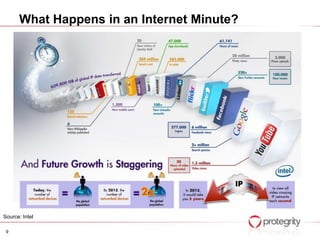
The document discusses how big data, increased data volumes, and weaknesses in security present a "perfect storm" risk scenario. It notes that while big data deployments are growing fast to realize business value, security is often not properly prioritized or implemented. This can allow breaches to go undetected. The document also outlines how data sources and volumes are expanding dramatically, while relevant security skills remain limited. Overall it argues that the confluence of these factors poses significant security challenges for organizations working with big data.