same letter, credit departments
send a series of letters.
• “Collection letters ask customers to pay for the goods and services they have already
received.”
• “Collection letters are used by an organization to entice its charge customers to pay an
outstanding charge-account balance.”
• Collection letters are written in a series. When collection letters are written in a series
beginning with a simple reminder and end with a warning letter indication legal action
the dues promptly by retaining the customers with the company.
Features of collection letter
Collection letters possess some distinct features that differentiate them from other business
letters. Some of the features of collection letter are as follows:
1. Parties involved: Buyer who buys on credit and seller are involved in collection letter.
Seller writes this letter to the buyer for payment of dues.
2. Series of letter: Collection letters are written in a series. The series includes remainder
letter, inquiry letter, appeal and urgency letter and warning letter.
3. Objective: The prime objective of writing collection letter is to realize the dues from the
customers.
4. Governing principle: The governing principle of the letter is to collect the dues by
retaining the customers with the company.
5. Referring the previous letter: When dunning letters are written in a series, every
subsequent letter mentions the reference of immediate earlier letter.
6. Threat for legal action: The last letter of collection letter series warns the customer that
the matter has been handed over to the lawyers for taking necessary legal action.
7. Sent through registered post: The seller sends collection letter especially, the lat letter
of the series though registered with acknowledgement to avoid unnecessary delay, or
missing of the letter or denial from the part of the customer.
8. Language: The letter is written by using friendly, persuasive but straightforward
language.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-152-320.jpg)



![COMMUNICATION
156rmmakaha@gmail.com
QUESTION
Claim letter [10]
CLAIM LETTER
• When affected buyer writes a letter to the seller raising complaints and demanding
compensation, it is known as clam letter.
• Generally, a losing buyer writes claim letters to the seller.
• However, sometimes the buyer writes the letter to the transportation authority if any
damage is caused by their negligence.
• Again, seller or transportation authority may also write claim letter to the buyer claiming
their demand.
• , “A claim letter is a message designed to inform its recipient about the writer’s
dissatisfaction with a product or service.”
• “A claim letter is a request for adjustment. When writes ask for something to which they
think they are entitled refund, replacement, exchange, payment for damages and so on the
letter is called a claim letter.”
Mode of claims or Type of claims
Although claim letters are written for possible compensation or adjustment but the mode of
claims asked for are not always same. Depending on the nature of damage or loss, the buyer can
claim one or more of the followings:
• Partial or full refund of purchase price of the product or service.
• Future delivery of the products with correct items.
• Replacement of defective products.
• Repair of the damaged products.
• Reduction in the price.
• Credit the amount to purchase account.
• Cancellation of order or portion of order.
• Rescheduling the payment installments.
• Correction of error in bill.
Making a Claim
Unfortunately, from time to time it is necessary to make a claim against unsatisfactory work. This
example business letter provides a strong example of a claim letter and includes important
phrases to express your dissatisfaction and future expectations when making a claim.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-156-320.jpg)
![COMMUNICATION
157rmmakaha@gmail.com
QUESTION
What are contents of claim letters?[10]
A dissatisfied party may either discontinue business contact or may complain through a claim
letter. The former option can never be recommended.
Complaint is basically unpleasant, therefore, should be based on the following points:
1. Statement of claim, supported by facts and figures.
2. Indication of loss and inconvenience.
3. Request for explanation of the cause.
4. Emphasis on quick action.
5. Suggestion for reasonable adjustment.
6. Courteous and non-accusatory words.
Adjusting a Claim
Even the best business may make a mistake from time to time. In this case, you may be called
upon to adjust a claim. This type of business letter provides an example to send to unsatisfied
customers making sure that you address their specific concerns, as well as retain them as future
customers.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-157-320.jpg)
![COMMUNICATION
158rmmakaha@gmail.com
QUESTION
M/s. Anna cloth store, House no. 07, Road no. 14 North 302, TUCSON AZ 85705, USA has
purchased 2000 meters of suit cloths with a total cost of 12000$. from Michel enterprise. :
M/s. Anna cloth store has returned the shipment as quality does not match with the order
specification.
Write a claim letter to the manager, Michel enterprise, 20, Kualampur, Malaysia, Claiming
full refund of the purchase price. [10]
M/s. Anna cloth store
House no. 07, Road no. 14 North 302,
TUCSON AZ 85705,
USA
November 27, 2013
Manager
Michel enterprise
(Wholesaler of quality fabrics)
20, Kualampur, Malaysia
Dear Manager,
On November 07, 2013 we purchased 2000 meters suit cloths. The quality of your
shipment does not match with our order specification. Since the use of low quality cloth
will damage our business goodwill, we have returned your shipment along with a request
for cash refund of 12000$.
We believe that your company has deep concern for its customers. We are also convinced
with the earlier dealing of your company.
Refunding the money within the next 10 days will be highly appreciated. We are looking
for future business.
Sincerely,
(Mr. Jonson)
Purchase Manager](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-158-320.jpg)
![COMMUNICATION
159rmmakaha@gmail.com
QUESTION
The Bangladesh Commerce College, Road No 7, Uttara, Dhaka has purchased some books
from Jamuna Publishing Pvt. Ltd. Bangla Bazar, Dhaka. The publisher has sent older
edition of the books.
Write a claim letter for replacing the books with the new edition.[10]
The Bangladesh Commerce College
ESTD. 1992
Road No. 7, Uttara, Dhaka.
Phone————————
November 25, 2013
Manager
Jamuna Publishing Pvt. Ltd.
Bangla Bazar, Dhaka
Dear Sir,
In response to our November 10, 2013 order letter, you have sent the ordered books. You
delivery has reached to us on November 20, 2013. We have got all the books. But you
have sent the older edition of some books.
Books of older edition are being returned. We are requesting for replacing the books with
2013 edition.
Your replacing the books soon will be appreciated
Sincerely
(Mr. Jonson)
Principal](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-159-320.jpg)
![COMMUNICATION
160rmmakaha@gmail.com
QUESTION
Suggestions for improving the effectiveness of claim letter |
Characteristics of good claim letter. [10]
A claim letter possesses the general qualities of a good commercial letter like completeness,
conciseness, use of easy and simple language etc. however, a good claim letter is one that has the
following characteristics:
1. Fair claim: An effective claim letter contains a realistic, fair and honest claim or request.
If the buyer makes any unfair claim, it proves his dishonesty. As a result business
relationship between buyer and seller may end.
2. Showing confidence upon the seller: The buyer should be confidant that seller will
accept his claim. Such confidence will motivate the seller to settle the claim with due
consideration.
3. Free form anger: An effective claim letter never shows anger to the recipient. Anger or
antagonism reduces the chance of getting compensation.
4. Inclusion of facts courteously: A good claim letter states all relevant facts logically.
Courteously and impersonally. It includes neither exaggerated nor irrelevant facts.
5. Definite request: An effective claim letter makes a definite request. Such request may
be of the followings:
o Replacement of the product or service.
o Partial or full refund of the purchase price of the product or service
o Replacement of shipments
o Cancellation of an order or part of the order
o Correction of an error in bill
6. Free from guess and opinion: It is unwise to guess or to give opinion holding any
specific person responsible for the damage. The letter should be written impersonally and
the charge of detecting the responsible persons should be given to the seller.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-160-320.jpg)
![COMMUNICATION
161rmmakaha@gmail.com
QUESTION
Complaint letter [10]
• In a simple way, the letter written by the customers to convey their complaints to the
seller of goods or to the transport authority is termed as complaint letter.
• In the process of supplying ordered goods to the customers, different persons and parties
are involved.
• Therefore, there is every possibility of inadvertent mistakes being committed by
someone.
• This may create inconvenience to the customers and even cause them financial loss.
• Therefore customers write letter to inform their inconveniences to the seller or to the
transport authority.
The letter written for this purpose is known complaint letter.
• In business, occurrence of mistakes is common and natural even though the parties are
causations and careful. Some of the customary mistakes are supplying low quality
products, charging high prices, low quality packaging, damage of products due to poor
packaging etc. so complaint letter is drafted by the buyer mentioning the mistakes
occurred or claiming for the damage to the seller or to the transportation authority.
Cause of drafting complaint letter
After placing orders, customers expect that sellers will deliver the products accordingly. If the
seller fails to do so, customers write complaint letter. Such letter is usually written for the
following reasons or causes:
• Merchandise not received.
• Part of the merchandise not received
• The merchandise received was not received
• Delivery of defective products
• Goods received in a damaged condition
• Quantity of good is not what was ordered
• Goods delivered to wring address
• Delivery of goods is delayed
• Impoliteness of office staff of the seller
• Delivery of mix-up products
• Clerical or book keeping errors
• Mistakes in the bill
• Charging high price
• Price included for goods returned
• Reminders for payment of bill already paid
• Poor quality of packaging
• Faulty insurance coverage
• Missing of products during transportation
• Carelessness of transportation authority
• Ignoring the provisions regarding brokerage, commission and discount](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-161-320.jpg)
![COMMUNICATION
162rmmakaha@gmail.com
QUESTION
Factors to be considered while drafting complaint letter [10]
A complaint letter should be written in a polite and considerate way by incorporating the
following factors or elements:
1. Specific cause of complaint: In a complaint letter, the customer should mention the
specific cause of complaint. This will help the seller to understand his fault and to take
necessary step for adjustment.
2. Nature of loss: Complaint letter must specify the nature and extent of damage caused in
terms of money, loss of sales, loss of service or goodwill.
3. Amount of loss: If any financial loss has to fault to the seller or transport authority,
actual amount of loss should be mentioned with supportive documents.
4. Possible remedy: A complaint letter should clearly indicate the probable remedies for
setting the complaint.
5. Avoiding assumptions: In the letter, the buyer should include only the actual event.
There should not be any assumption on the part of the buyer.
6. Courteous language: Language of complaint letter should be simple, easy, courteous
and friendly. However, its tone should be straightforward.
7. Documentary proof: Sufficient documents should be enclosed as proof of complaint.
Without necessary documents, the letter may have no value to the recipient.
8. Controlling anger: Though anger is a natural reaction of the affected buyer, it is not wise
to express anger. Rather, the buyer should make the complaint in a respectful and
considerate way.
9. Art of presentation: Complaint should be made artfully. That is the buyer should raise
the complaint in a way that does not hurt the seller. Artful presentation requires raising
the complaints passively rather than directly.
10. Mentioning preventive measures for future: For preventing the mistakes in future, the
buyer can suggest the seller some alternative course of actions.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-162-320.jpg)
![COMMUNICATION
163rmmakaha@gmail.com
QUESTION
M/s. Anna Food Products Ltd. has placed an order on December 05, 2013 to Mr. Michel
Flour Mills Ltd. For 2000 bags of flour to be sent within December 15, 2013. Mr. Michel
Flour Mills has accepted the order but the delivery of shipment was delayed for 3 (three)
days, draft a complaint letter to the Manager, Mr. Michel Flour Mills Ltd. 10, Washington,
New York, for the delay. [10]
M/s. Anna Food Products Ltd.
302, TUCSON AZ 85705,
USA
December 20, 2013
Manager
Michel Flour Mills Ltd.
10, Washington, New York
Dear Manager,
We have placed an order on December 05, 2013 for 2000 bags of flour to be sent within
December 15, 2013. You have sent an order acknowledgement letter and promised to deliver the
shipment within the stipulate time. But it is unfortunate that the actual delivery was delayed for
03 (Three) days.
Due to your delay in sending the shipment, we could not maintain promise with our customers.
Recurrence of this problem will force us to business elsewhere.
We expect that you will take the matter seriously and will take necessary step to prevent its
recurrence. We are looking for future business.
Thanking you,
(Mr. Jonson)
Manager](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-163-320.jpg)
![COMMUNICATION
164rmmakaha@gmail.com
QUESTION
M/s. Anna enterprise, House no. 07, Road no. 14 North 302, TUCSON AZ 85705, USA, is
the seller of high quality local and foreign furniture for home and office. It has purchased
100 nos. office desks from Michel furniture Ltd. Kualalampur, Malaysia, on February 10,
2013. After receiving the shipment, some of the desks were found defective. Write a
complaint letter to the manager of Michel furniture Ltd.[10]
M/s. Anna enterprise
House no. 07, Road no. 14
North 302, TUCSON AZ 85705,
USA
February 25, 2013
Manager
Michel furniture Ltd.
Kualampur, Malaysia.
Dear Manager,
We have purchased 100 nos. of office desks on February 10, 2013 and the shipment reached to us
on February 22, 2013. After inspection of the shipment, we have found 20 (Twenty) defective
desks. Sale of the defective desks will have a negative impact on our reputation. Therefore, we
have kept those desks in the storeroom.
We believe that it was an inadvertent mistake and you will take necessary step to stop its
recurrence.
We are waiting for your decision regarding the defective desks.
Thanking you,
(Mr. Mr. Jonson)
Manager](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-164-320.jpg)
![COMMUNICATION
165rmmakaha@gmail.com
QUESTION
Adjustment letter [10]
• Adjustment letter is a reply letter to the buyer’s complaint or claim.
• In other words, when seller or transportation authority writes letter in response to the
complaint or claim letter of the buyer, it is known as adjustment letter.
• This letter informs the customer either acceptance or rejection of their complaints and
claims. Acceptance of the claims may take different forms such as simply regretting for
the mistakes, or making correction to the mistakes through payment of compensation.
Reply to complaint letter plays a vital role in enhancing the goodwill of a company and
maintaining relationships with the customers.
• “An adjustment letter is the reply to a compliant or claim letter”.
• Finally, we can say that an adjustment letter gives answer to the customer’s claim letter.
Though this letter, the seller notifies the customer whether his claim is granted or
rejected. Since this letter settles the claims of the customers, it is also termed as letter of
claim settlement. This letter helps to build and maintain goodwill with the customers.
• An adjustment letter is a reply to a complaint (claim letter).
•
• It is better to make adjustment than to risk losing a customer.
• Complaints should not be discouraged, because (1) they provide a means of discovering
and correcting poor service, and (2) They provide an opportunity to win back goodwill.
Analysis of Complaint:
In dealing with a complaint all related facts should be investigated to determine (a) whether the
complaint is justified and (b) whether, and how, adjustment is to be effected.
Justification of Complaint:
Experience proves that most of the complaints are justified. They are usually a result of fault on
the part of the seller or third party (transporter, etc.). A complaint is considered unfair when buyer
is at fault and the request is for undue advantage.
Grant of Adjustment:
A justified complain needs proper adjustment, e.g., refunding money, replacing merchandise,
performing additional service, admitting fault and assuring care in future, and taking rightful
action against third party responsible for the damage. Proper explanation is necessary if buyer is
at fault or complaint is based on misunderstanding.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-165-320.jpg)

![COMMUNICATION
167rmmakaha@gmail.com
QUESTION
Factors to be considered while drafting Adjustment Letter Or,
Contents of Adjustment Letter [10]
In drafting adjustment letter, the following points should be kept in mind so that in can convince
the affected buyer:
1. Acknowledging the claim letter: At the begging of the adjustment letter, seller
should acknowledge the claim letter of the customer and thank the customer for
pointing out the mistakes.
2. Regretting for mistakes: Reply letter should regret for the mistakes and
inconvenience of the seller sincerely. If the seller is definitely at fault, he can
apologize by saying,” I am sorry”, “We apologize” etc.
3. Immediate reply: After receiving the complaint from the buyer, the seller should
give its reply immediately. Delay in reply may create further arrogance.
4. Granting immediate promise: If the customer demanded for something specific
like a refund or replacement, the seller should grant the promise immediately.
5. Assuring preventive measures: After receiving the claim from the customers,
preventive measures taken by seller should be indicated. Seller must also assure
the customer that he will not face any such inconvenience in future.
6. Offering further cooperation: In order to promote goodwill of the company and
sustain relationship with customers, the seller should offer further cooperation and
assurance of satisfaction.
7. Convincing customer: If the claim of the customer is unfair, unreasonable and
unjust, the seller should not react violently. Rather, he should convince the buyer
to consider the matter from the seller’s angle.
8. Courteous and friendly language: The language of adjustment letter must be
courteous and friendly. Such language will cool down the anger of the buyer.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-167-320.jpg)
![COMMUNICATION
168rmmakaha@gmail.com
QUESTION
Write an adjustment letter [10]](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-168-320.jpg)
![COMMUNICATION
169rmmakaha@gmail.com
QUESTION
Memorandum[10]
What is memo or memorandum?
• Memorandum is popularly known as memo.
• The literal meaning of the word memorandum is a note to assist the memory.
• Memos are the written internal communication means for exchanging information
relating to day-to-day functions within the organizations.
• “Memorandum is a form of letters written inside the business”.
• “Memos are used to communicate with other employees, regardless of where the
employees may be located in the same organization.”
• “Memo is a written communication form one person to another (or a group of people)
within the same organization.”
• So, memorandum or memos are an internal short note or letter in which information
exchanged among superiors and subordinates or same potion of employees in the
organizational structure.
Advantages of memo
We know memorandum serves various purposes. it is a common means of writer, communication
within the organization. The main advantages of memos are discussed below:
1. Time saving: We can see that may organizations use printed memo. As it is usually
printed, it takes less time to draft it.
2. Less formality: No formality is necessary in drafting a memo, usually inside address,
salutation and complimentary closing is omitted in it.
3. Maintenance good relationship: It can help to maintain the good relationship among the
boss and subordinates, because the bossing attitude is absent here.
4. Low cost: The cost of communication through a memo is less than those of others.
5. References: Memo is a written document. So, it can be used for future references.
6. Inform the decisions and actions: The main objective of memo is to inform the
decisions and actions. For this purpose, it should be written by the higher authority.
7. Request the decisions and actions: The objective of memo is to request the decisions
and actions. For this objective, it may be drafted by the sub-ordinate.
8. Provide information: Another important objective of the memo is to provide
information form one level to another within the business.
9. Remain someone of action: Memo is also written to remind someone of action, if
requires.
10. Others: Issuing orders and instructions, providing response, providing suggestions,
presenting informal report, solving problems.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-169-320.jpg)

![COMMUNICATION
171rmmakaha@gmail.com
QUESTION
Different Parts of a Memo [10]
Here you will get Different structure or parts of a memo. There are usually three main parts to a
memo:
1. The heading
2. The subject and date
3. The message.
1. The Heading: The heading of a memorandum is usually printed. It contains the name of the
organization and ‘To’ and ‘From’ sections. Make sure you address the reader by this or her
correct name and job title. Be specific and concise in your subject line.
In section ‘To’, a courtesy title – Miss, Mrs., Mr., Dr. is often included. But in section ‘From’ the
write does not use a courtesy title. The heading segment follows this general format:
2. The subject and Date: The subject is a brief statement telling what the memo is about. The
subject line is not a complete sentence but rather a concise phrase which indicates some specific
information. The date of writing memo is also important to take action in time.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-171-320.jpg)


![COMMUNICATION
174rmmakaha@gmail.com
QUESTION
Contents of a CV [10]
Contents of resume: Contents and layout of resume or curriculum vitae vary widely. There is no
single best way to write resume.
However, a factual and effective resume usually contains the following contents:
1. Opening section: Opening section of a resume generally includes following two items:
o Identifying information: Identifying information includes name, contact address
(both present and permanent), e-mail address and telephone number of the applicant.
o Career objective: A modern resume includes a statement of immediate and long-
term career objective of applicant. This statement helps the employer to evaluate
what type of job the applicant likes. Career objective also helps the employer to
categorize the applicants.
2. Education or academic qualification: This section of resume contains a list of degree
achieved along with name of the in situation granting the degree, year of obtaining the
degree, courses taken, position obtained etc.
3. Work experience: In this section, a list of employment and description of work experience
are incorporated by following a reveres chorological order. It mentions employer’s name and
location, duration of employment and position held.
4. Achievements and awards: This section includes school and community memberships,
offices held, honors, publications, language skills etc. of the applicant.
5. Personal data: Personal data include applicant’s age, religion, gender, nationality, marital
status, hobby, height, date of availability etc.
6. Reference: Most resumes mention references from which the employer can seek information
about the applicant. Generally, name of the former employers and teachers are mentioned as
reference.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-174-320.jpg)
![COMMUNICATION
175rmmakaha@gmail.com
QUESTION
REPORTS [10]
• Are fixed format documents. They are written as a result of instructions given to someone
to investigate and report on a problem.
• A report is written for a clear purpose and to a particular audience. Specific information
and evidence are presented, analyzed and applied to a particular problem or issue.
• The information is presented in a clearly structured format making use of sections and
headings so that the information is easy to locate and follow.
• When you are asked to write a report you will usually be given a report brief which
provides you with instructions and guidelines.
• The report brief may outline the purpose, audience and problem or issue that your report
must address, together with any specific requirements for format or structure.
• This guide offers a general introduction to report writing; be sure also to take account of
specific instructions provided by your department.
Purposes or Objective of Business Reports
Reports are the primary means of communication in organization. In large-scale organizations,
there is no alternative to use reports. Reports also play an important role in small-scale
organizations. Some points highlighting the purposes or objectives or important of business report
are presented below-
1. Transmitting Information: Business report is very important for transmitting information
from one person to another or form one level to another. Although a manager can personally
collect required information in a small scale enterprise, it is not possible in the context of a
large scale organization. In the latter case, the managers rely on reports for obtaining
necessary information.
Interpretation and Explanation of event: Report provides interpretation and explanation of
information. As a result, readers can easily understand it.
2. Making decisions: A report is the basic management tool for making decisions. The job of a
manager is nothing but making decisions. Reports supply necessary information to managers
to solve problems.
3. Communication with external stakeholders: In addition to internal use, reports also
communicate information to the external stakeholders like shareholders, creditors, customers,
suppliers, government officials and various regulatory agencies. In the absence of formal
business report, such stakeholders would remain at dark about the organizations.
4. Development of information base: Reports also contribute to the development of
information base in organization. It develops information base in two ways. Firstly, day to
day information is recorded permanently for writing reports. Secondly, the written reports are
preserved for future reference. In these ways, reports help in developing a strong and sound
information base.
5. Developing labour management relationship: Reports also help to improve labour
management relationship particularly, in large organizations. In a large organization, there is
little opportunity of direct communication between top-level management and employees. In](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-175-320.jpg)


![COMMUNICATION
178rmmakaha@gmail.com
QUESTION
TYPES OF REPORTS:[10]
• Informative report (stresses about facts) –give the facts of a situation. The writer will
also stress the procedures
• Investigative Reports (gives results of an investigation and recommends action) – are
written because the writer has been instructed to investigate the problem, draw
conclusions from the facts and recommendations. The writer for example has been asked
to investigate the causes of the factory fire, draw conclusions and recommendations
• Feasibility Reports (examines whether something can be done or not and recommend
action) are related to investigation reports. They are written because someone has been
instructed to investigate whether something can or should be done or not.
• Evaluative reports – investigation and feasibility reports evaluate the facts.
• Technical reports – contains large amounts of technical information. Information often
set in tables, graphs e.tc
• Interim reports - Are written to inform managers of the progress of a project.
PROGRESS REPORTS
• Progress reports are common and critical documents in science and engineering.
• The basic point of a progress report is to summarize the status, progress, and likely future
for a particular project.
• In a progress report you are often expected to commit to an exact schedule for the project
completion, discuss the status of the materials being used and account for the money
spent, and summarize concretely both the current findings and the predicted results. T
• he professionalism of the progress report is often vital to the future of the project.
Style for Progress Reports
The following stylistic advice can be applied to most progress reports you write:
• Include a working title and the words “Progress Report” at the top of the page.
• Use section headings in the report to simplify both the writing and reading process.
• Open the report with a “Scope and Purpose” section, where you give a condensed version
of your future report’s introduction and objective.
• Always include a section entitled, for example, “Progress,” which summarizes the work’s
pace and progress and explains any snafus, dilemmas, or setbacks.
• Always include a section entitled, for example, “Remaining Work,” which honestly
assesses the work that must still be completed. Think right on the page in this section,
posing questions, speculating meaningfully, exploring your options.
• Always include a section that projects the expected results. Commit to a schedule for
obtaining those results if possible.
• If necessary, include a section in which you directly solicit advice from your teacher or
advisor. Be forthright and professional about the nature of the advice you need.
• Keep your paragraphs short and focused—just a few paragraphs per section, typically.](https://image.slidesharecdn.com/communicationcomputerskillswip-160222173611/85/COMMUNICATION-COMPUTER-SKILLS-178-320.jpg)



