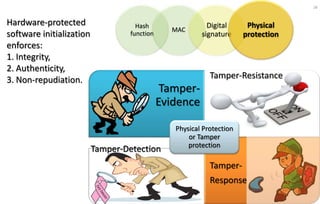
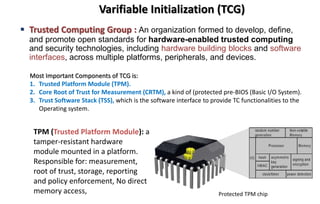
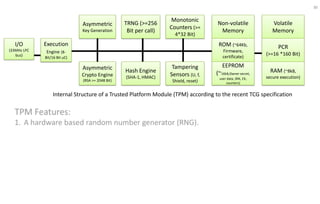
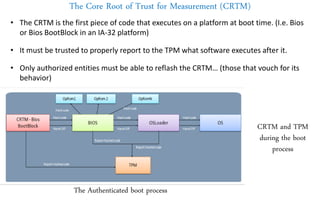
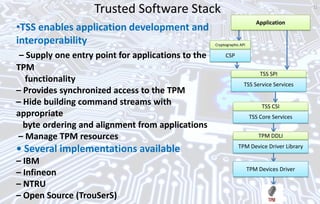
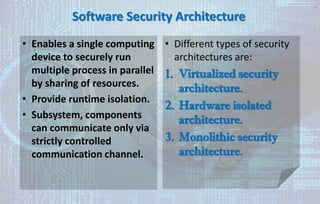
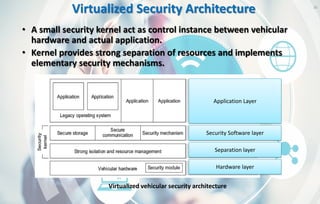
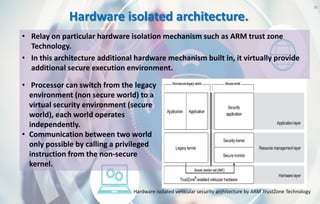
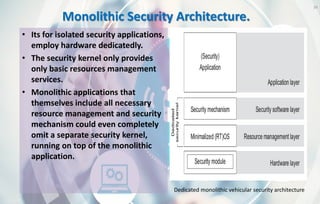
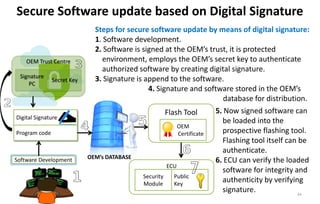
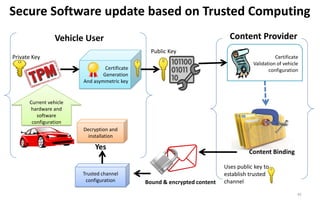
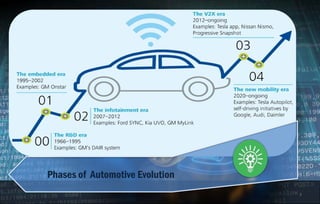
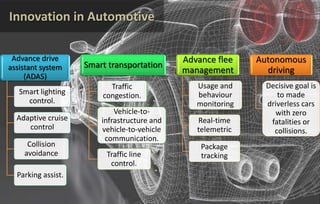
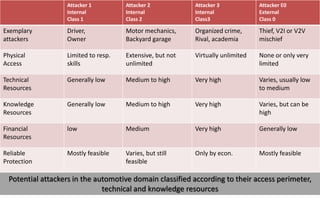
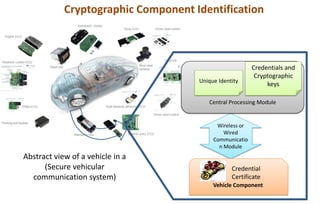
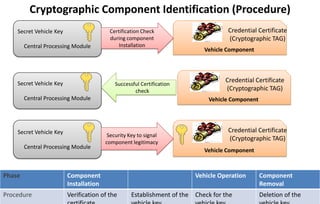
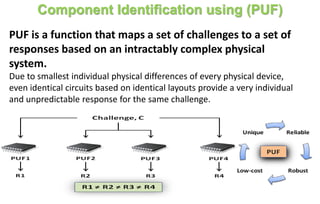
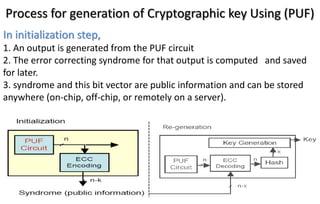
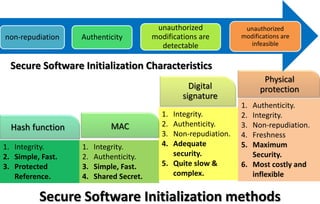
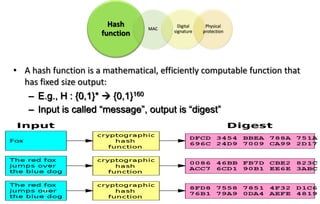
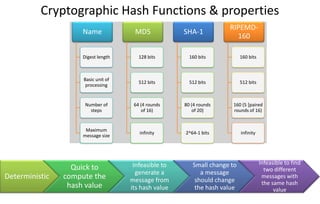
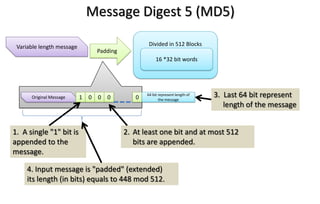
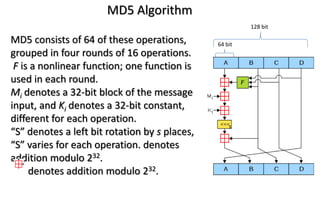
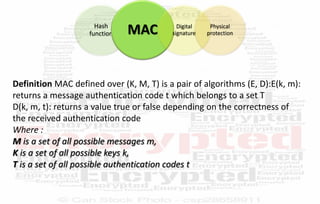
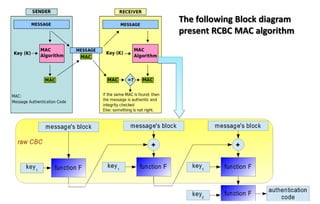
This document discusses automotive cyber security. It begins by outlining the evolution of automotive technology and the increased connectivity of modern vehicles. This connectivity introduces new security challenges as vehicles can be attacked remotely by hackers. The document then classifies different types of attackers and attacks, including logical and physical attacks. It discusses methods for secure component identification using cryptography and physically unclonable functions. The document also covers secure software initialization, updates, and architectures. Finally, it discusses secure vehicular communication.





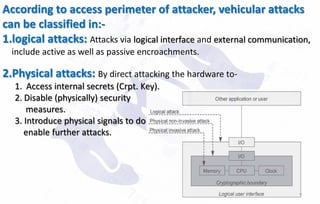
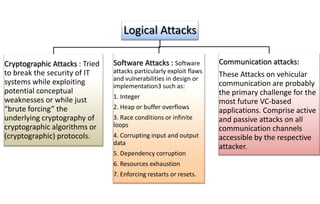
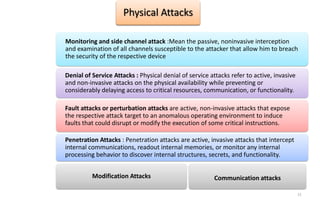
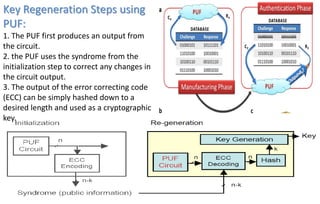
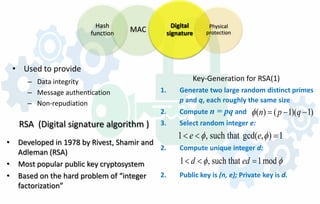
![Alice p=5 q=7 n = 35
φ(n) = 4*6=24
e = 5; d: ed = 5d =1 mod 24 ;
=> d = 5
Public key: (n=35, e=5)
Private key: d=5
M = [0, n-1] For all m Є M
R(m)=m m = 26; R(m) = 26
s = 265 mod 35 = 31
message
Signing
algorithm
message signature
Signer’s private key
Unsecured channel
Signer
Signature
verification
algorithm
Signer’s public key
Verifier
Ok / not Ok](https://image.slidesharecdn.com/cybersecurityppt-190814034501/85/Cyber-securityppt-27-320.jpg)