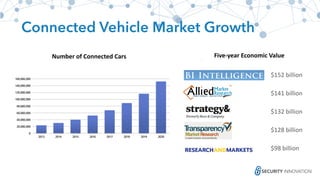
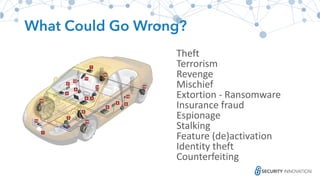
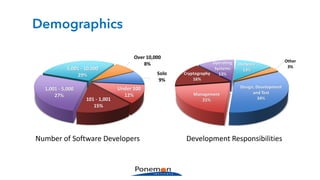
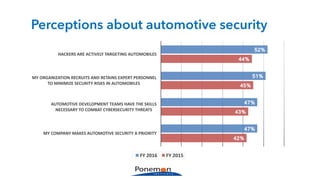
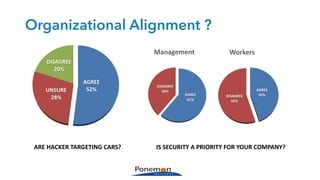
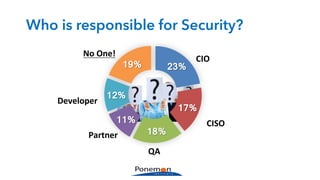
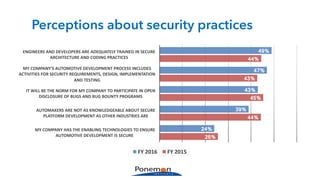
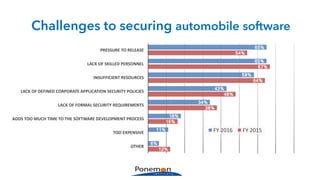
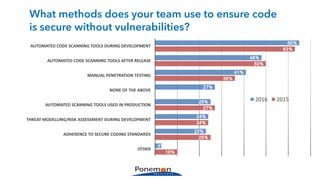
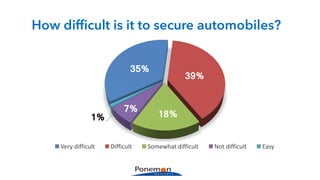
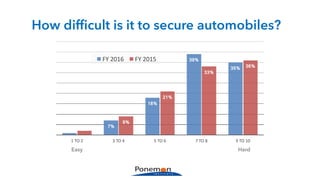
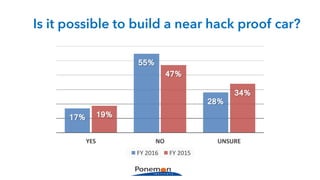
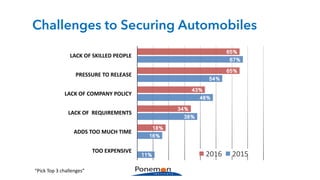
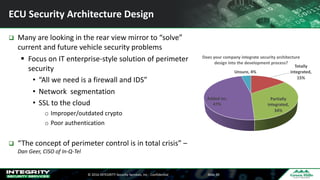
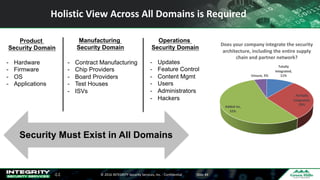
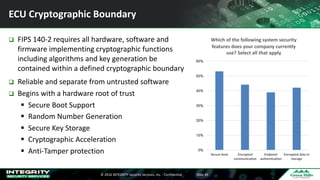
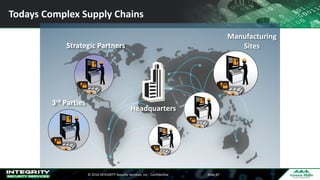
The Ponemon Institute's survey highlights significant gaps in automotive cybersecurity, revealing that many developers and executives are concerned about hacking threats but face challenges such as lack of skilled personnel and outdated technology. The study indicates that automakers feel less knowledgeable about secure software development compared to other industries, and there is no clear point of responsibility for cybersecurity. Despite these issues, there are signs of a maturing approach to security within the automotive sector.