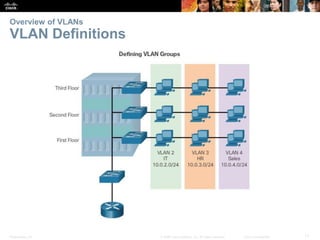
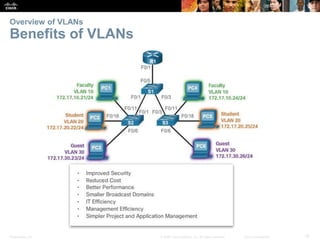
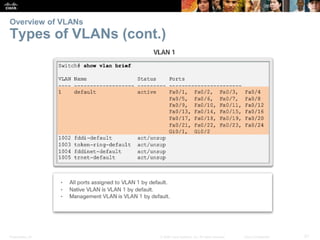
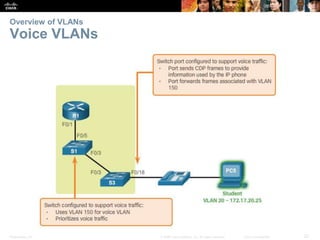
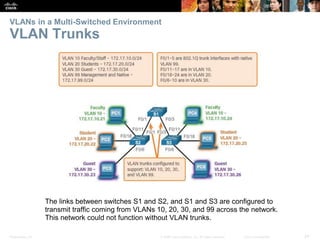
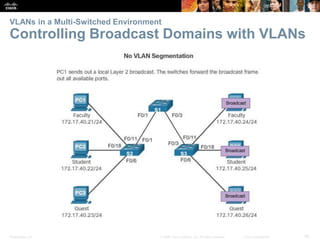
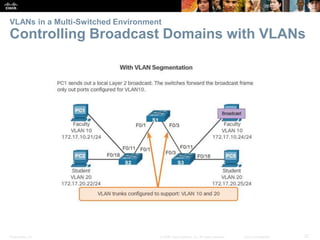
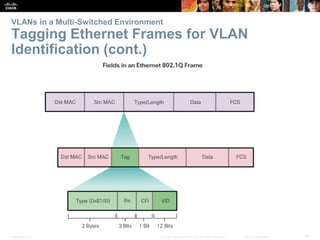
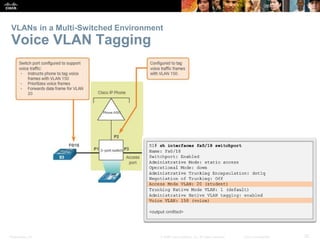
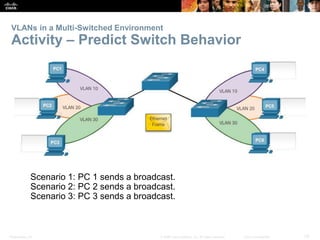
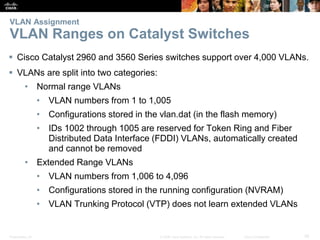
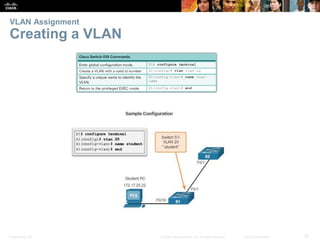
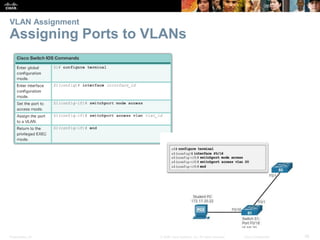
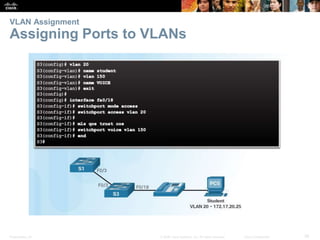
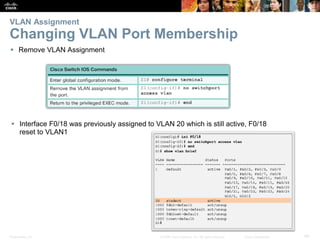
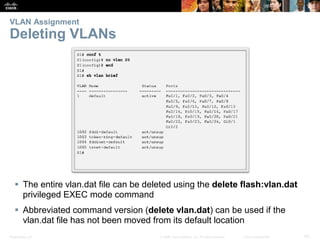
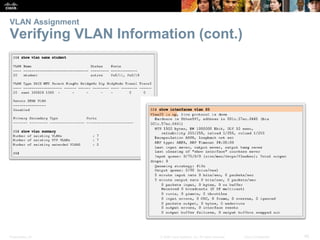
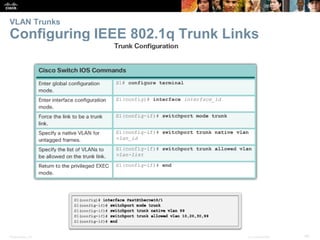
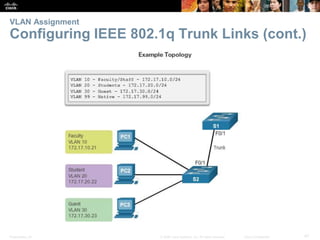
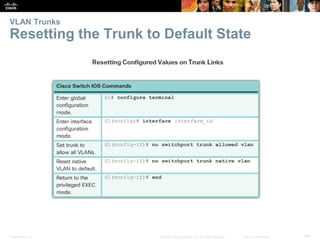
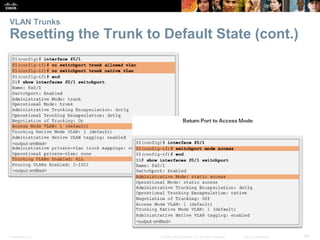
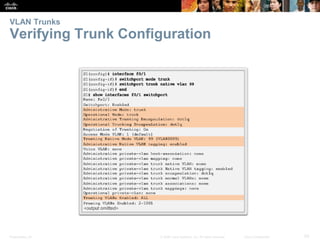
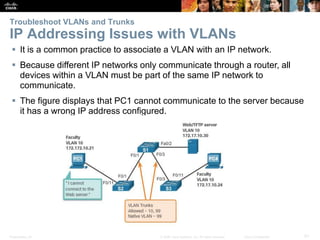
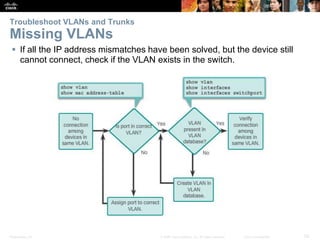
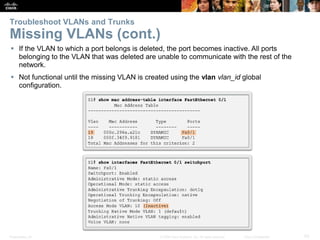
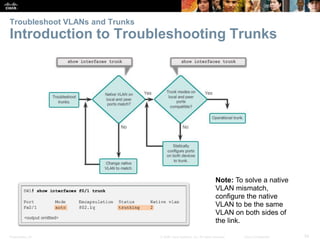
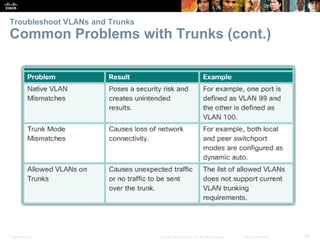
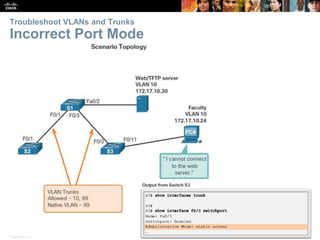
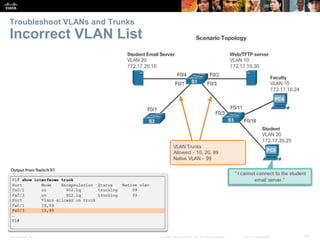
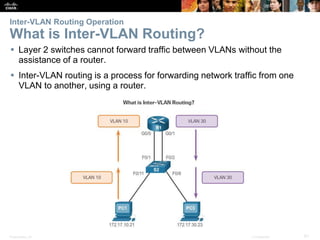
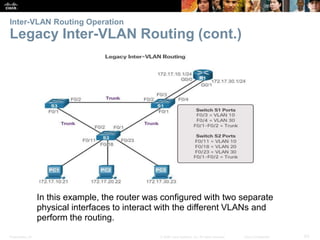
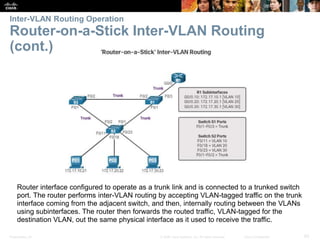
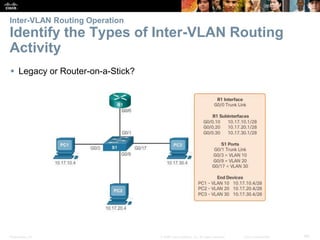
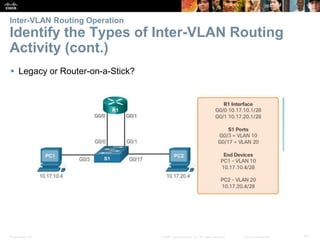
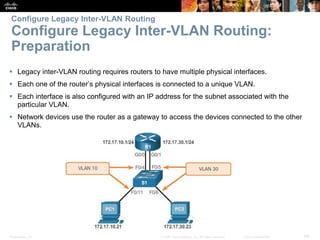
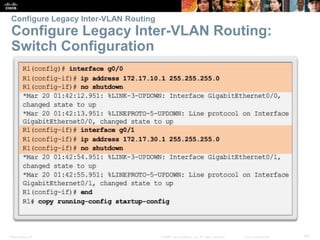
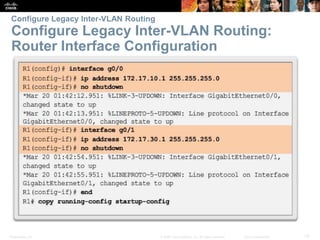
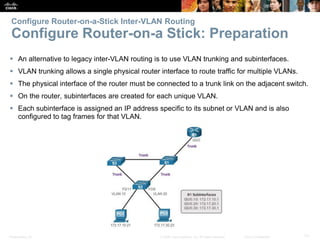
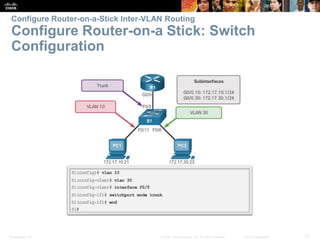
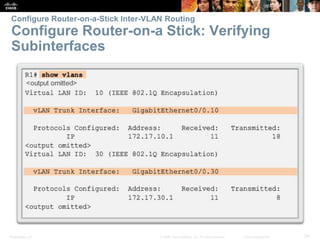
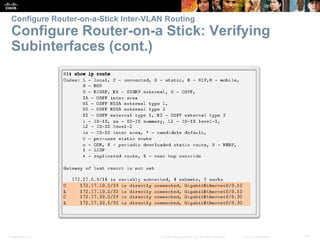
This document contains a chapter from a Cisco CCNA Routing and Switching course on VLANs. It begins with objectives for sections on VLAN segmentation, implementations, and inter-VLAN routing. It then provides explanations and examples of VLAN definitions and benefits, types of VLANs including voice VLANs, VLAN trunks, controlling broadcast domains with VLANs, tagging Ethernet frames for VLAN identification, native VLANs, and configuring VLAN assignments, trunk links, and verifying and deleting VLAN information.