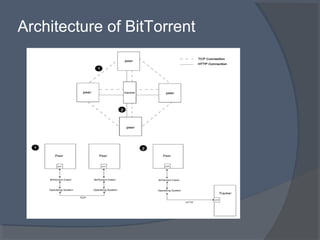
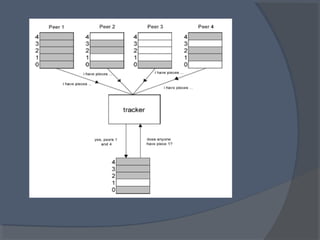
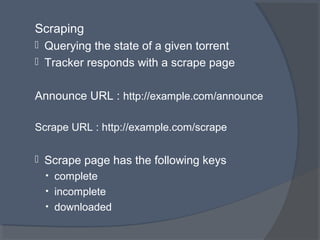
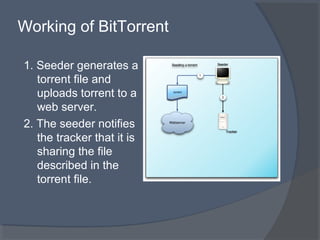
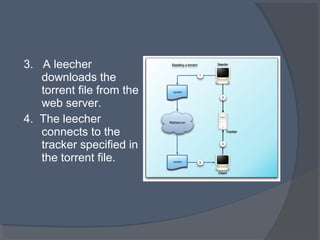
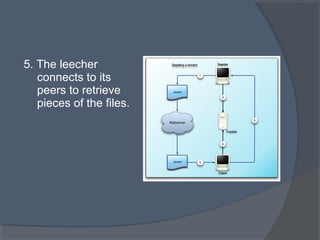
This document discusses the architecture and workings of the BitTorrent protocol. It begins with an introduction and overview of other file transfer methods. The key components of the BitTorrent system are then explained, including the torrent file, tracker, peers, and client software. The document outlines how BitTorrent uses a decentralized structure and tit-for-tat data exchange between peers to efficiently distribute file pieces across the network with no single point of failure.