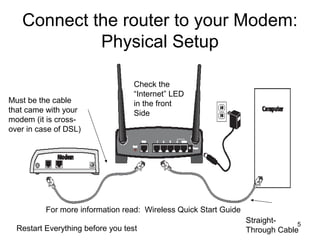
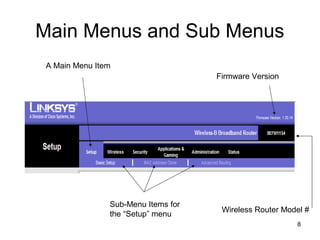
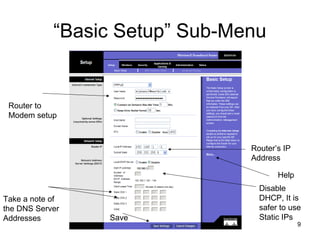
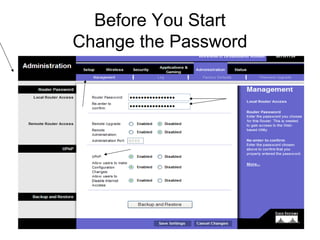
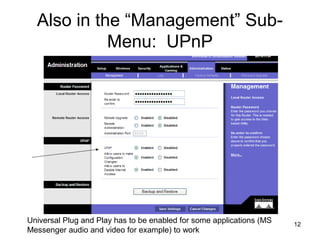
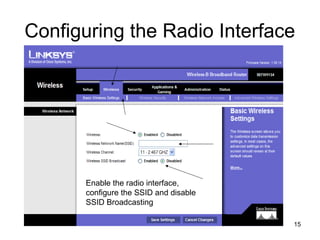
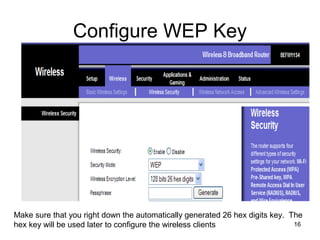
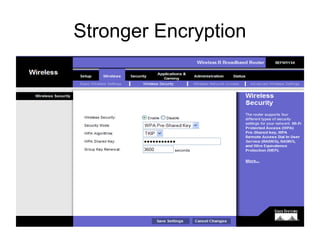
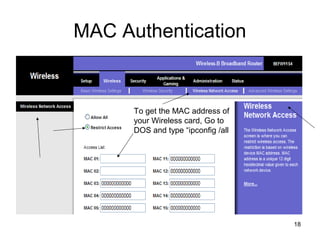
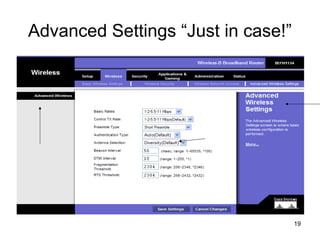
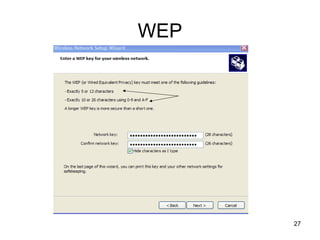
The document provides detailed instructions for configuring a Linksys wireless router, including physical connections, broadband modem interfacing, and various setup procedures. Key topics include updating firmware, configuring wireless settings such as SSID and security, and managing device settings for optimal performance. It also offers troubleshooting tips for Windows firewall and guidance on client configurations.