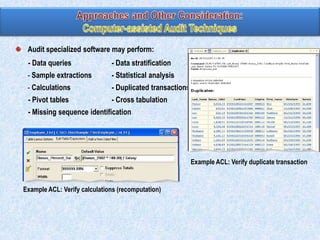
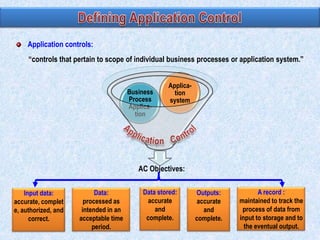
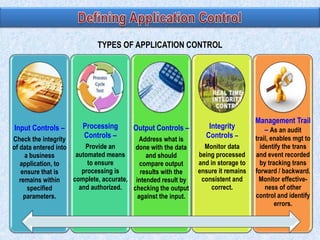
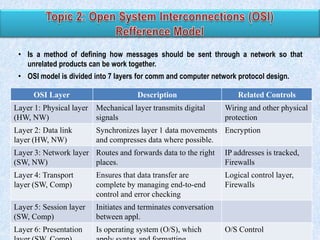
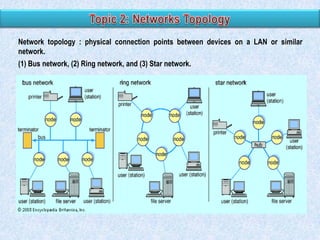
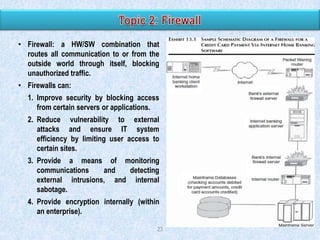
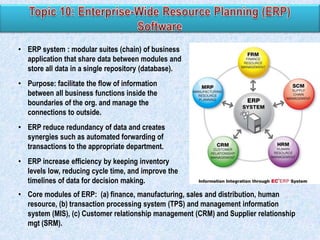
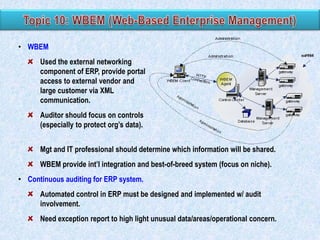
The document discusses various types of application controls. It begins by listing the most common types as input control, process control, and output control. It then provides more details on each type of application control, including definitions and examples. It explains that application controls regulate the input, processing, and output of an application in order to ensure complete and accurate processing of data. The risks of input, processing, and outputs are also summarized.









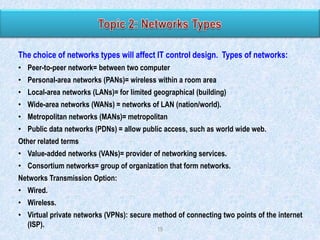







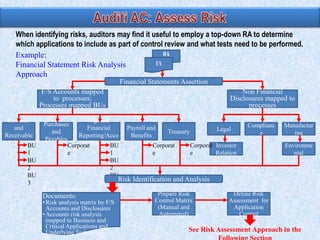

![Composite scores = ∑ (risk factor weight x risk scale) and adding the totals.
The composite score of 375 = [(20 x 5) + (10 x 1) + (10 x 5 ) +…].
For this example, the auditor may determine that the application control review will
include all applications with a score > 200.
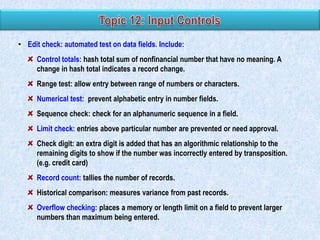
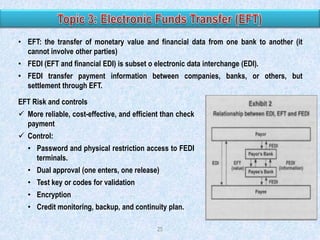
Risk Factor Weighting
20
10
10
10
10
10
Applica- Application
Design
PreApp supports Frequency of Complexity
tion
contains
effective- packaded more than one
change
of change
primary ness of the
or
critical business
controls App control developed
process
15
15
100
Financial Effectivenes Composite
impact
s of the
scores
ITGCs
App A
5
1
5
5
3
3
5
2
375
App B
1
1
2
1
1
1
4
2
170
App C
5
2
2
1
5
5
5
2
245
App D
5
3
5
1
5
5
5
2
395
App E
5
1
1
1
1
1
3
2
225](https://image.slidesharecdn.com/03-140215091504-phpapp02/85/03-2-application-control-35-320.jpg)