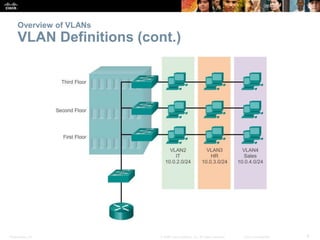
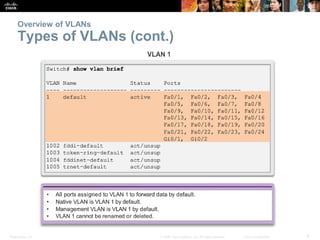
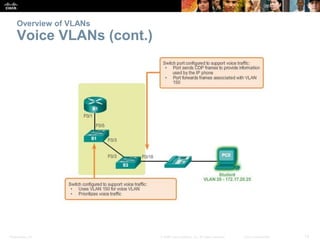
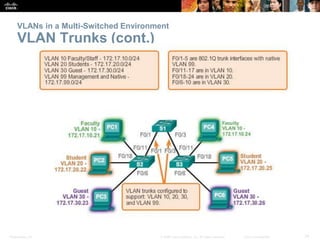
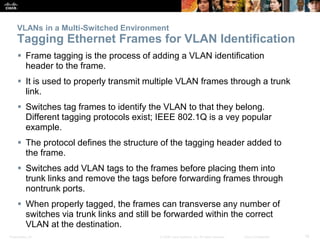
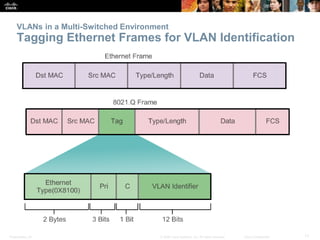
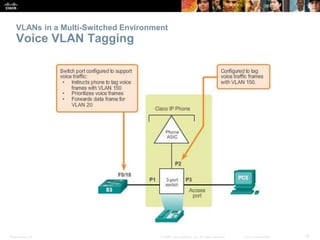
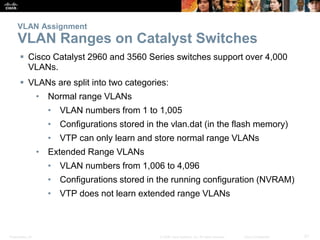
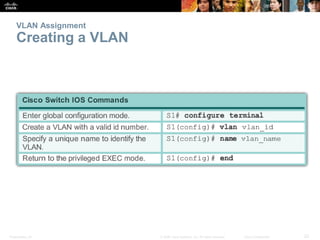
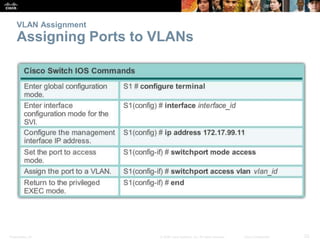
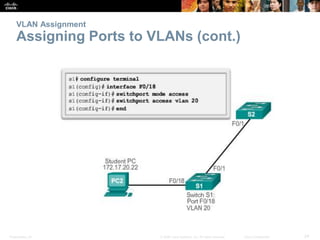
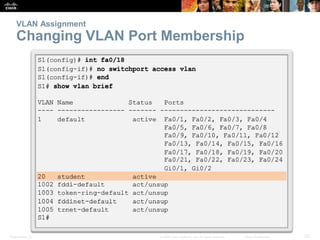
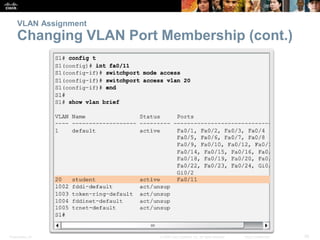
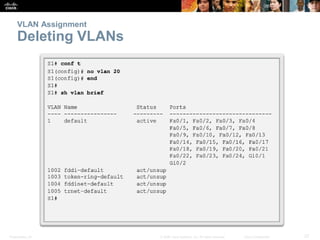
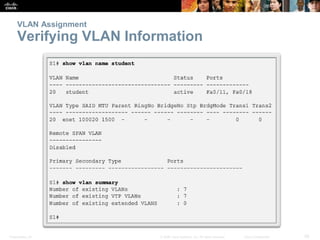
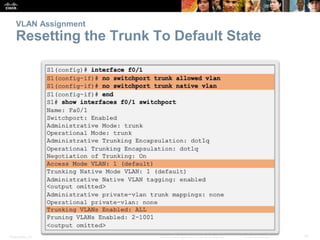
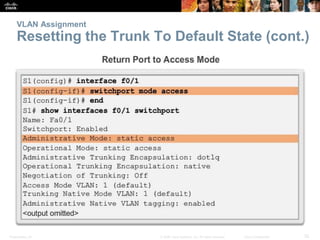
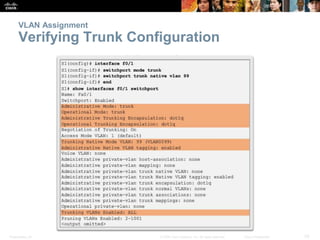
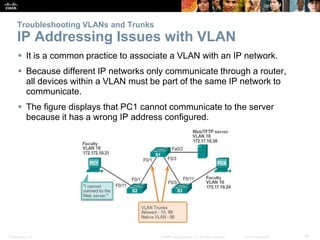
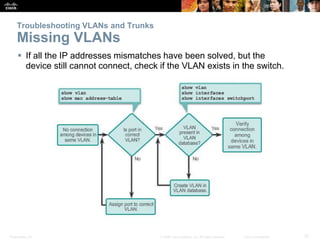
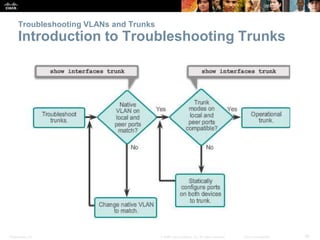
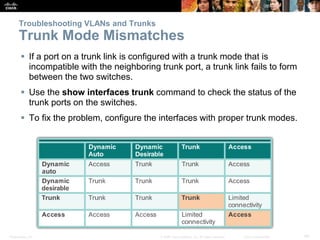
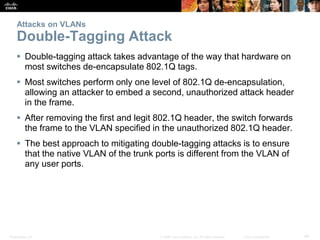
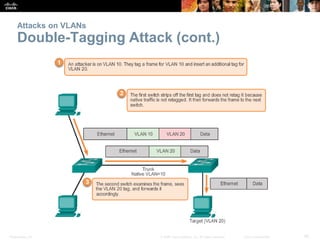
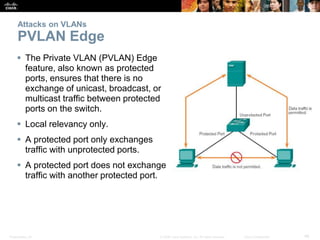
This document discusses VLANs and their implementation in Cisco switches. It covers VLAN segmentation and types of VLANs, how switches use 802.1Q tagging to identify VLAN traffic on trunk links between switches, and best practices for VLAN security and design including mitigating VLAN hopping and double-tagging attacks. Configuration topics include creating VLANs, assigning ports, configuring trunks, and troubleshooting. The objectives are to explain VLAN purposes, switch forwarding based on VLANs, and configure and secure VLAN environments.