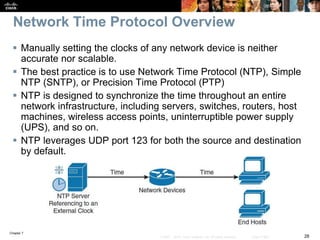
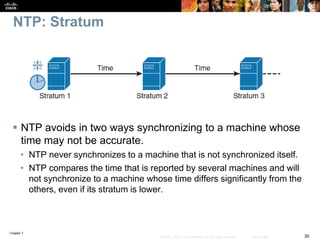
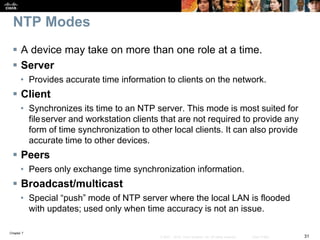
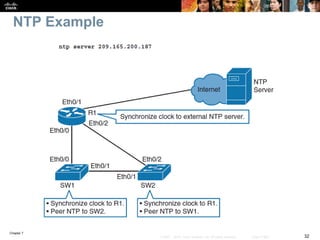
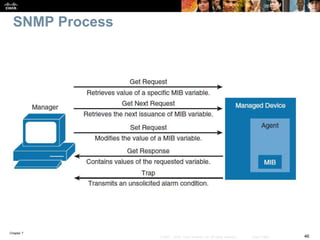
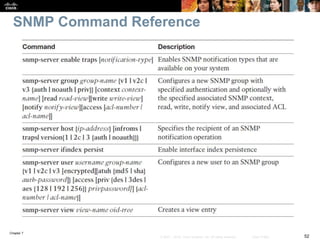
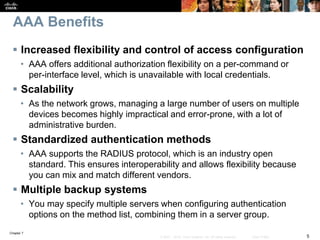
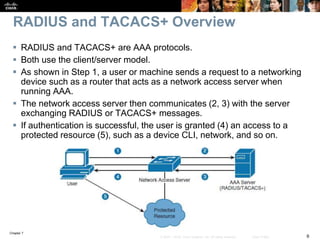
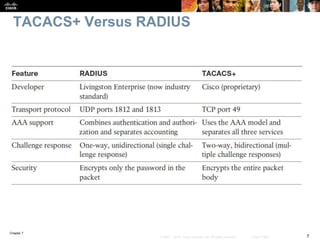
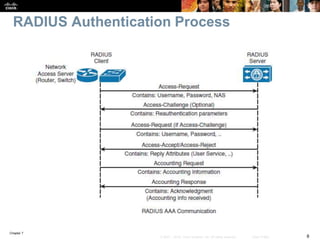
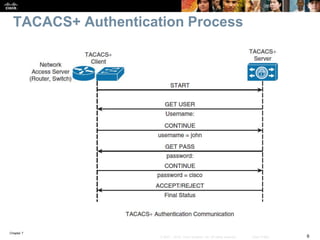
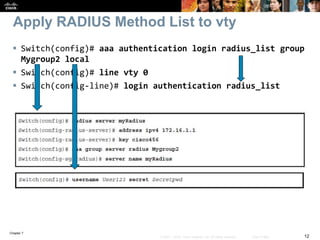
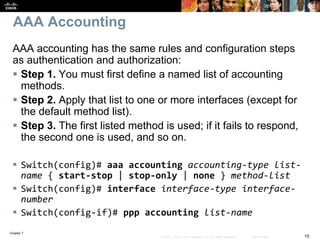
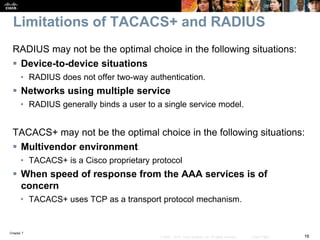
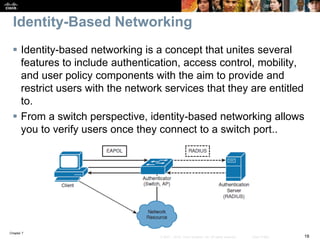
This chapter discusses network management topics including AAA (authentication, authorization, and accounting), 802.1X identity-based networking, NTP (Network Time Protocol), and SNMP (Simple Network Management Protocol). It provides details on configuring AAA using RADIUS and TACACS+ as well as 802.1X authentication. It also explains the need for accurate timekeeping via NTP and how to manually configure the system clock and implement daylight saving time adjustments.





![Chapter 7
11© 2007 – 2016, Cisco Systems, Inc. All rights reserved. Cisco Public
Configuring RADIUS Access
Switch(config)# radius server configuration-name
Switch(config-radius-server)# address ipv4 hostname [auth-
port integer ] [ acct-port integer]
Switch(config-radius-server)# key string
Switch(config)# aaa group server radius group-name
Switch(config-sg-radius)# server name configuration-name](https://image.slidesharecdn.com/switchv7ch07-180212080846/85/CCNP-Switching-Chapter-7-11-320.jpg)







![Chapter 7
26© 2007 – 2016, Cisco Systems, Inc. All rights reserved. Cisco Public
Setting Summer Time
clock summer-time zone recurring [ week day
month hh:mm week day month hh:mm [offset]]
clock summer-time zone date date month year
hh:mm date month year hh:mm [ offset ]
clock summer-time zone date month date year
hh:mm month date year hh:mm [ offset ]](https://image.slidesharecdn.com/switchv7ch07-180212080846/85/CCNP-Switching-Chapter-7-26-320.jpg)