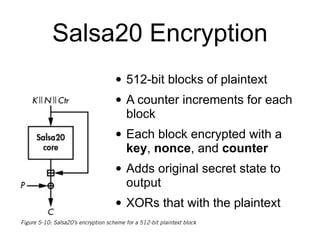
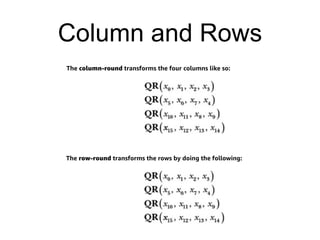
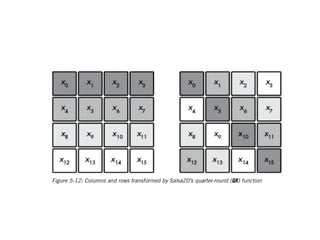
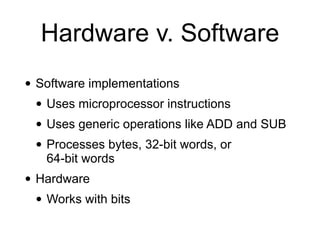
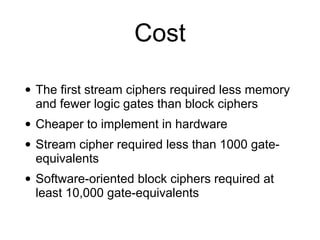
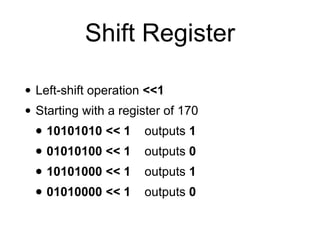
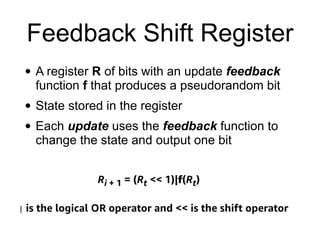
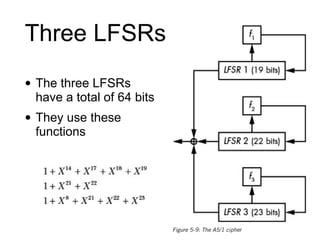
The document provides a comprehensive overview of stream ciphers, focusing on their workings, types, security weaknesses, and examples such as RC4 and Salsa20. It discusses the role of the NSA in cryptography, including their influence on cipher design, and highlights historical vulnerabilities, nonce reuse issues, and practical attacks on specific algorithms. Additionally, it compares hardware and software implementations, emphasizing the efficiency of stream ciphers in various contexts.





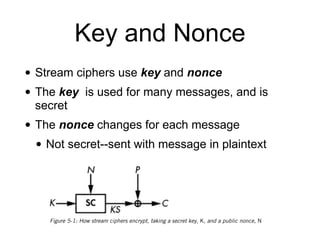


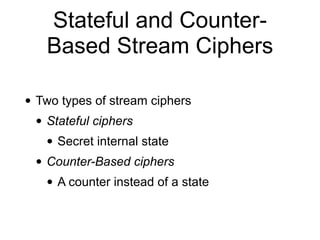
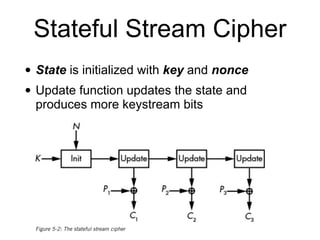
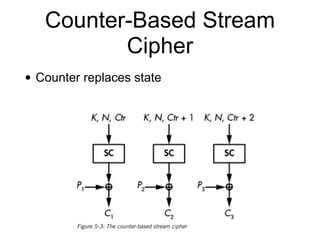



























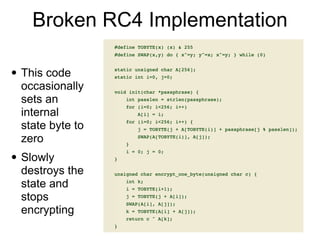
![How RC4 Works
• Internal state is 256 bytes, starting at
• S[0]=0; S[1]=1; S[2]=2, ... S[255]=255
• All it does is shuffle those values around like a
deck of cards
• No XOR or OR or AND](https://image.slidesharecdn.com/141-ch5-210922212008/85/CNIT-141-5-Stream-Ciphers-57-320.jpg)