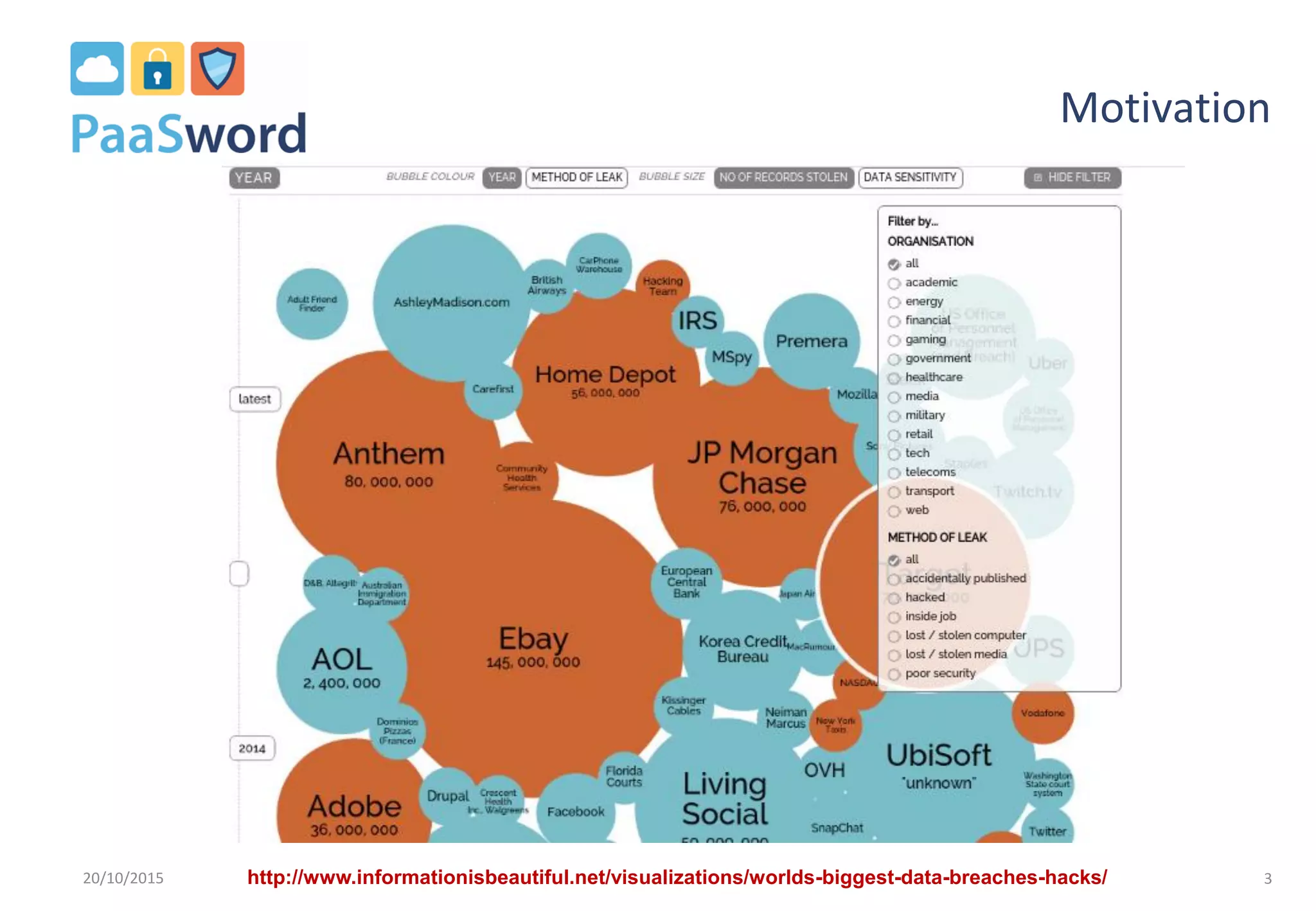
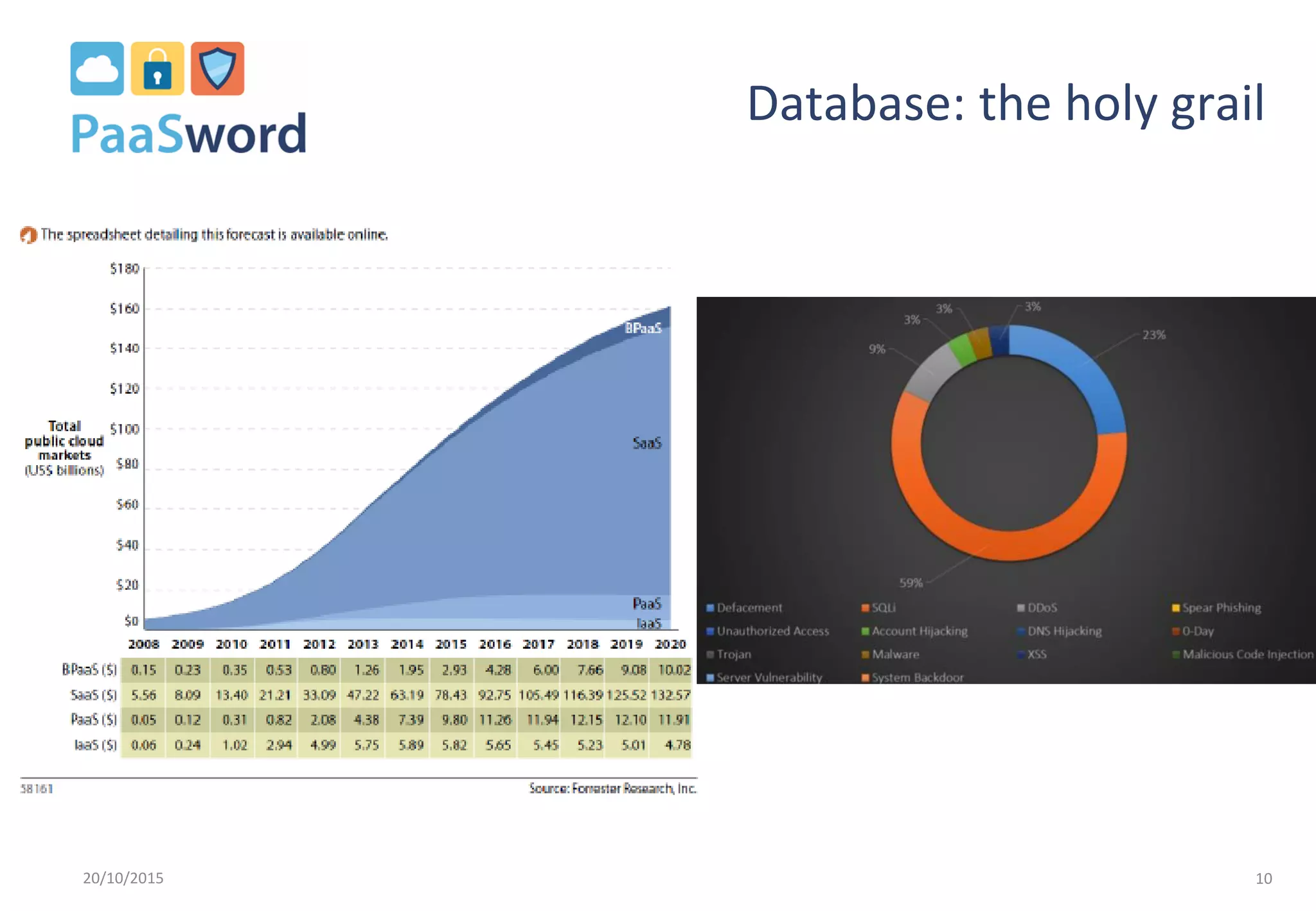
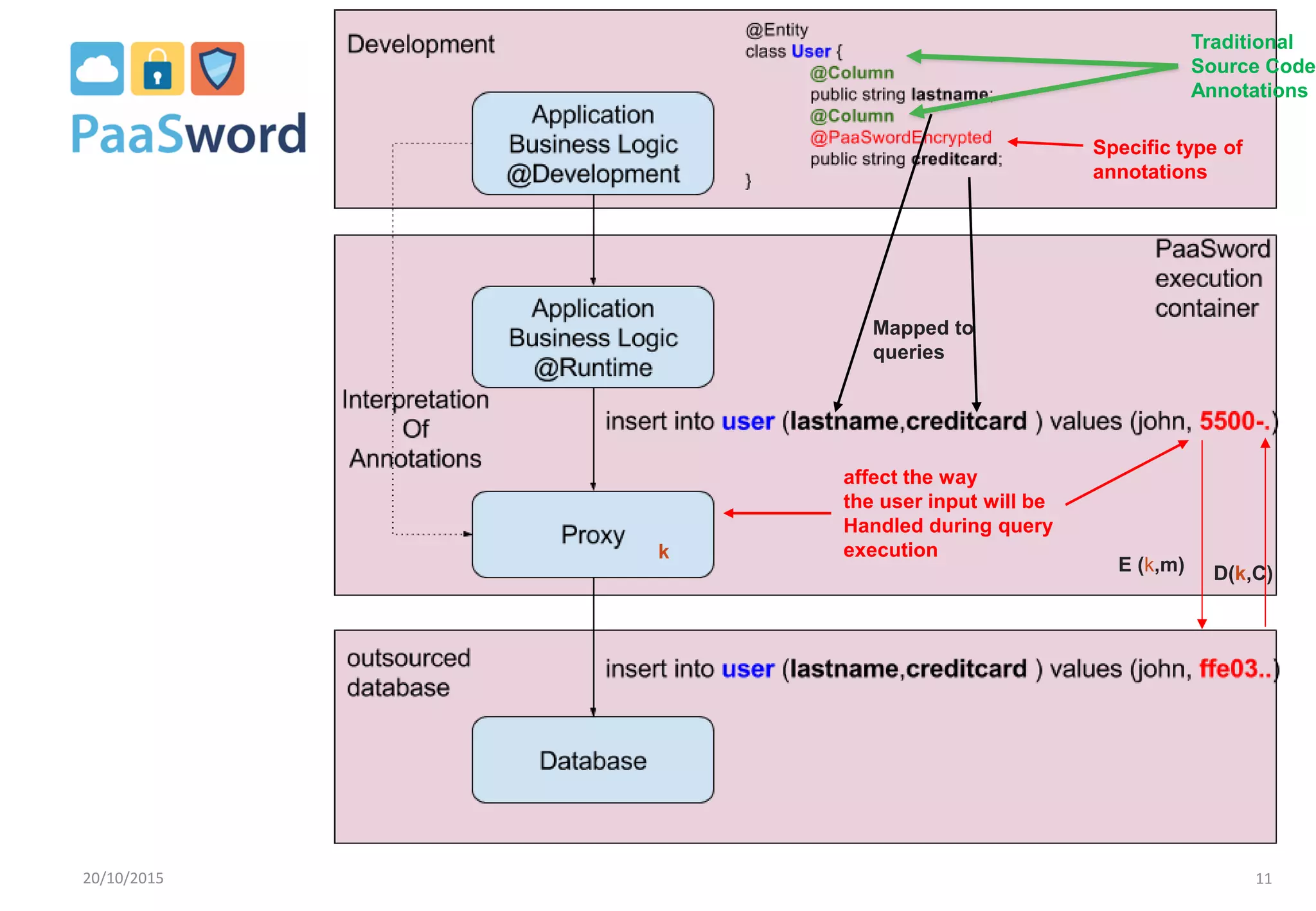
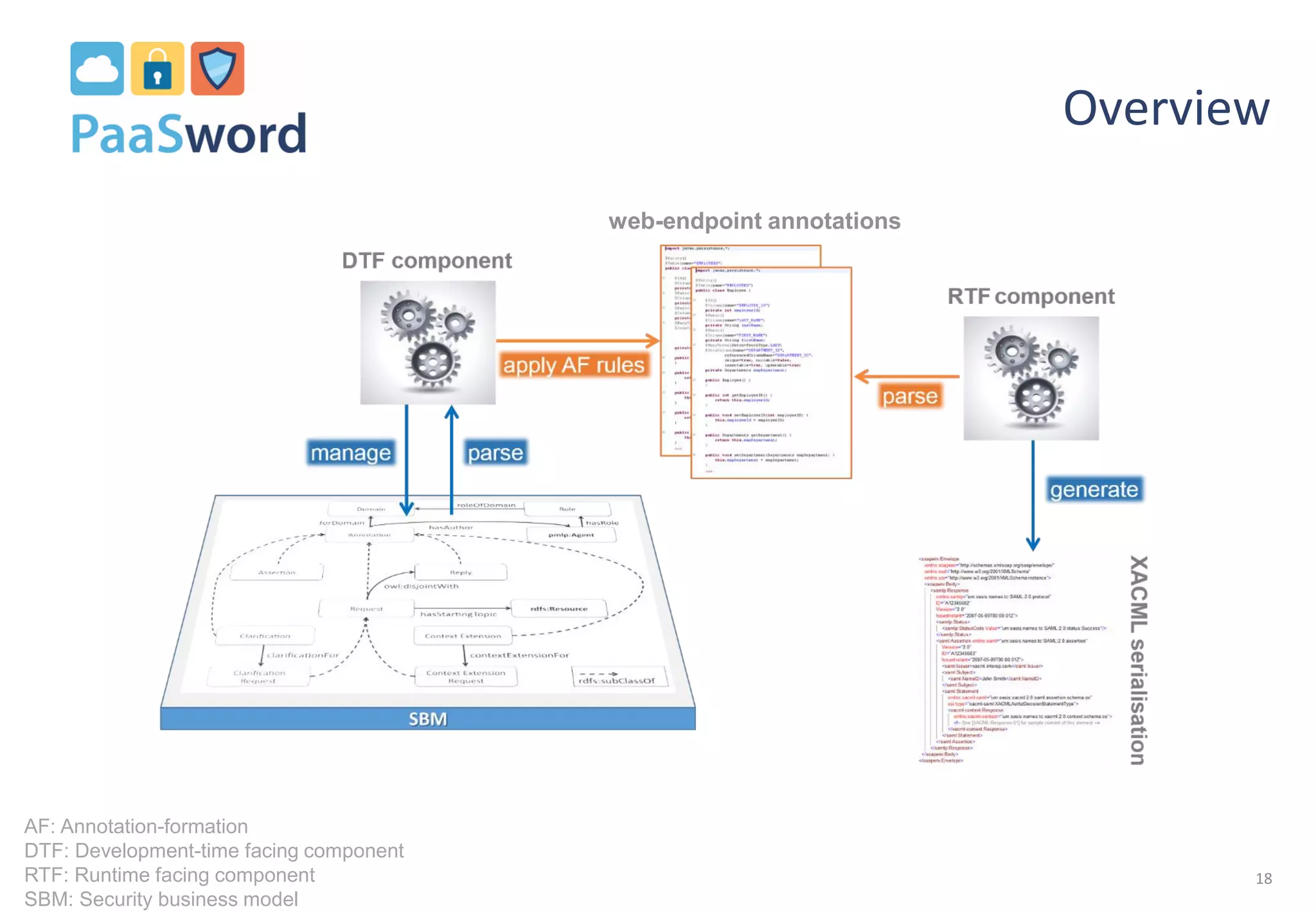
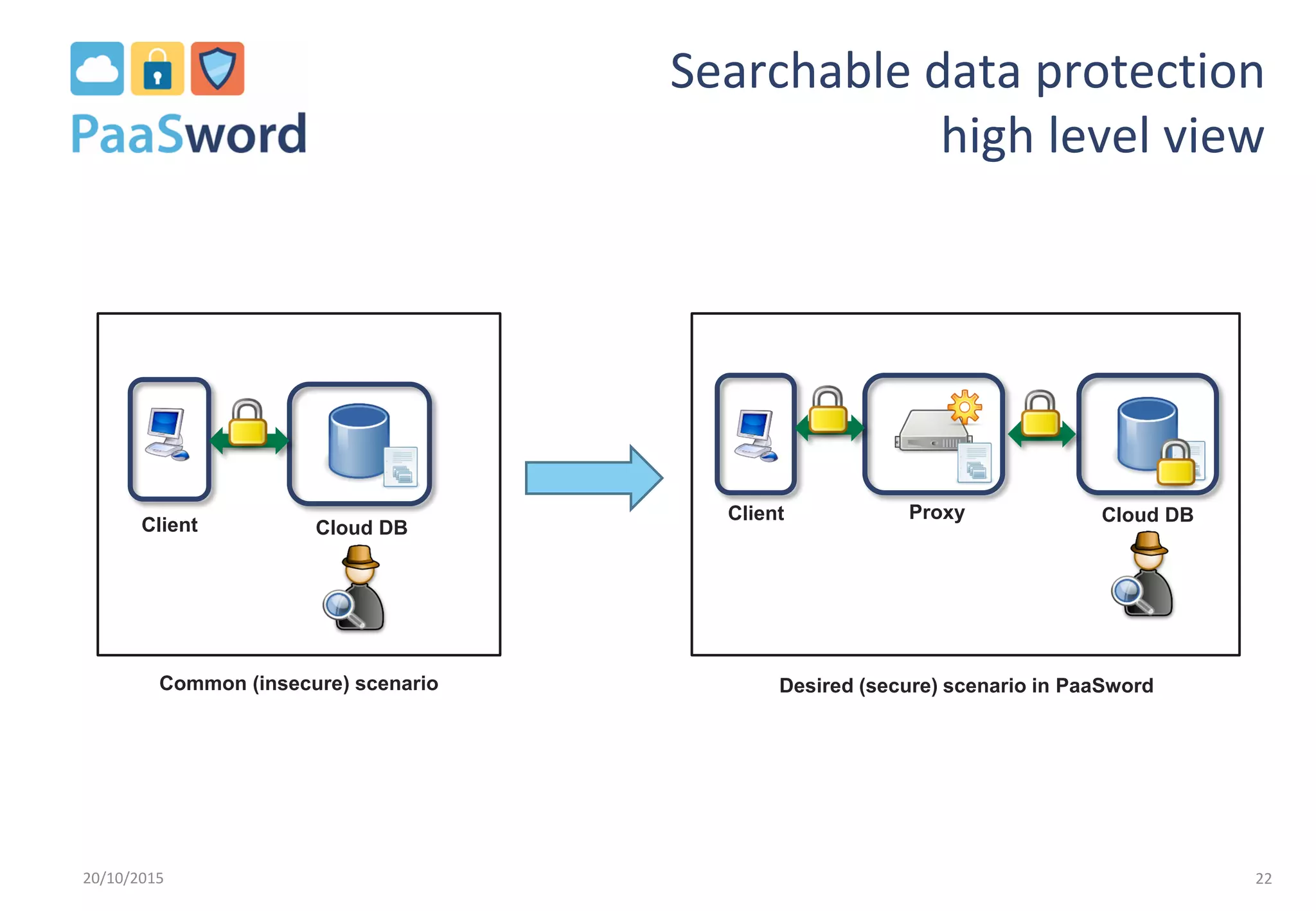
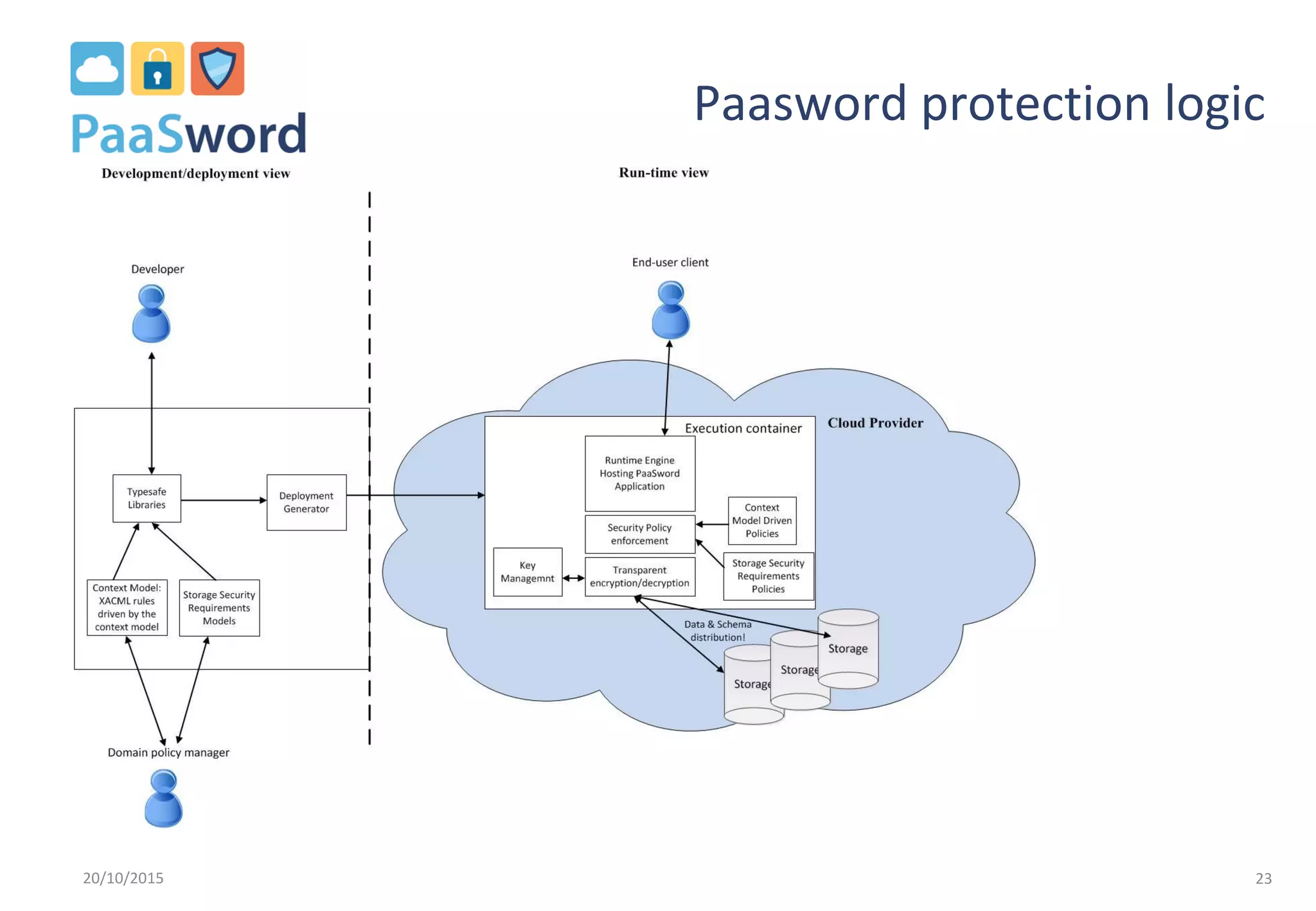
The document introduces a privacy-preserving framework called PaaSword aimed at enabling secure application development in cloud environments, addressing the challenges posed by increased data breaches. It emphasizes the importance of integrating security-by-design principles and context-aware security models to enhance data protection without burdening developers. The presentation also outlines the need for transparent data protection tools offered by cloud platforms to simplify security configurations for both developers and end-users.