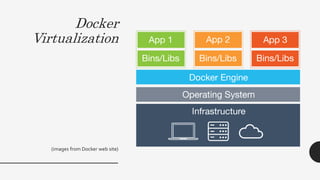
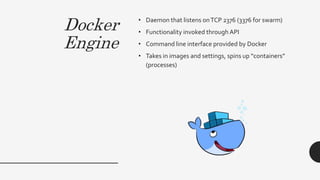
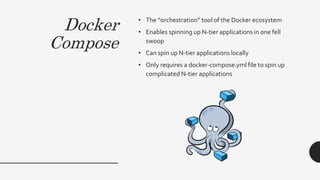
The document provides a comprehensive overview of the Docker ecosystem, including its core components like Docker Engine, Docker Registry, Docker Machine, Docker Compose, and Docker Swarm, highlighting their functionalities and benefits. It also discusses potential pitfalls and security considerations related to Docker, emphasizing the importance of understanding its architecture and the need for proper security configurations. The presentation is delivered by Christopher Grayson, the founder of Web Sight.io, who draws on his expertise in the field.