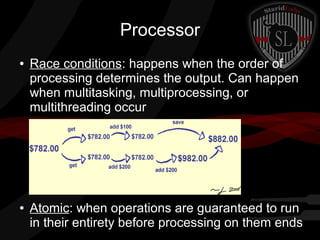
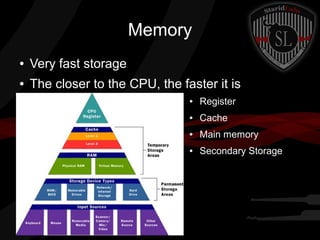
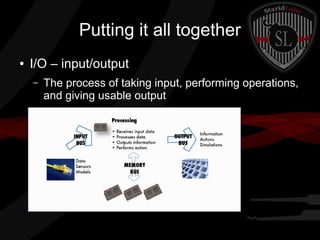
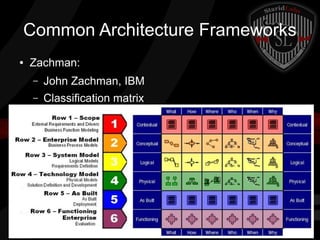
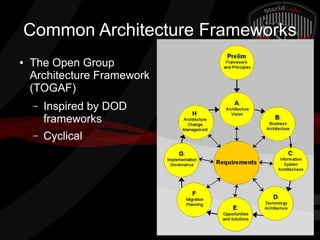
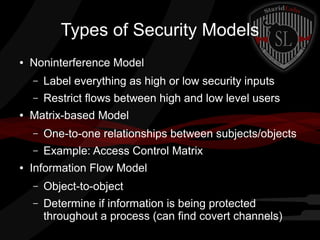
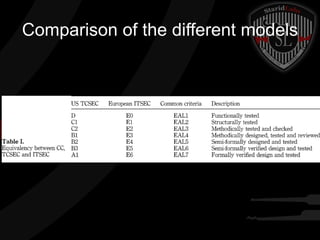
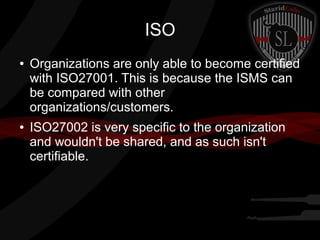
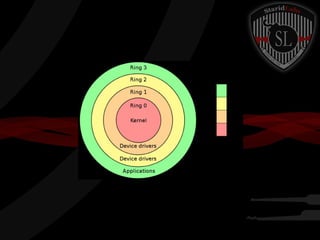
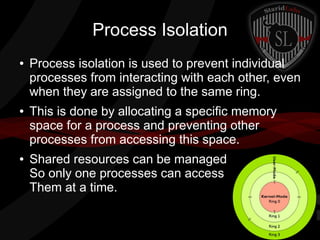
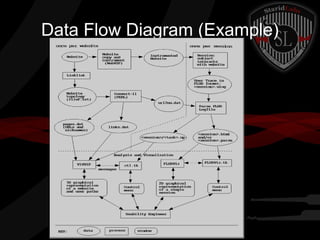
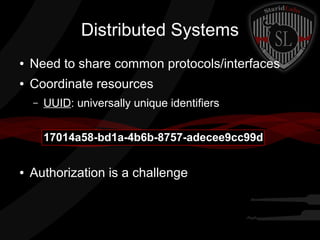
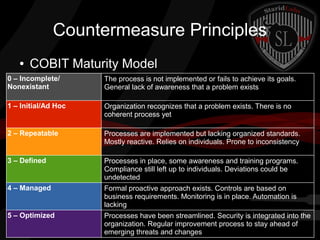
This document provides a high-level summary of the key concepts covered in Domain 6 of the CISSP CBK third edition on pages 902-1003 regarding security architecture and design. It discusses common system components like processors, memory, and peripherals. It also covers security models, frameworks for security architecture like Zachman and TOGAF, standards like ISO 27001, and mechanisms to provide security capabilities in information systems such as access control, secure memory management, and cryptographic protections.