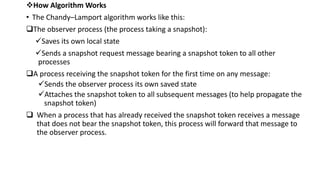
The document summarizes the Chandy-Lamport algorithm, which is used to record a consistent global state of an asynchronous distributed system. It works by having an observer process initiate a snapshot by saving its state and sending snapshot request messages bearing a token to other processes. Processes receiving the token for the first time save their state and attach the token to outgoing messages to propagate it. The observer receives states and messages to construct a consistent global snapshot.