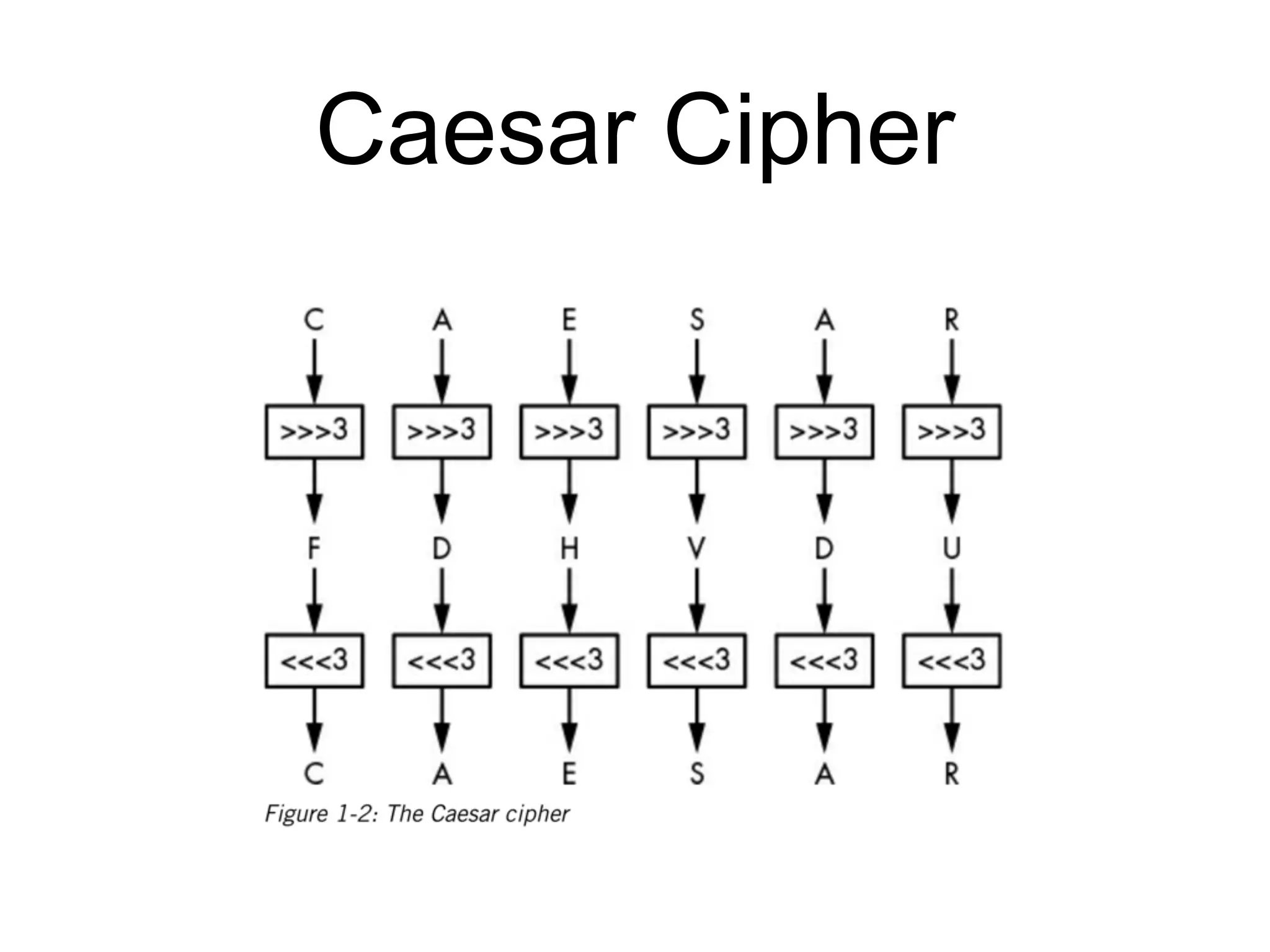
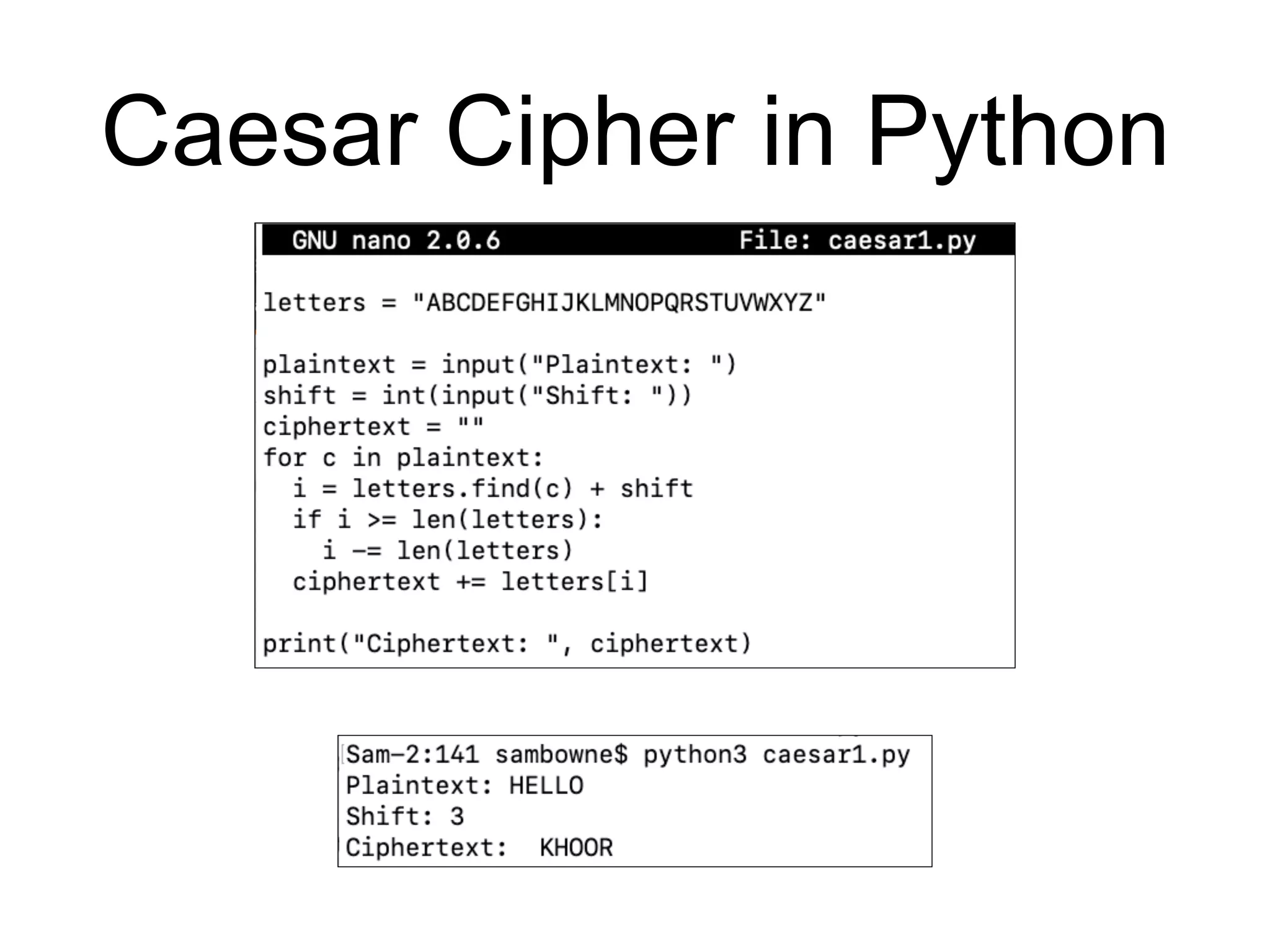
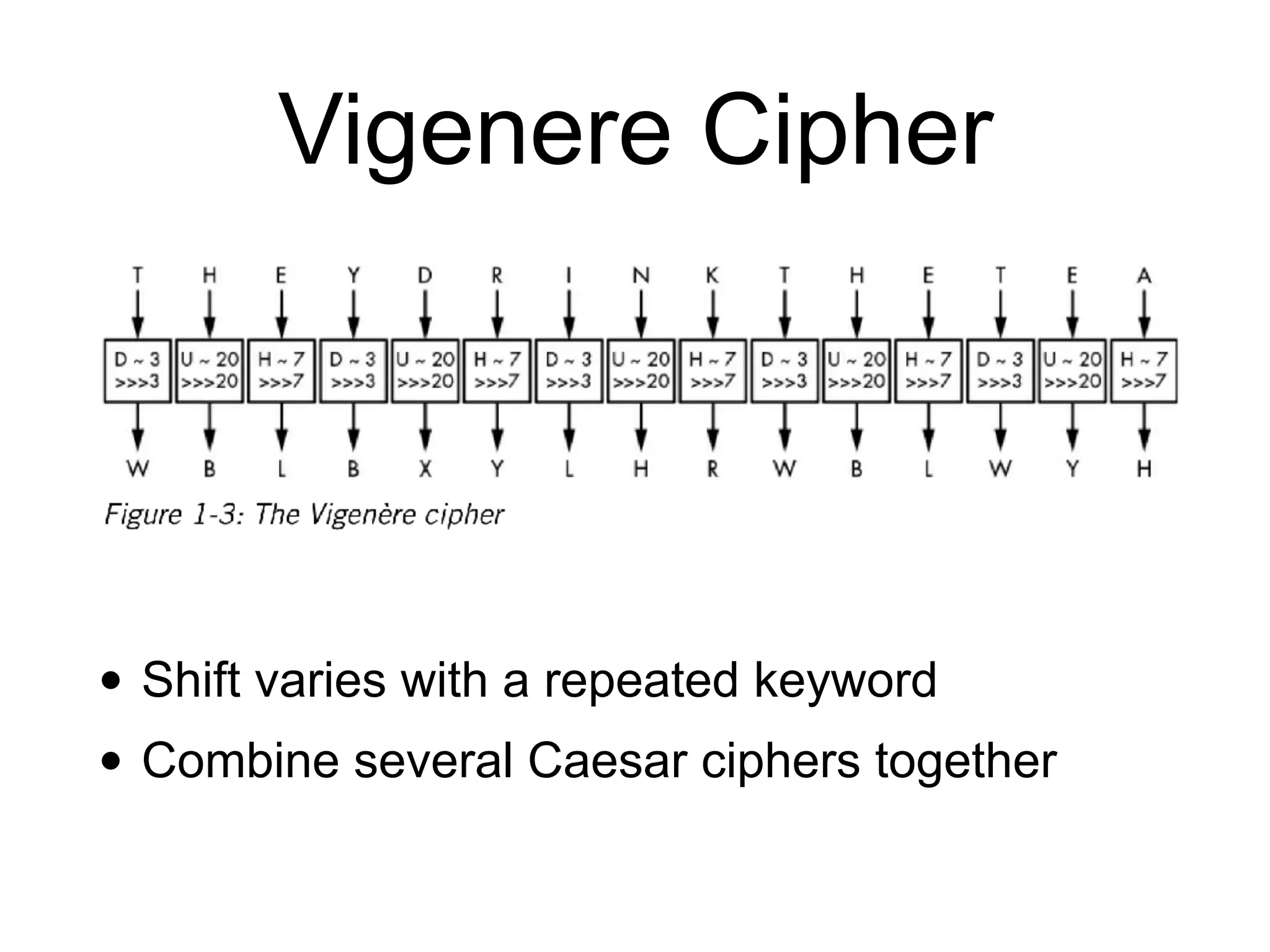
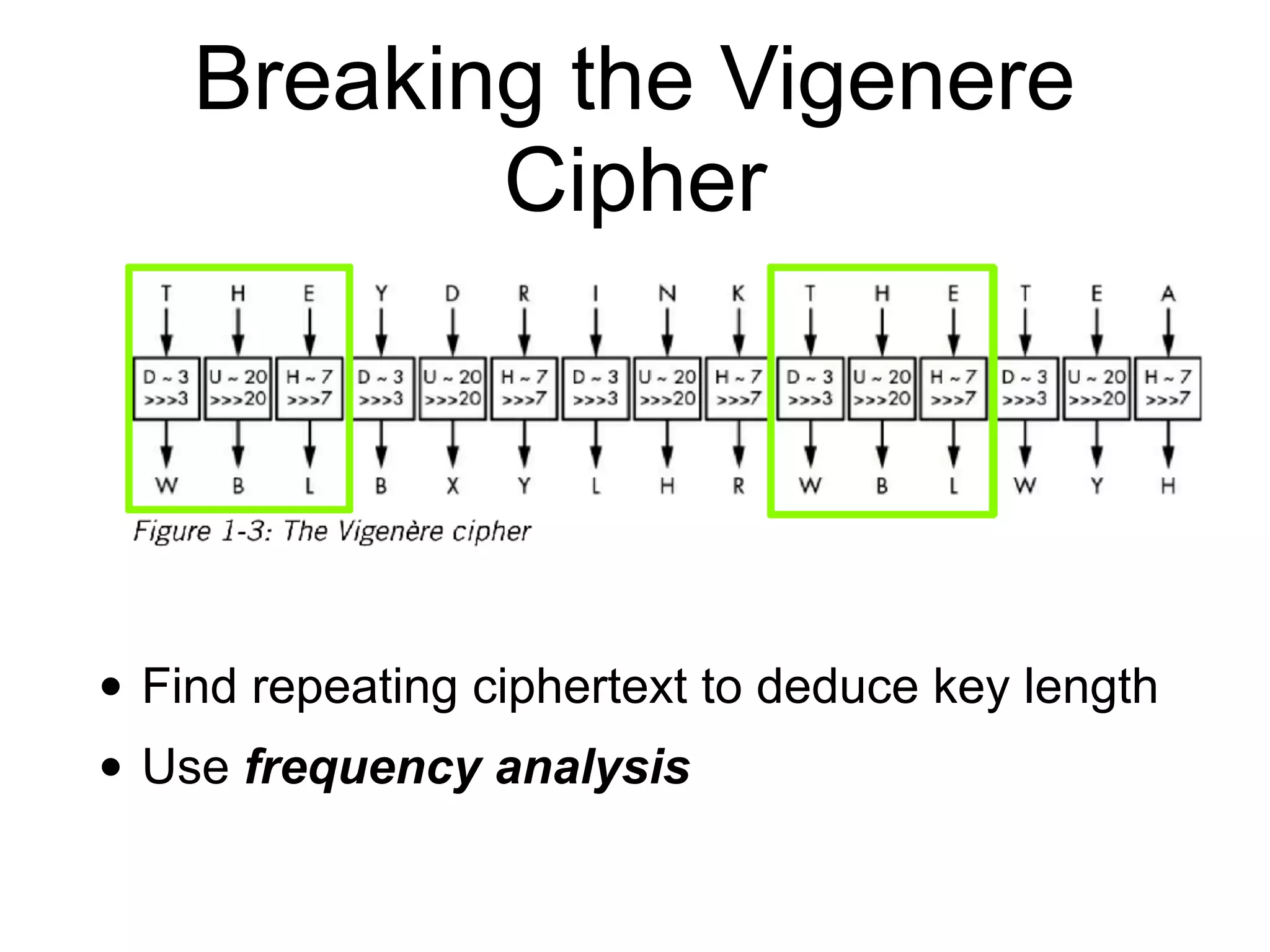
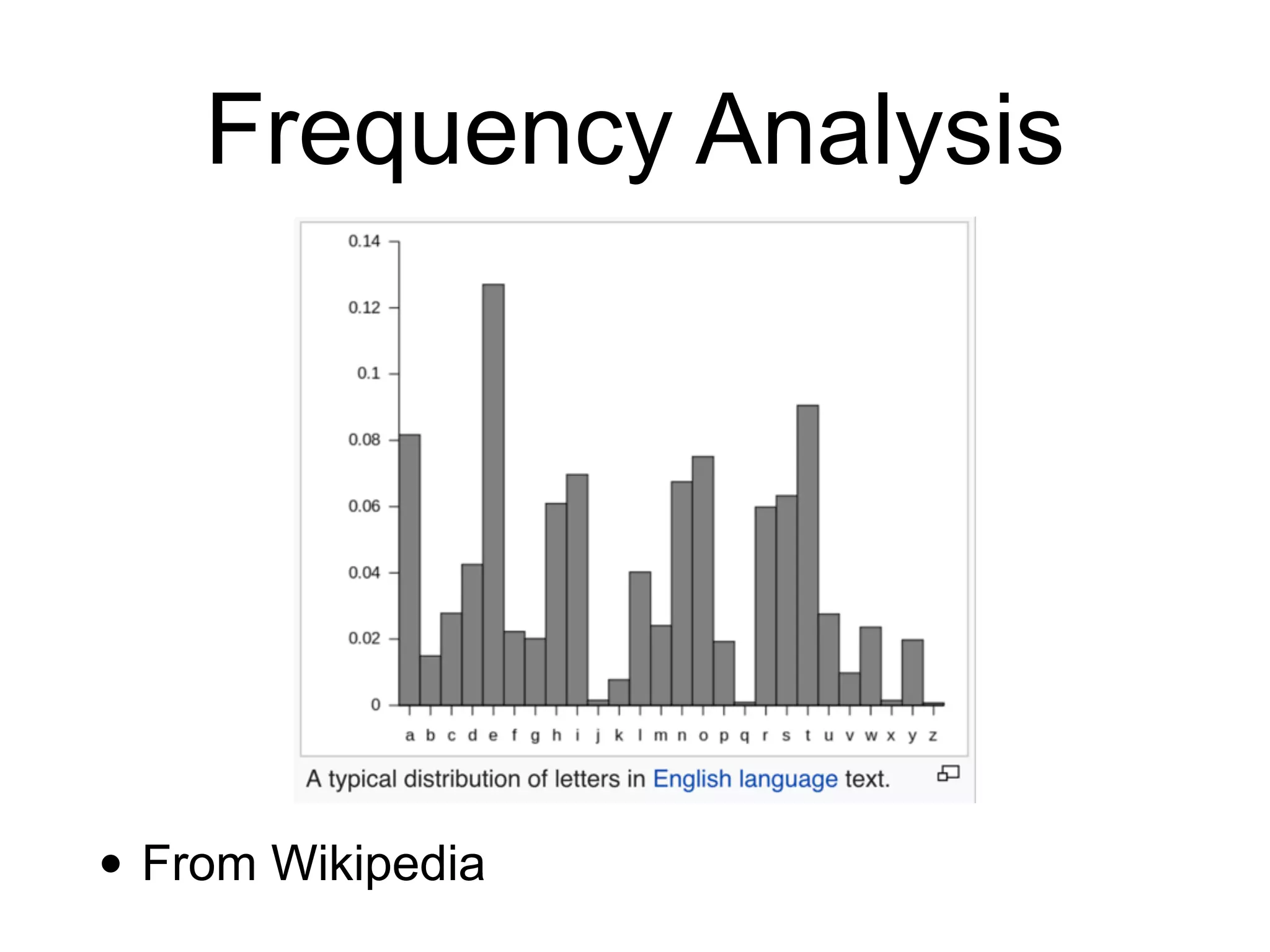
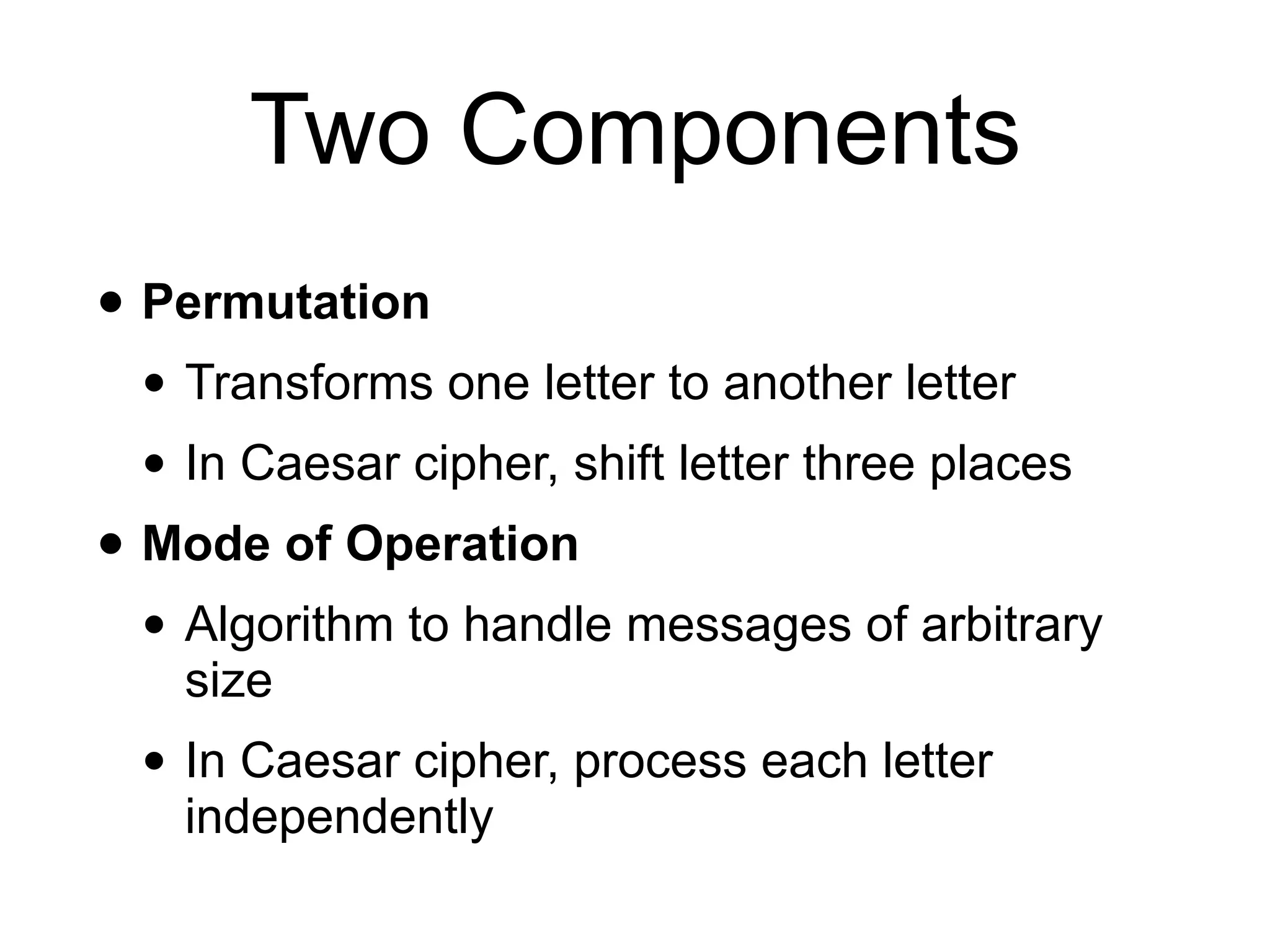
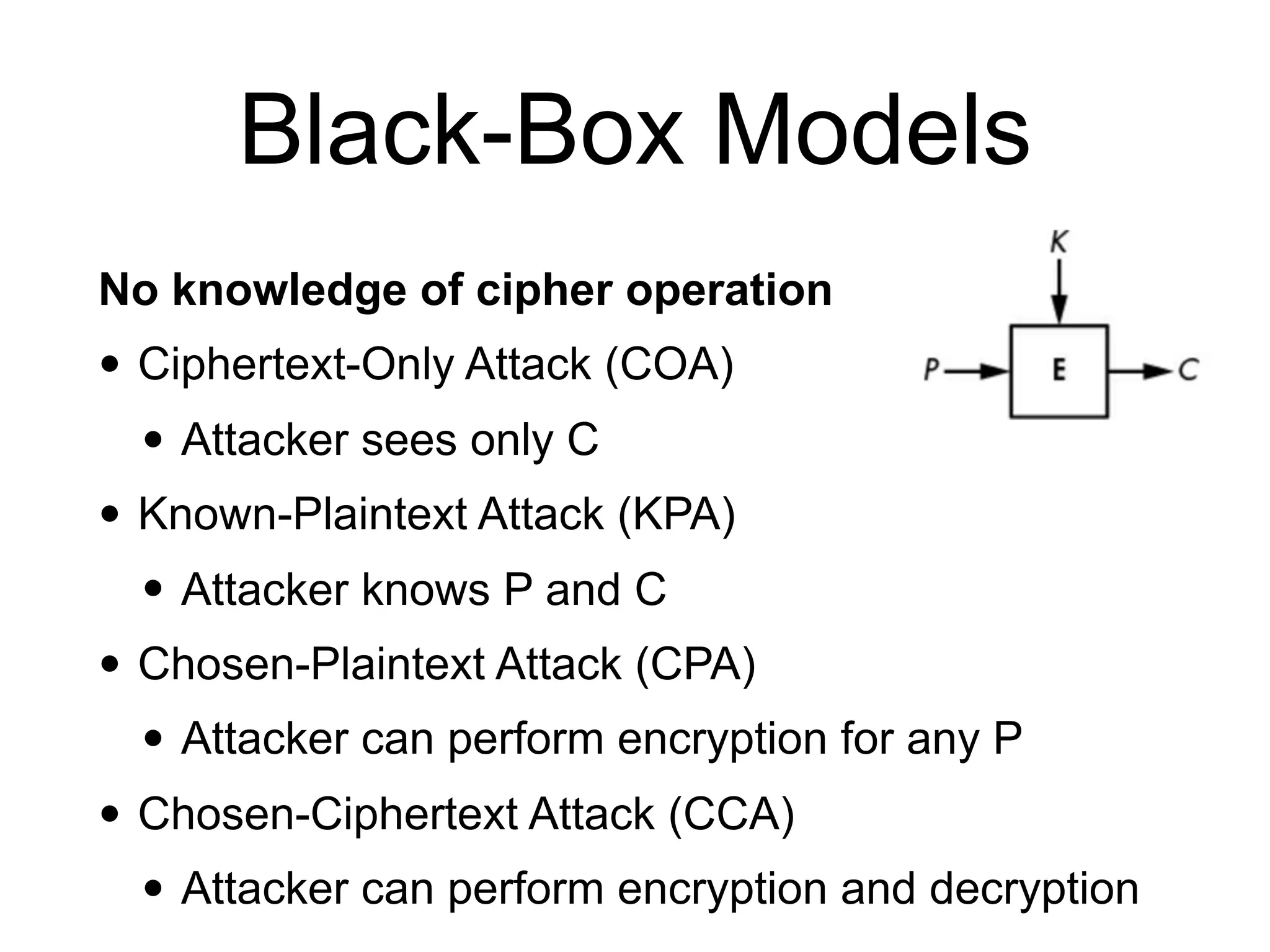
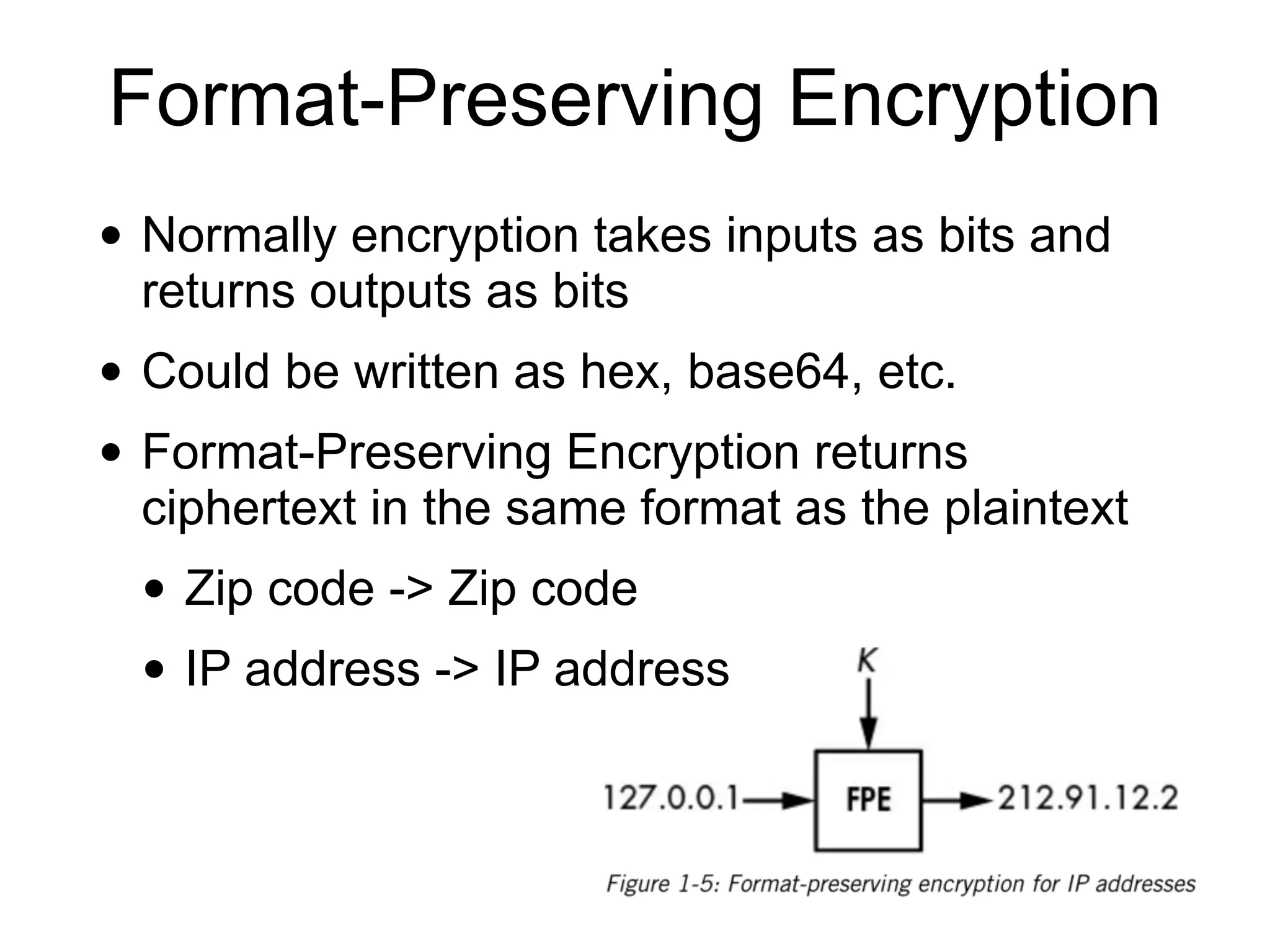
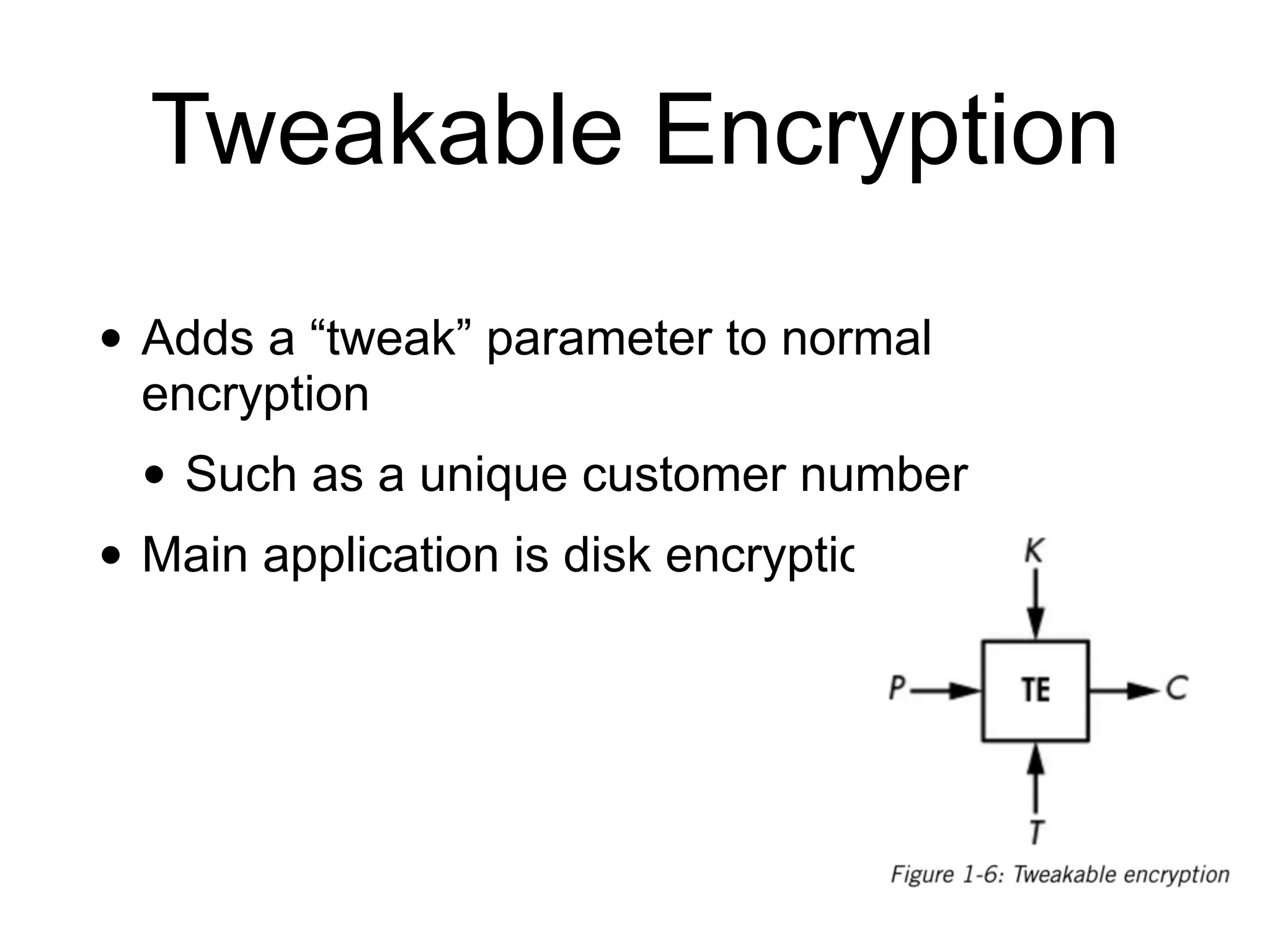
This document provides an overview of cryptography topics for computer networks, including the basics of encryption with keys and ciphertexts. It discusses classical ciphers like the Caesar cipher and the Vigenere cipher. It also covers modern symmetric ciphers, the one-time pad, encryption security models, asymmetric encryption, and ways encryption can be used beyond just encrypting data, as well as how implementations can potentially go wrong.