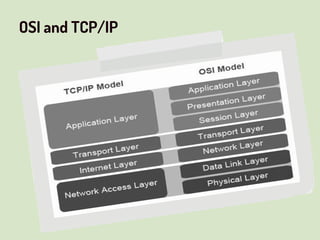
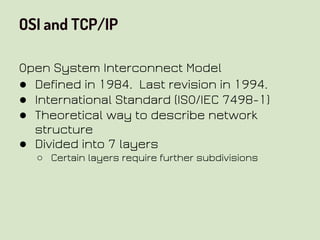
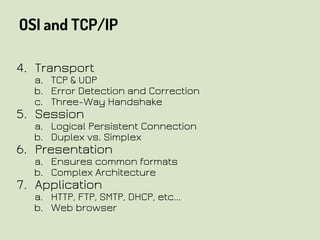
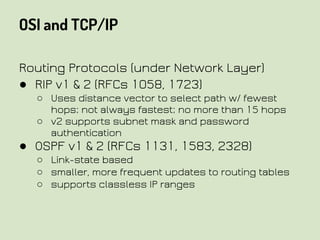
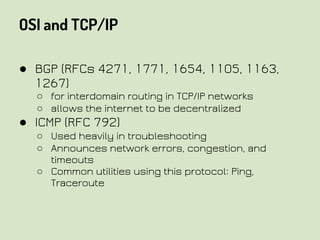
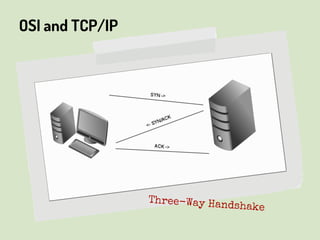
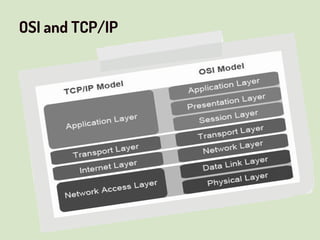
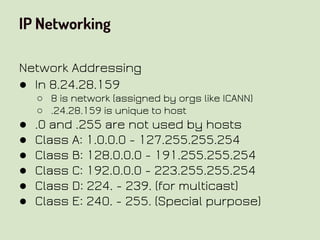
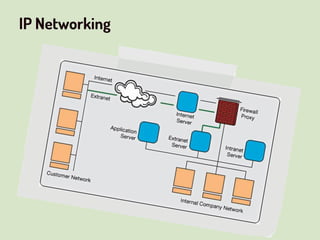
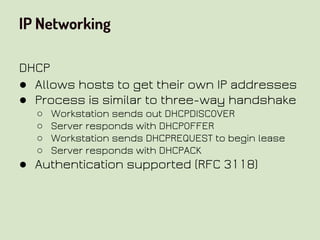
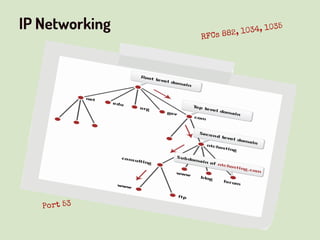
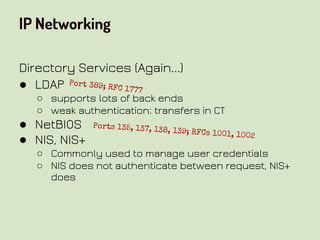
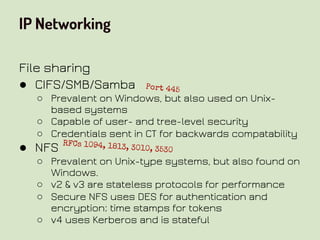
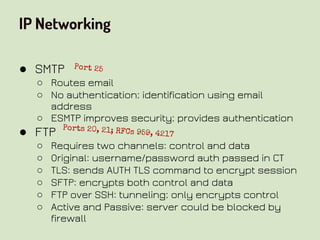
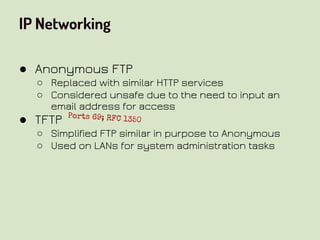
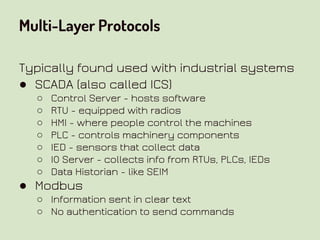
This document provides an overview of network security concepts related to the OSI model, TCP/IP, IP networking, and multi-layer protocols. It describes the seven layers of the OSI model and compares it to the TCP/IP model. It discusses IP addressing schemes, routing protocols, TCP/IP ports, DHCP, ICMP, and networking services like DNS, LDAP, FTP, SMTP, and HTTP. It also covers implications of industrial control systems that use multi-layer protocols like SCADA and Modbus.