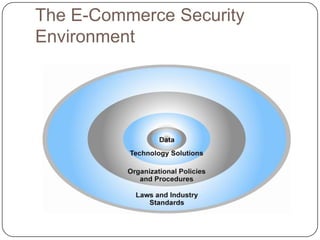
E-commerce security faces significant threats from cybercrime, including identity theft, phishing, and various forms of hacking, with losses in the billions projected annually. Effective e-commerce security requires a combination of technology solutions like encryption and policy frameworks designed to mitigate risks. While advancements have been made, balancing security with usability remains a challenge as organizations strive to protect both consumer data and their operational integrity.