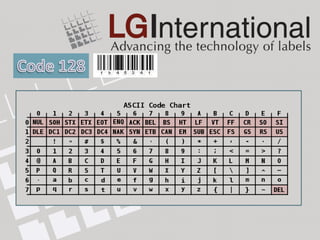
The document provides an introduction to barcodes, including a brief history and overview of their advantages such as speed, cost integrity, ease of setup, data effectiveness, and accuracy. It discusses different barcode symbologies such as 1D barcodes like Code 39 and Code 128, and 2D barcodes like QR code, PDF417, and Datamatrix. Key aspects of barcode composition and factors that can affect scannability like print quality are also covered.