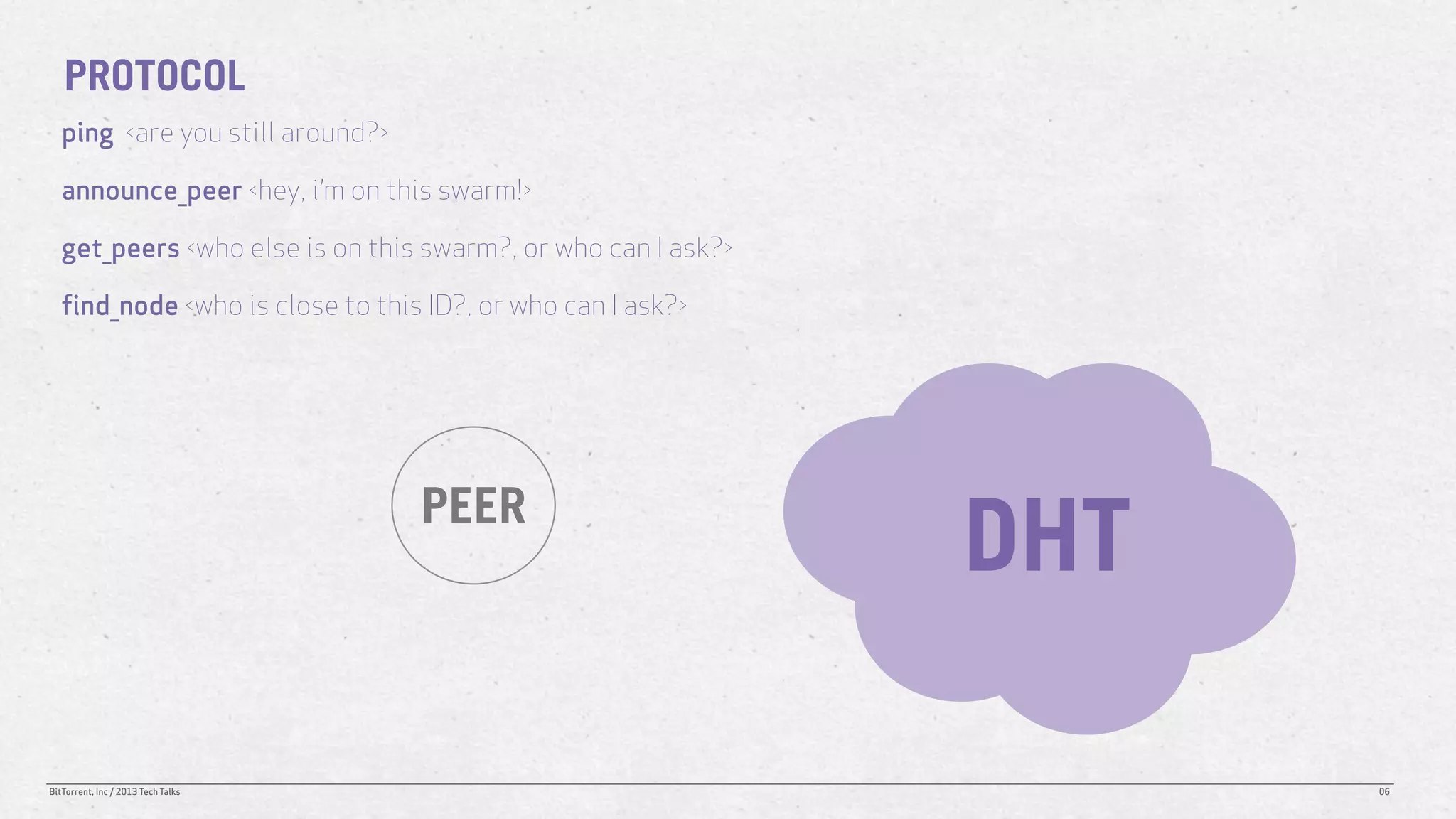
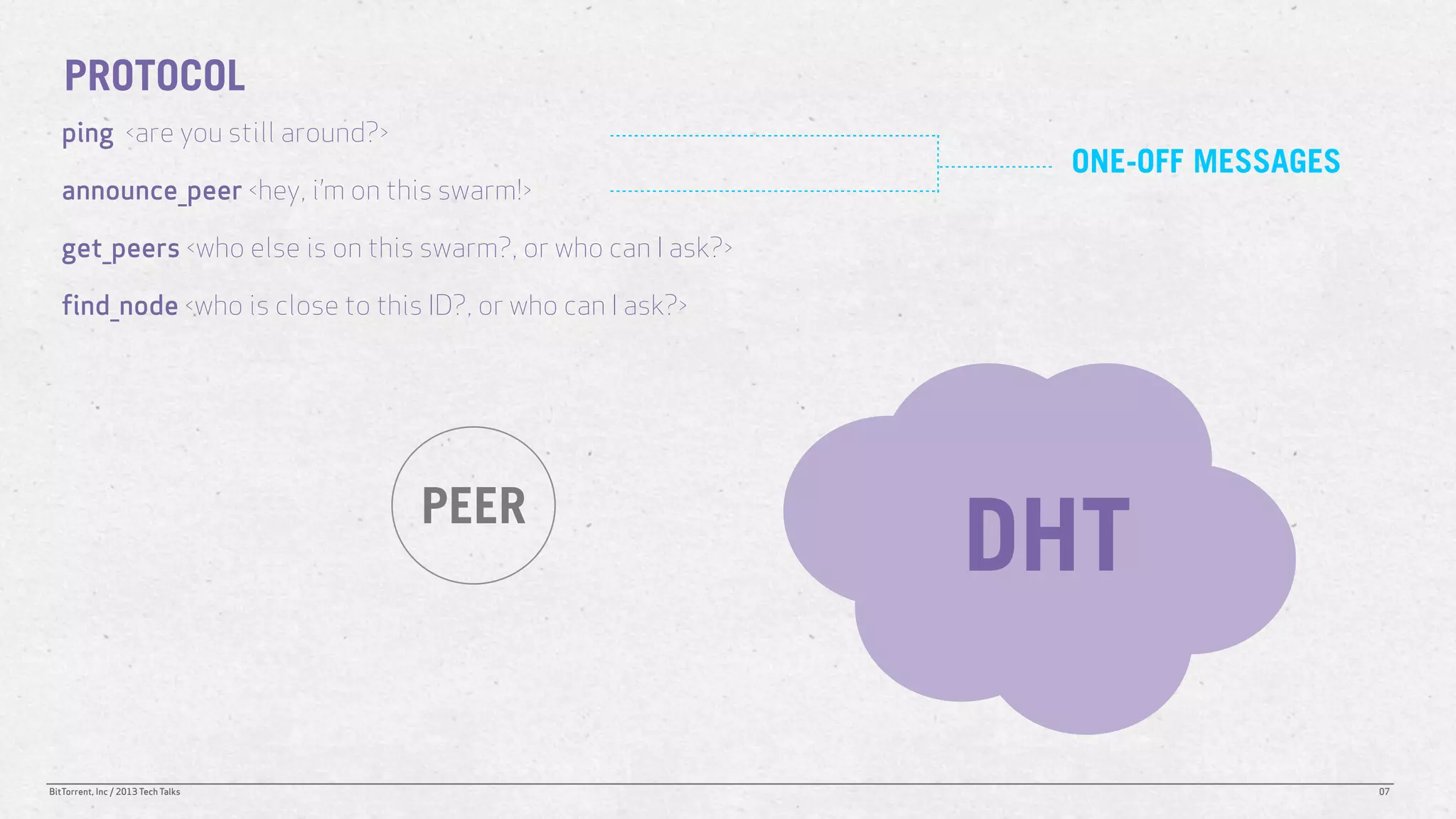
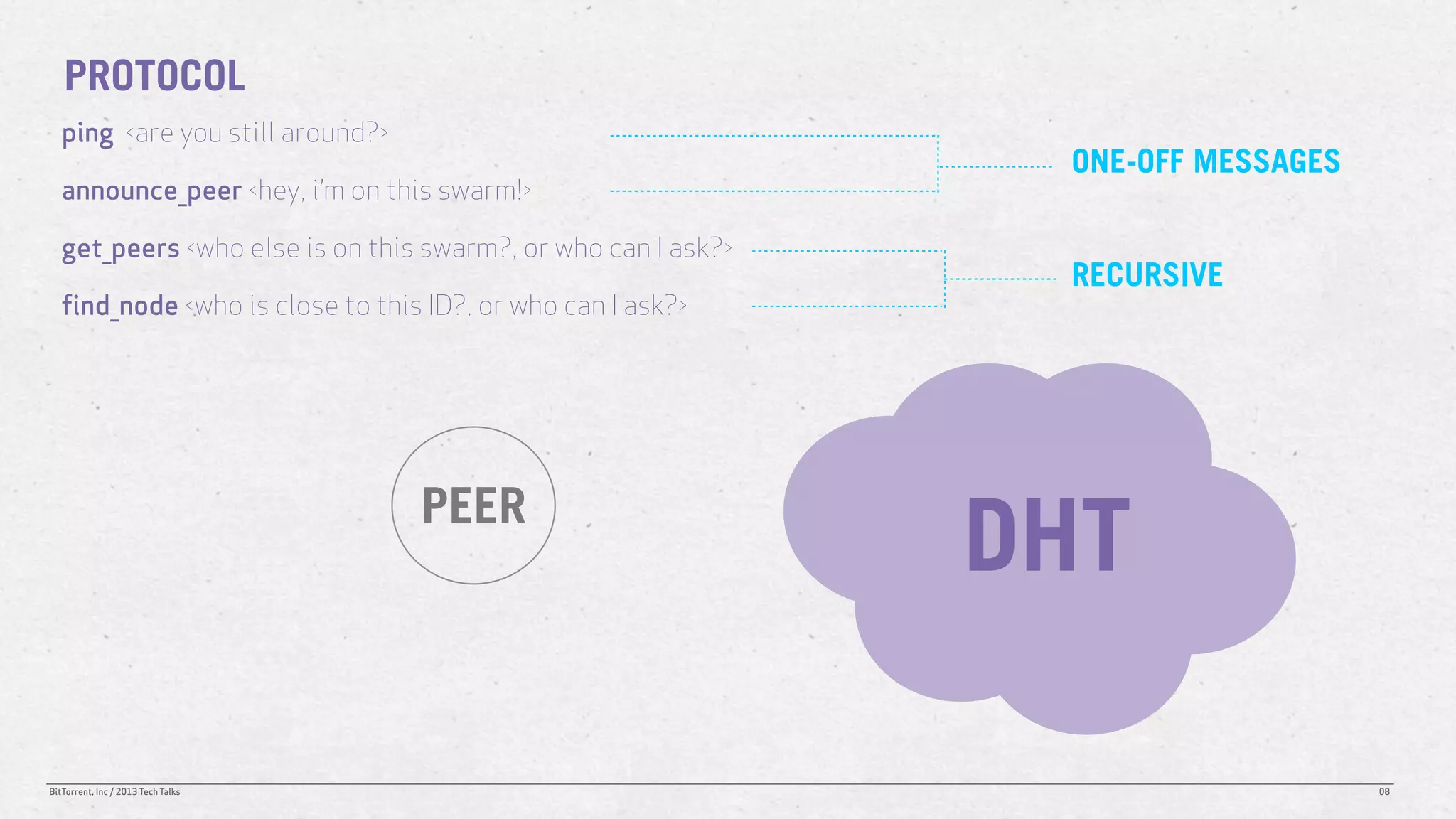
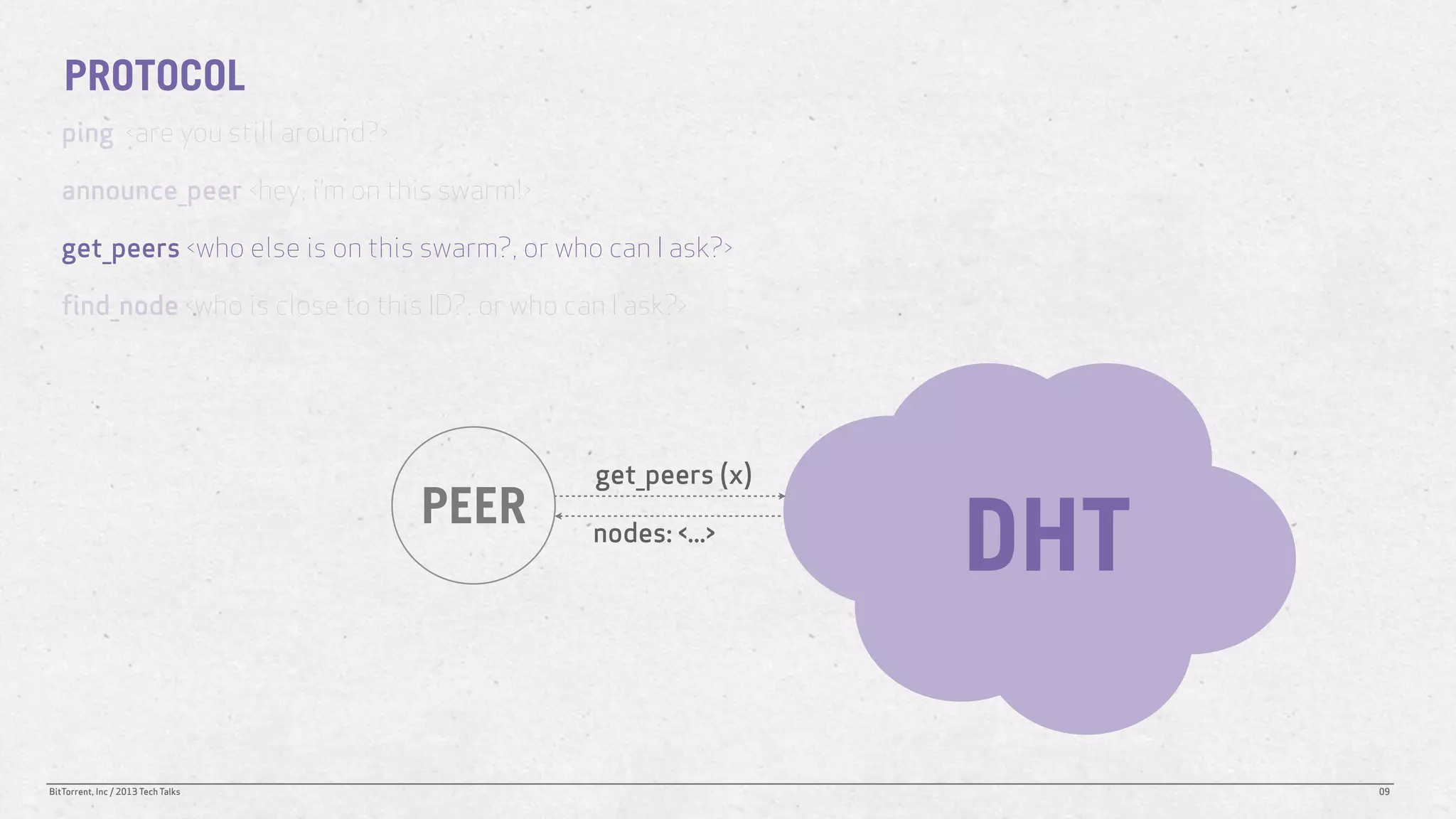
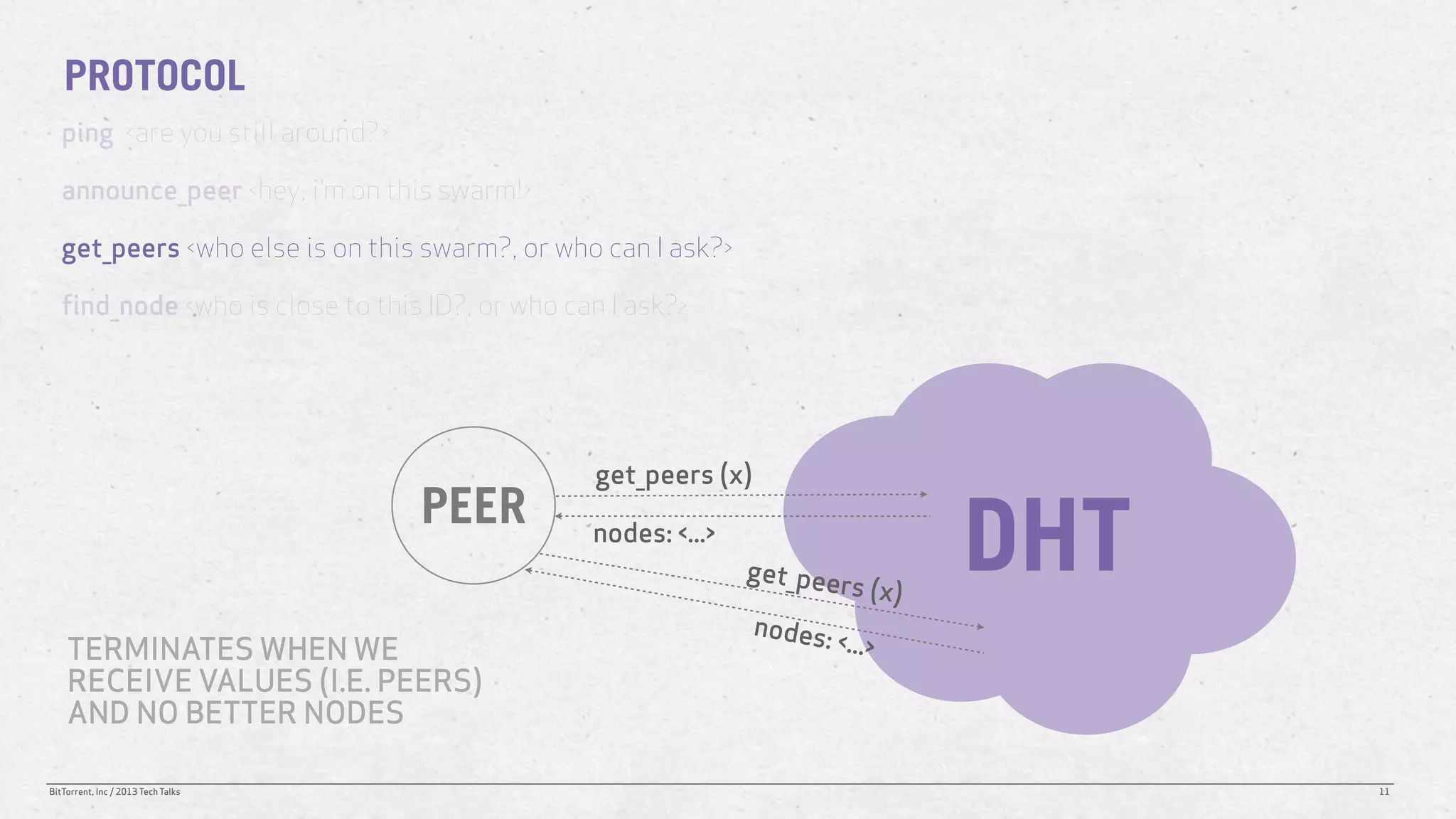
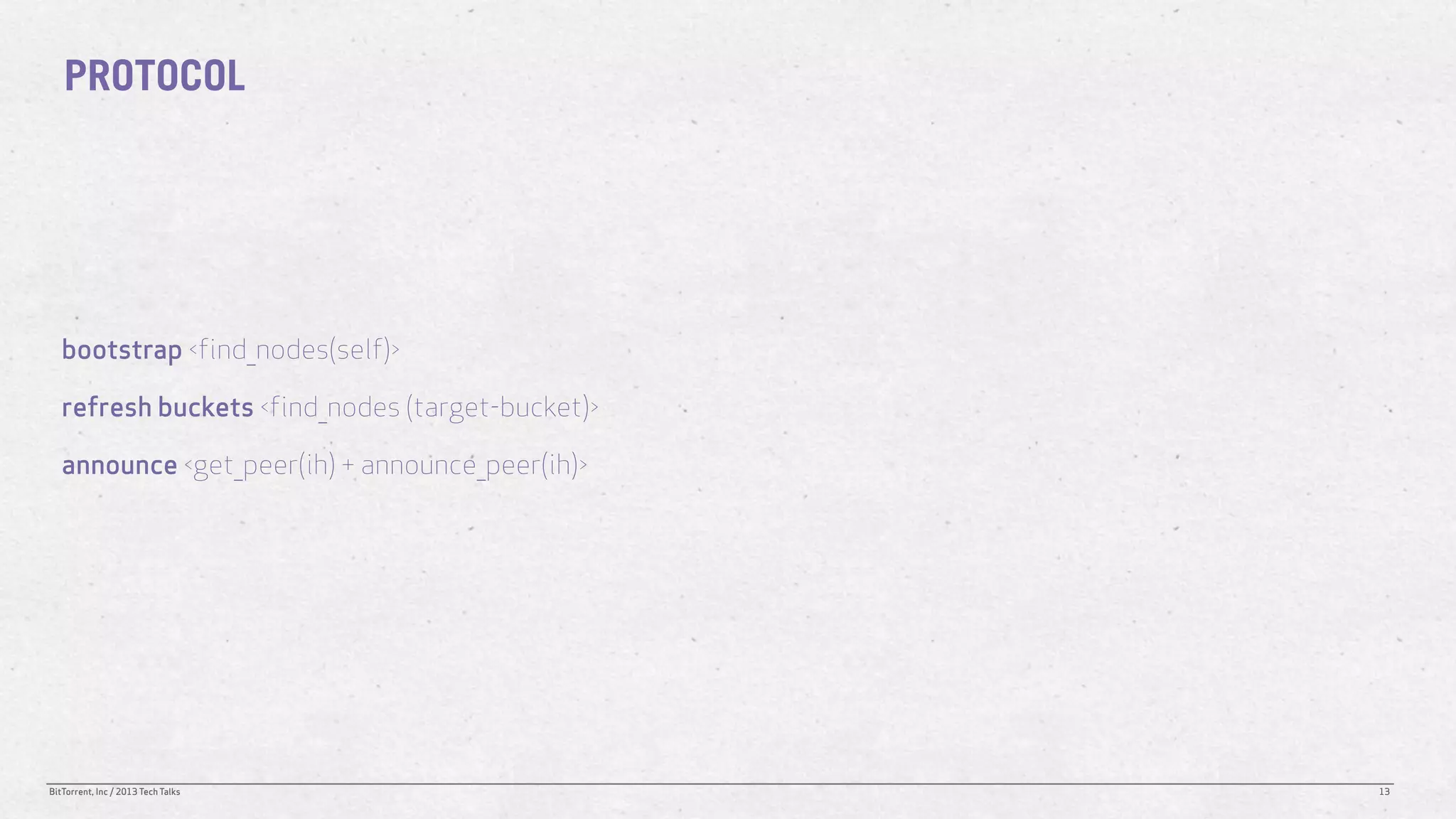
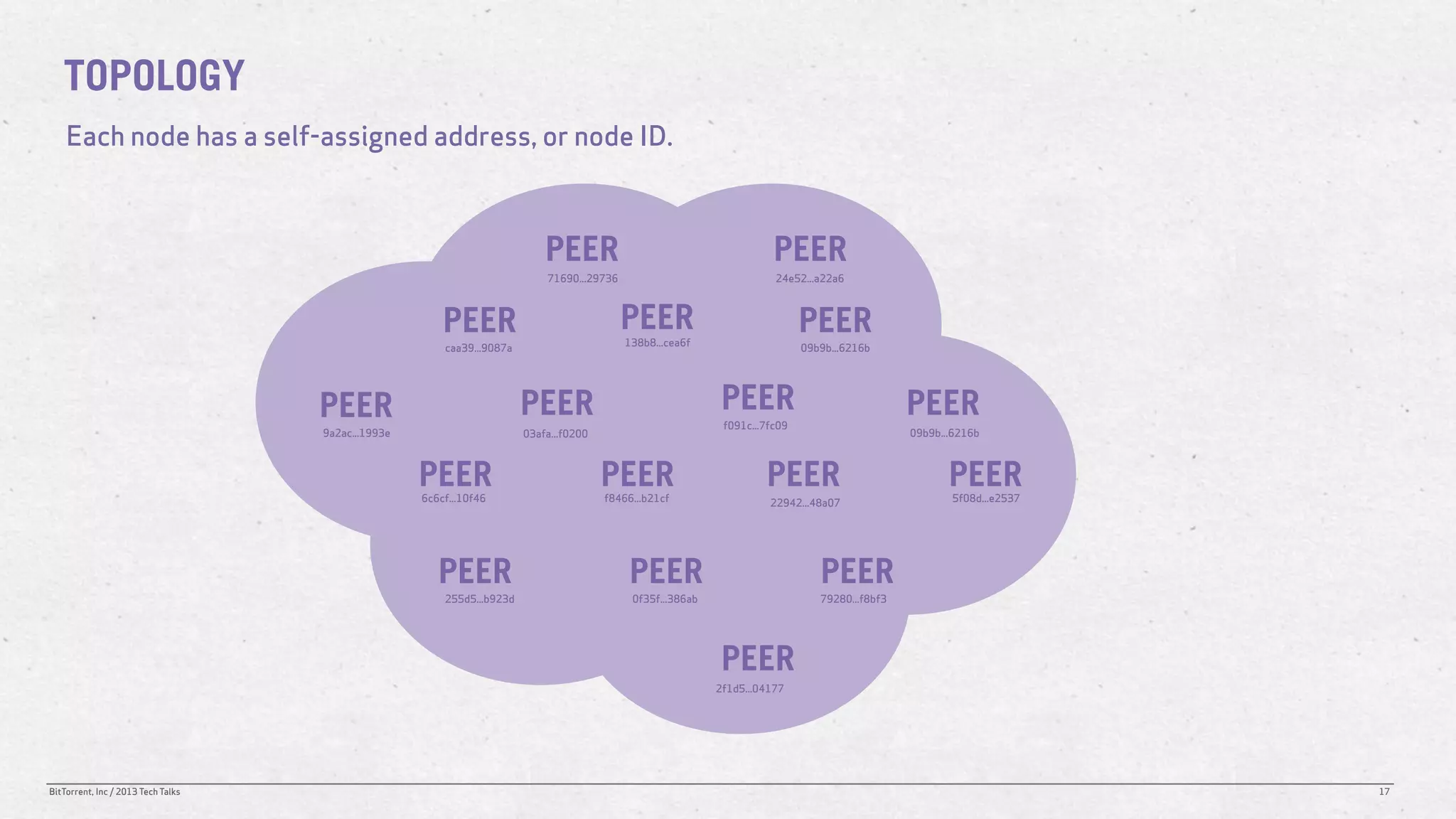
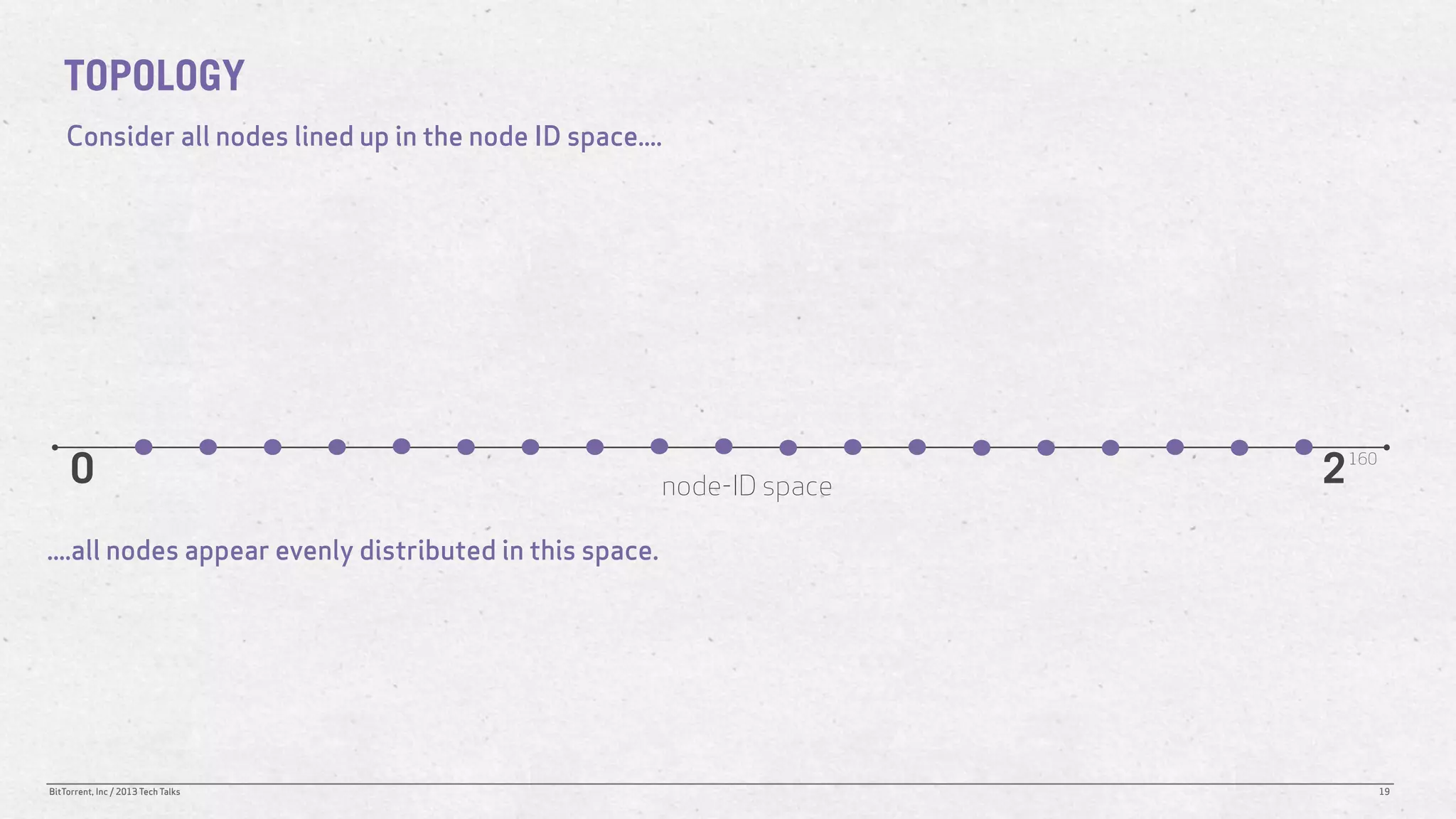
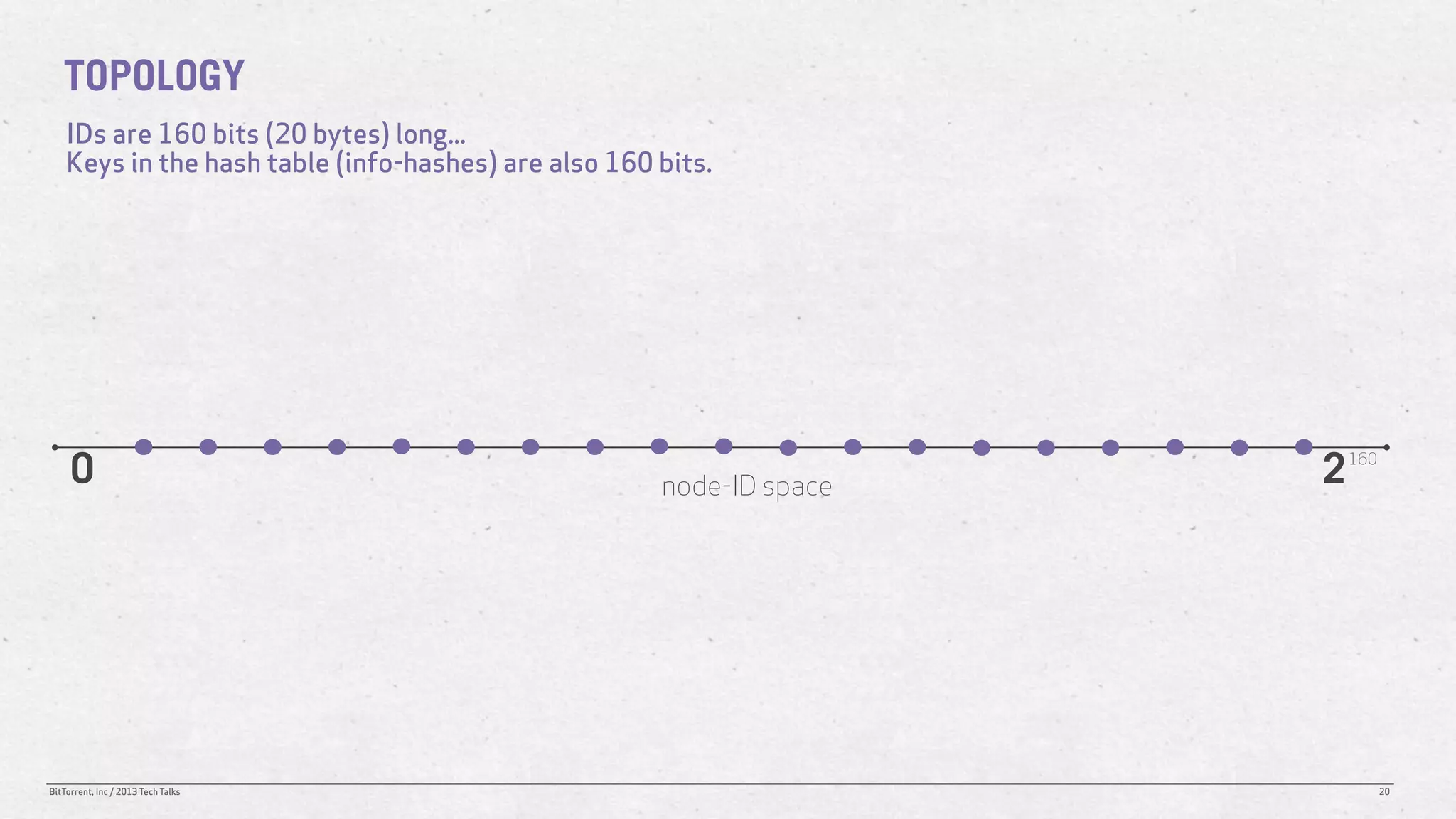
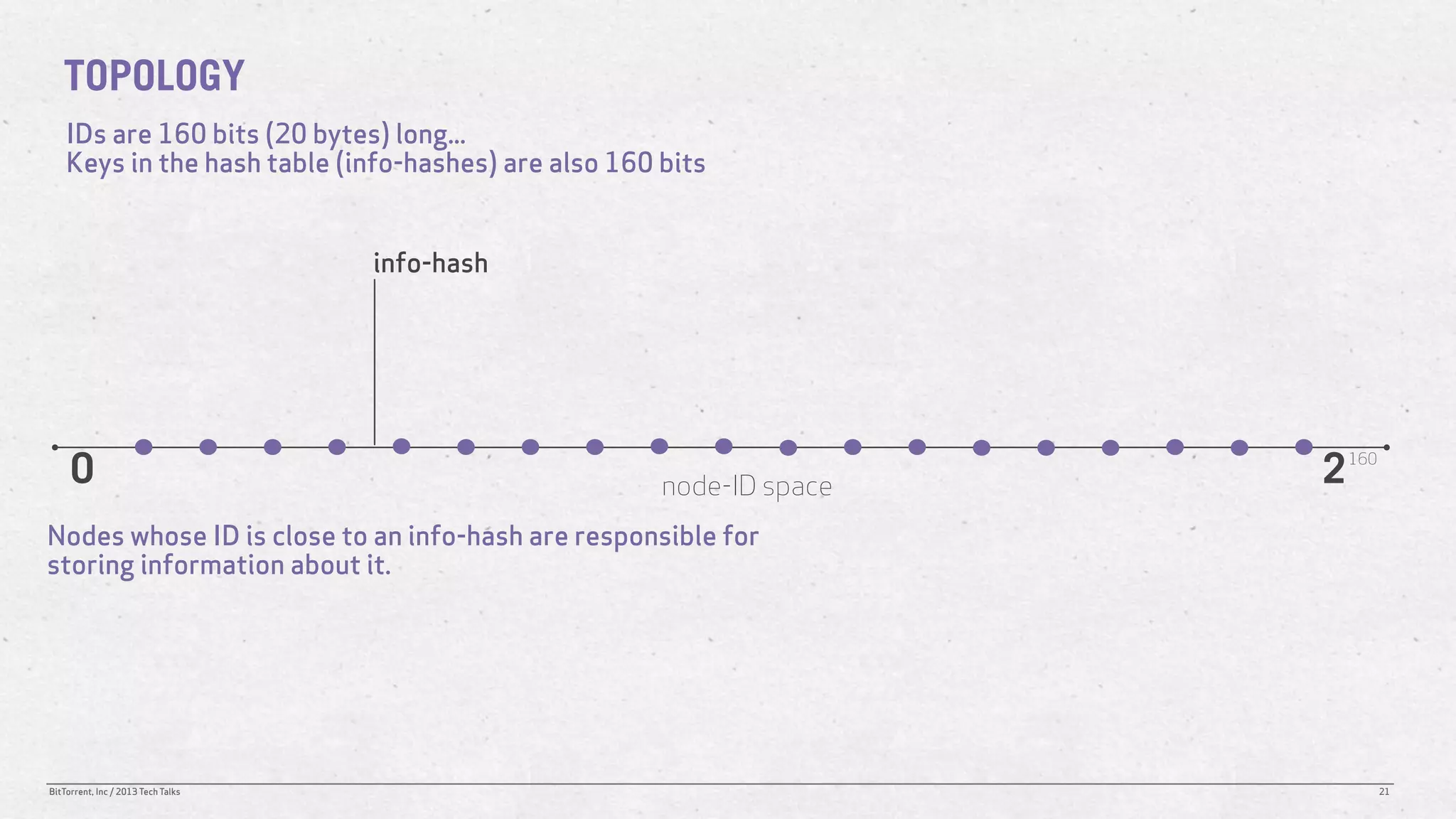
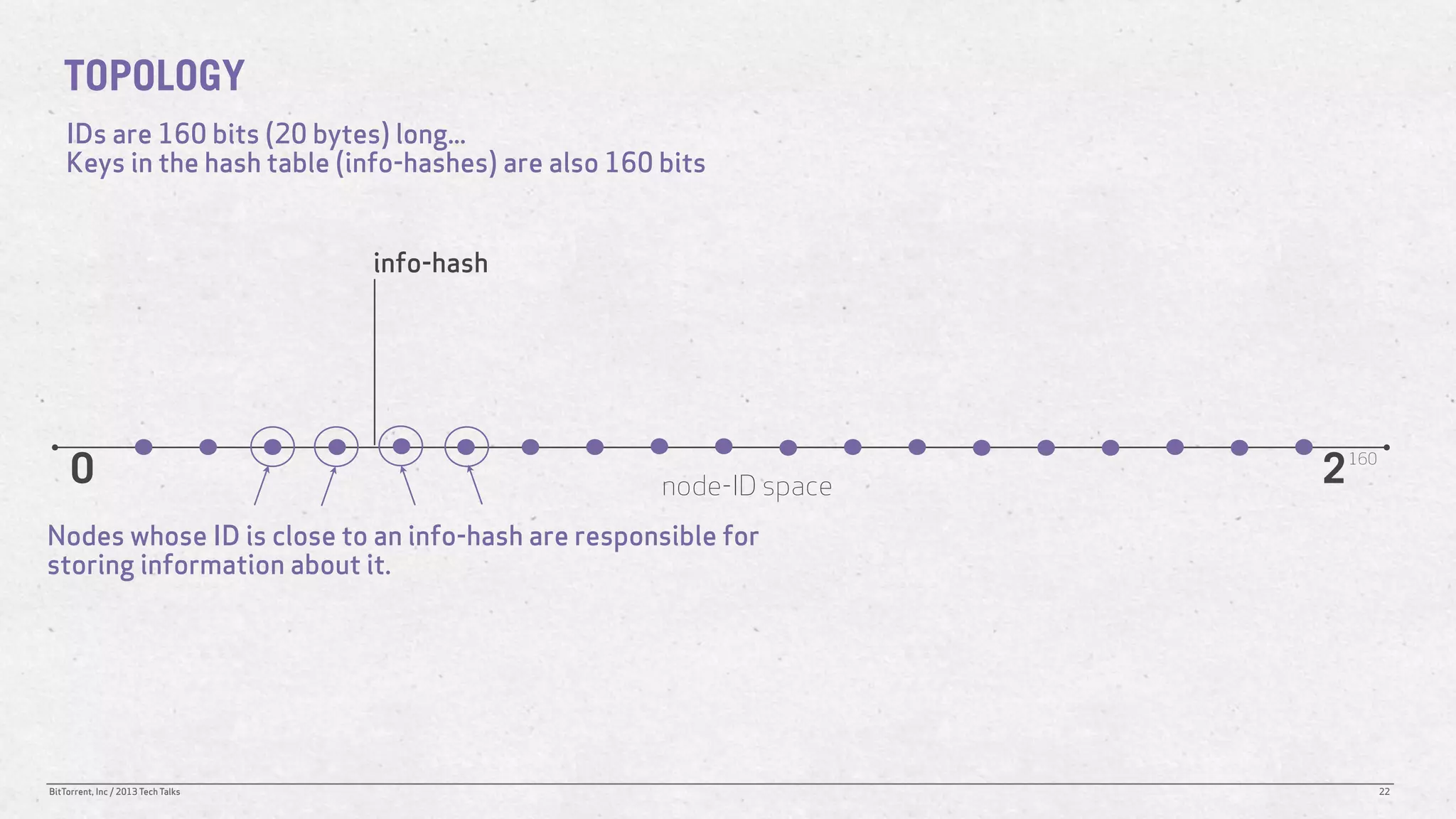
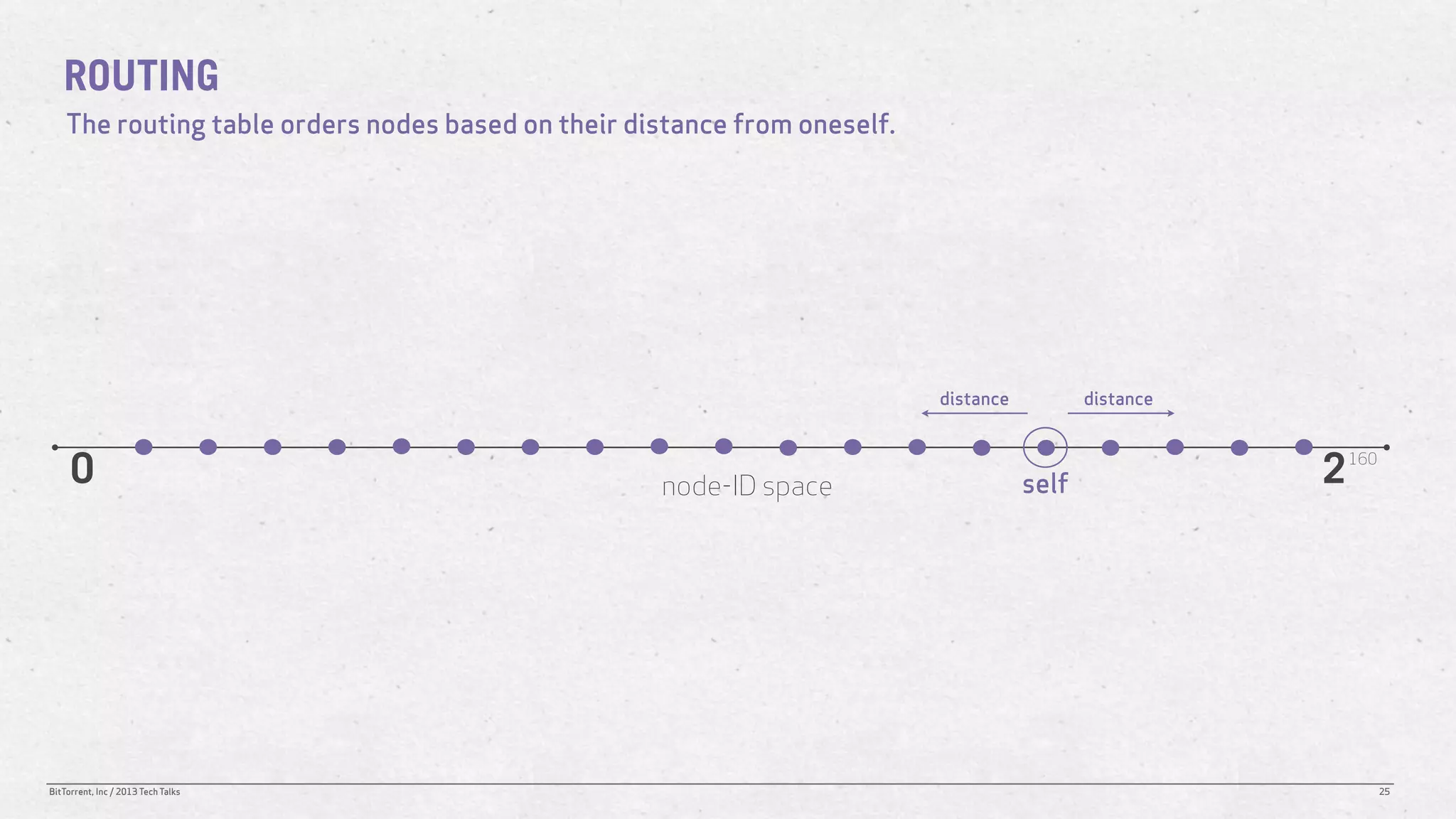
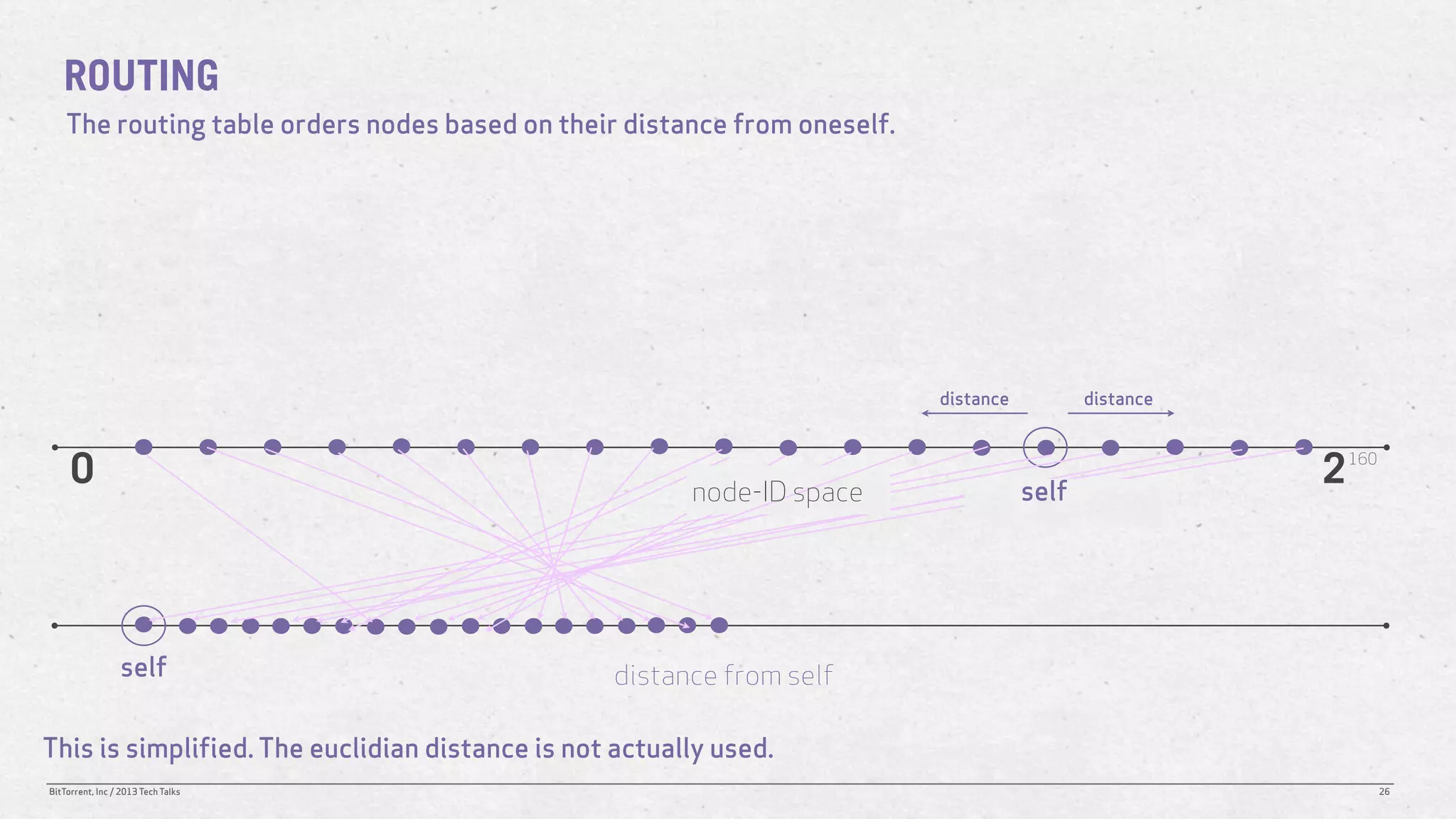
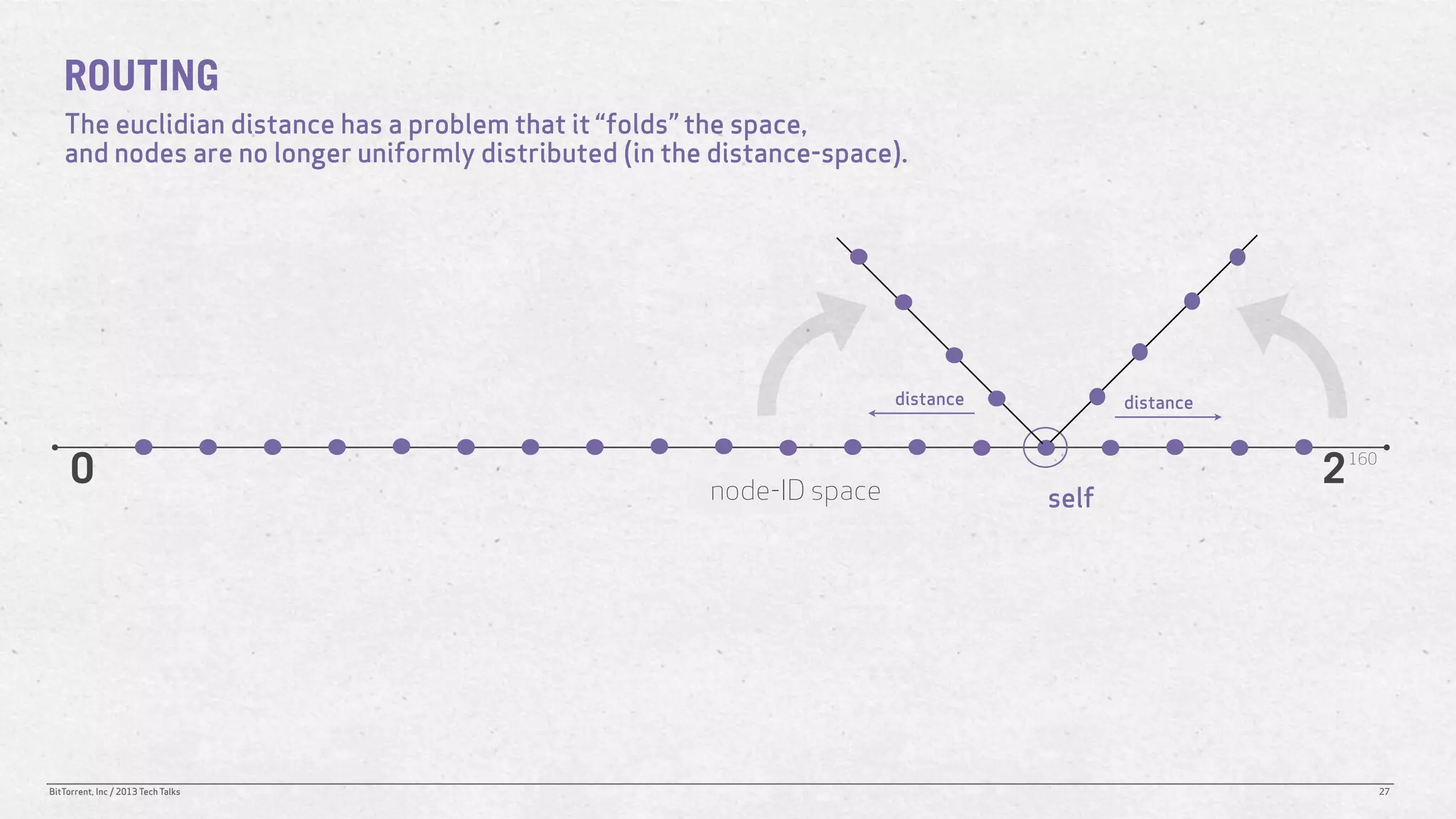
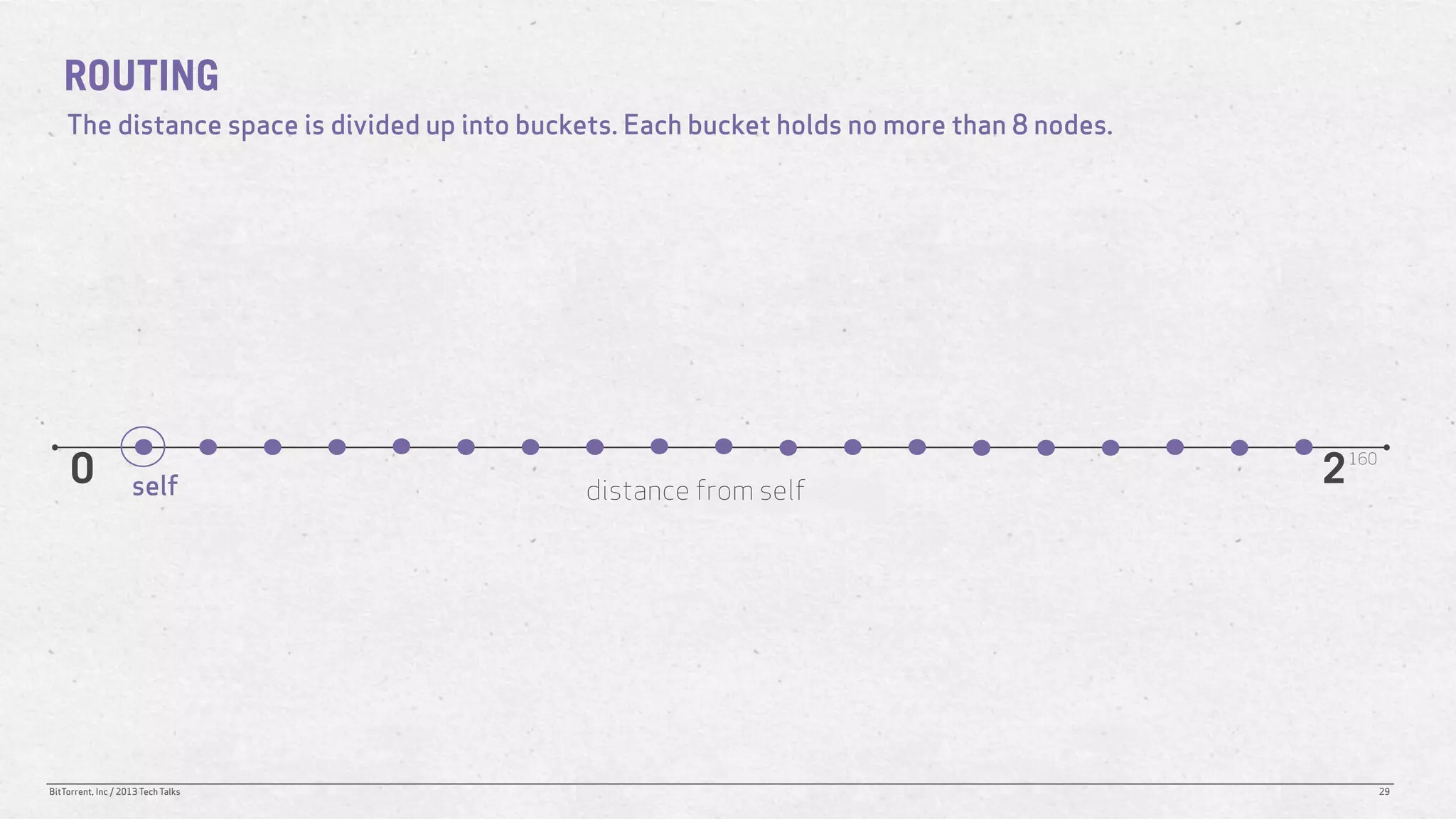
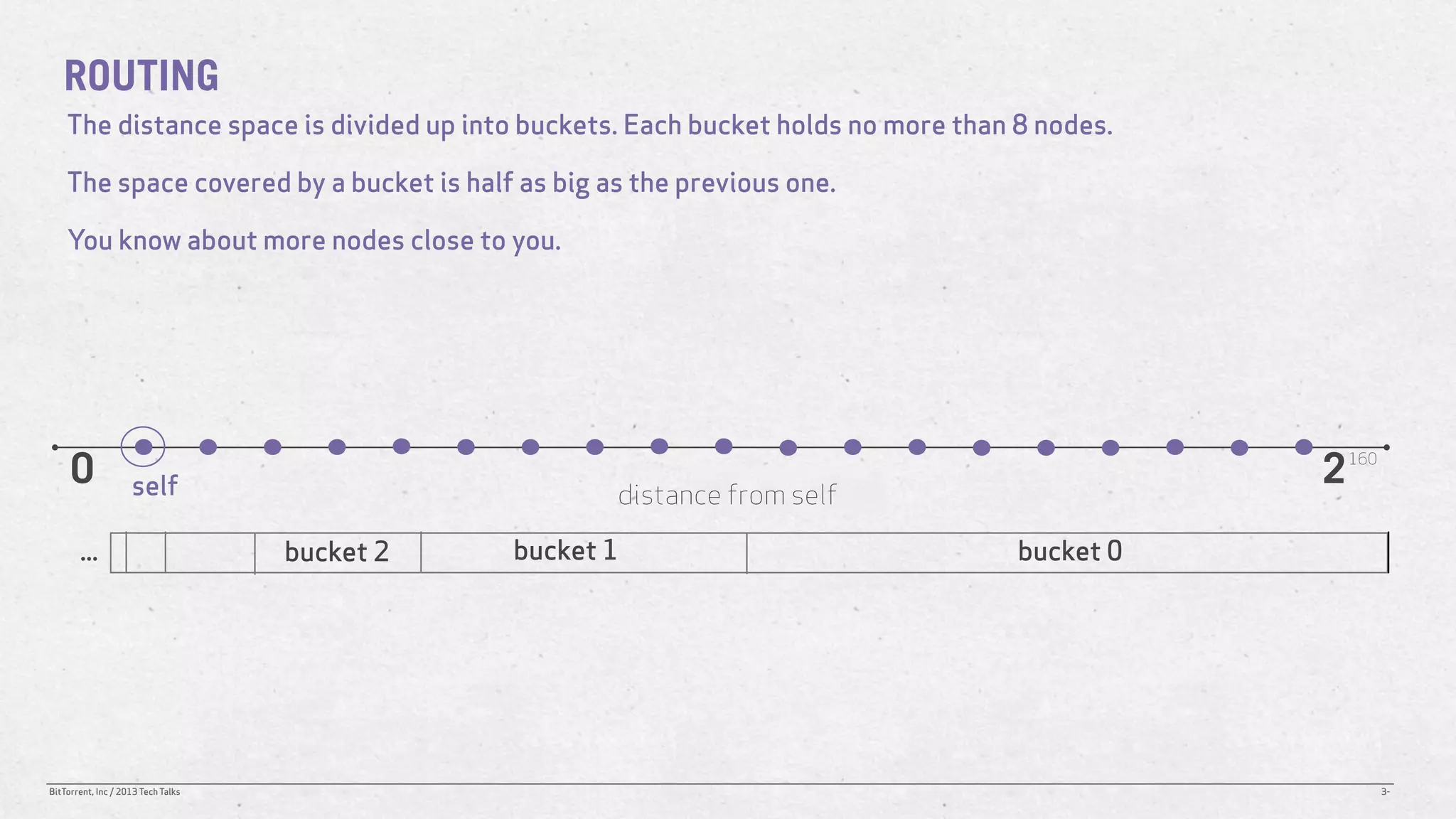
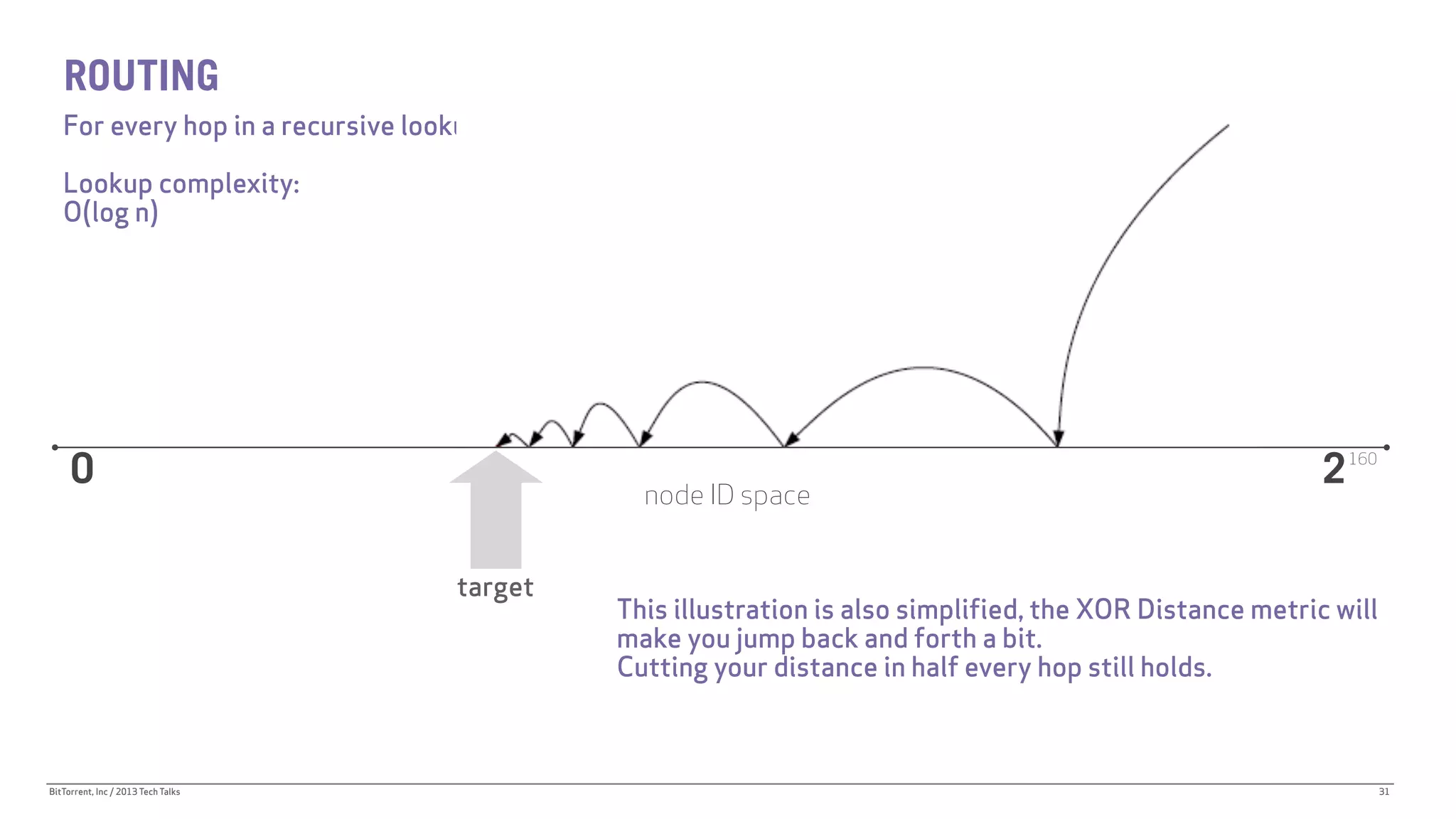
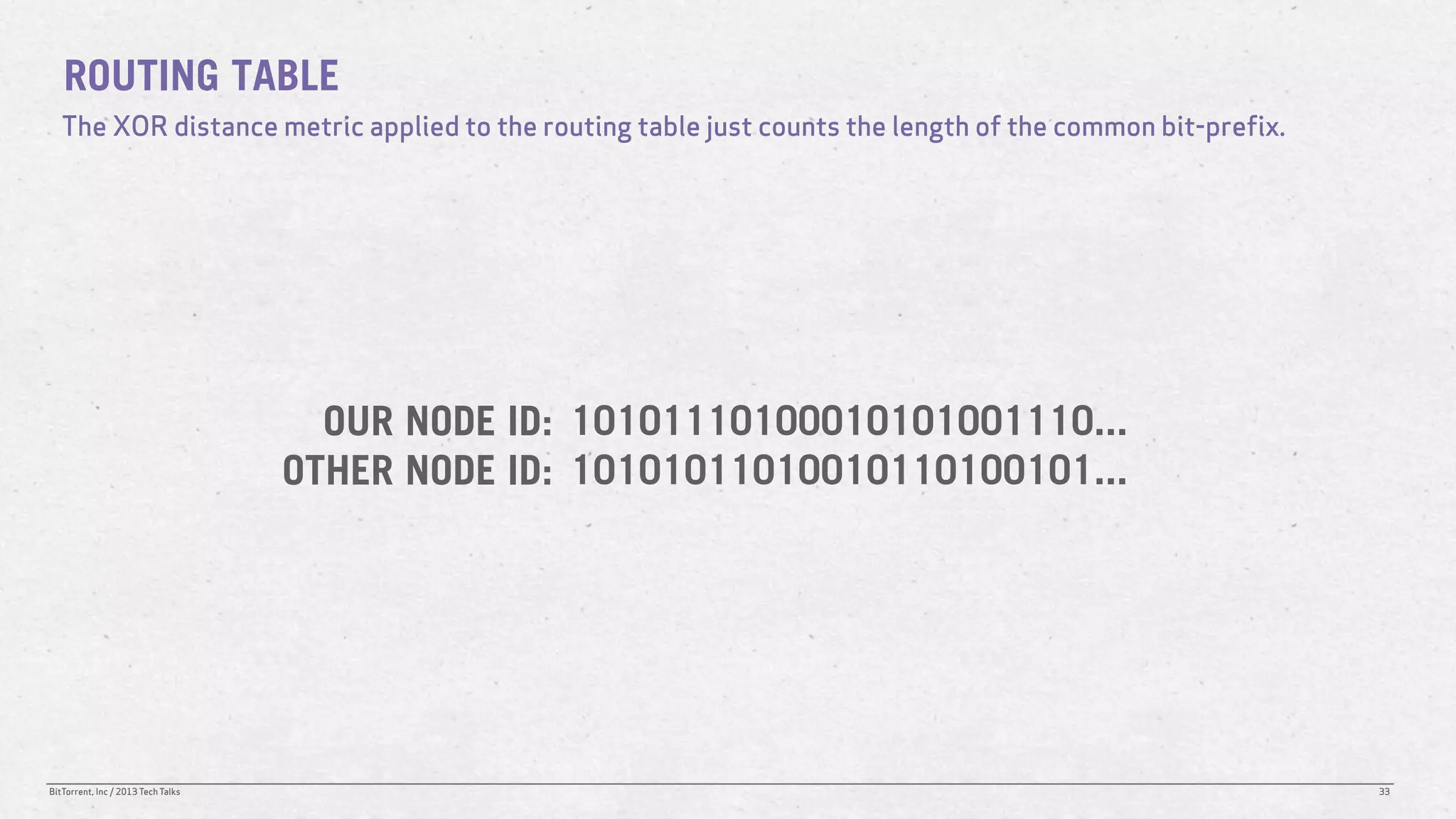
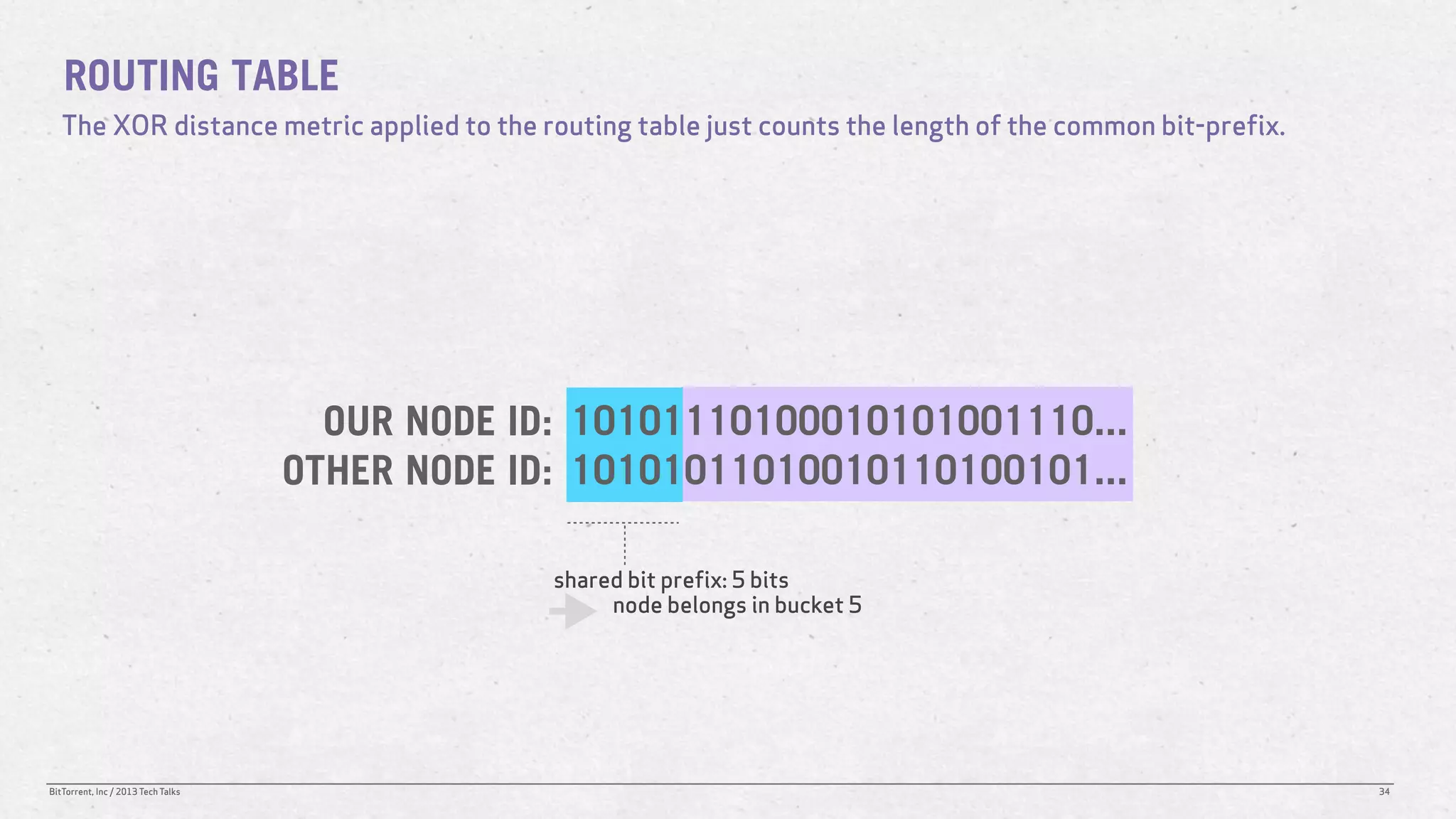
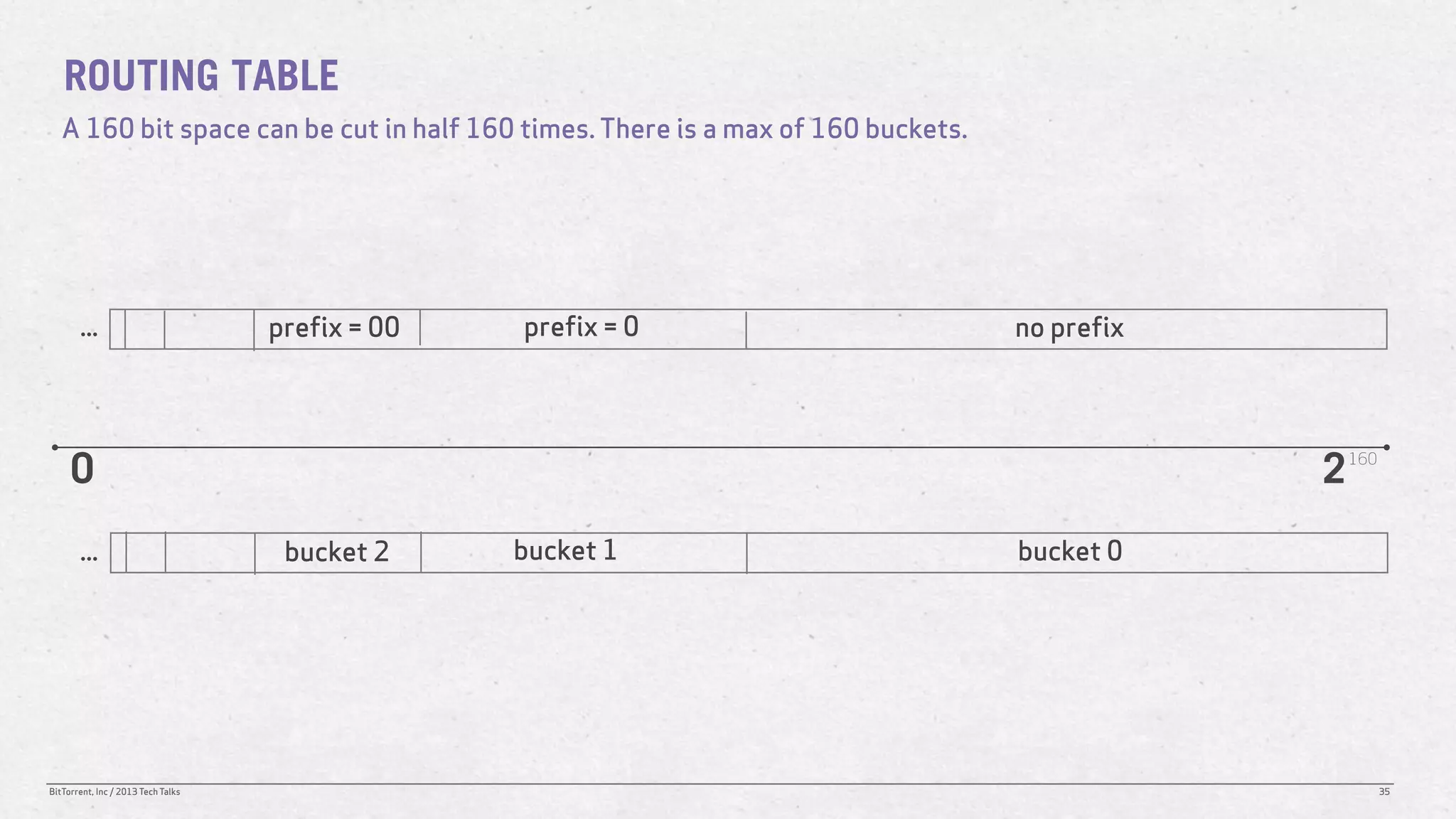
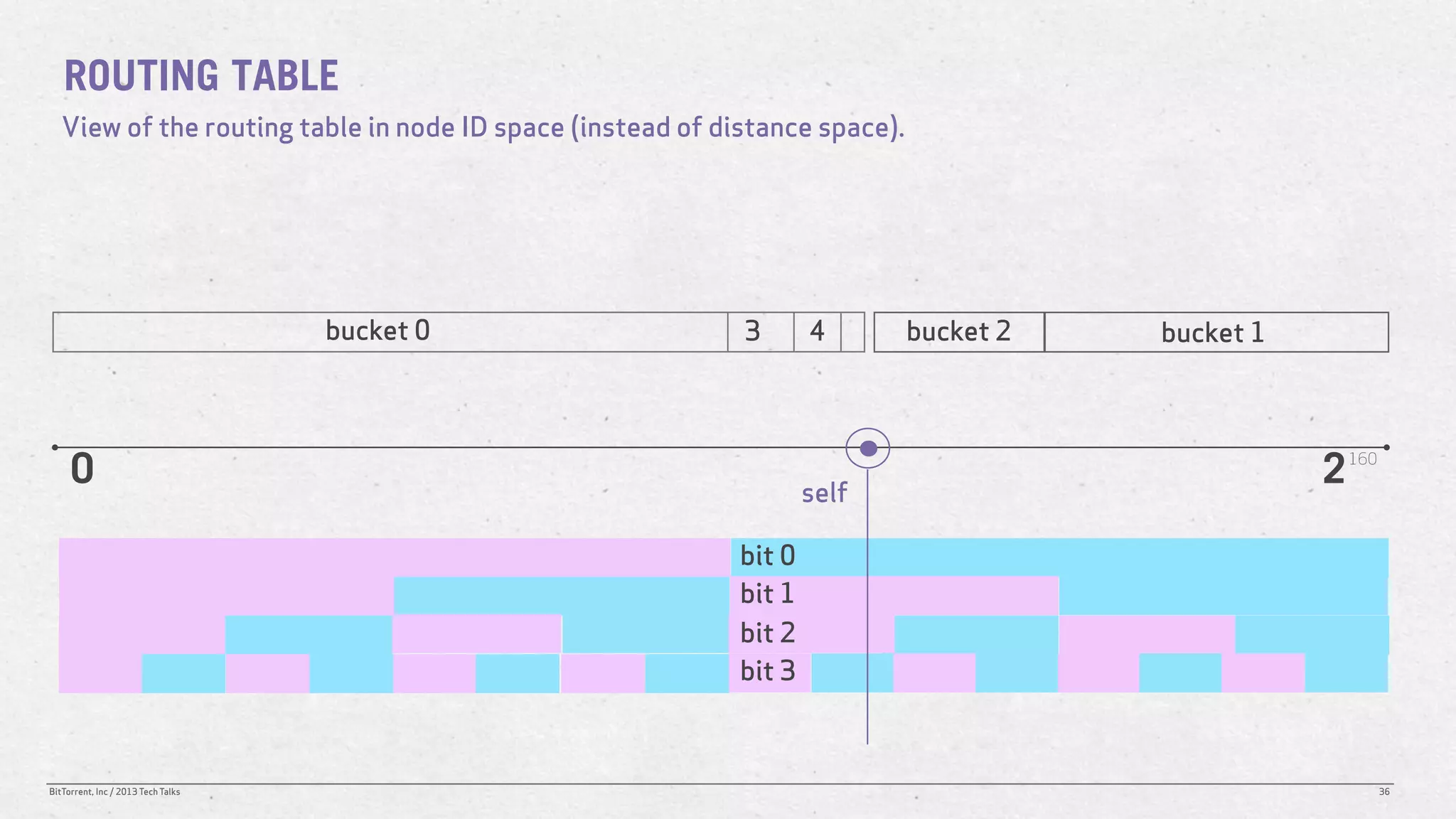
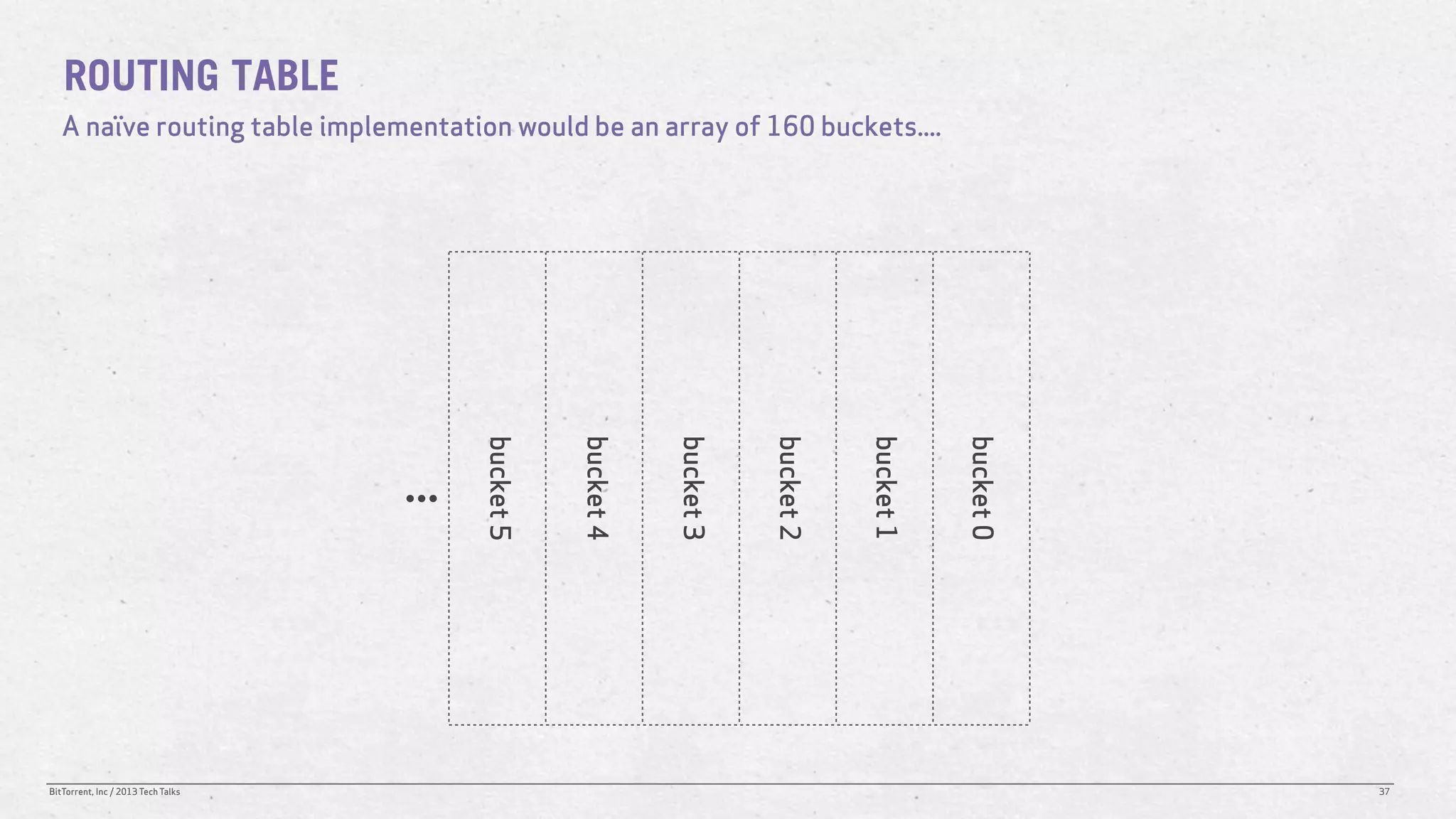
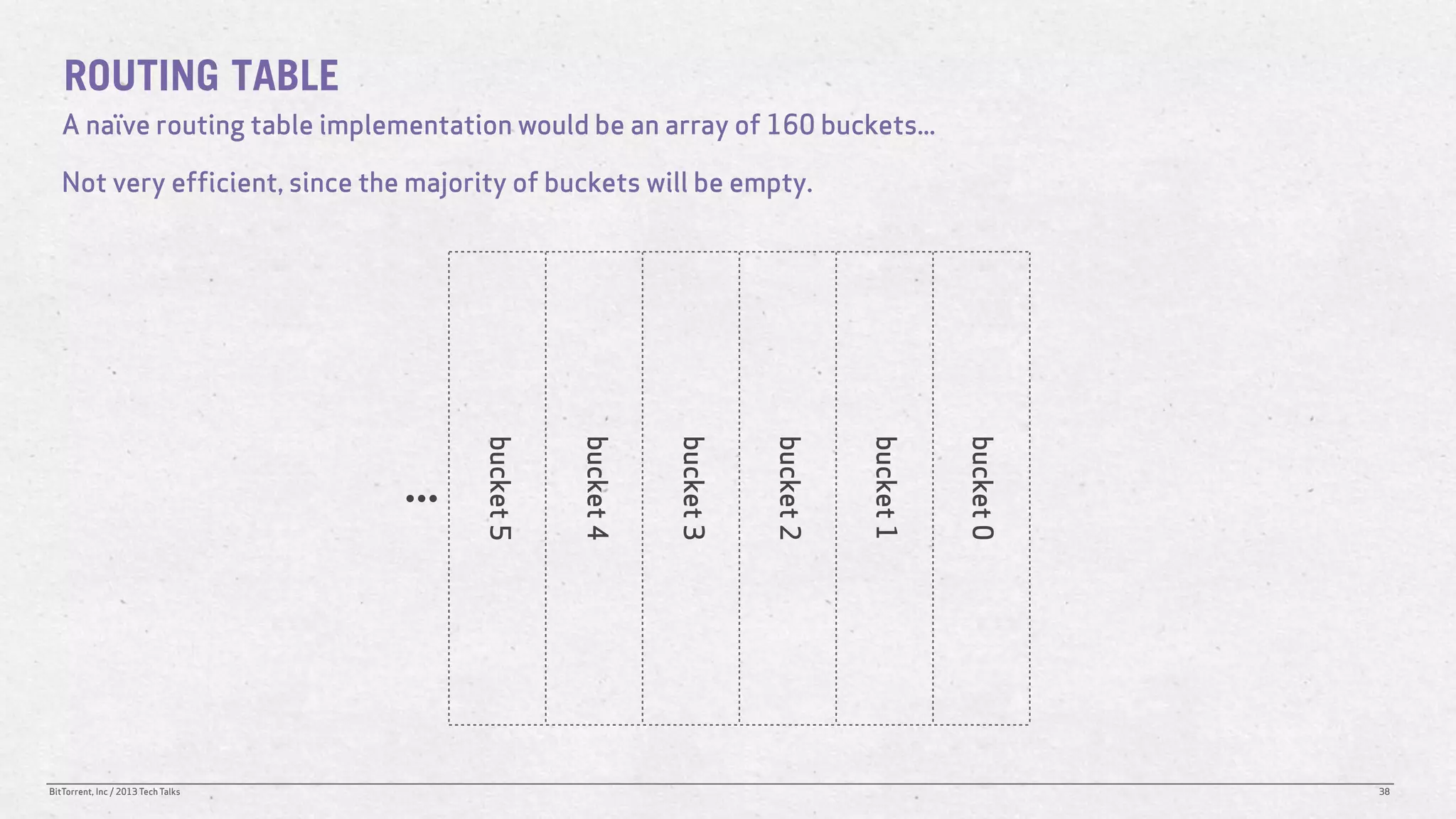
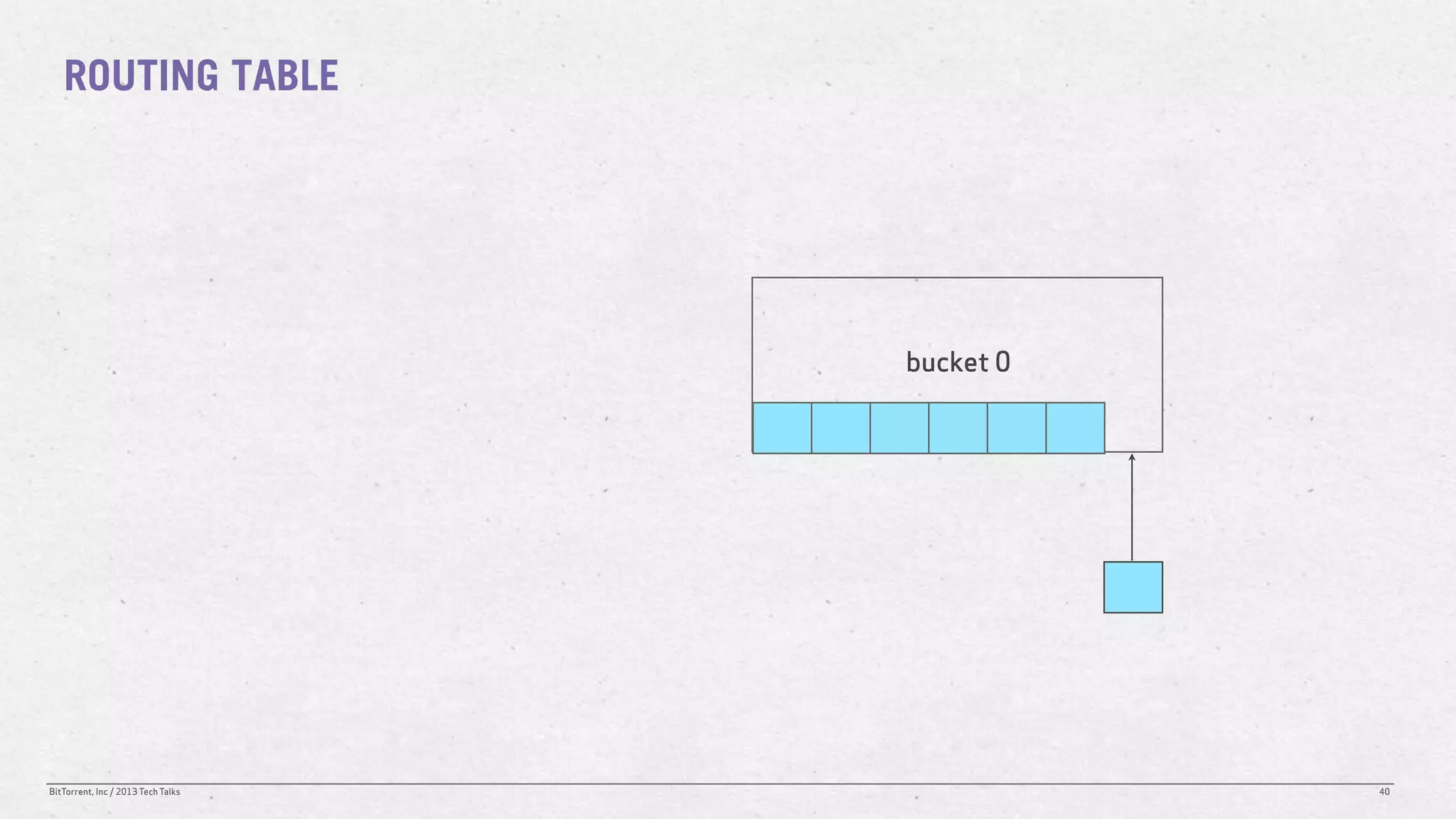
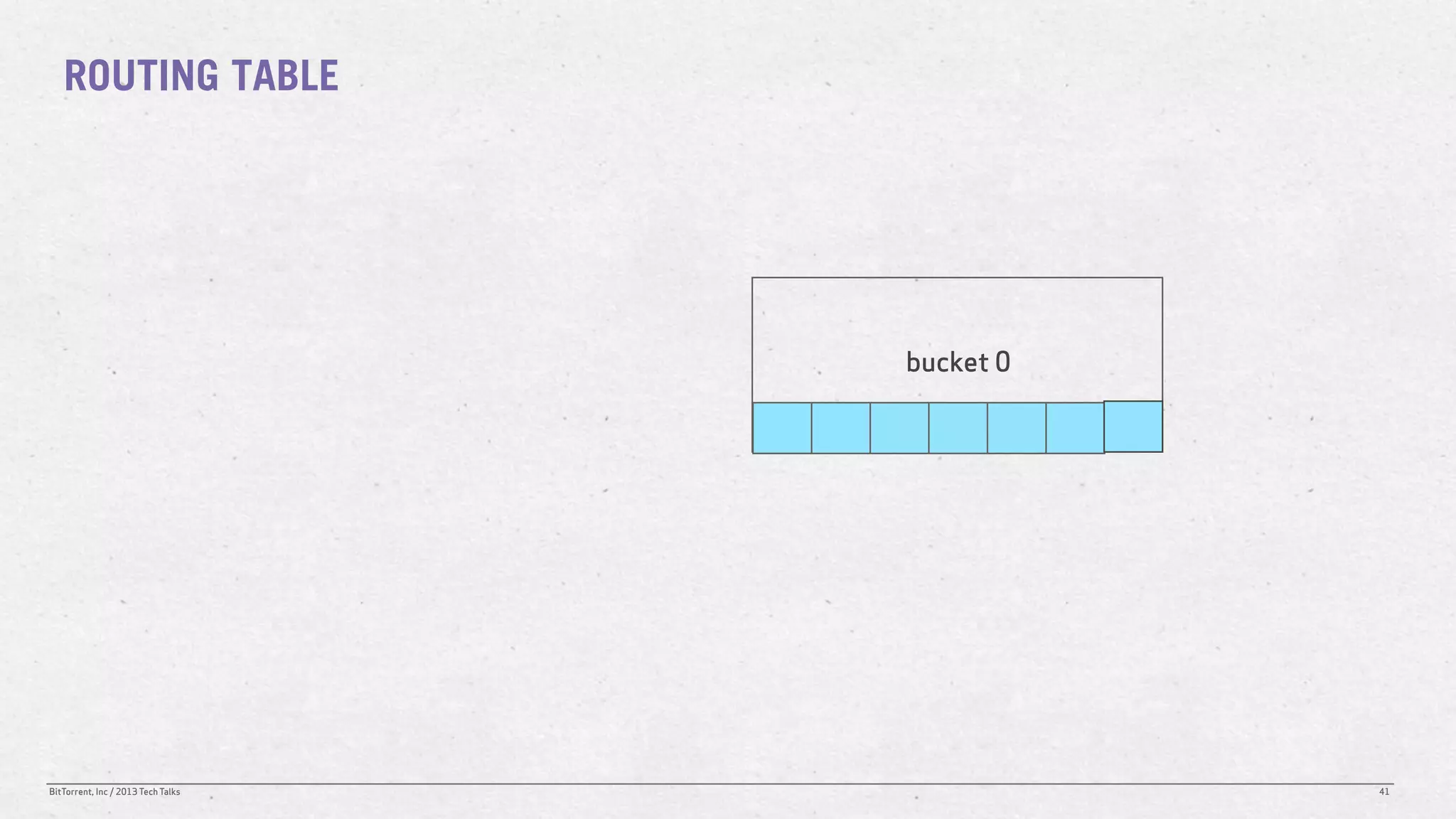
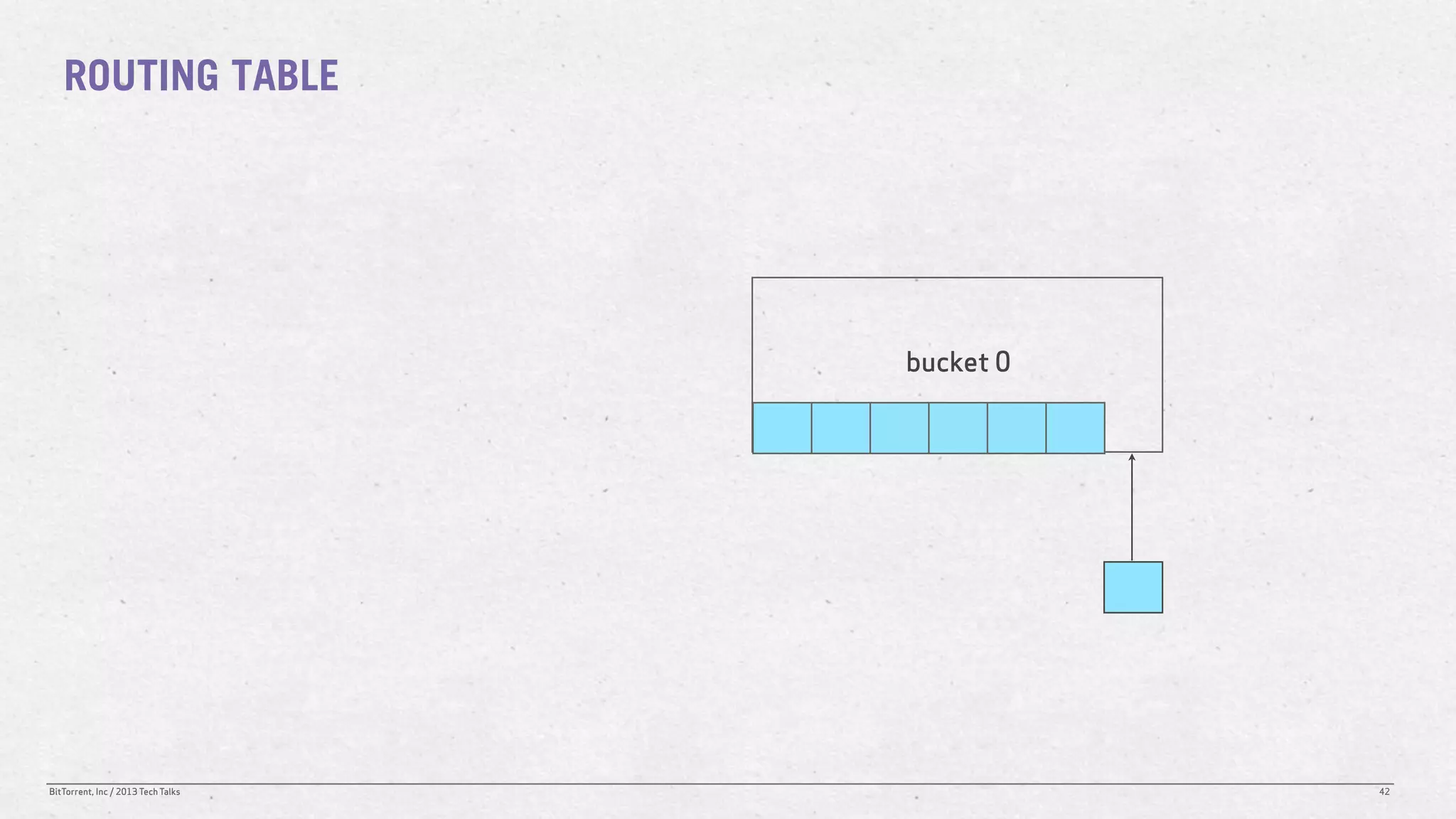
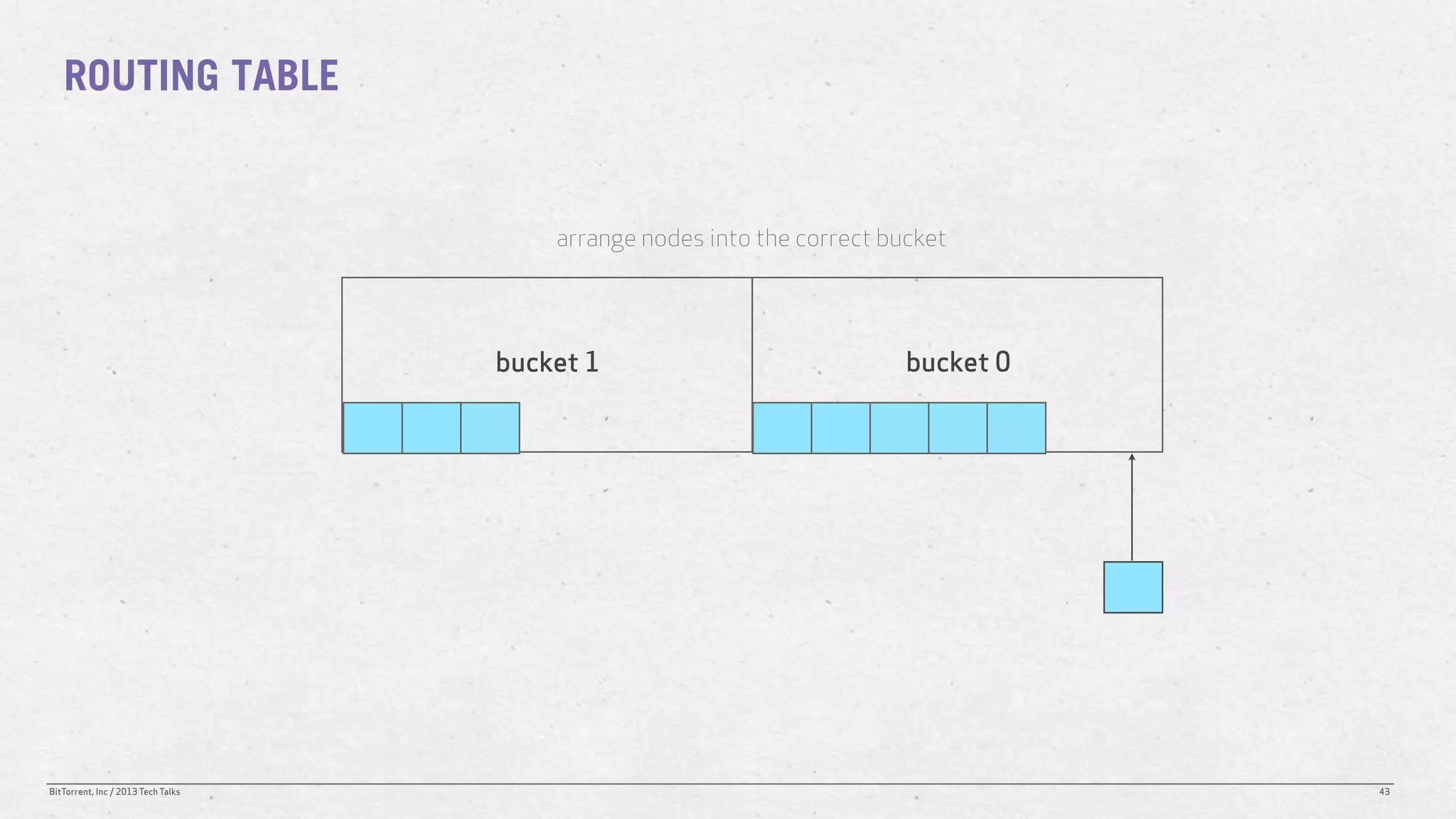
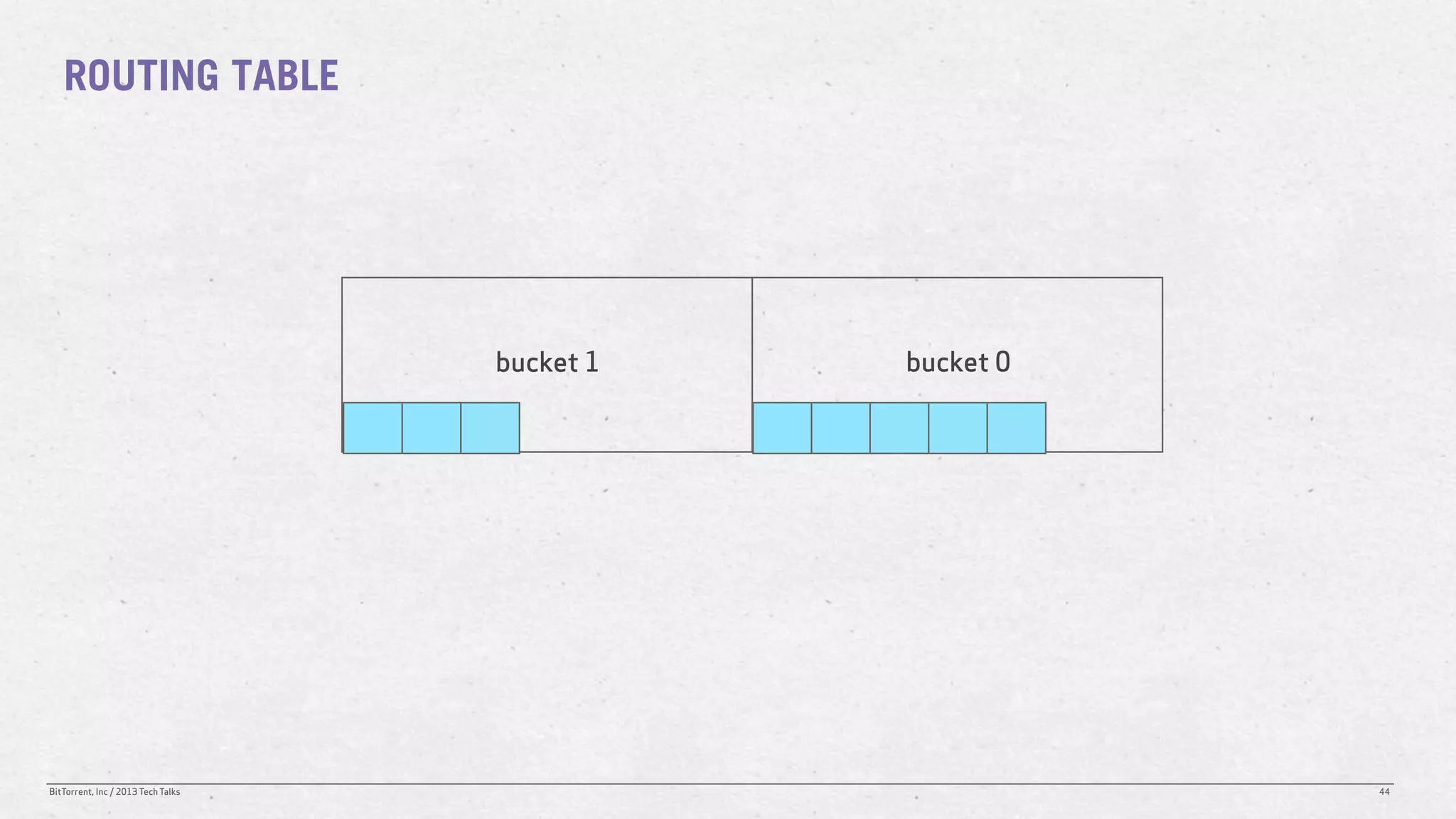
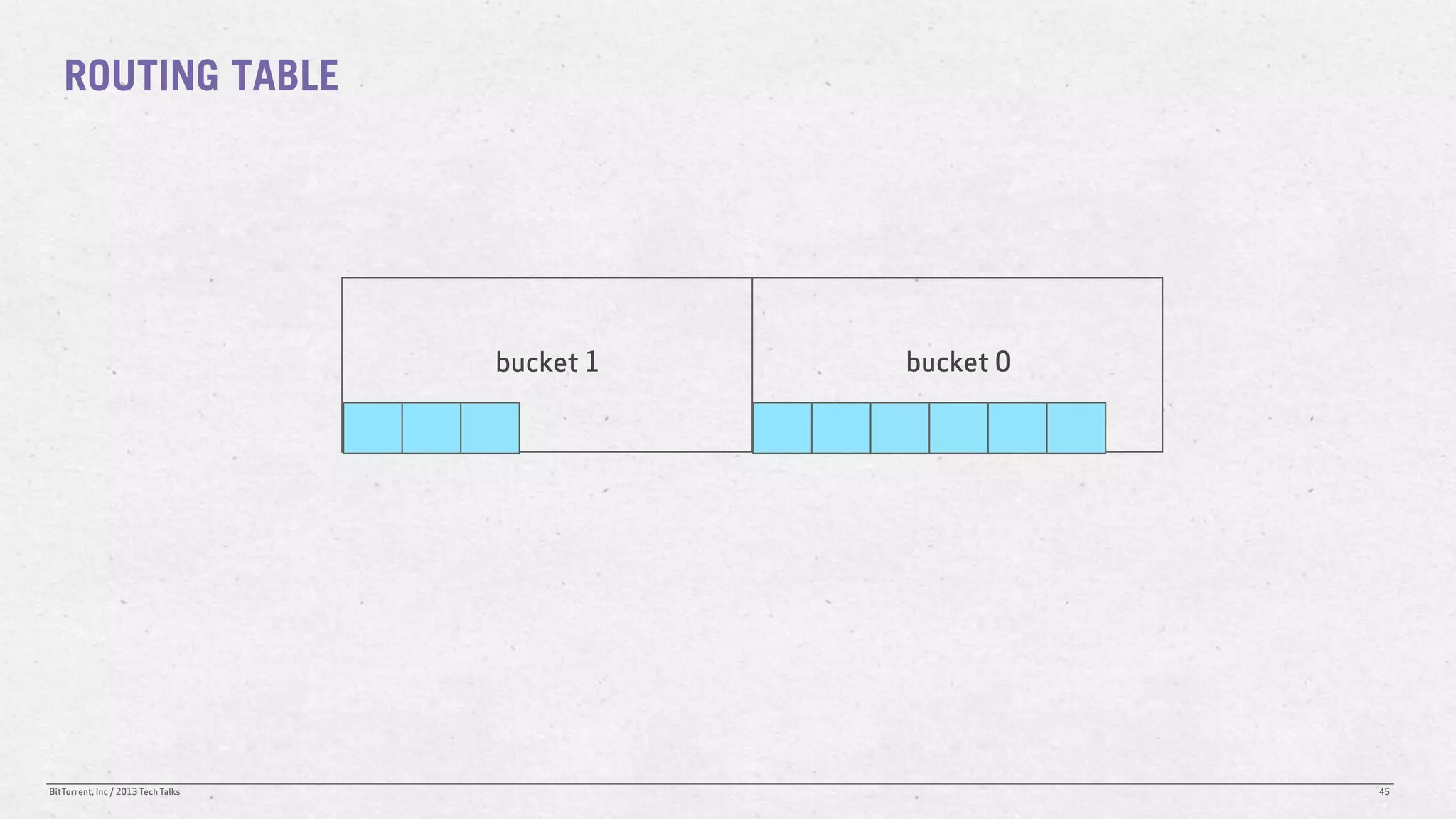
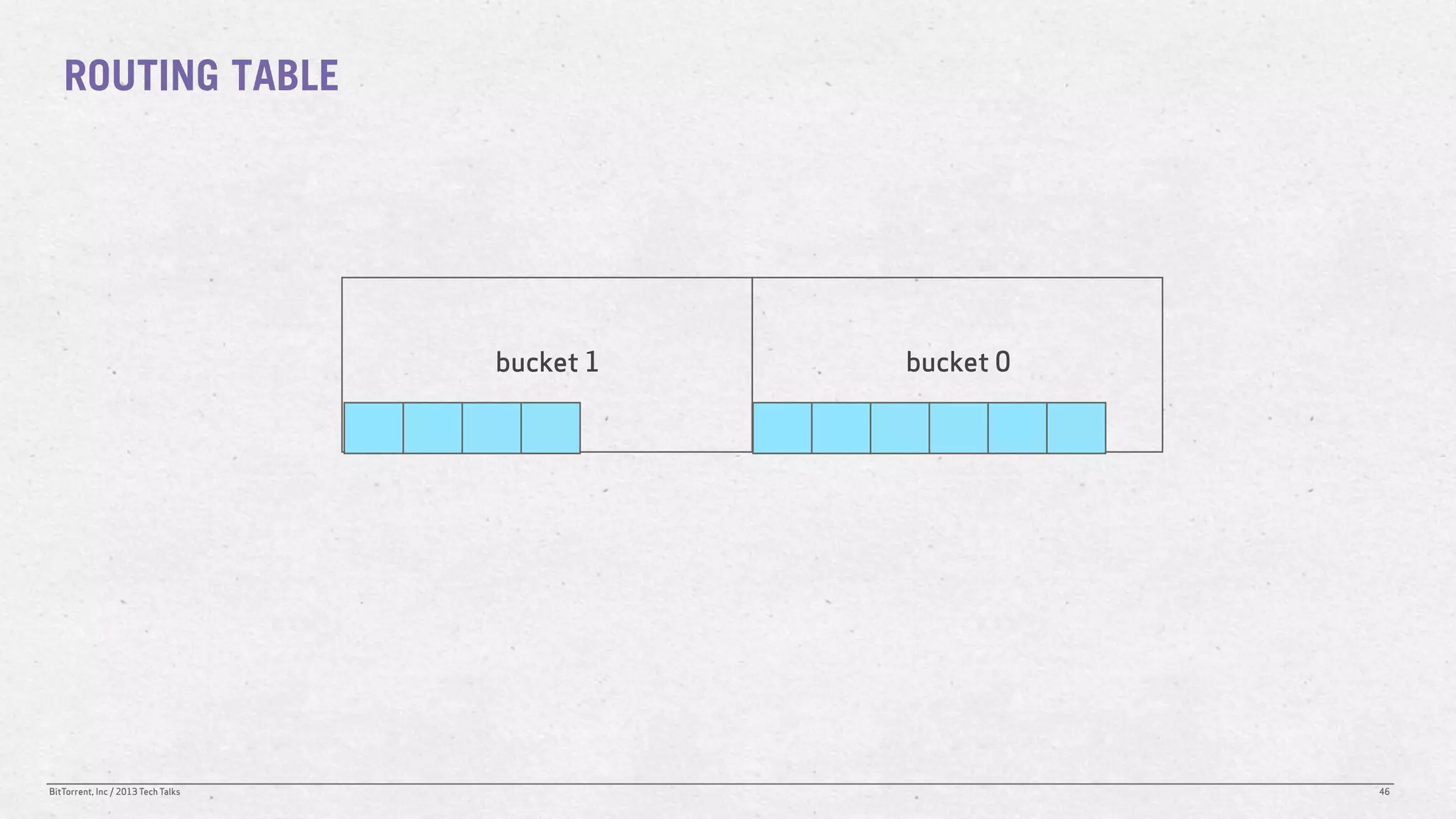
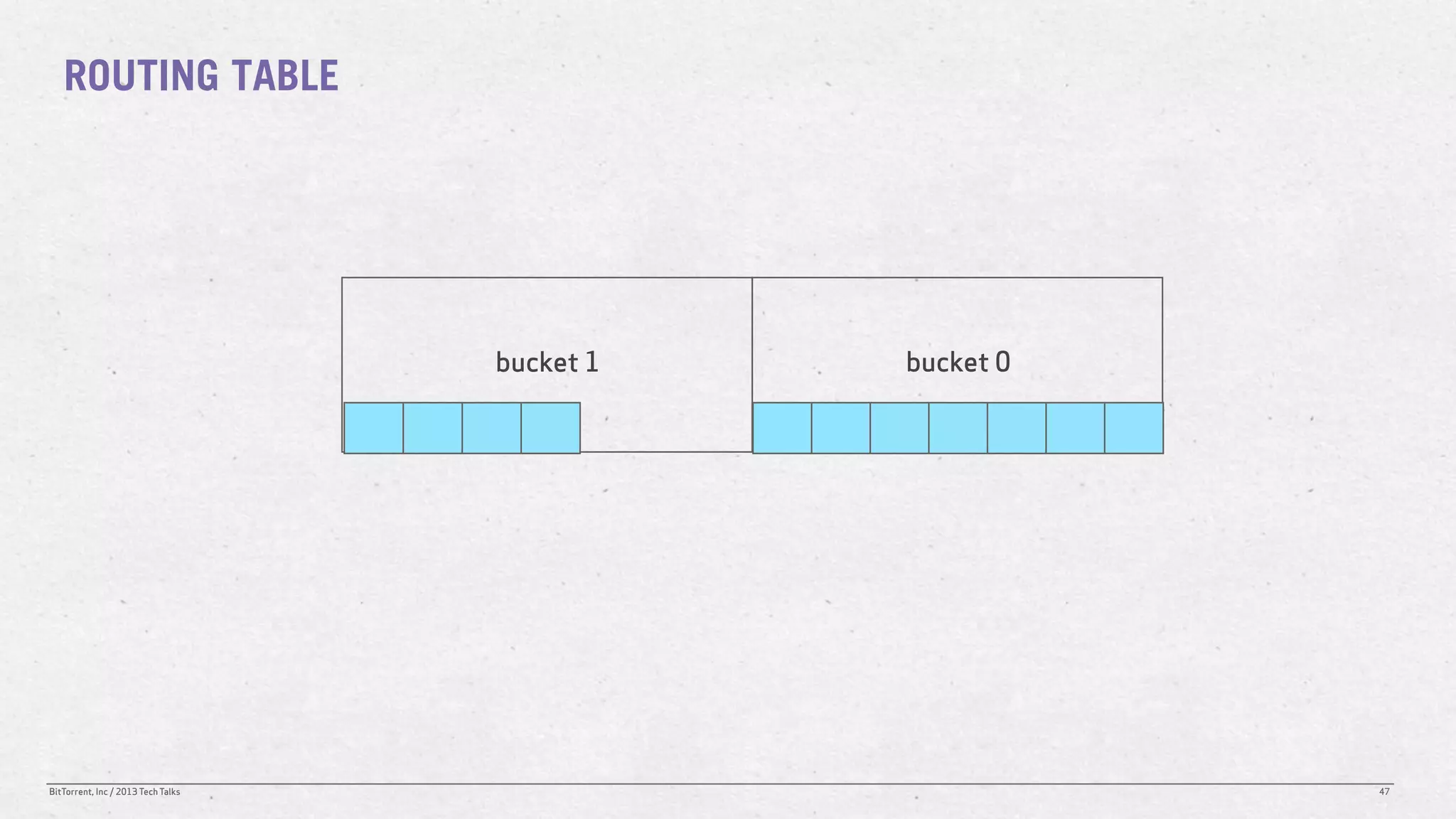
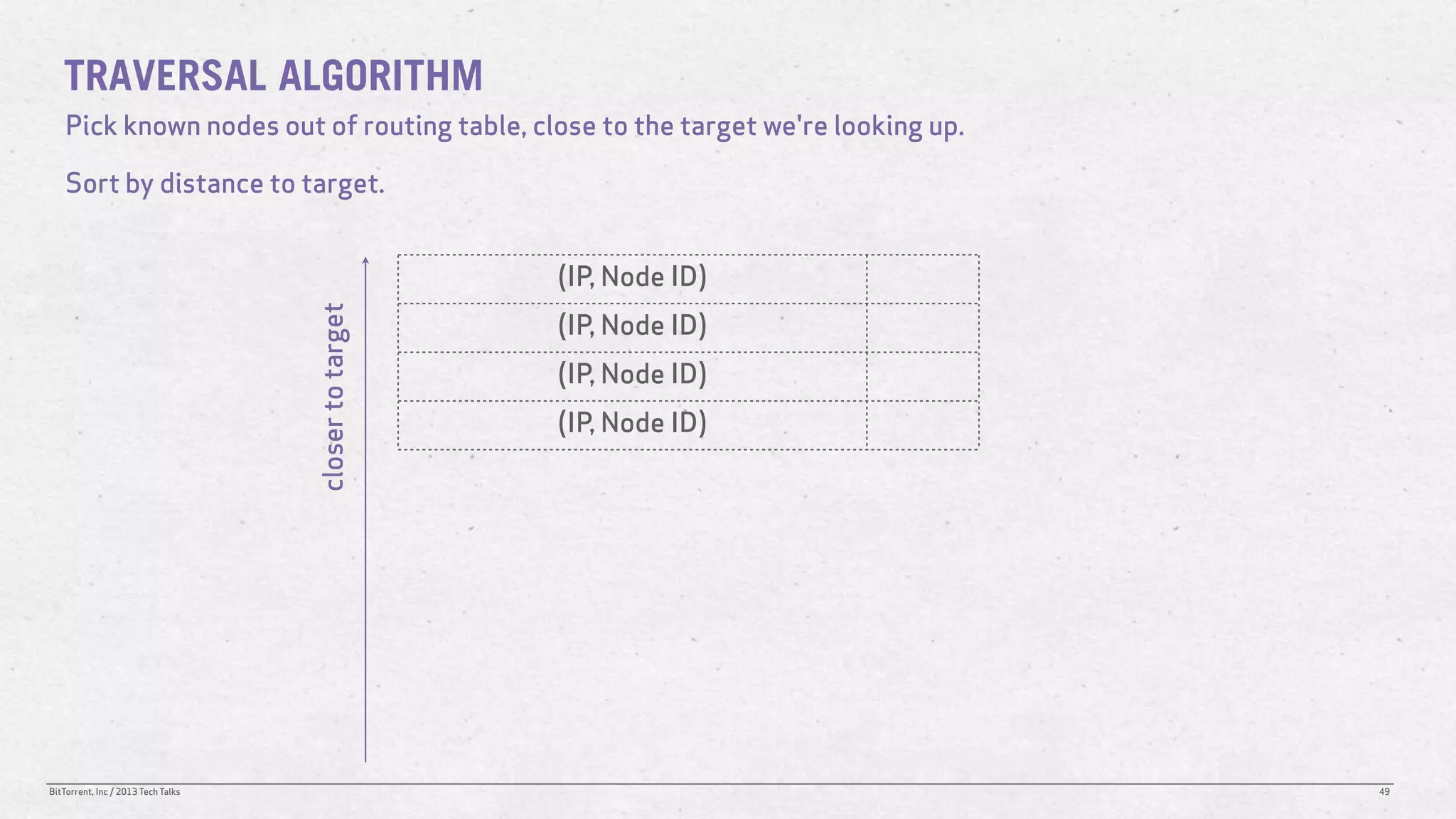
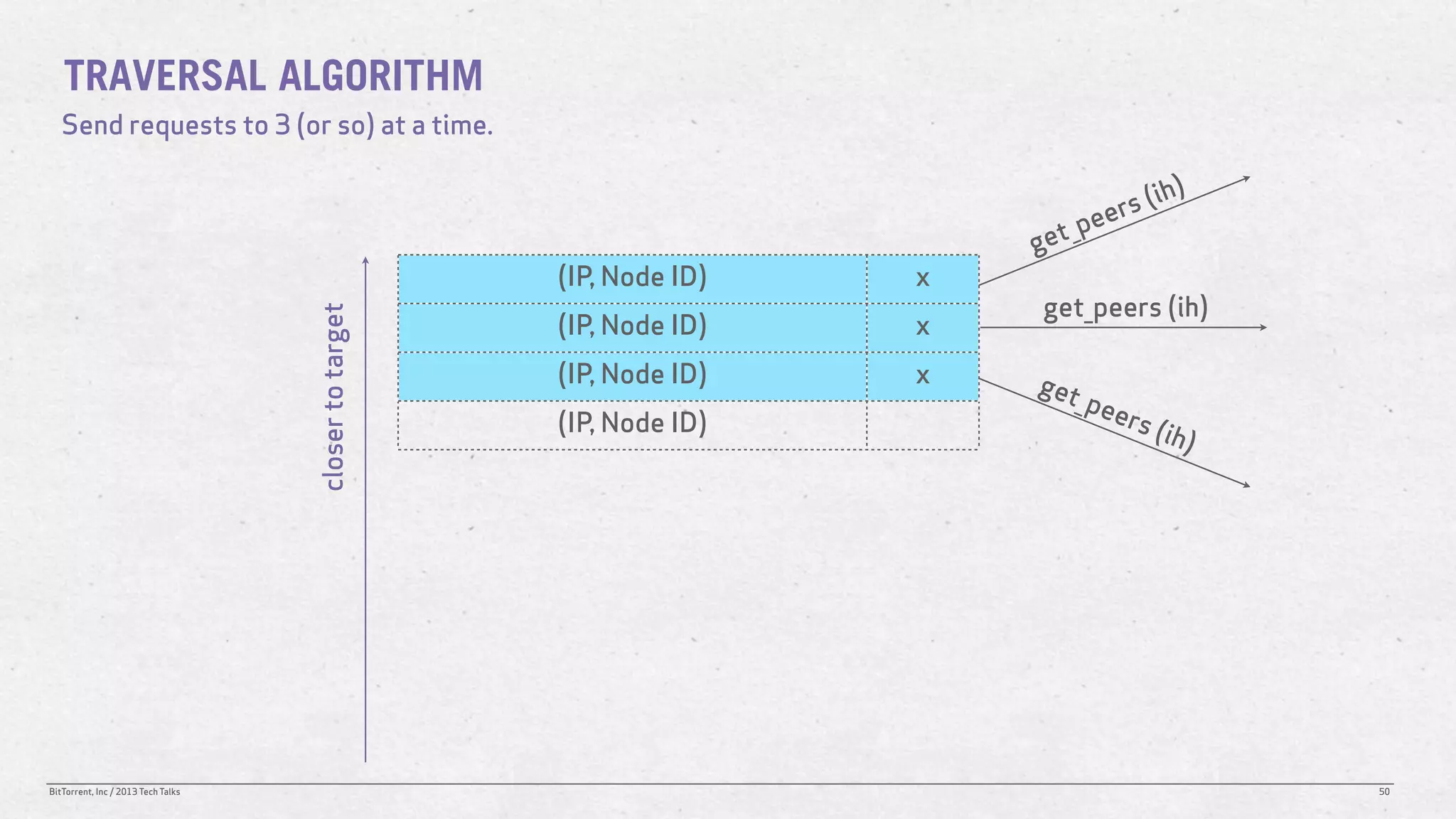
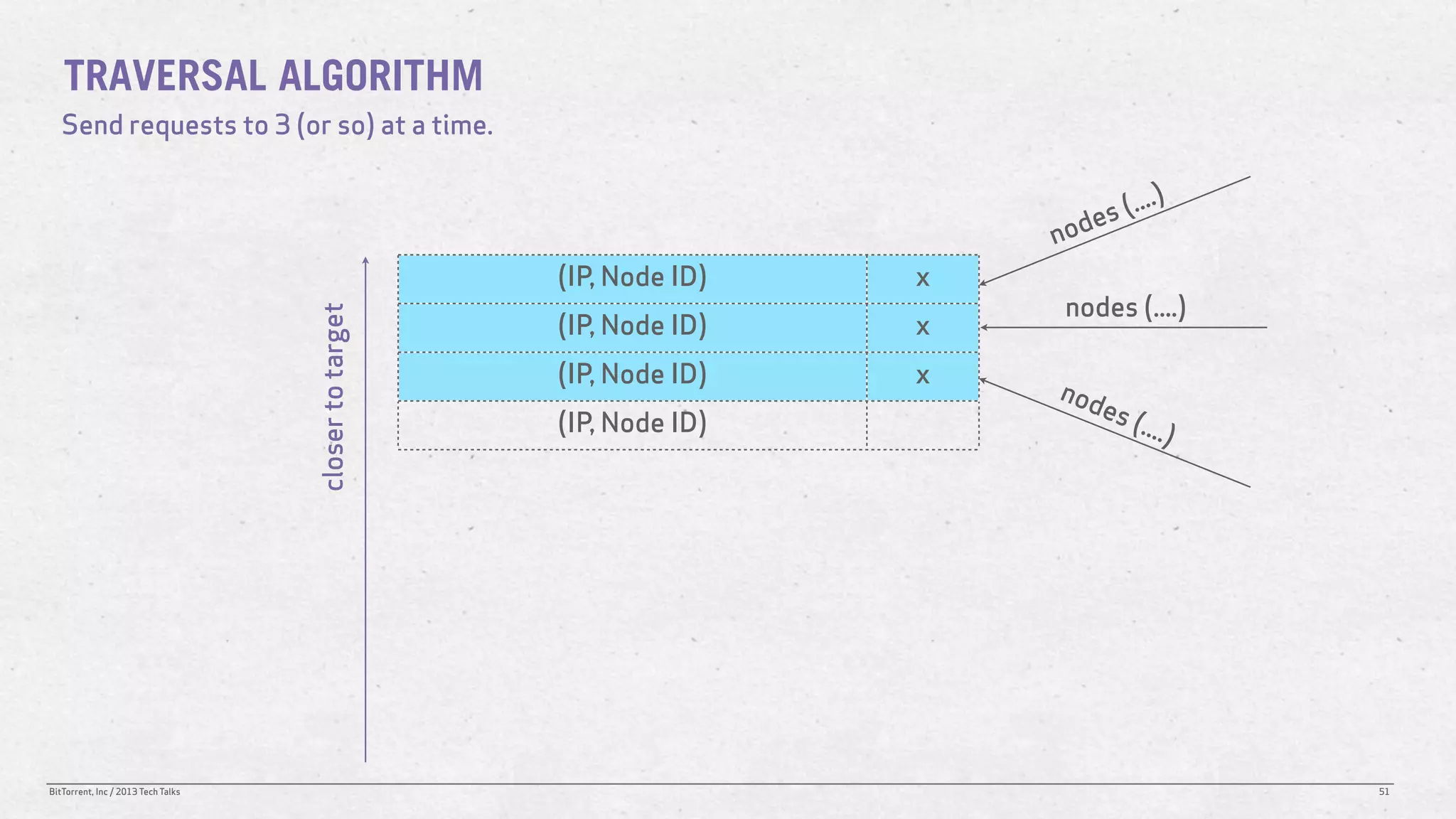
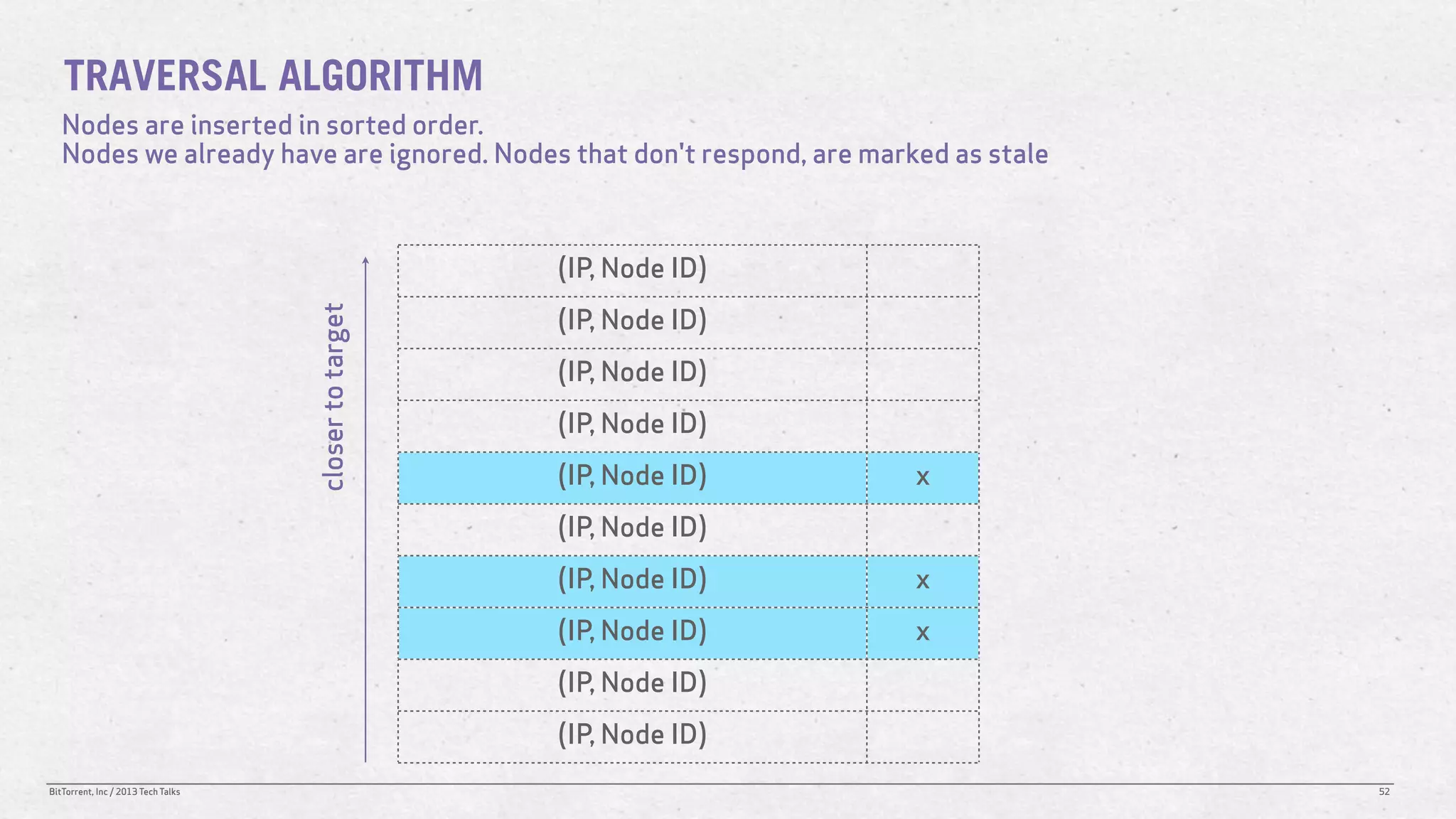
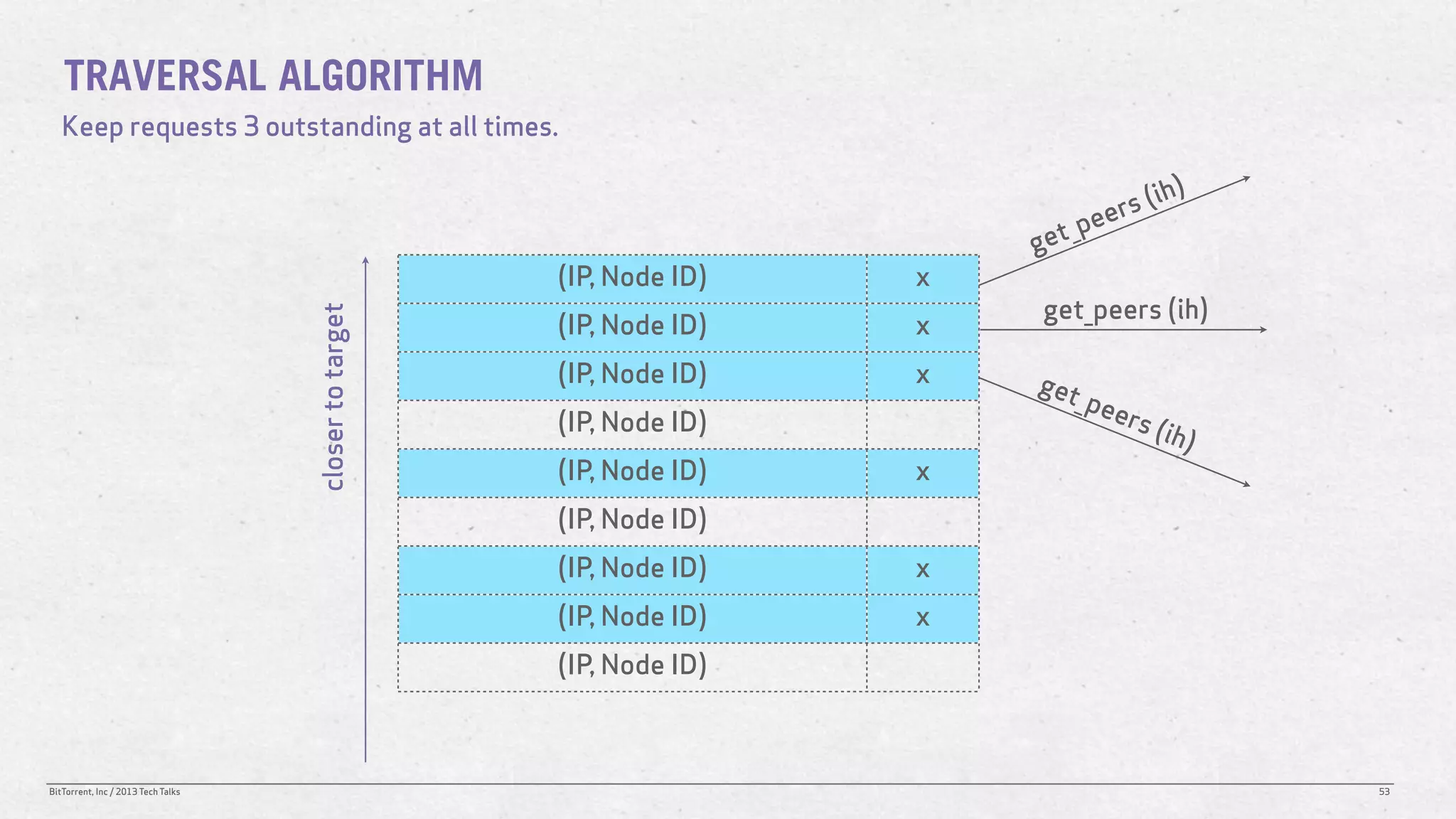
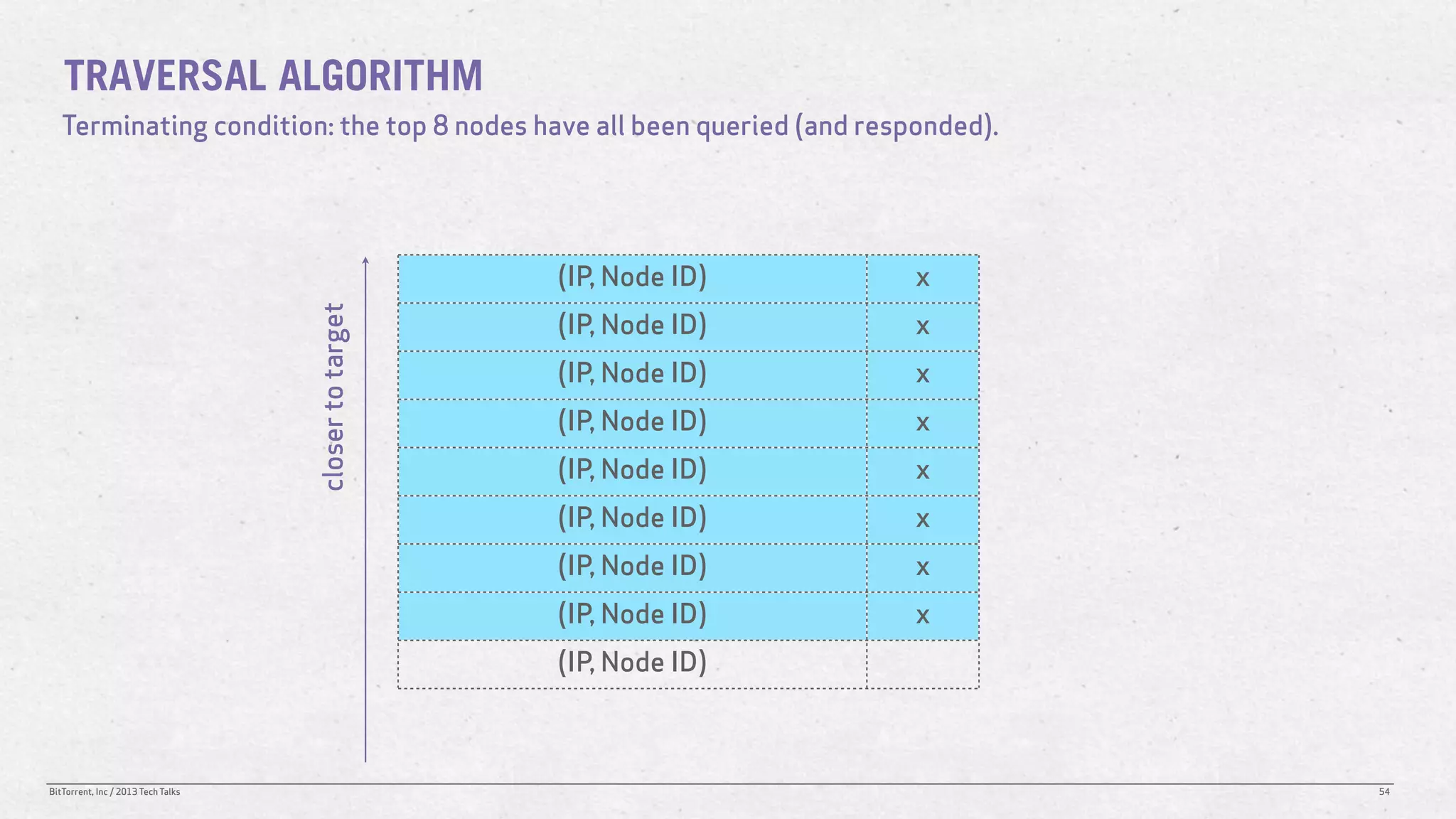
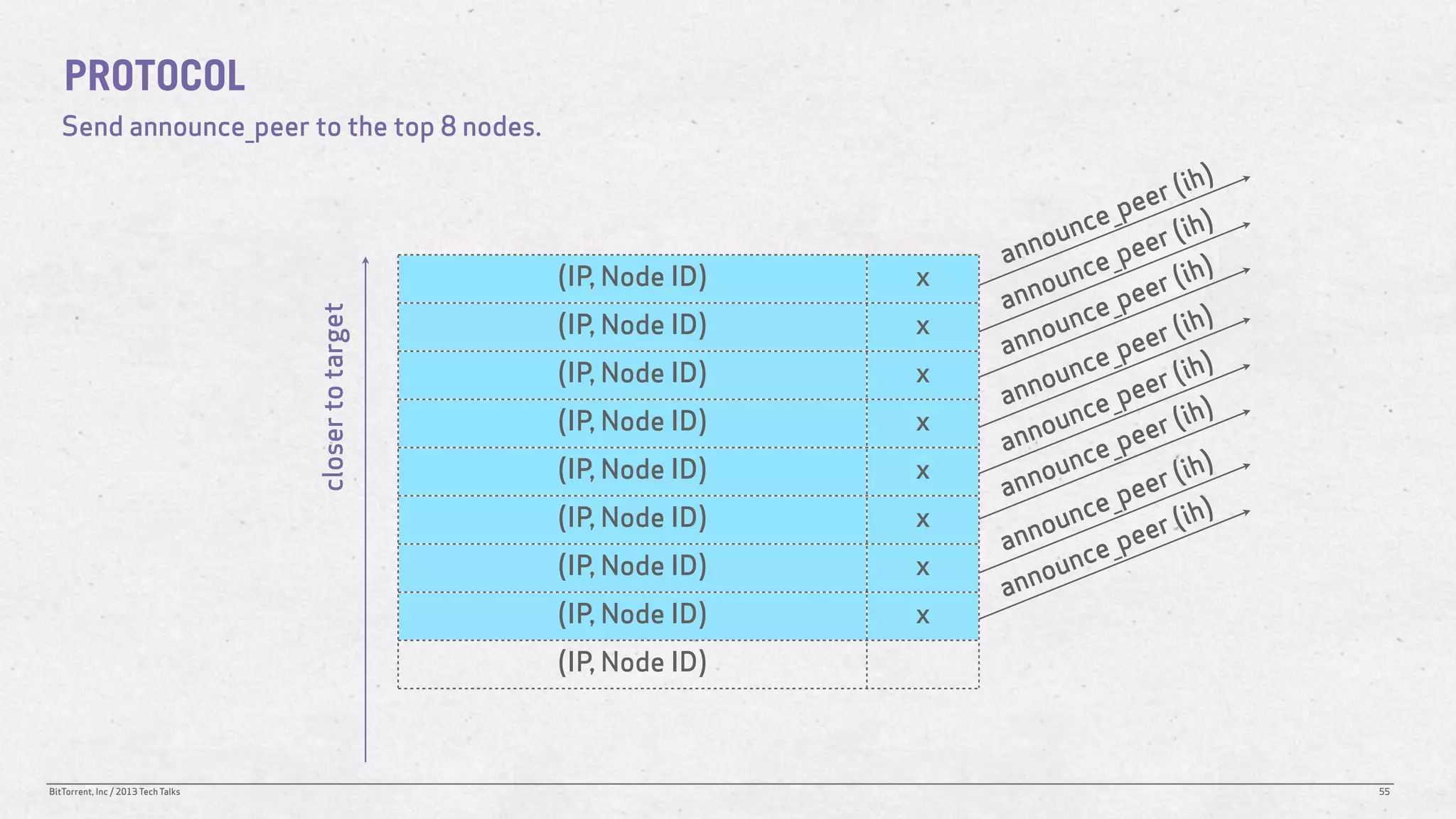
The document discusses the Distributed Hash Table (DHT) used in BitTorrent to facilitate peer discovery by managing how nodes communicate and share information within the network. It outlines protocols for node messaging, routing, and the structure of their lookup process, emphasizing the XOR distance metric for node organization and efficient routing. Additionally, it explains how nodes are grouped in buckets for optimized querying and retrieval of peers on different swarms.