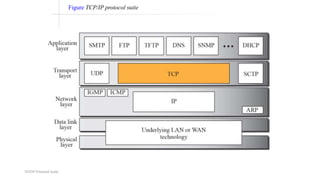
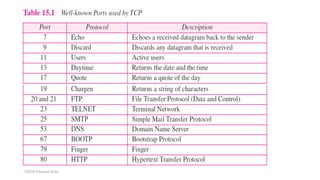
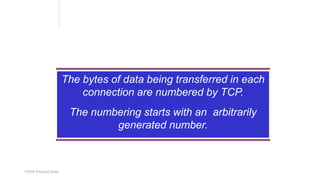
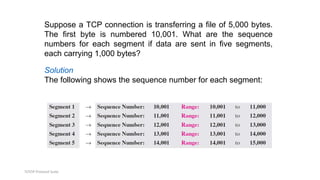
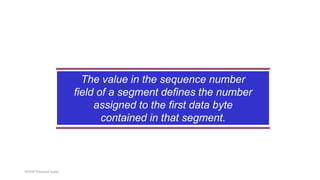
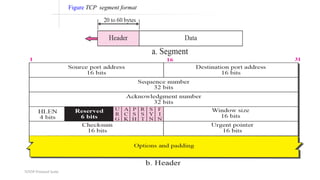
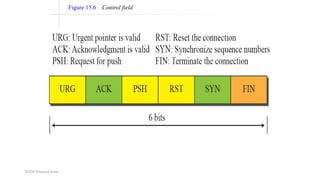
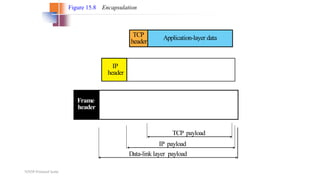
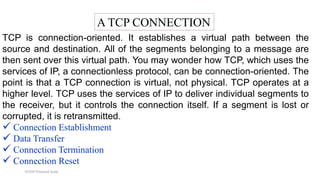
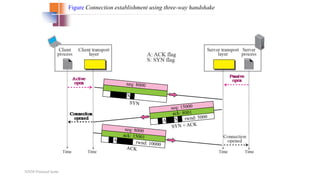
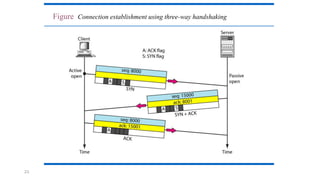
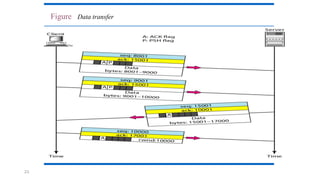
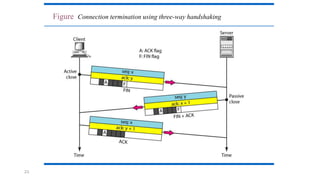
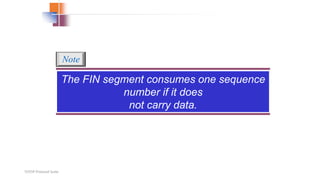
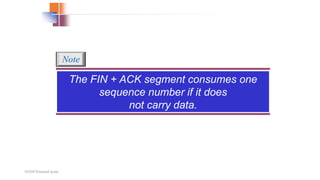
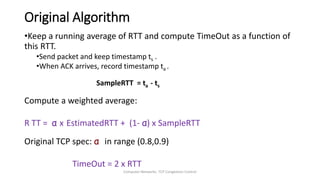
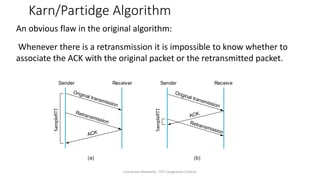
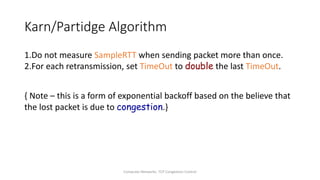
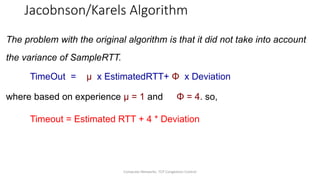
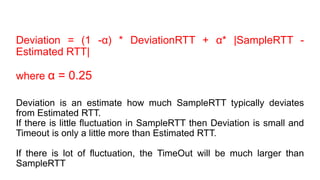
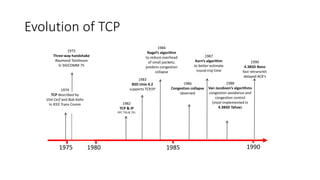
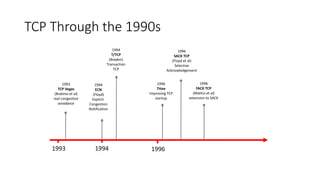
TCP provides reliable data transfer through several key features:
- It numbers data bytes and uses acknowledgments to ensure all bytes are received correctly. If bytes are lost, they are retransmitted.
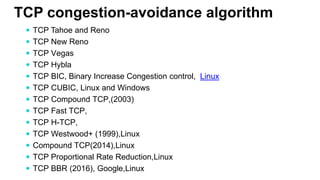
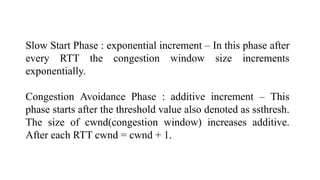
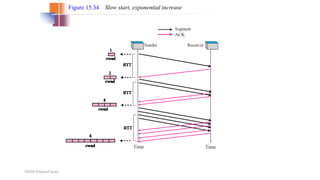
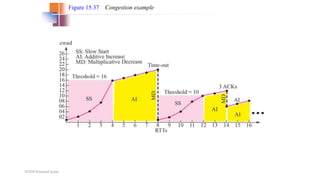
- Congestion control algorithms like slow start and congestion avoidance allow TCP to gradually increase data transfer rates while avoiding overwhelming the network.
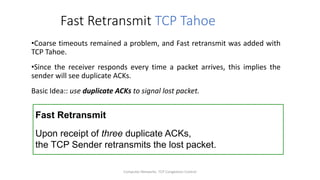
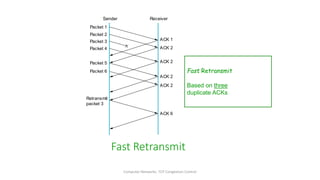
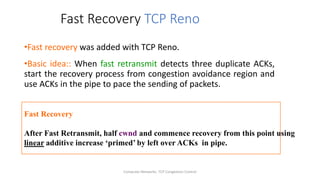
- Fast retransmit detects lost packets sooner by retransmitting on three duplicate ACKs, while fast recovery resumes data transfer using ACKs still in the pipe.