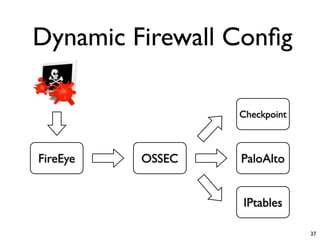
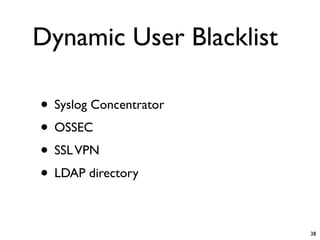
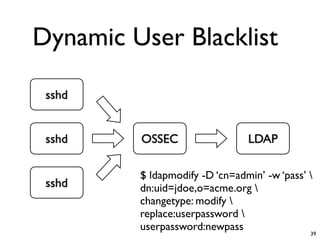
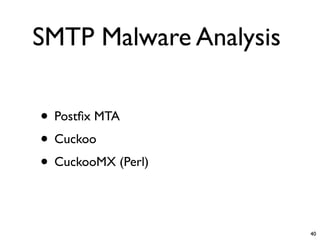
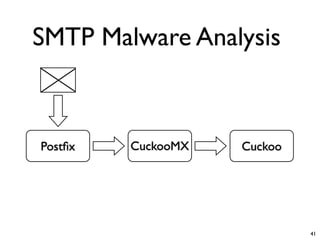
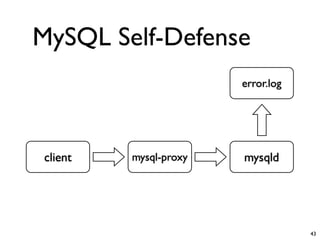
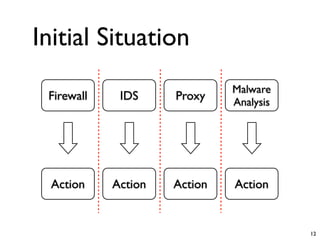
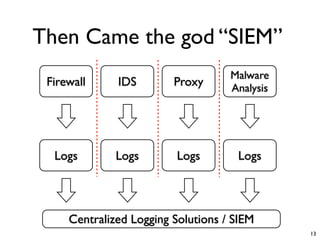
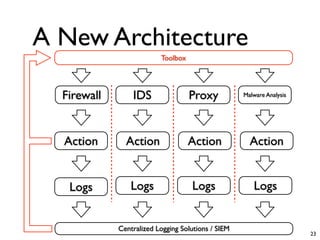
Unity Makes Strength discusses how security tools and systems can benefit from sharing information and coordinating responses through open communication. The presentation outlines examples of using common protocols and APIs to integrate firewalls, intrusion detection, malware analysis and other tools. Dynamic integration allows the systems to automatically update configurations and block threats in real-time based on intelligence from multiple sources. While powerful, proper controls and testing are needed to avoid potential risks from increased connectivity.













![Automation is the Key
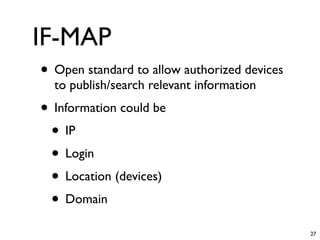
• We’re all lazy people!
• Expect!
use Expect;
my $e = Expect->new();
my $c = “ssh $user@$host”;
$e = Expect->spawn($c) or die “No SSH?”;
$e->Expect($timeout,
[
qr’password: $’,
sub {
my $fh = shift;
print $fh $passwordn”;
}
]
22](https://image.slidesharecdn.com/unitymakesstrength-121103175427-phpapp02/85/Unity-makes-strength-22-320.jpg)
![HTTPS
• Generate an API key
https://10.0.0.1/api/?type=keygen&user=foo&password=bar
• Submit XML requests
https://10.0.0.1/api/?type=config&key=xxx&action=set&xpath=/
config/device/entry[@name=localhost]/vsys/
entry[@name=vsys1]/address/
entry[@name=NewHost]&element=<ip-
netmask>192.168.0.1</ip-netmask><description>Test</
description>
25](https://image.slidesharecdn.com/unitymakesstrength-121103175427-phpapp02/85/Unity-makes-strength-25-320.jpg)