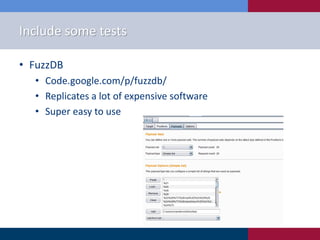
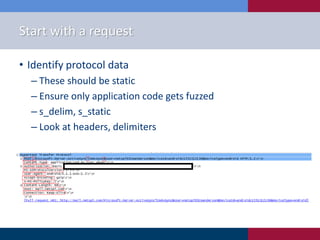
The document discusses the practice of fuzzing as an automatic testing procedure, explaining its significance and applications in identifying vulnerabilities in complex applications. It contrasts whitebox and blackbox testing and suggests various tools and techniques for effective fuzzing, such as Burp Suite and Sulley. Additionally, it emphasizes the importance of tailored tests, analysis of results, and continuous refinement in the fuzzing process.










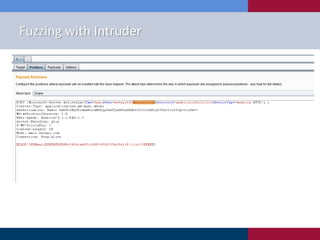




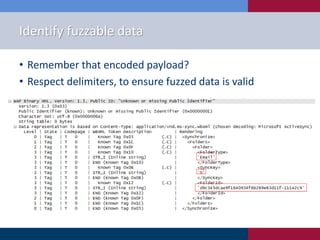



![Session targets
• Identify target protocol, and
procmon/netmon ports
Activesync_target=sessions.target(“ip.ip.ip.ip”, port)
Activesync_target.netmon=pedrpc.client(“ip.ip.ip.ip”,port) #these
are chosen when you run the netmon binary on the target
Activesync_target.procmon=pedrpc.client(“ip.ip.ip.ip”,port)
Activesync_target.procmon_options =
{“proc_name”: “process_name”,
“stop_commands”: [‘cmd_to_stop_service’],
“start_commands”: [‘cmd_to_start_again’]}
• Run the procmon and netmon binaries
before you begin fuzzing
‒ install sulley on the target](https://image.slidesharecdn.com/fuzzingandyou-automatingwhiteboxtesting-130418112833-phpapp02/85/Fuzzing-and-You-Automating-Whitebox-Testing-23-320.jpg)