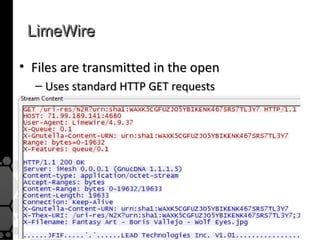
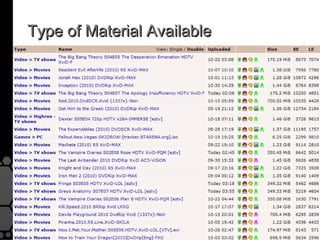
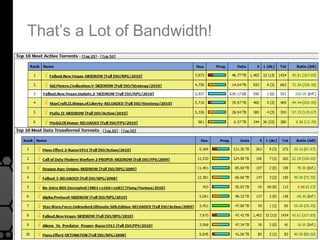
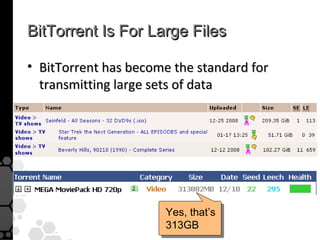
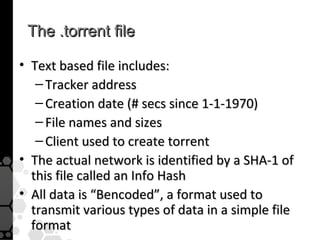
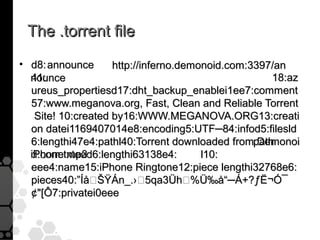
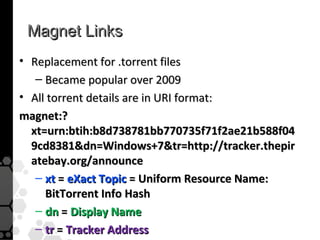
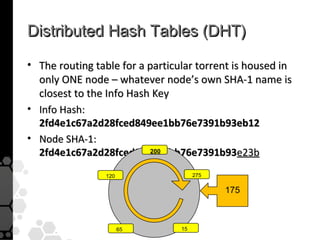
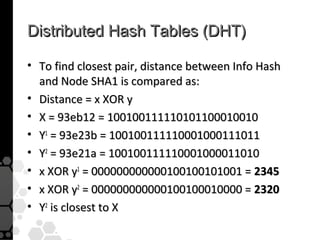
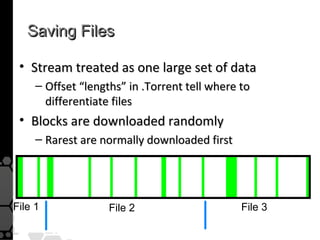
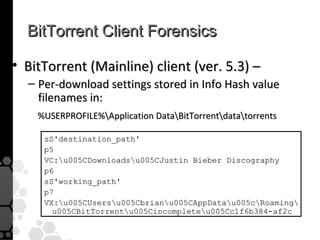
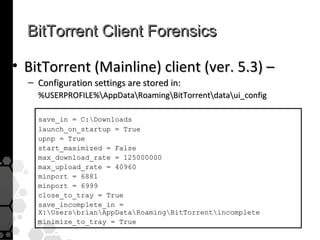
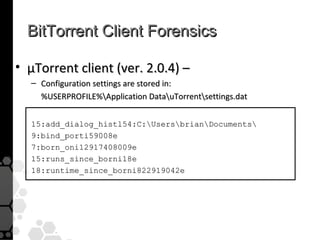
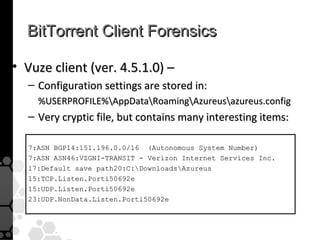
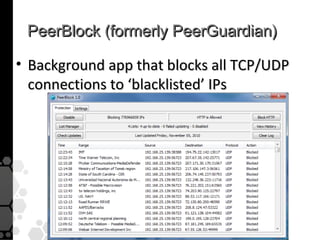
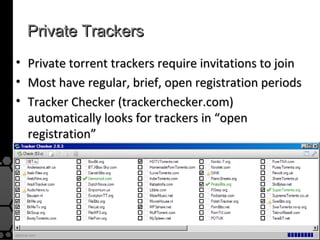
The document discusses the history, legal developments, and technical aspects of peer-to-peer (P2P) file sharing platforms, focusing on prominent clients like Kazaa, BitTorrent, and LimeWire. It details legal complications faced by these platforms, including notable court cases, copyright infringement issues, and the evolution of technology used in file sharing such as .torrent files and magnet links. Additionally, it highlights the forensic implications of these platforms for tracking user behavior and data extraction from network captures.