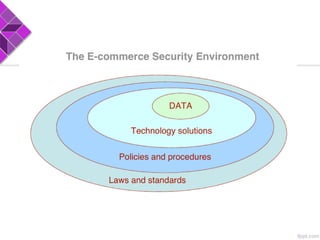
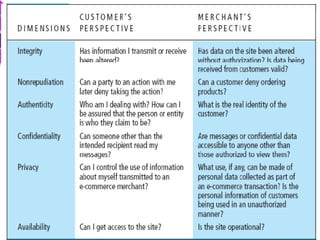
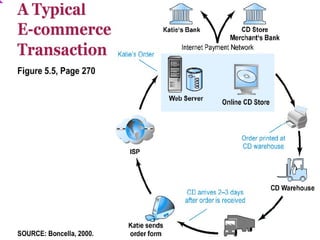
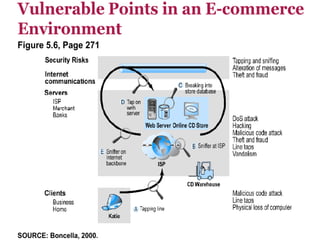
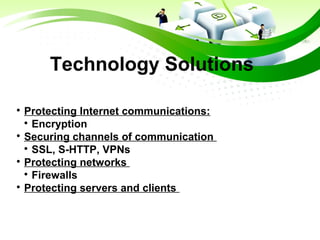
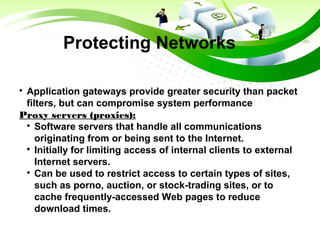
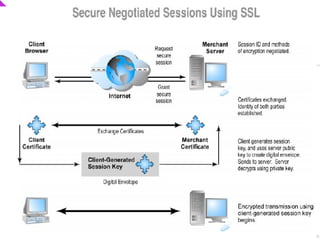
This document discusses e-commerce security threats and solutions. It outlines several security threats including malware, phishing, hacking, credit card and identity fraud. It also examines dimensions of e-security like integrity, authenticity, confidentiality and availability. The tension between security and ease of use is explored. Technology solutions to secure communications and networks through encryption, SSL, firewalls and anti-virus software are presented.