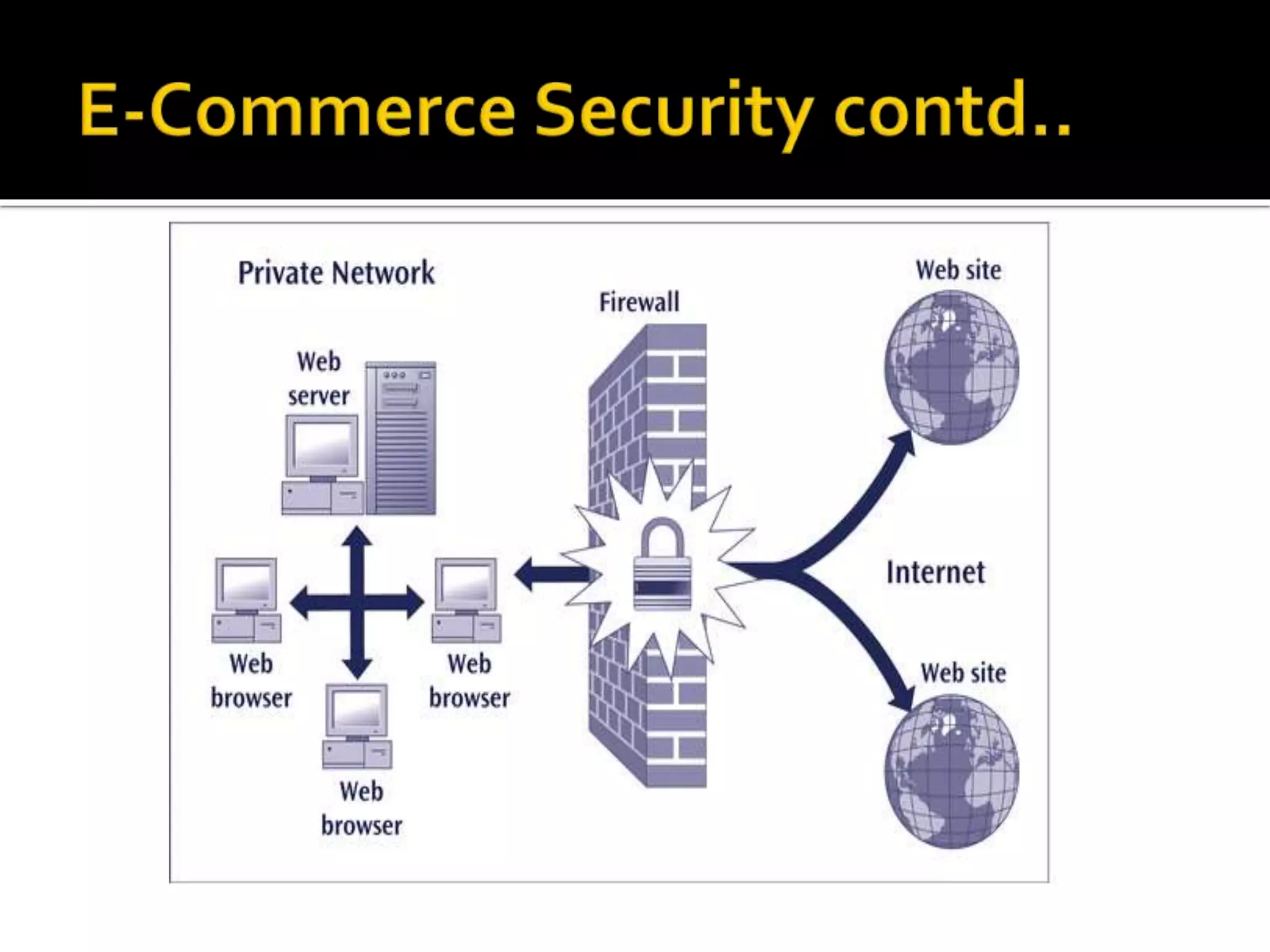
This document summarizes security issues and threats facing e-businesses. It discusses how computerization and networking have increased security risks by exposing private networks to public threats. Technical attacks like hacking, malware, and denial of service as well as non-technical social engineering pose major risks. The document recommends tools like passwords, firewalls, and encryption to protect data and transactions. Regular security audits and testing are also advised to evaluate vulnerabilities and safeguard e-commerce over the long run as threats continue evolving.