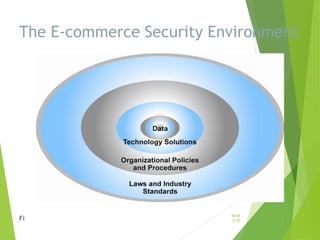
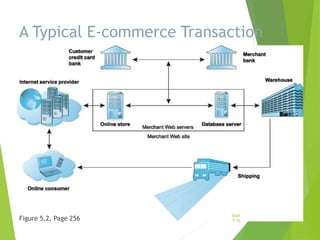
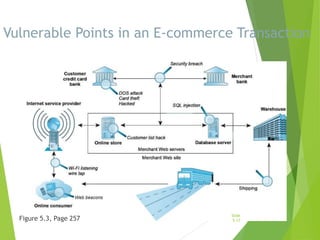
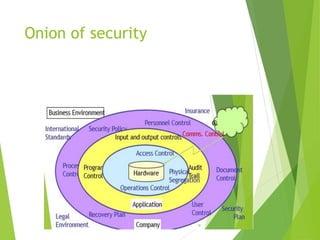
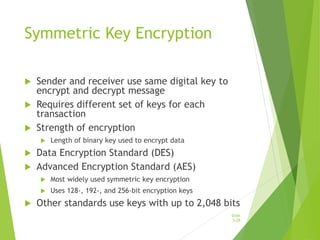
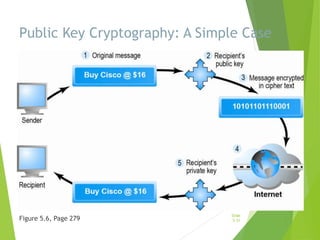
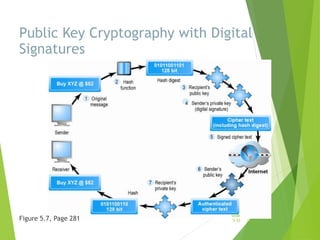
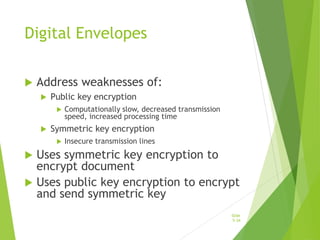
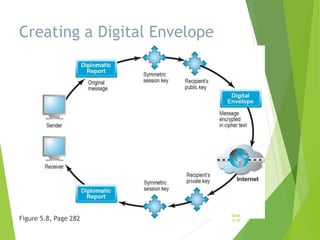
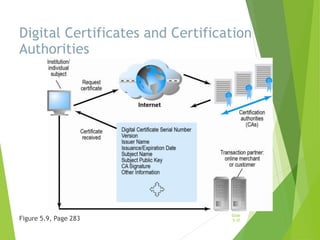
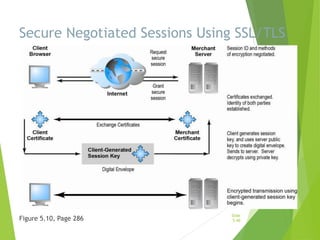
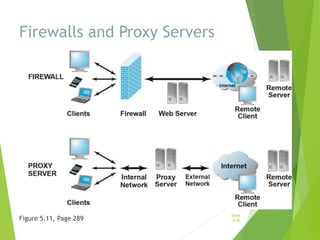
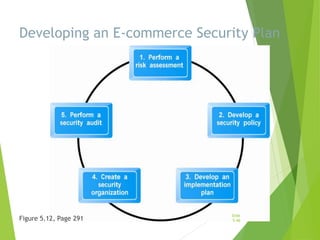
Chapter 5 focuses on e-commerce security, outlining the threats posed by cybercrime and the vulnerabilities within client, server, and communication pipelines. Key statistics reveal that the majority of cybersecurity breaches result from human error, with financial motives behind a significant percentage of cyber incidents. The chapter discusses the importance of a security policy, management procedures, encryption technologies, and various legislation in protecting sensitive information and achieving robust security in e-commerce environments.