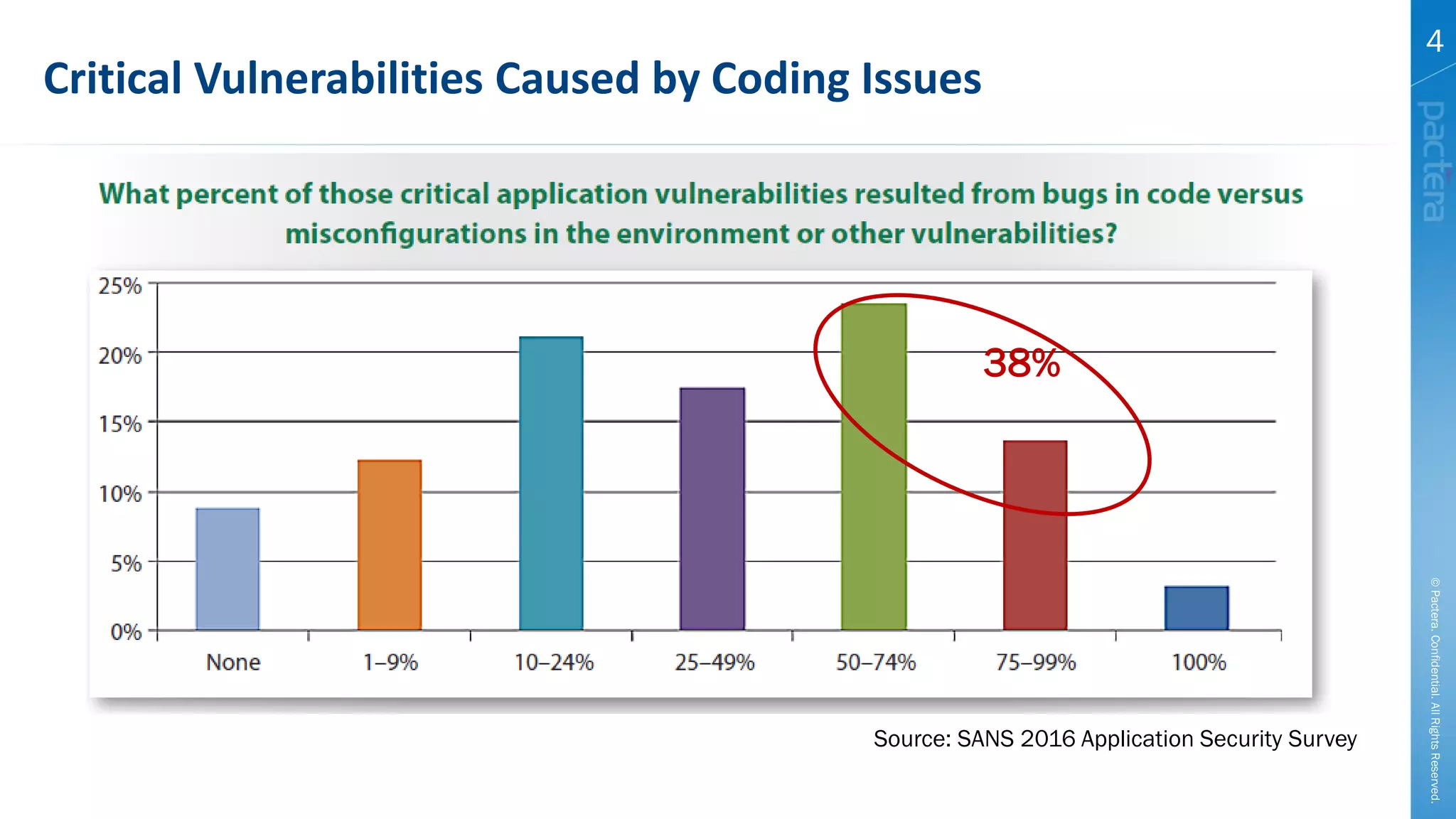
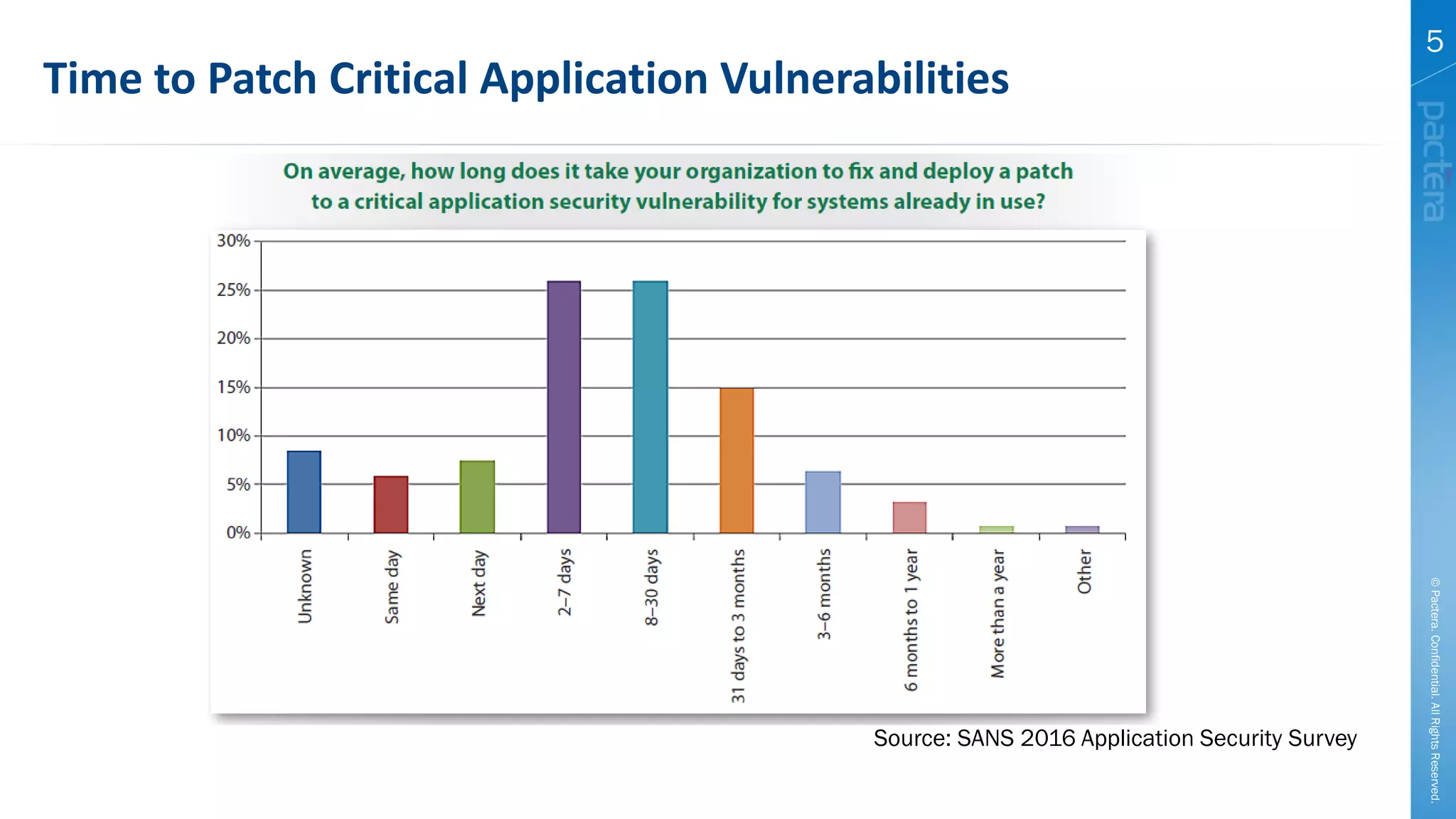
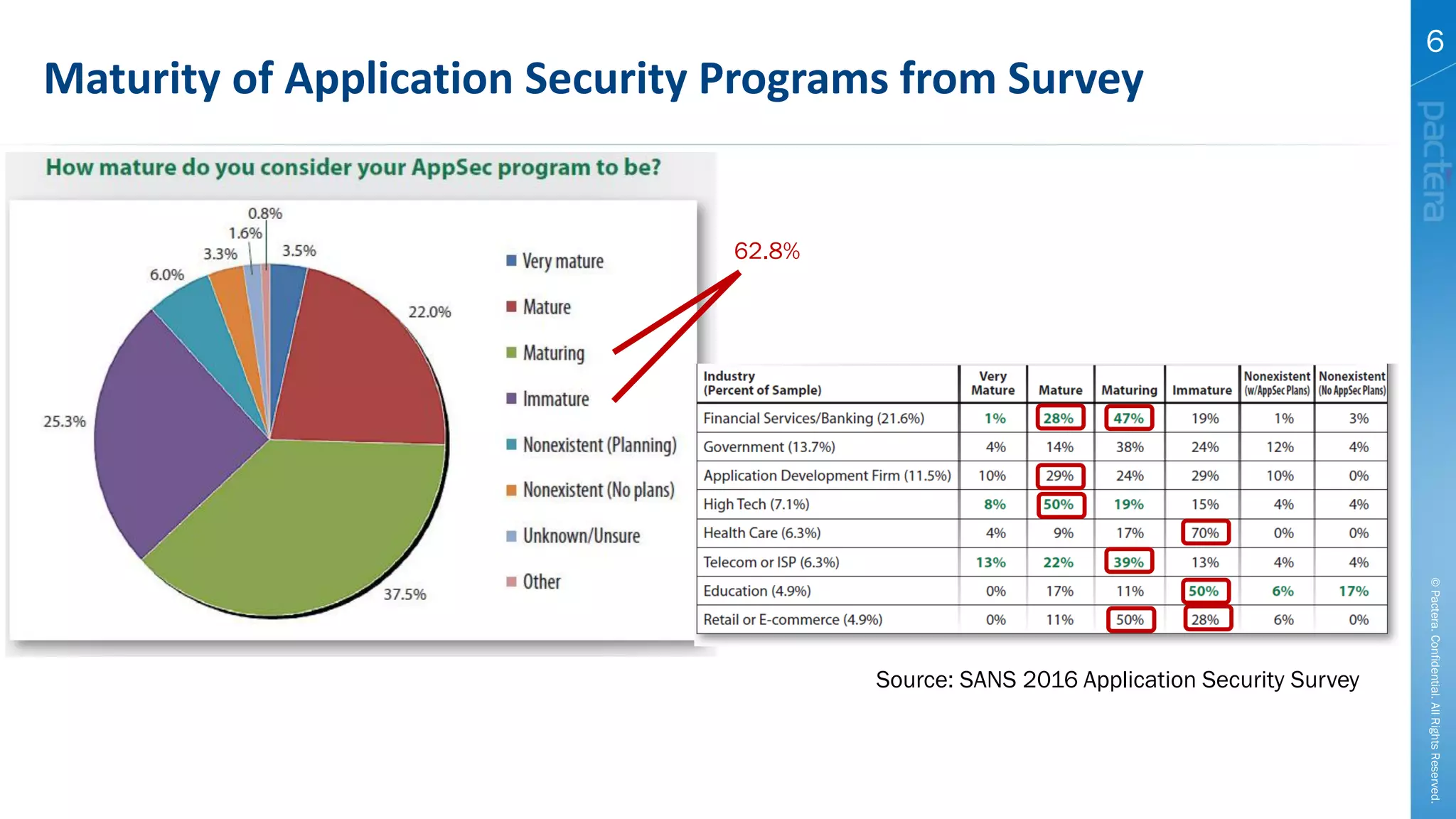
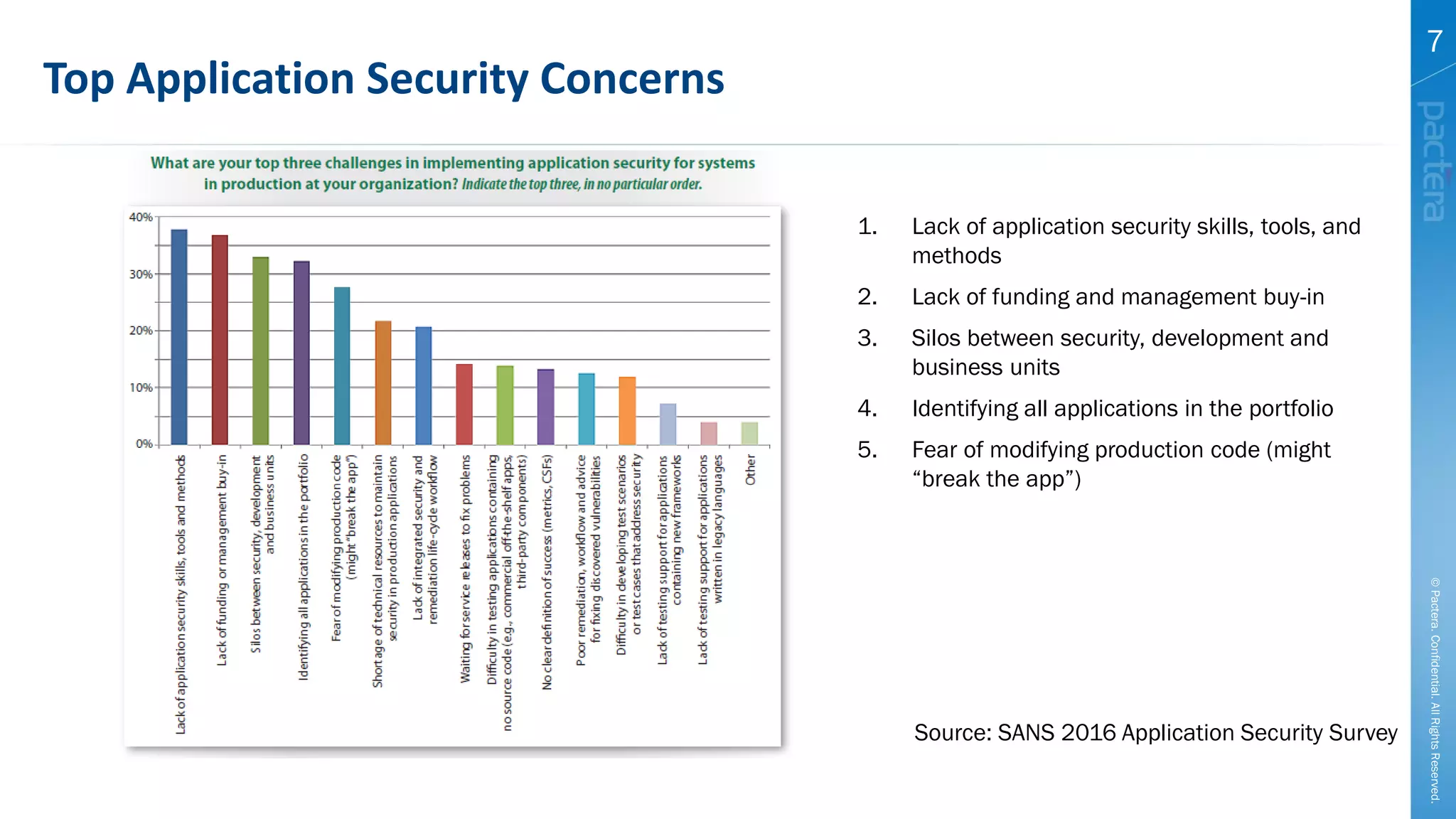
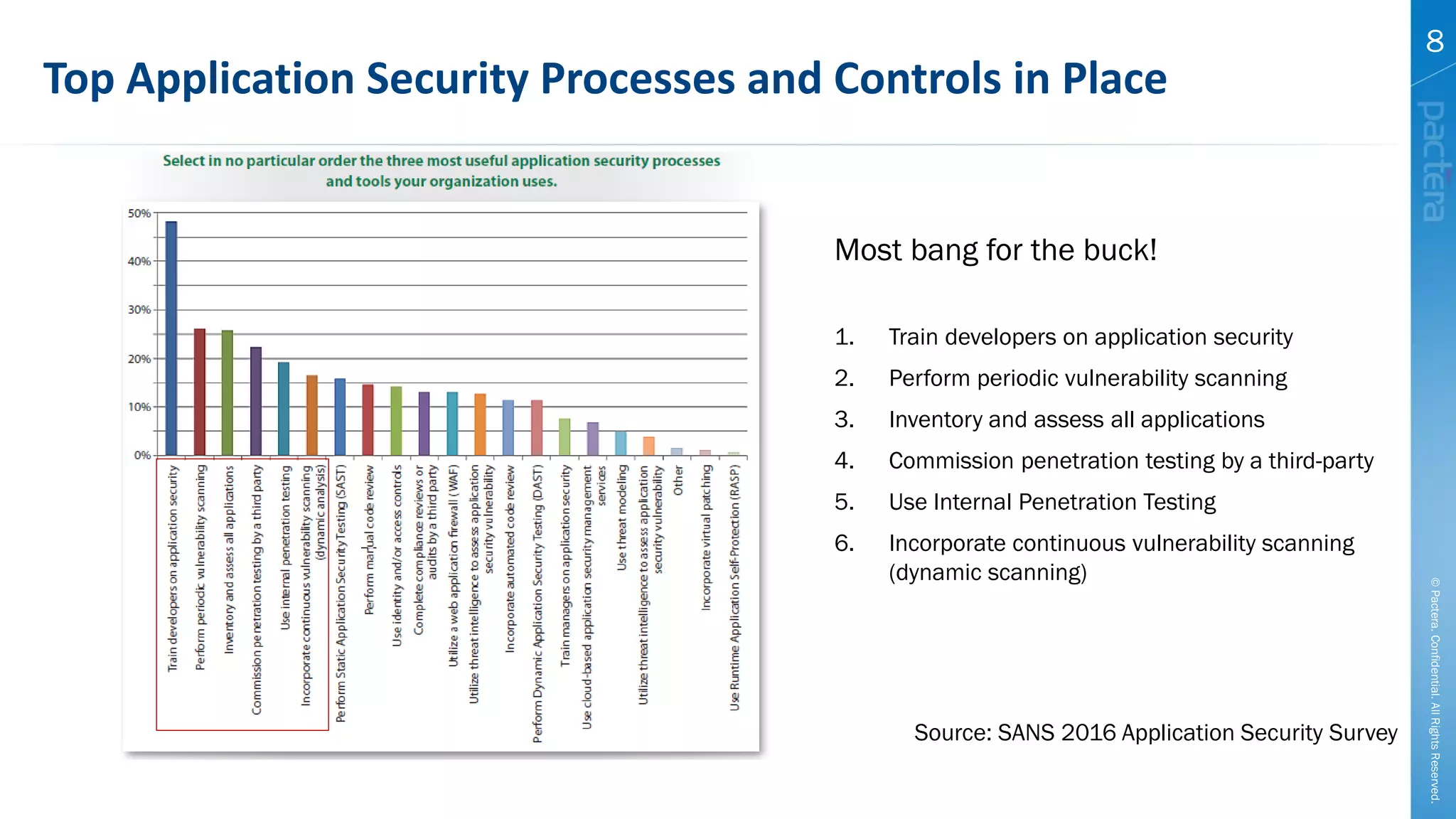
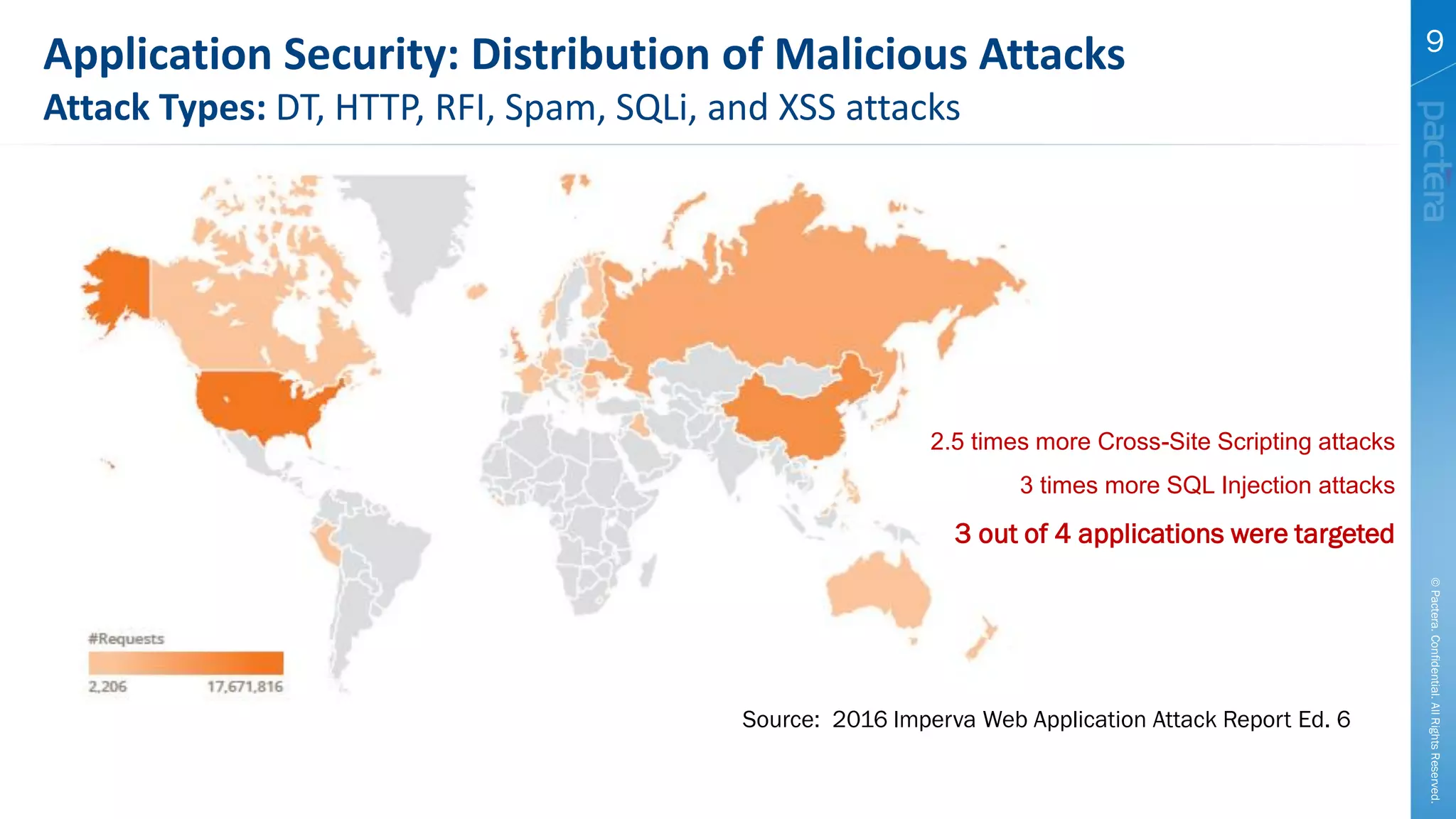
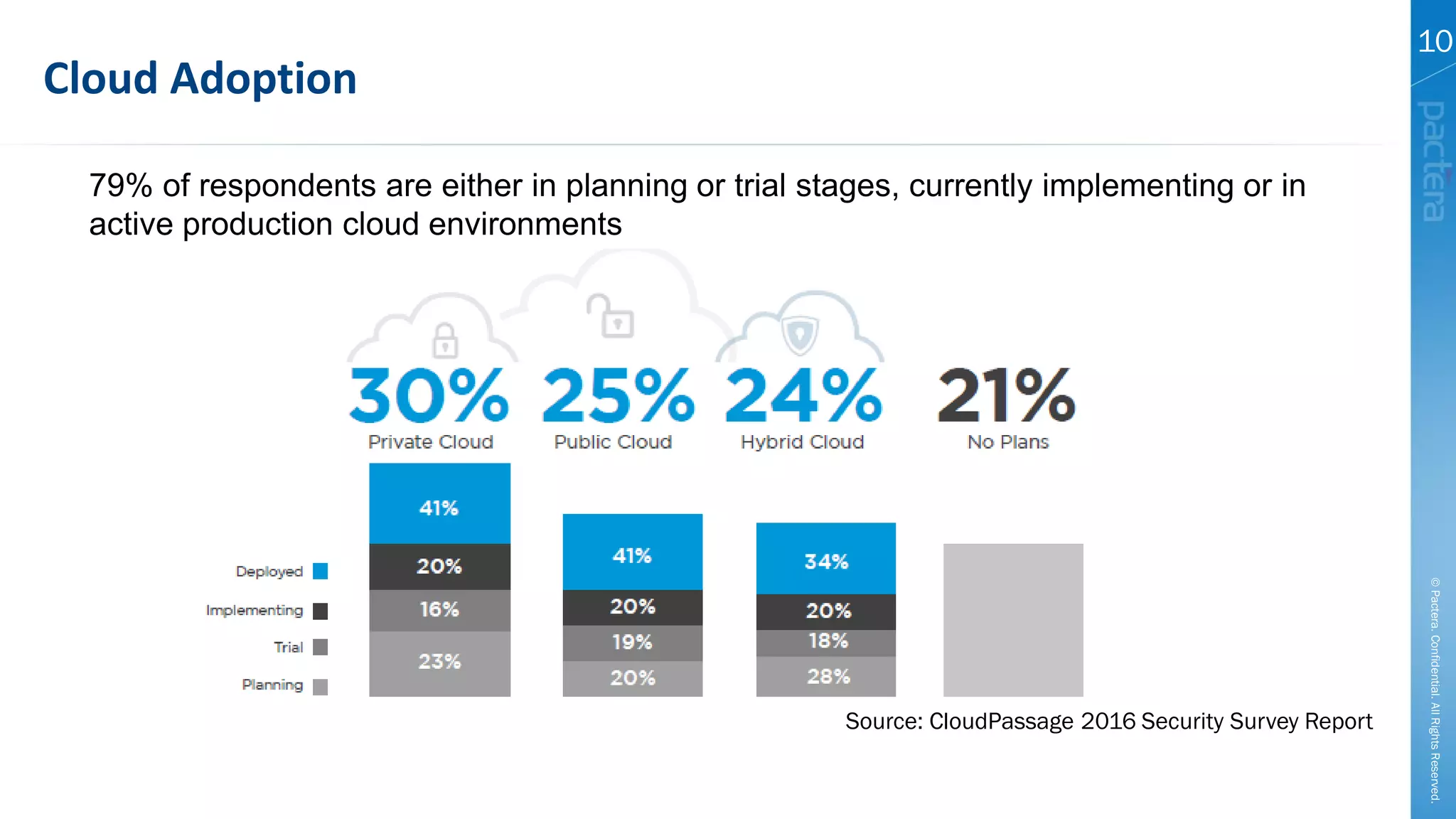
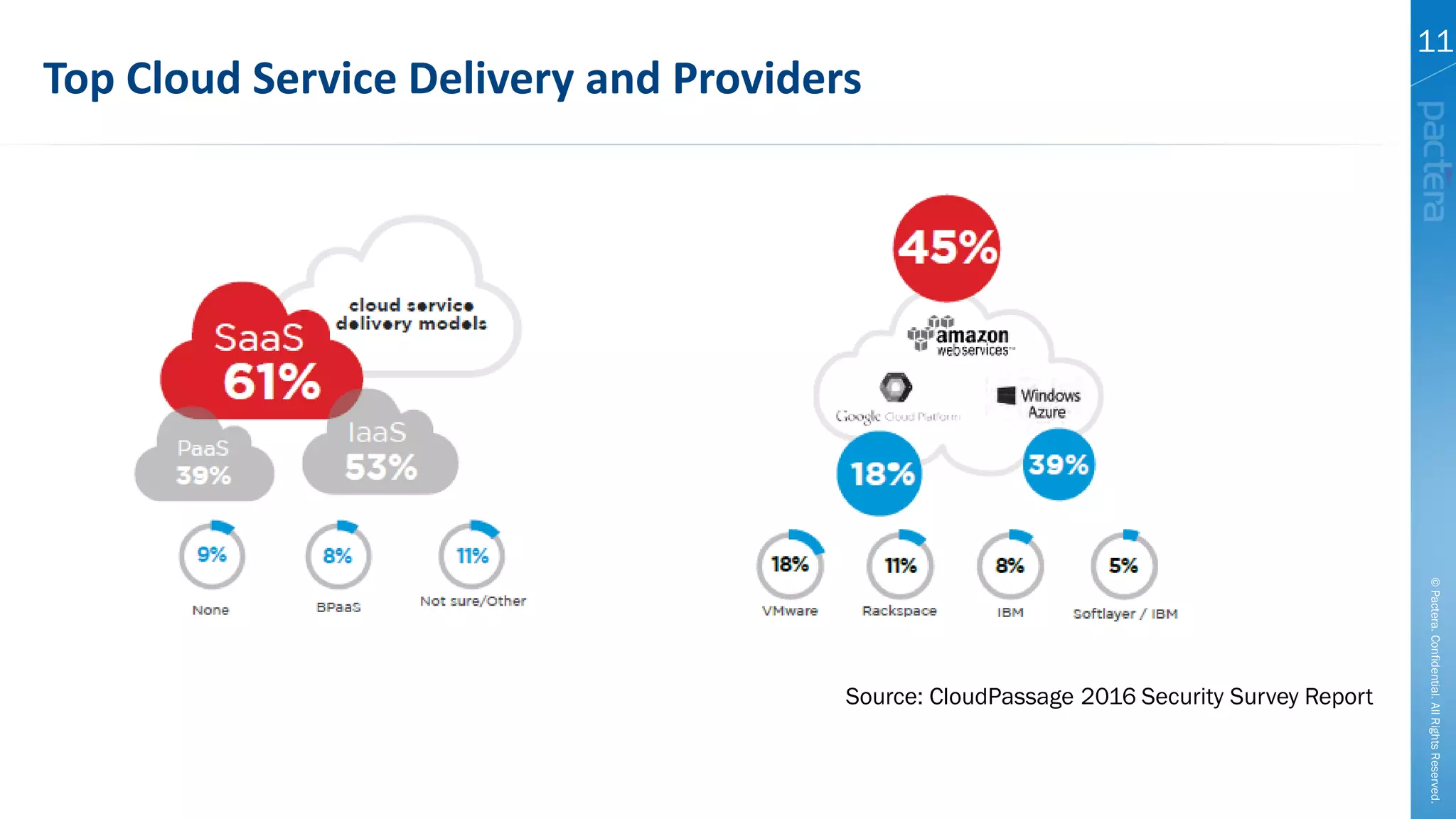
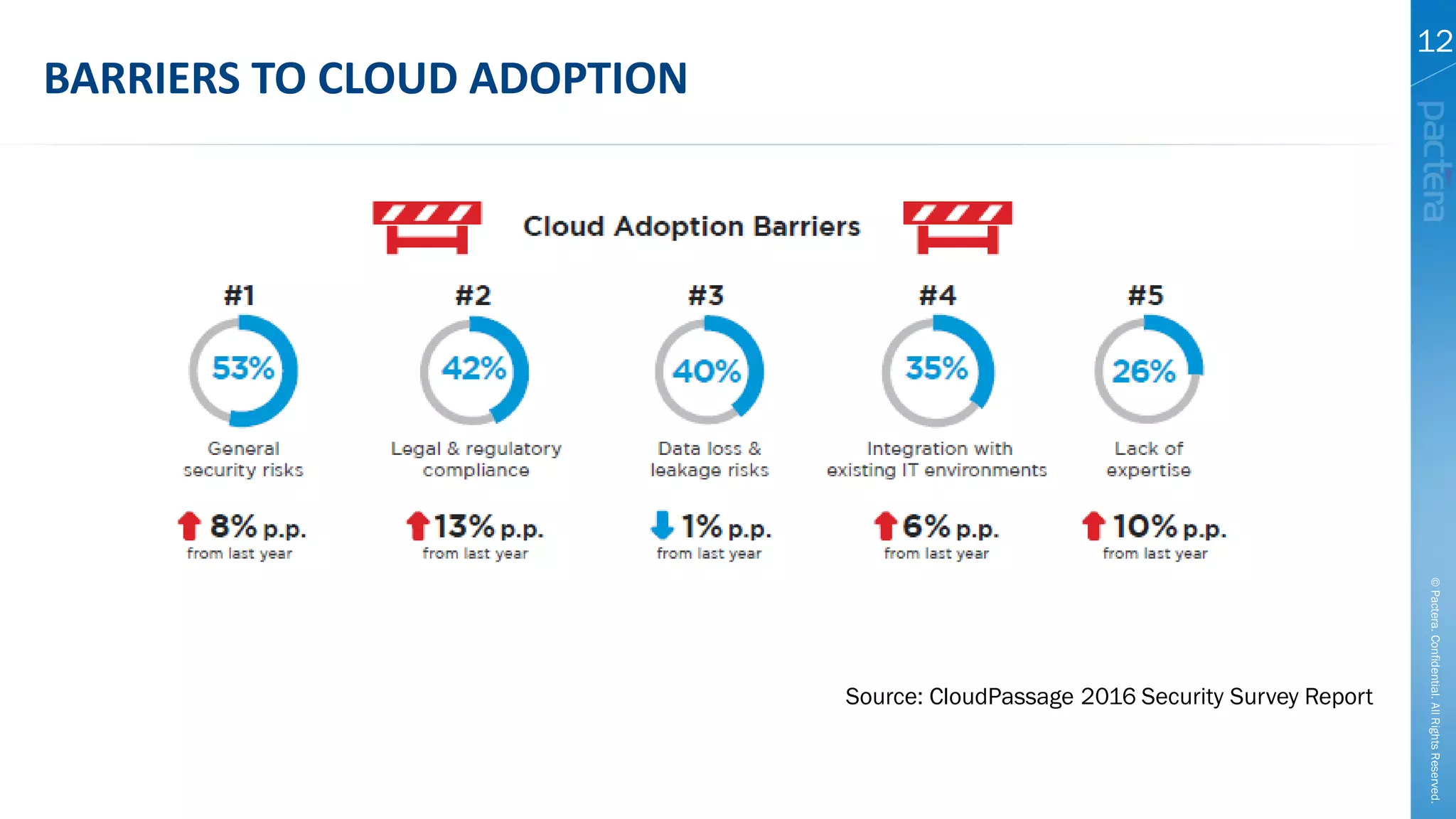
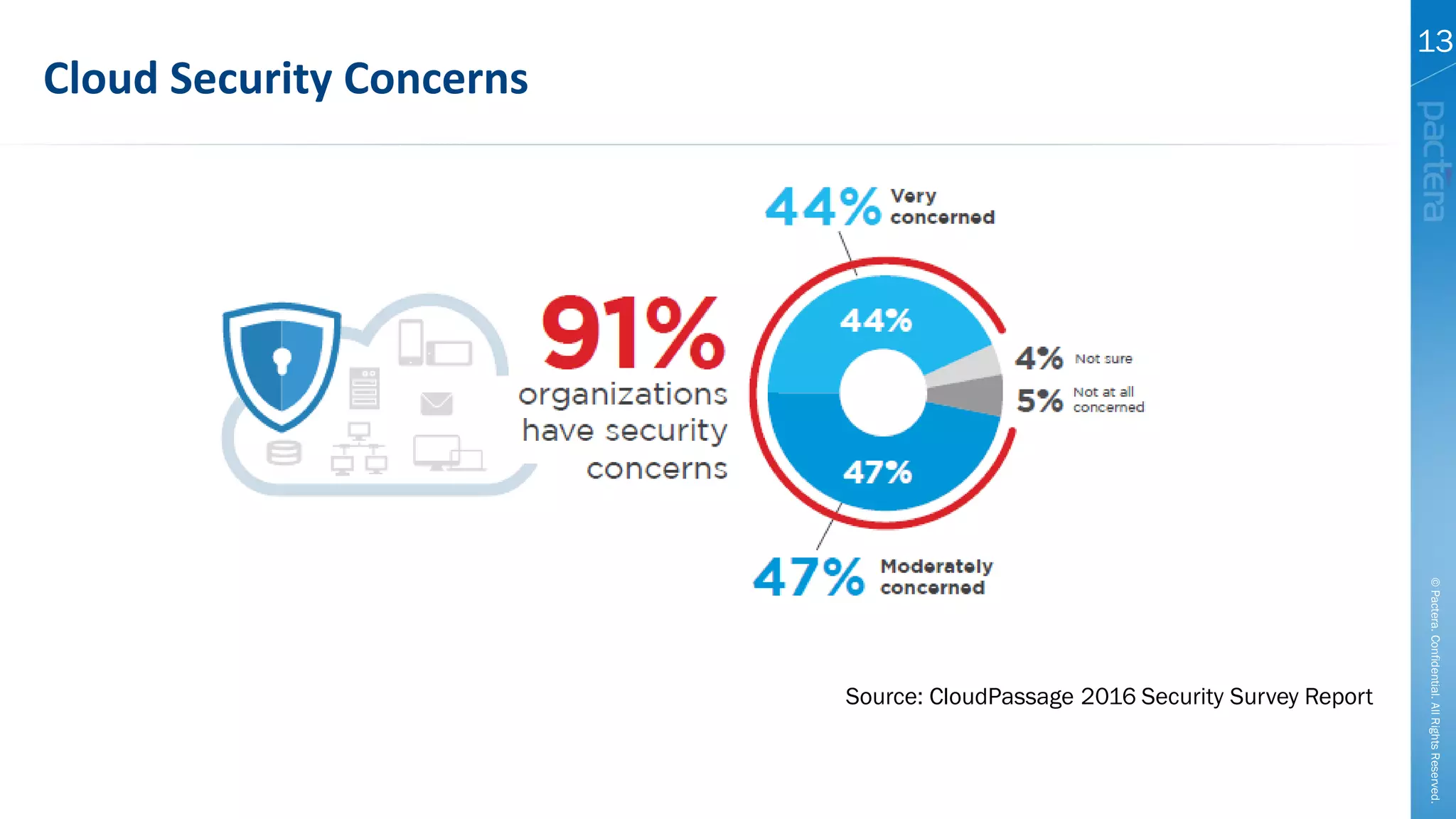
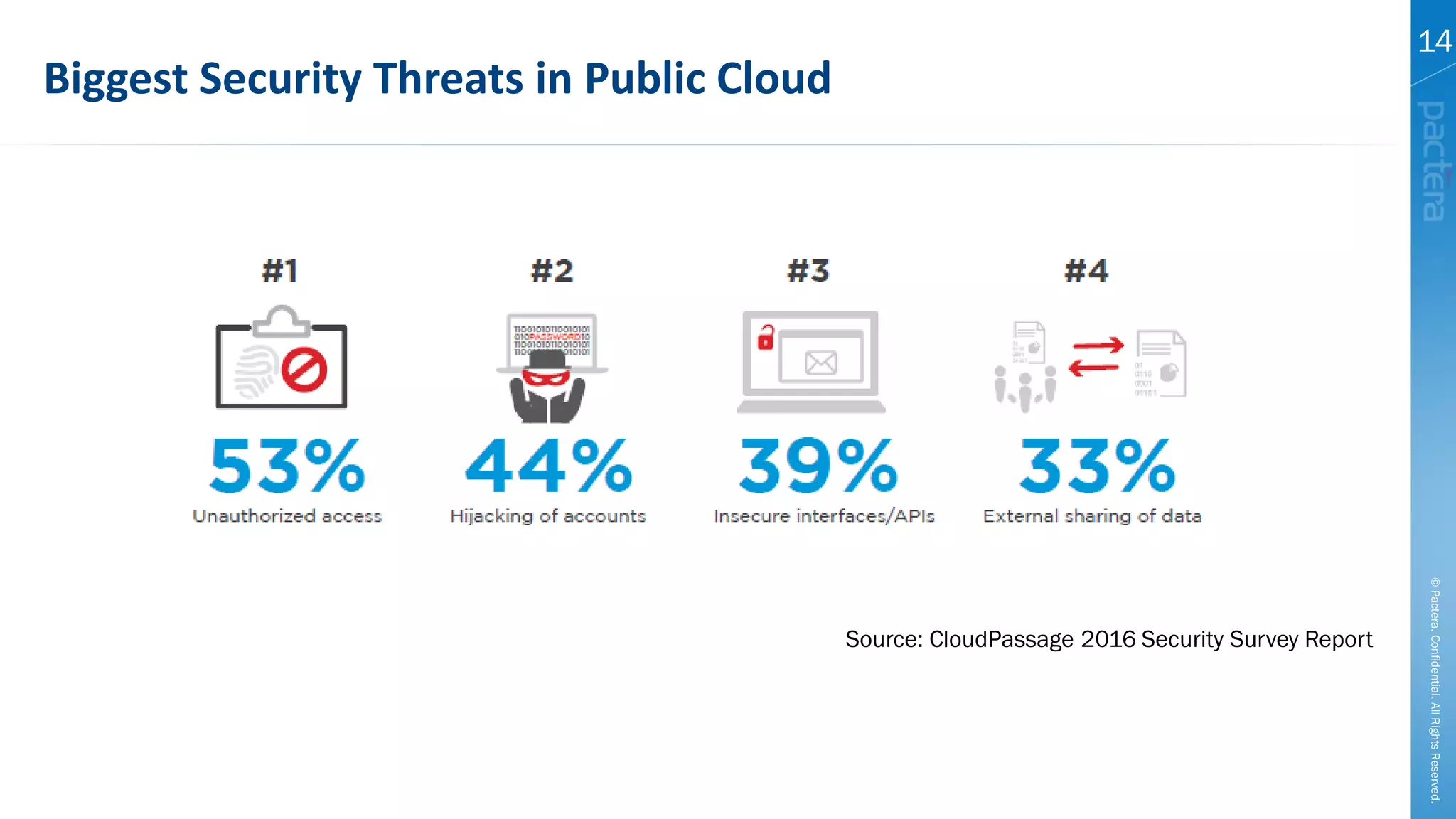
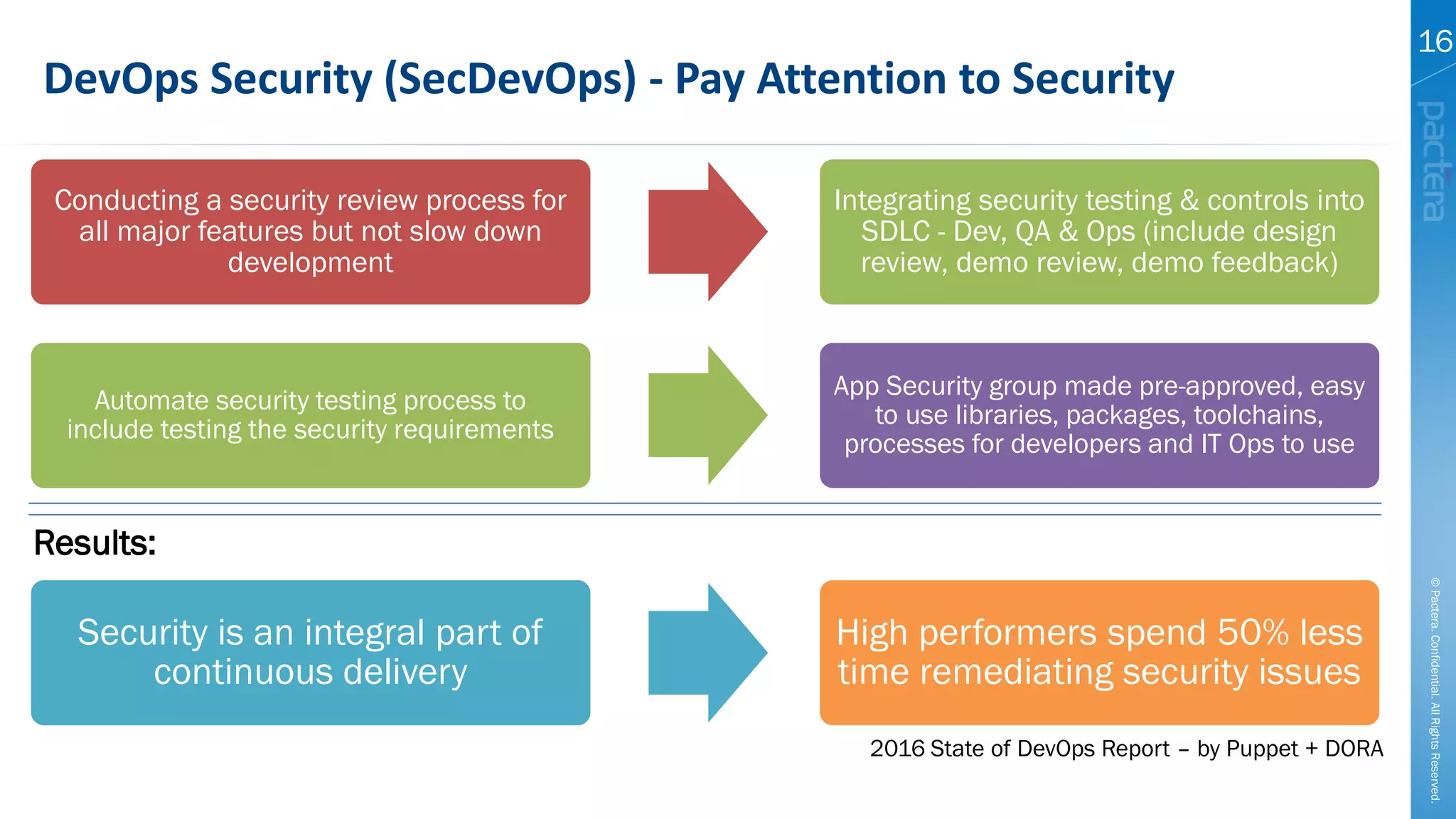
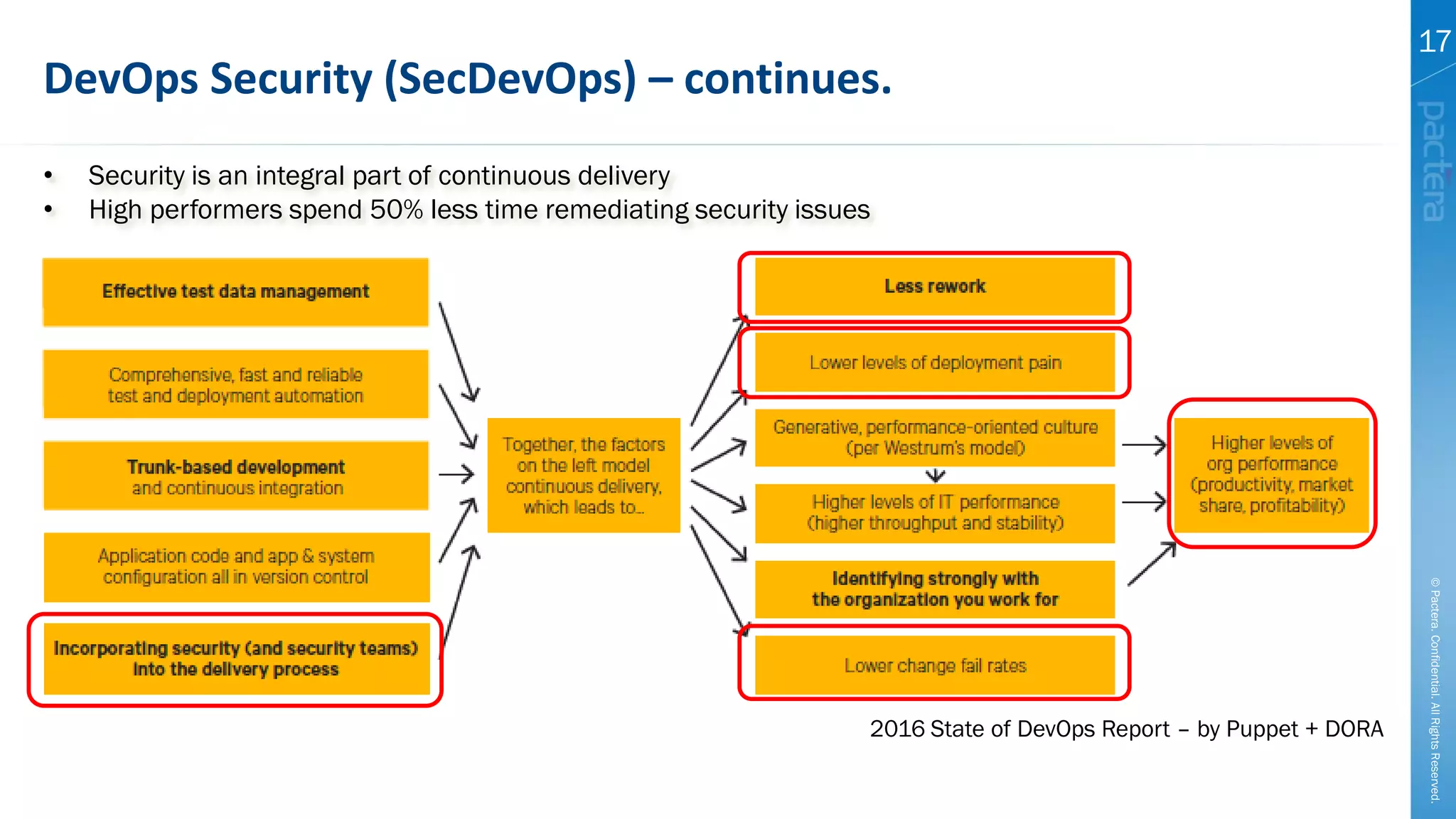
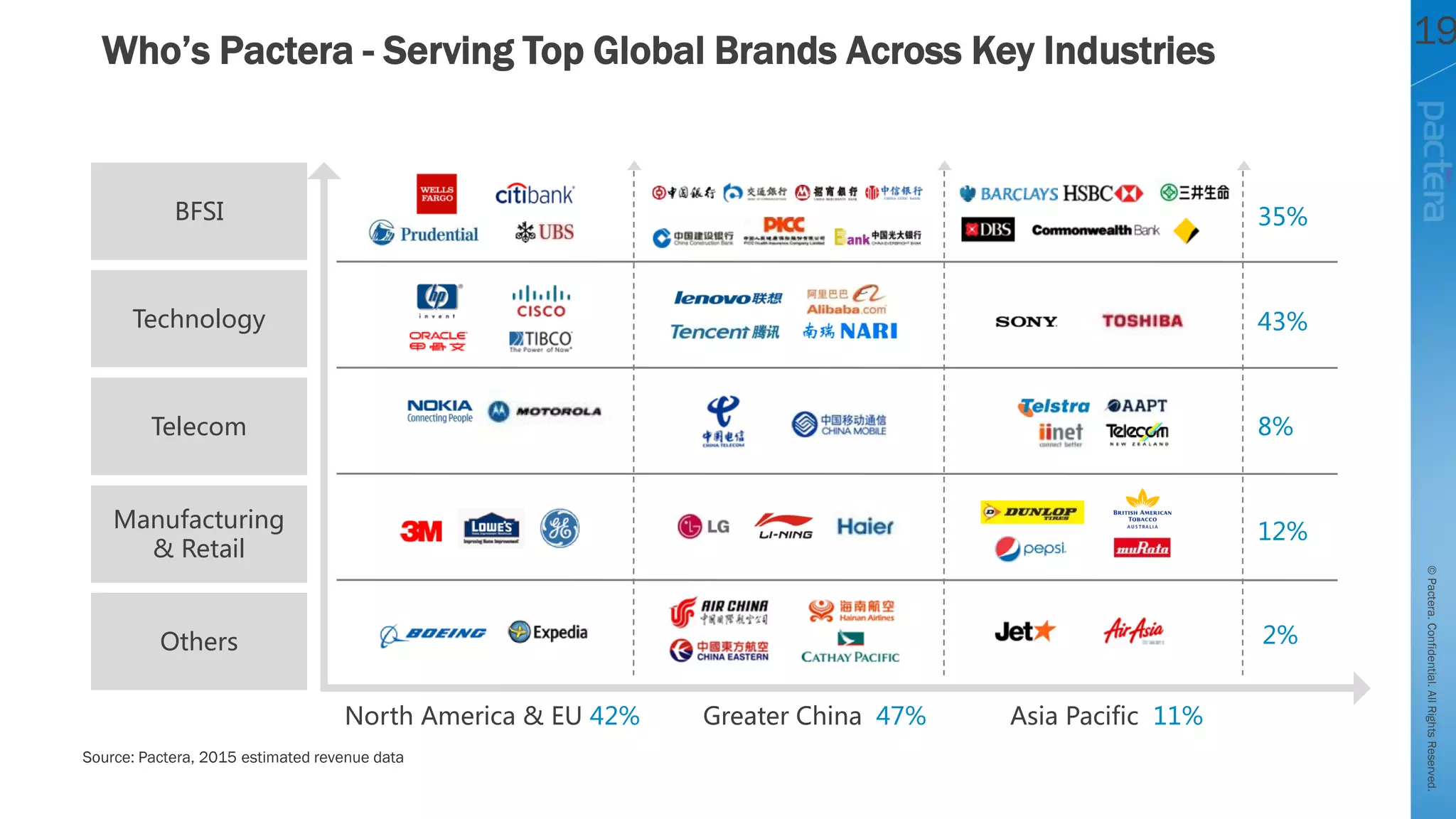
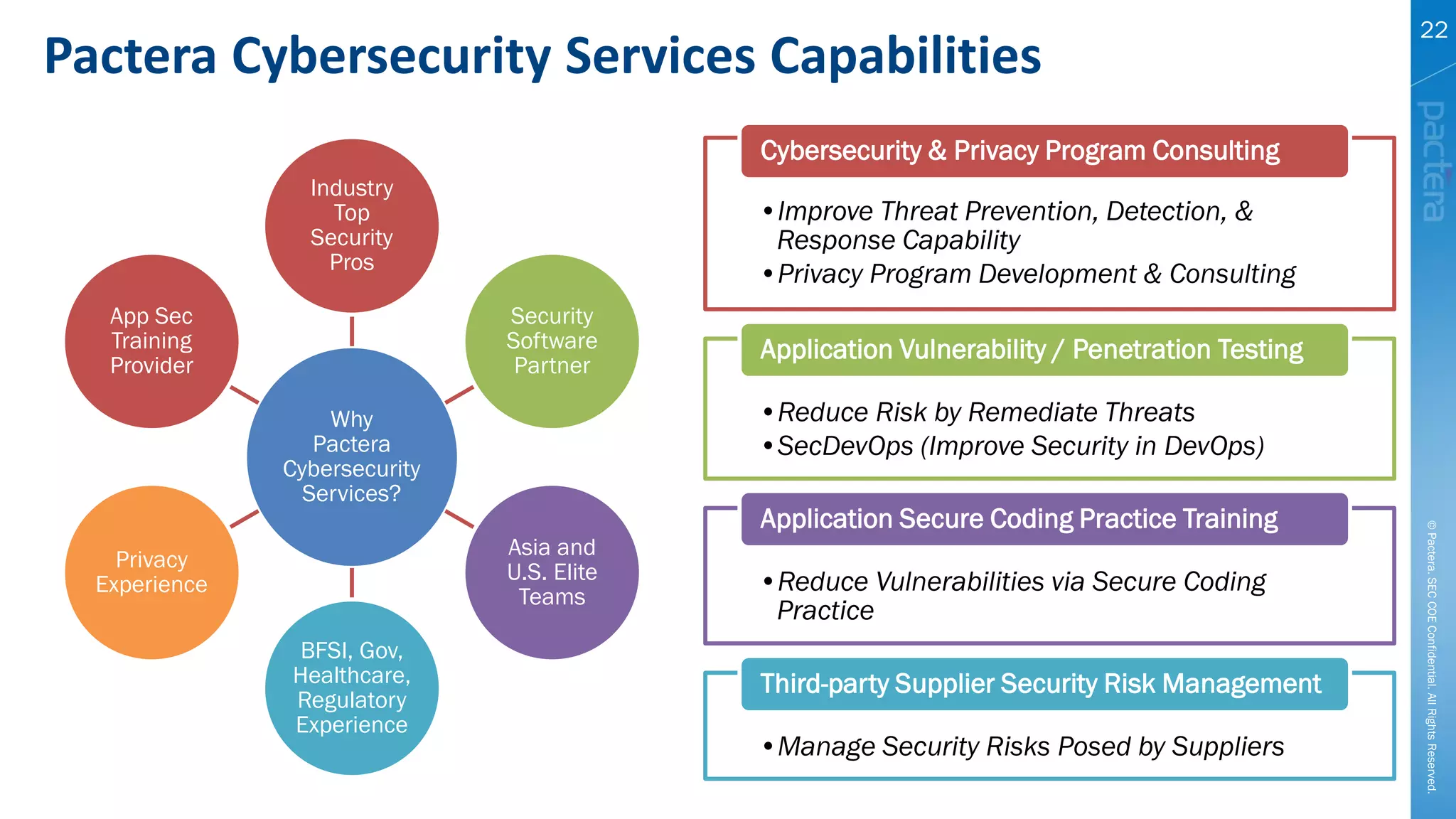
This document summarizes cybersecurity trends from surveys conducted in 2016. It finds that 38% of organizations have a maturing application security program, while 41% cited public-facing web applications as the leading cause of breaches. Regarding cloud security, 79% of respondents are implementing or using cloud environments actively, with infrastructure as a service being the most popular service. The document also introduces Pactera's cybersecurity services capabilities, which include application security testing, secure development training, and third-party risk management.