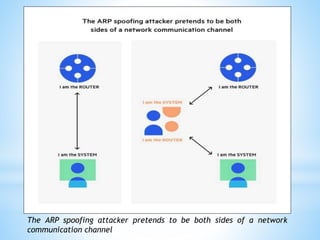
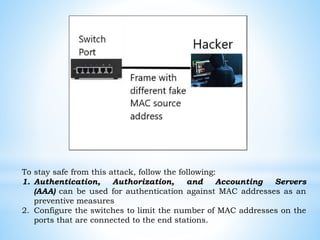
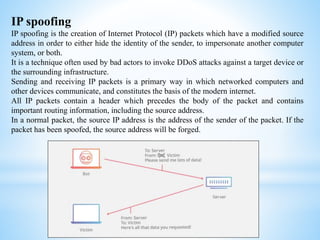
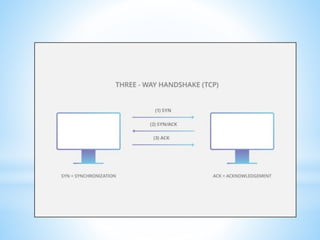
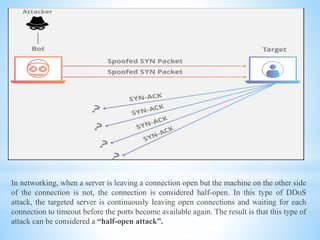
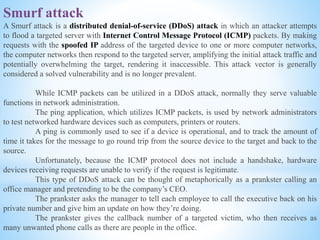
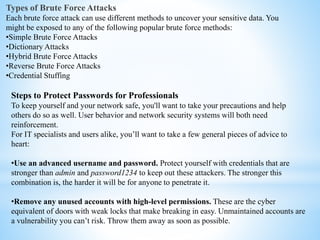
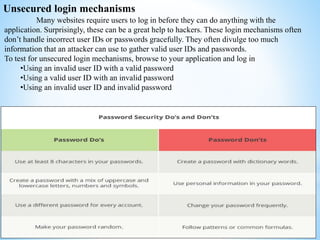
This document discusses several cybersecurity topics including ARP spoofing, password cracking, WEP vulnerabilities, MAC flooding, IP spoofing, and SYN flood attacks. It provides details on how each works and potential prevention and mitigation techniques. ARP spoofing allows attackers to intercept network traffic by spoofing MAC addresses. Password cracking involves recovering passwords through methods like brute force attacks or rainbow tables. WEP has security flaws in its use of short, static IVs and lack of integrity checks. MAC flooding overwhelms switches by sending fake MAC addresses. IP spoofing and SYN floods are types of DDoS attacks that respectively modify source IP addresses or abuse the TCP three-way handshake. Defenses include ingress filtering, egress filtering, and SYN cookies.