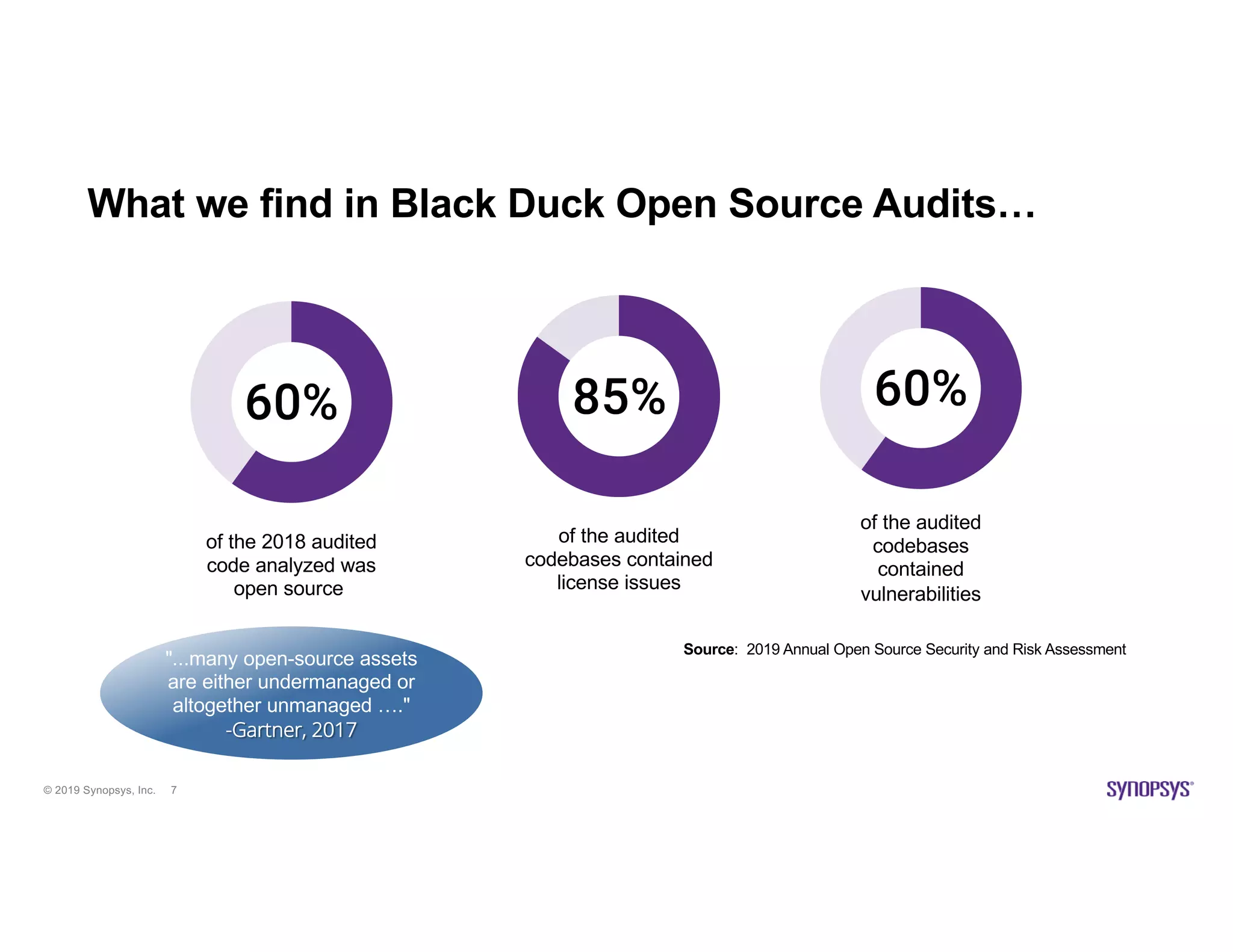
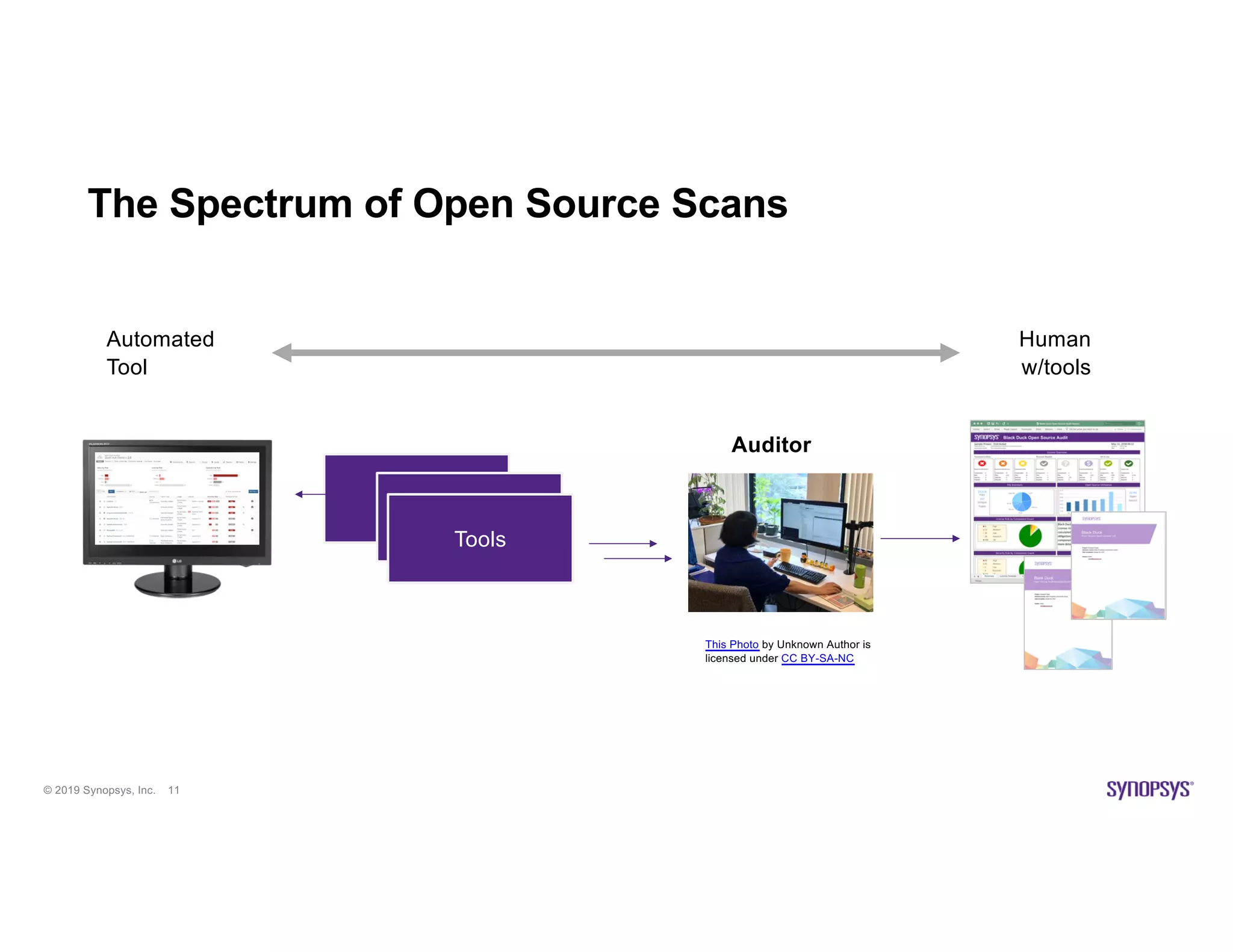
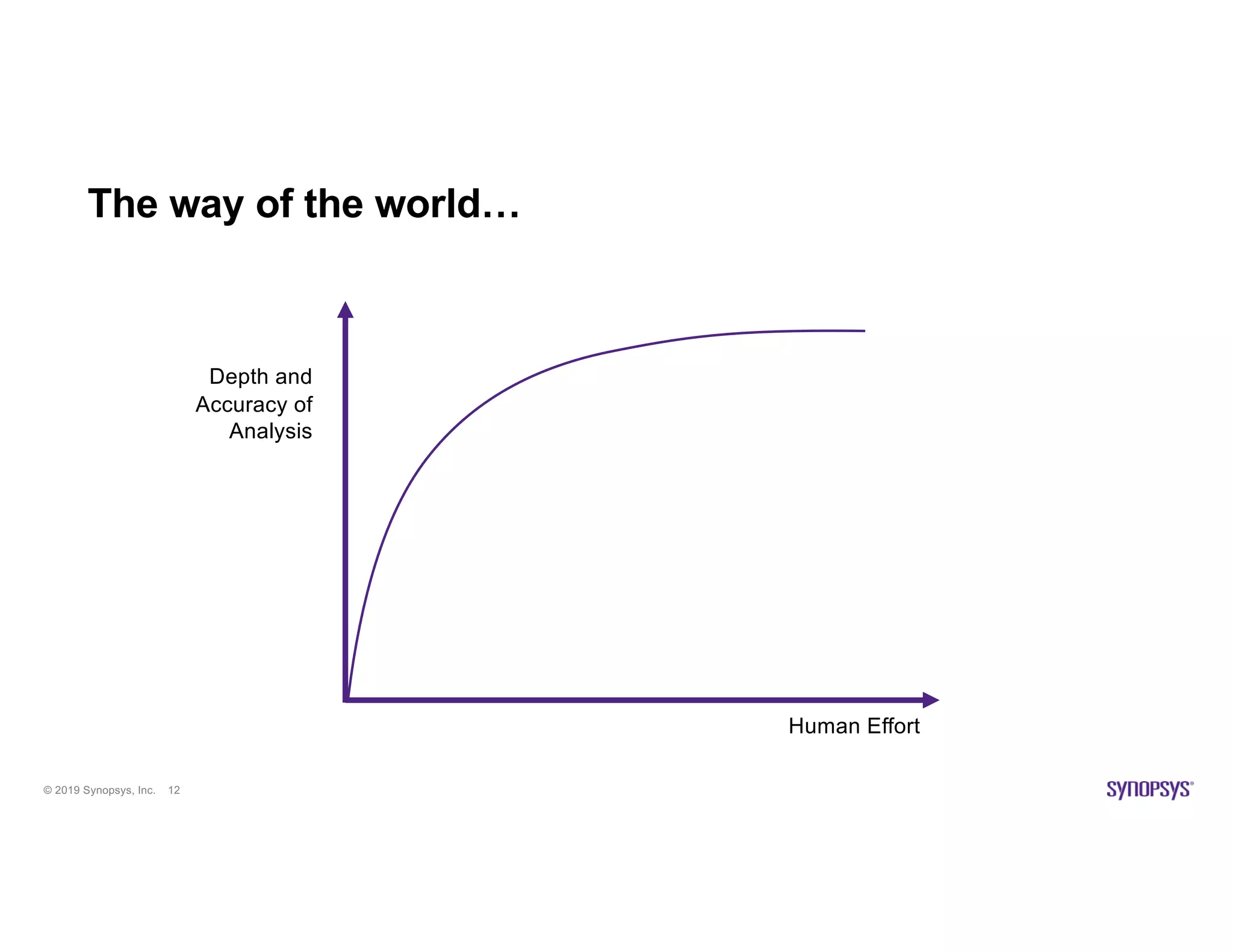
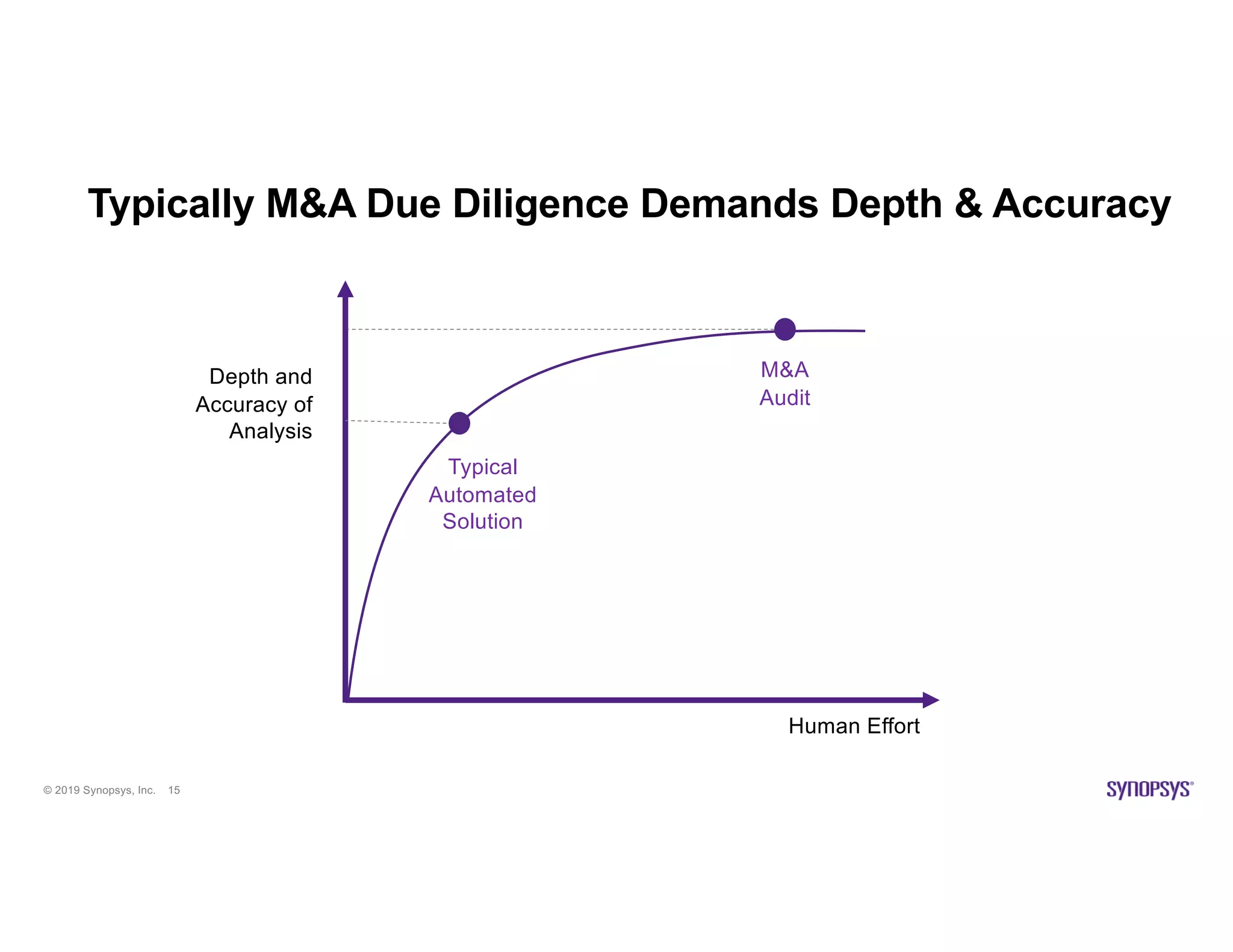
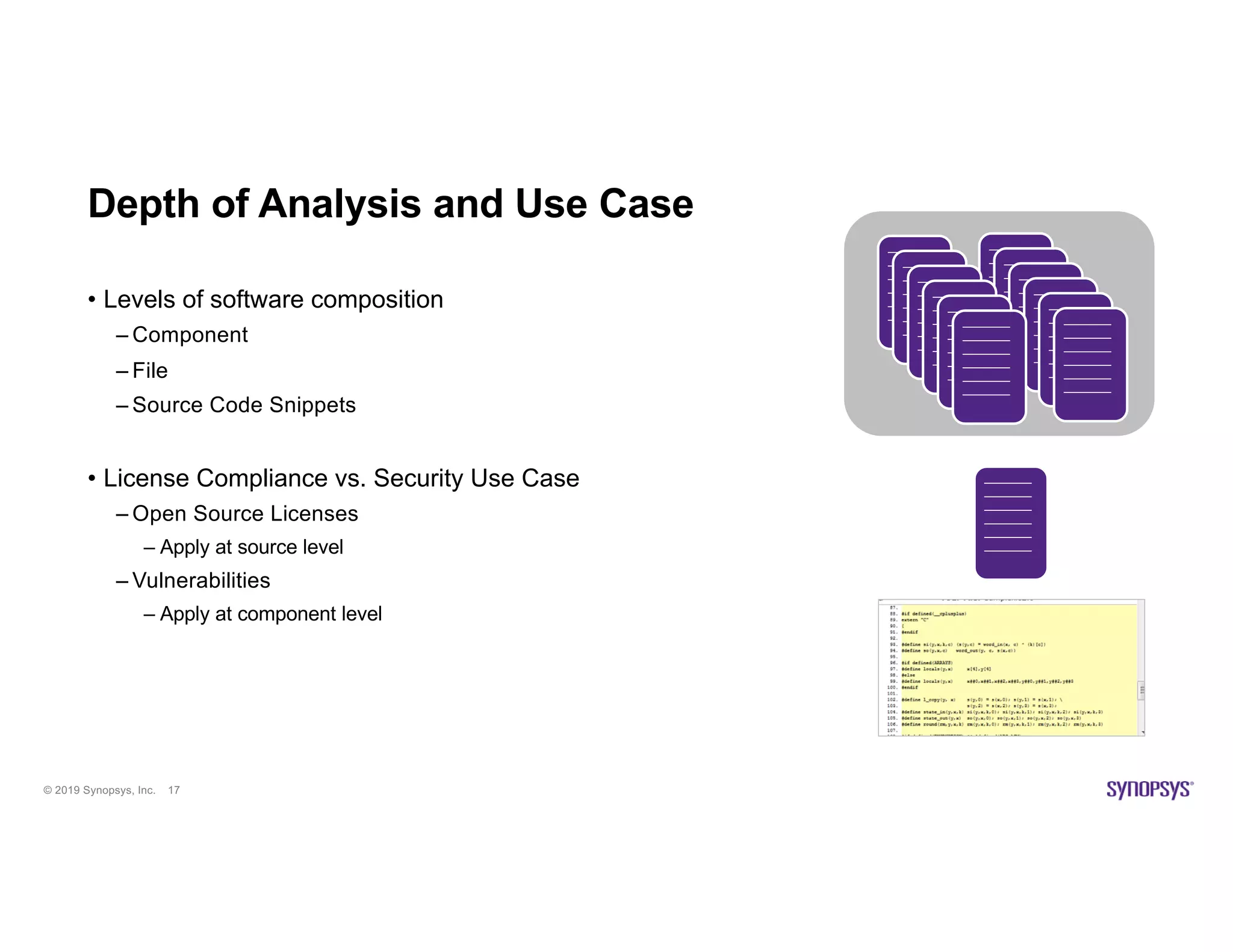
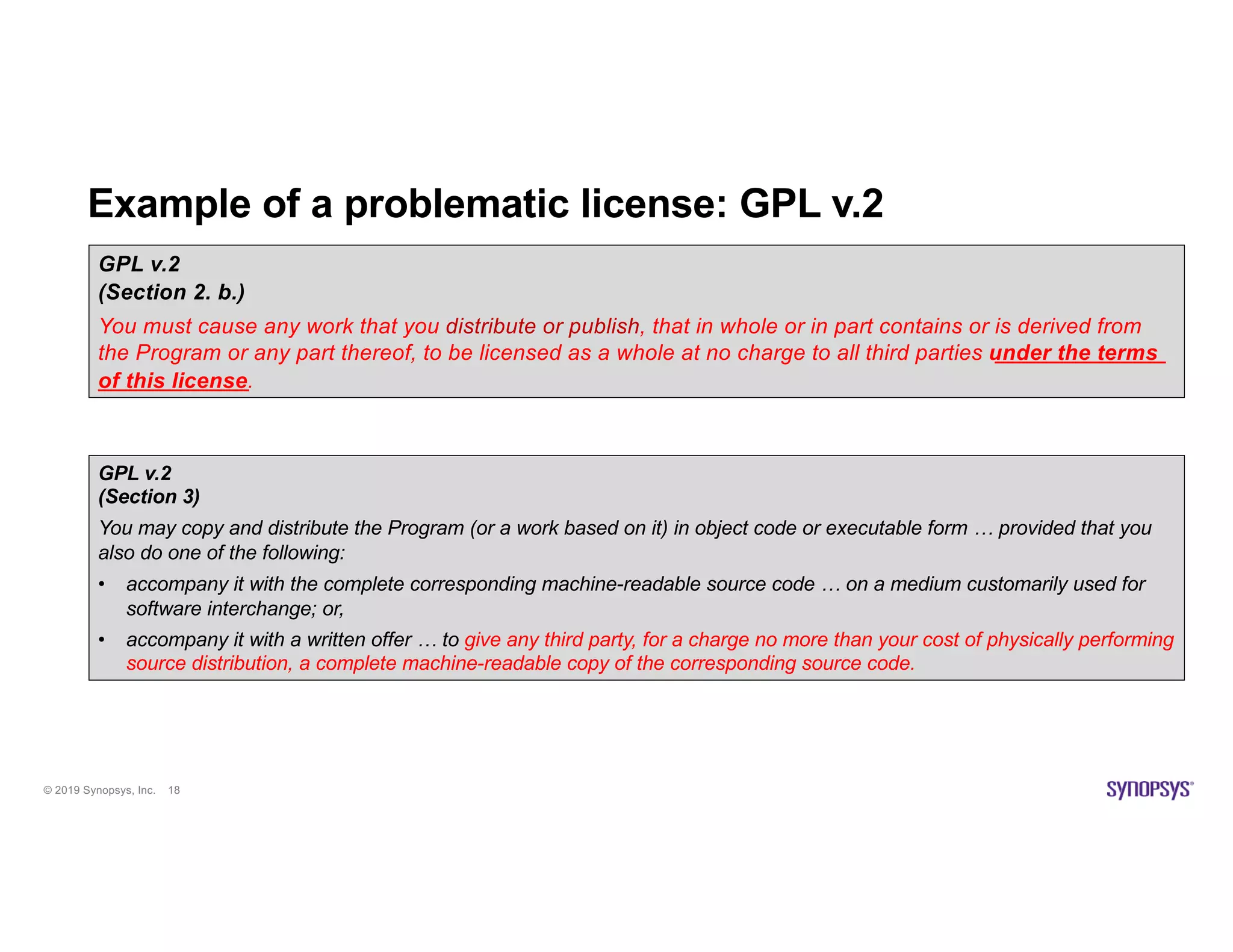
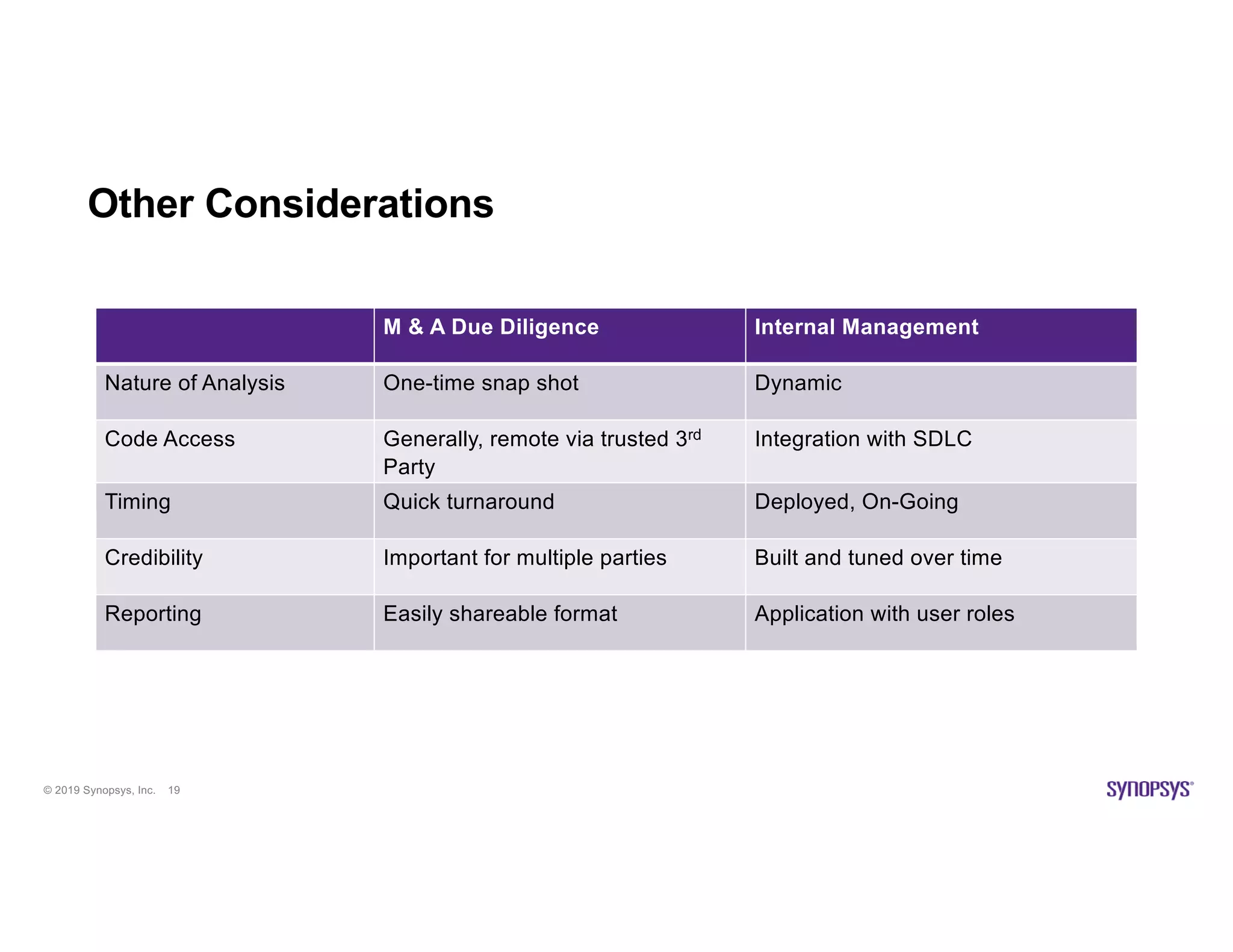
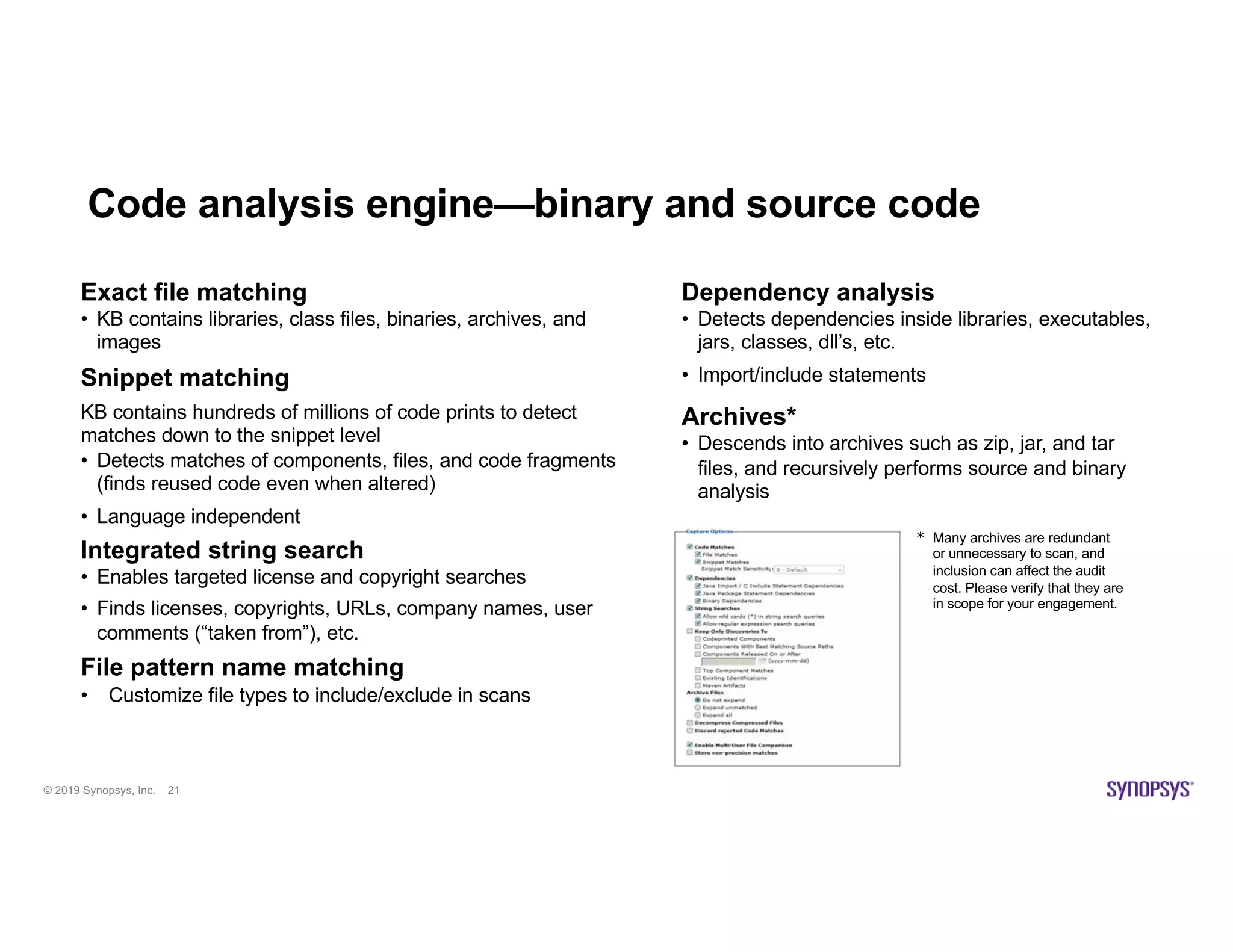
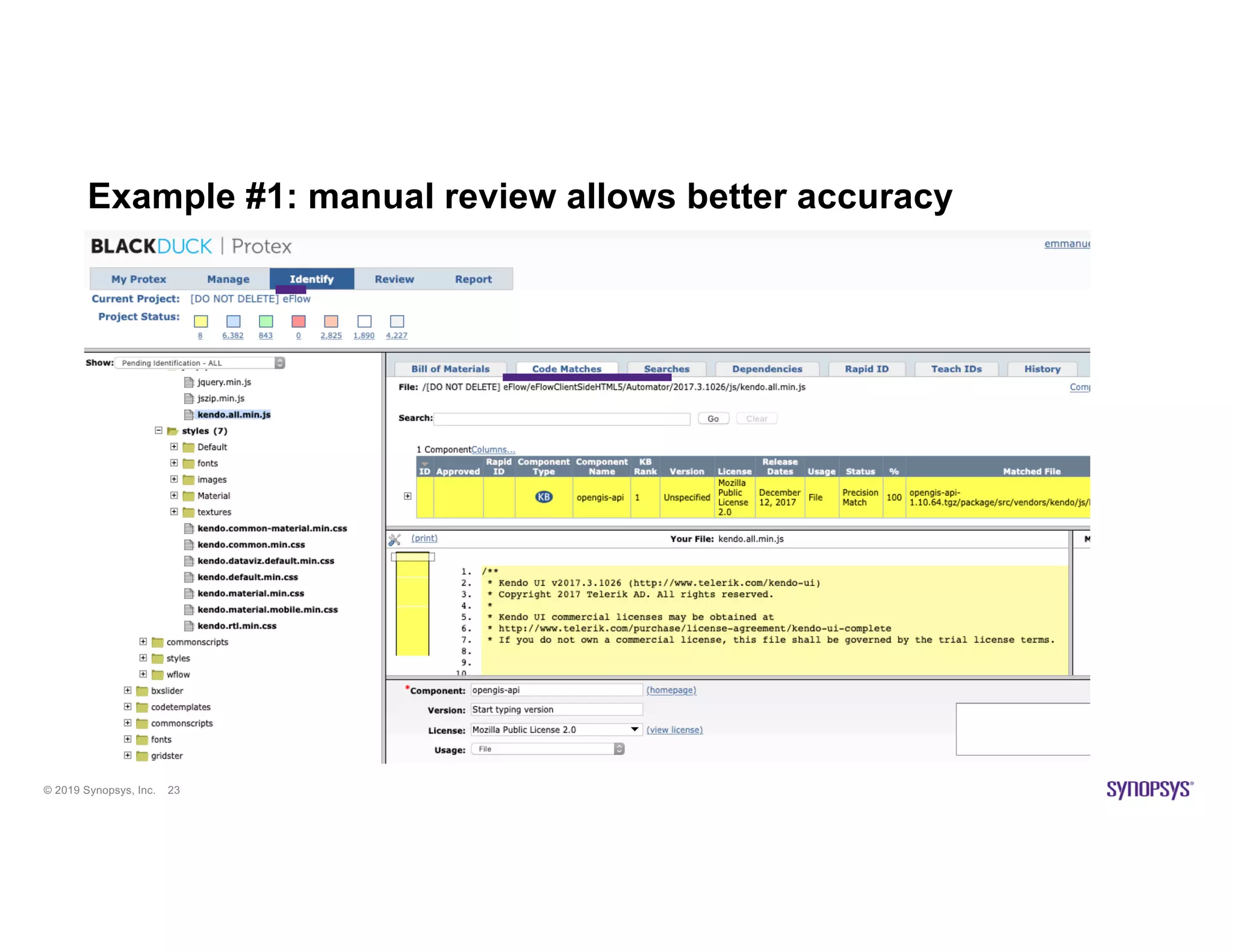
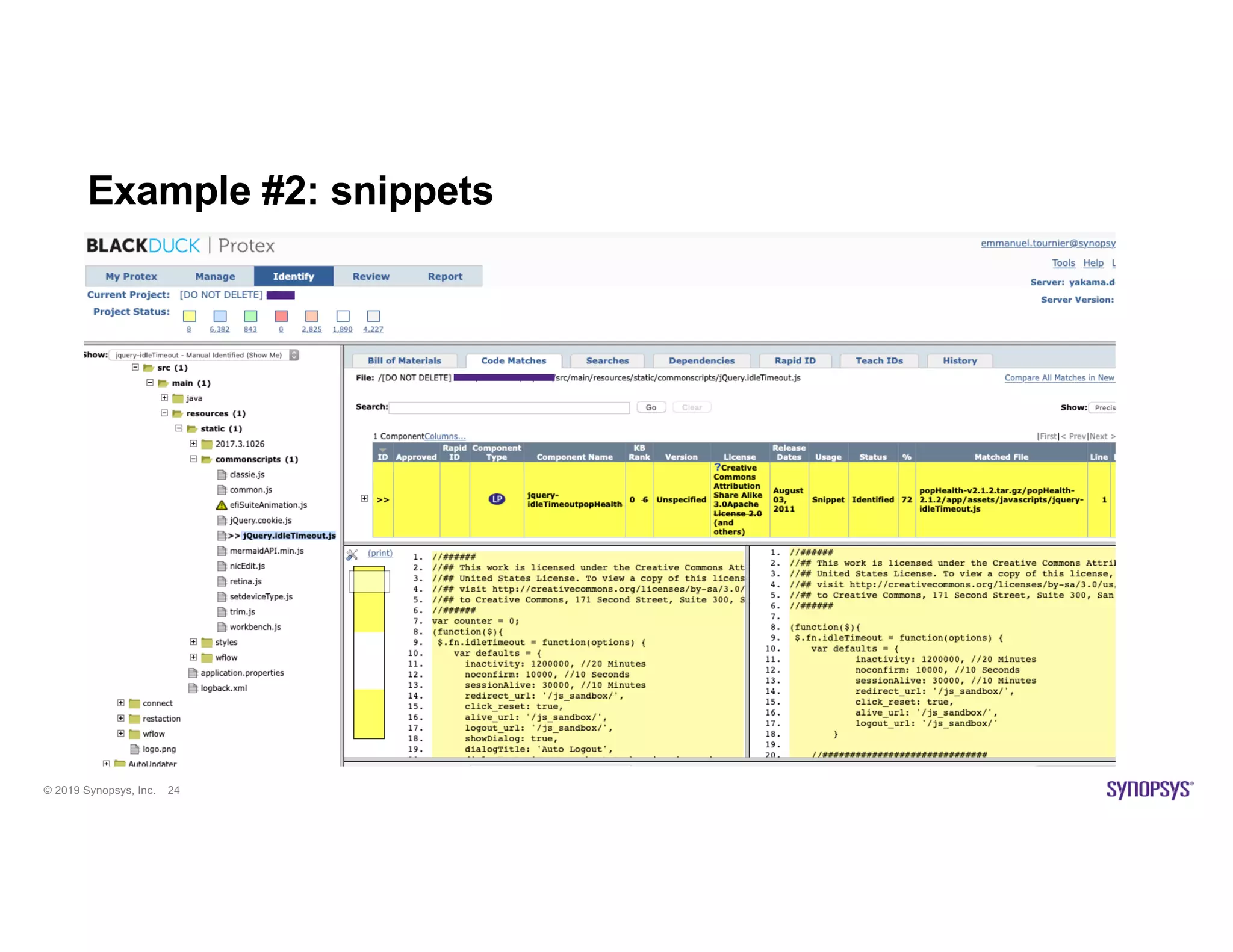
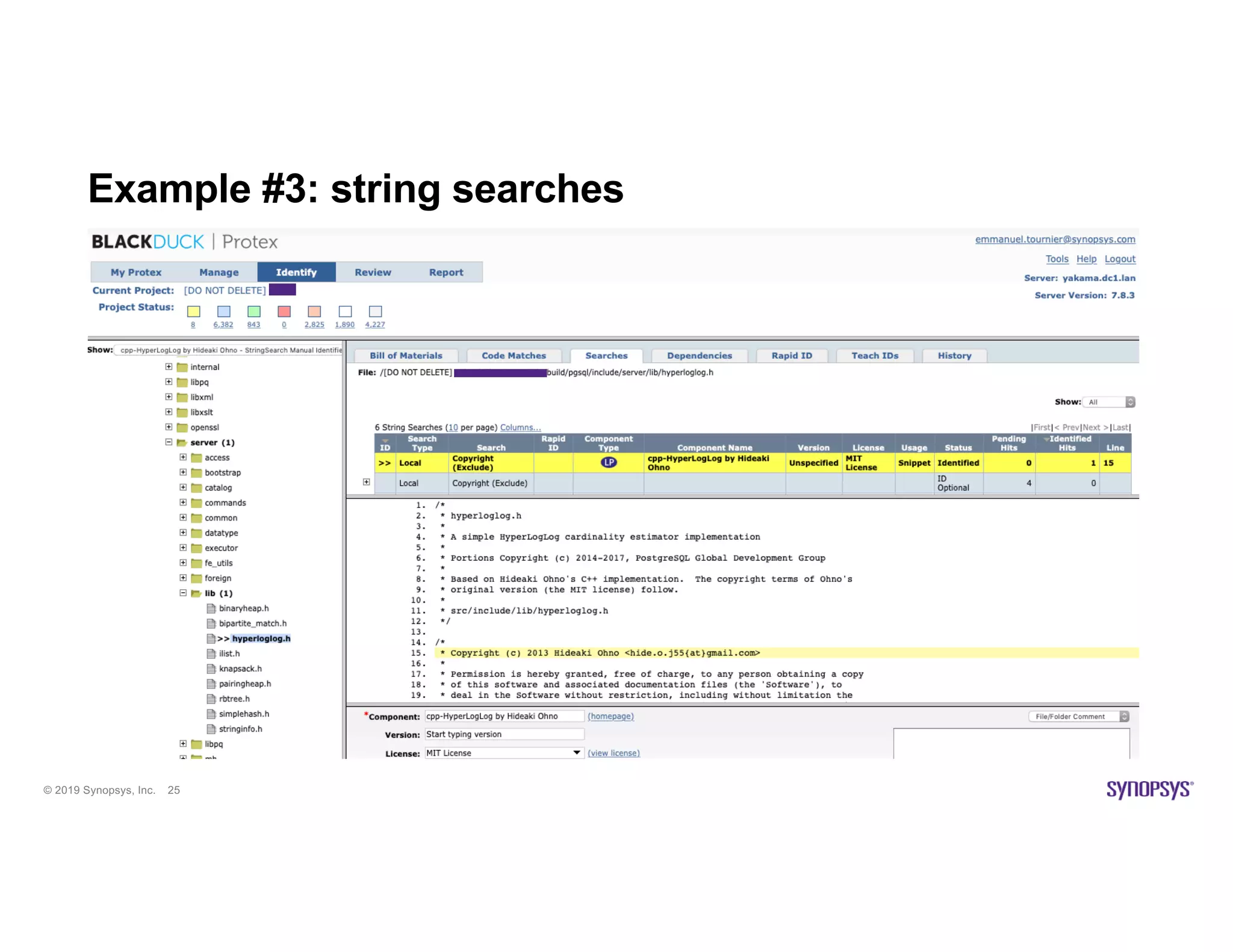
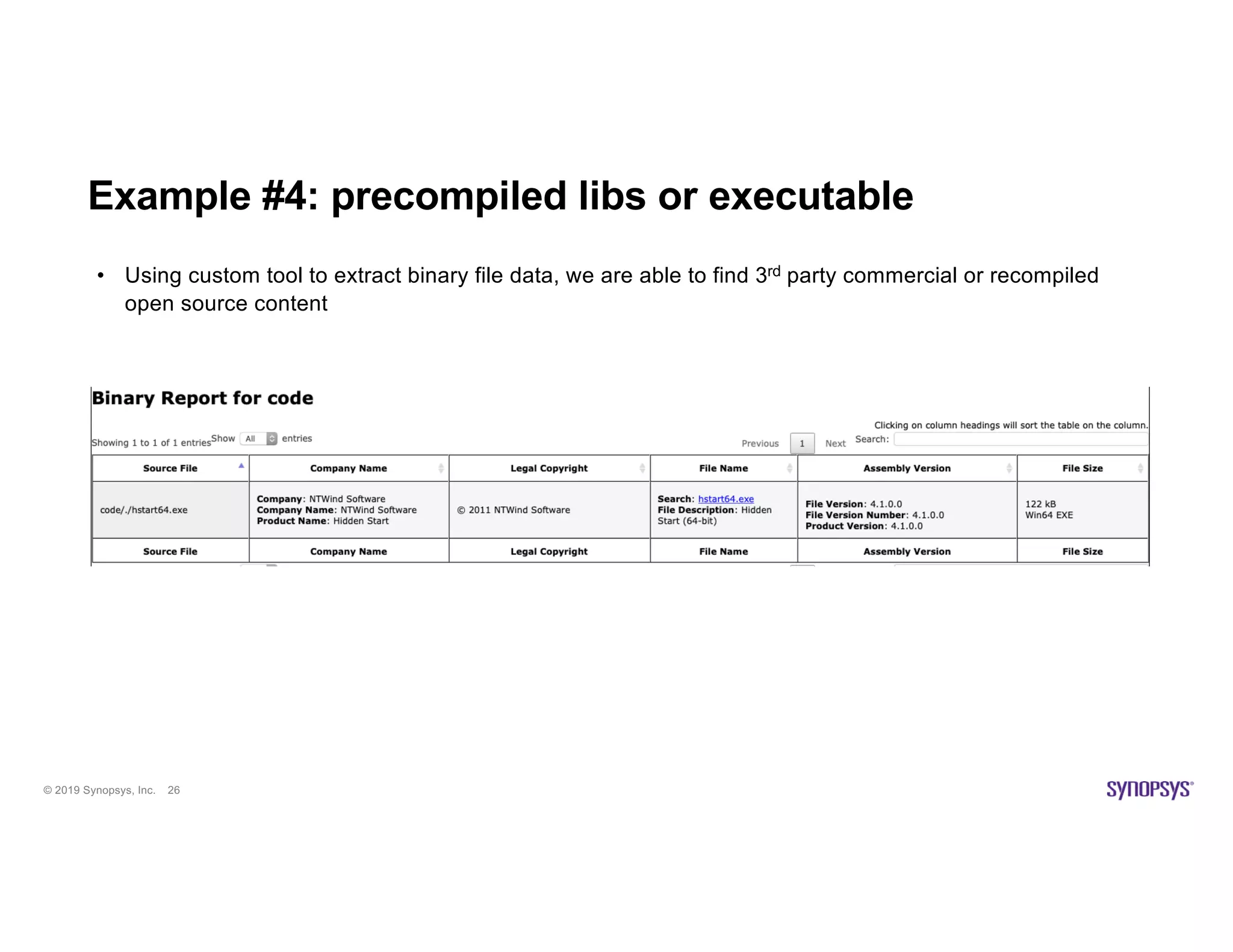
The document discusses the importance of open source scanning in software management, highlighting the various risks associated with unmanaged open source code, such as licensing, security vulnerabilities, and quality issues. It emphasizes that not all open source scans are equal, suggesting that trade-offs in depth and accuracy depend on specific scenarios and requirements, particularly during M&A due diligence. The document also outlines strategies for effective open source management, including the need for thorough audits and the integration of manual and automated analysis techniques.