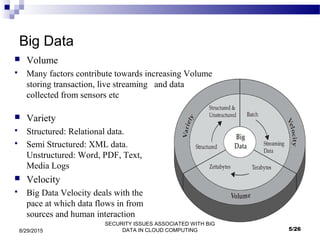
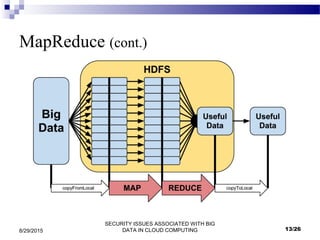
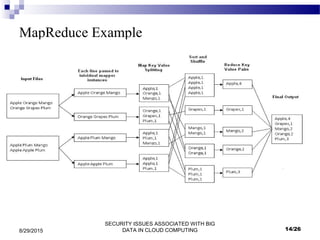
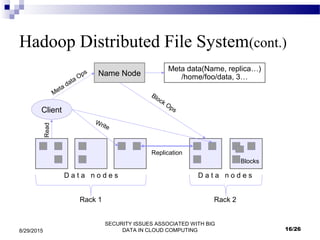
This document outlines security issues associated with big data in cloud computing. It begins with introductions to big data, cloud computing, and Hadoop. It describes how big data is related to cloud computing and discusses advantages and applications of big data. The document then discusses security issues at the network, authentication, and data levels. It proposes several approaches to address these security issues, such as file encryption, network encryption, and access control. Finally, it discusses conclusions and opportunities for future work.