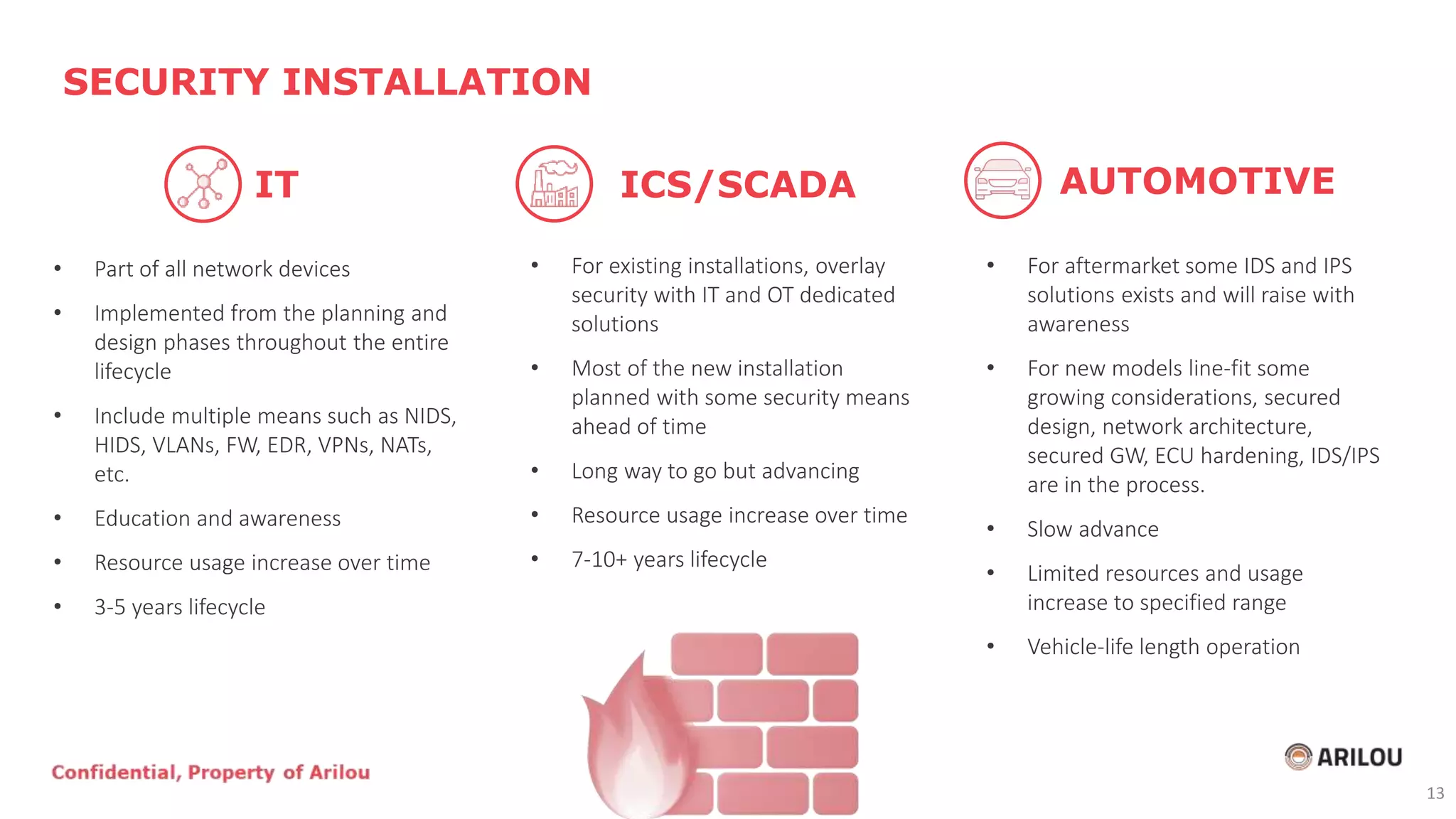
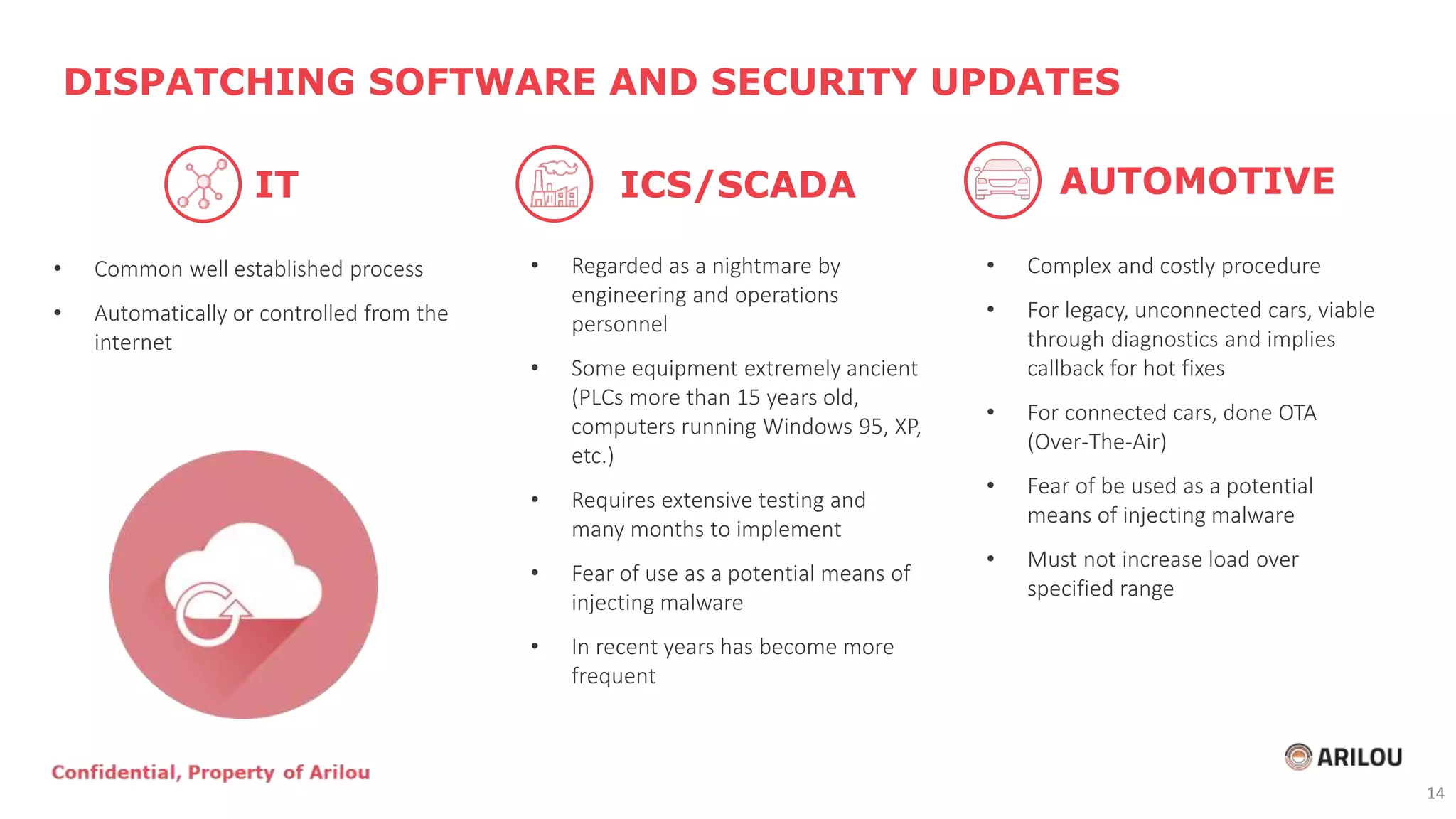
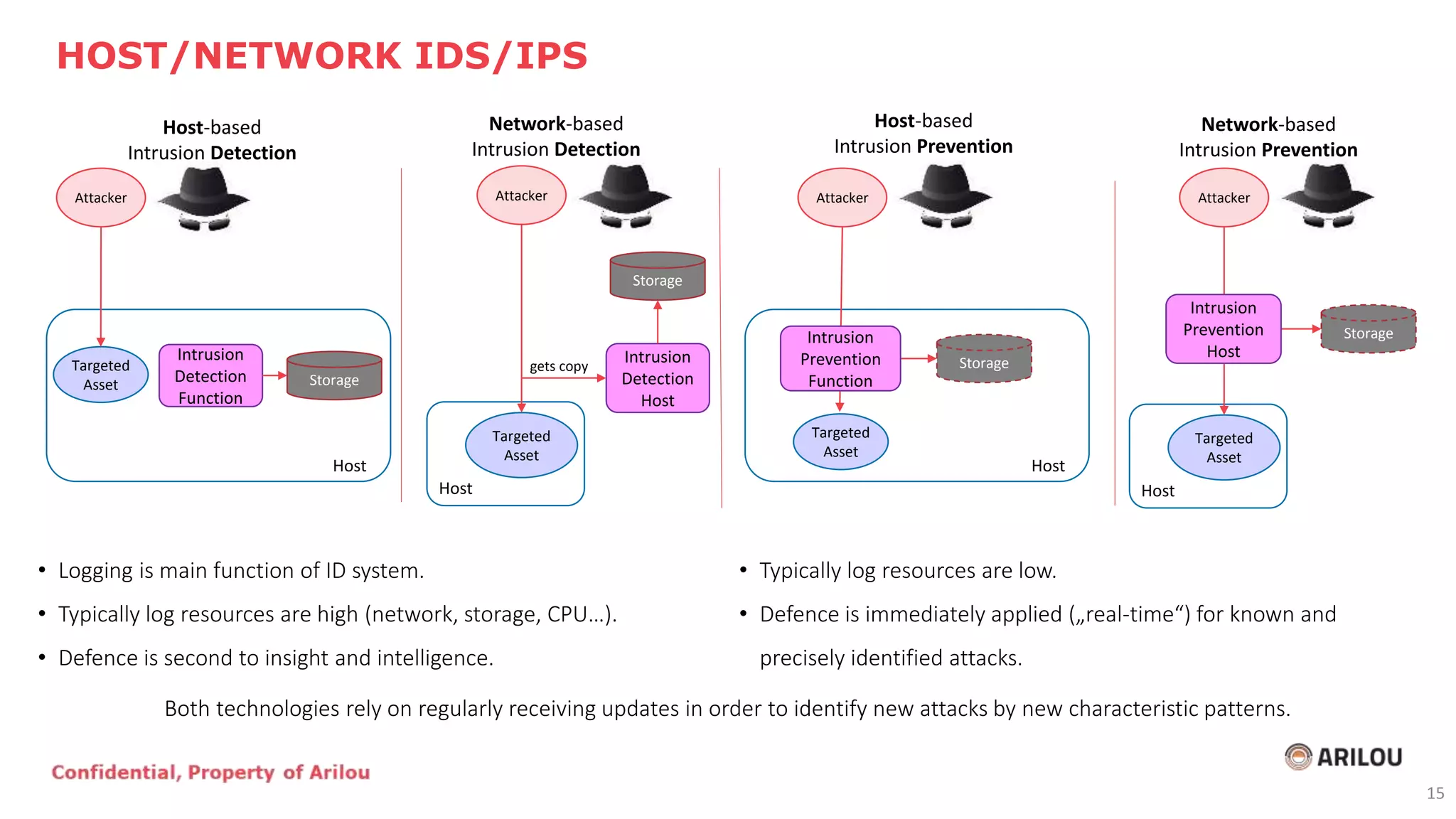
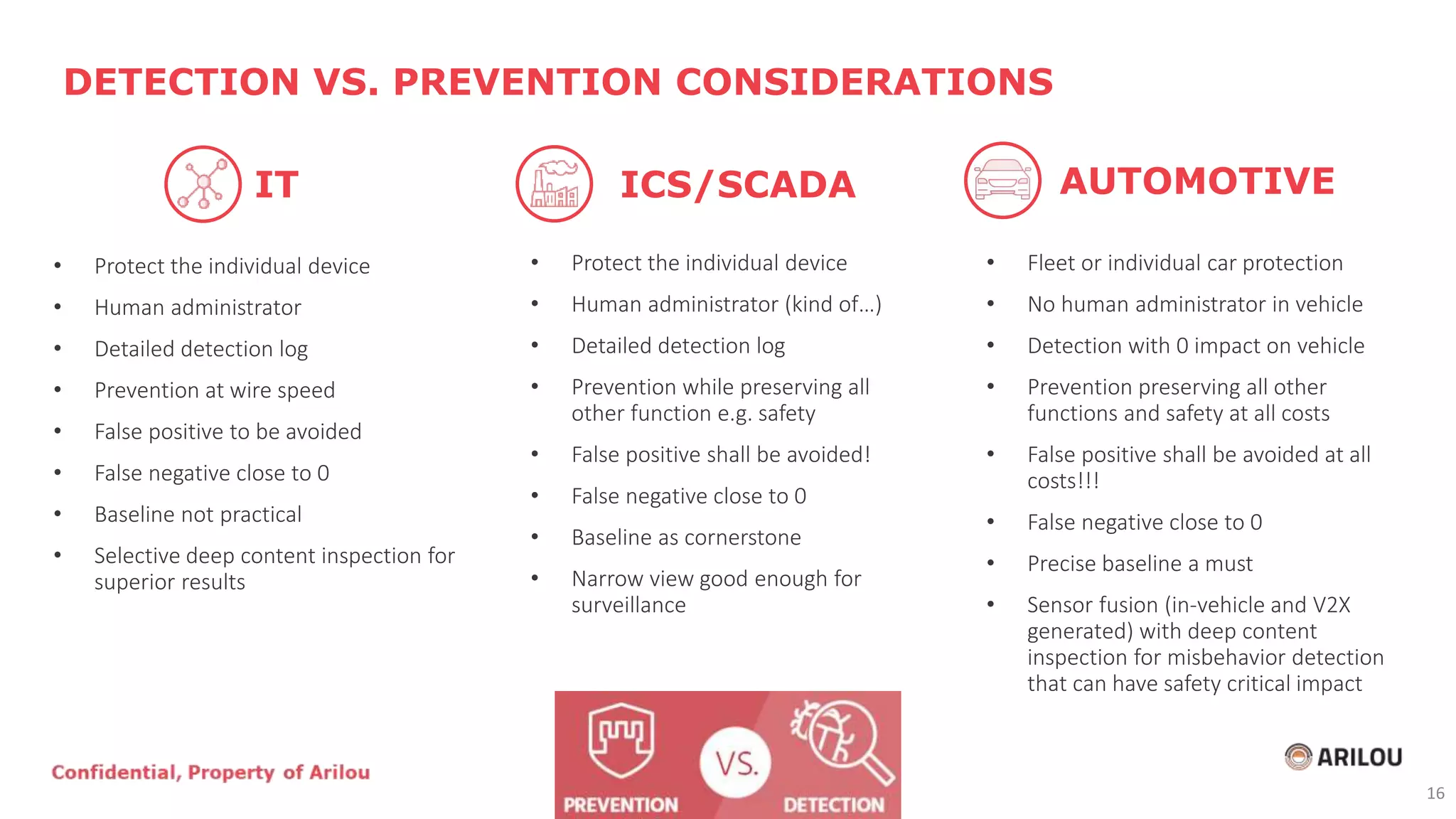
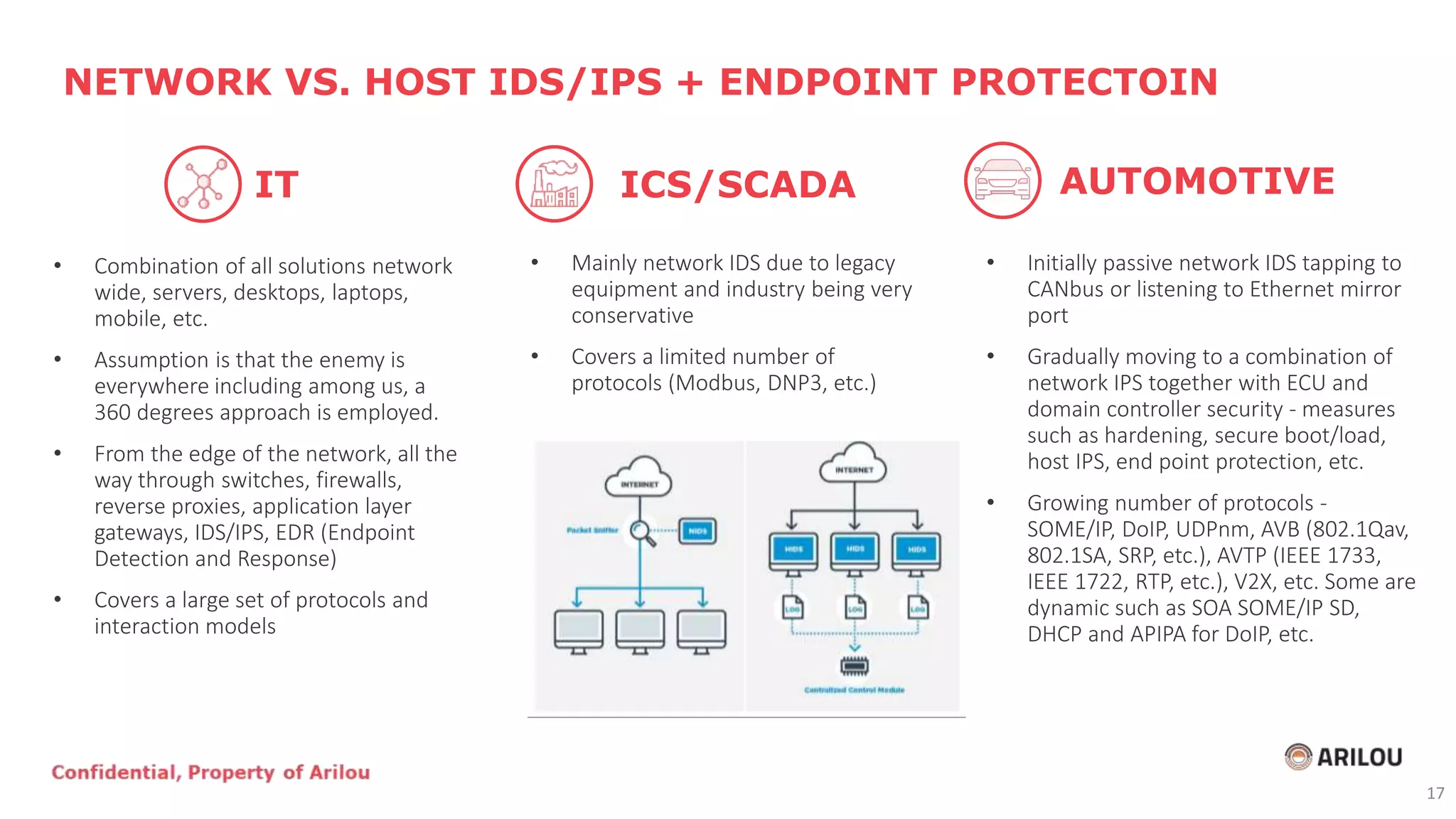
The document discusses the evolution and current state of cybersecurity in the automotive and operational technology sectors, highlighting the convergence of IT and OT, as well as the emergence of connected vehicles. It outlines various cyber threats, attack vectors, and the importance of security measures such as secured network architecture and incident response teams. Additionally, it emphasizes the need for organizations to address cybersecurity challenges proactively and invest in layered defense strategies to protect against potential attacks.