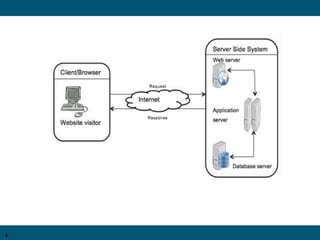
Web applications are increasingly targeted by cyber criminals. This document proposes solutions to common web application attacks like SQL injection (SQLIA) and cross-site request forgery (CSRF). It suggests encrypting sensitive data to prevent SQLIA and using secret cross-site request forgery tokens for each request to block unauthorized form submissions and prevent CSRF. An example e-commerce application called Instant Media is presented to demonstrate these vulnerabilities. The proposed solutions aim to enhance web security without additional overhead.