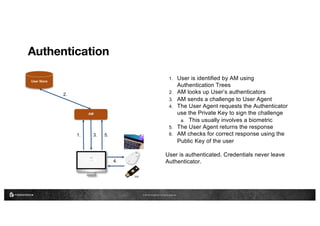
This document summarizes a talk on FIDO2/WebAuthn standards for strong authentication. It provides a history of the FIDO Alliance and their specifications. It describes the key aspects of FIDO2, including bound authenticators that can only be used on a single device. It outlines how WebAuthn allows strong authentication through public/private key cryptography without credentials leaving the authenticator device. The benefits are strong authentication on many platforms, ease of integration for developers, and a better security and user experience compared to passwords. Diagrams demonstrate the registration and authentication flows using public/private key techniques.