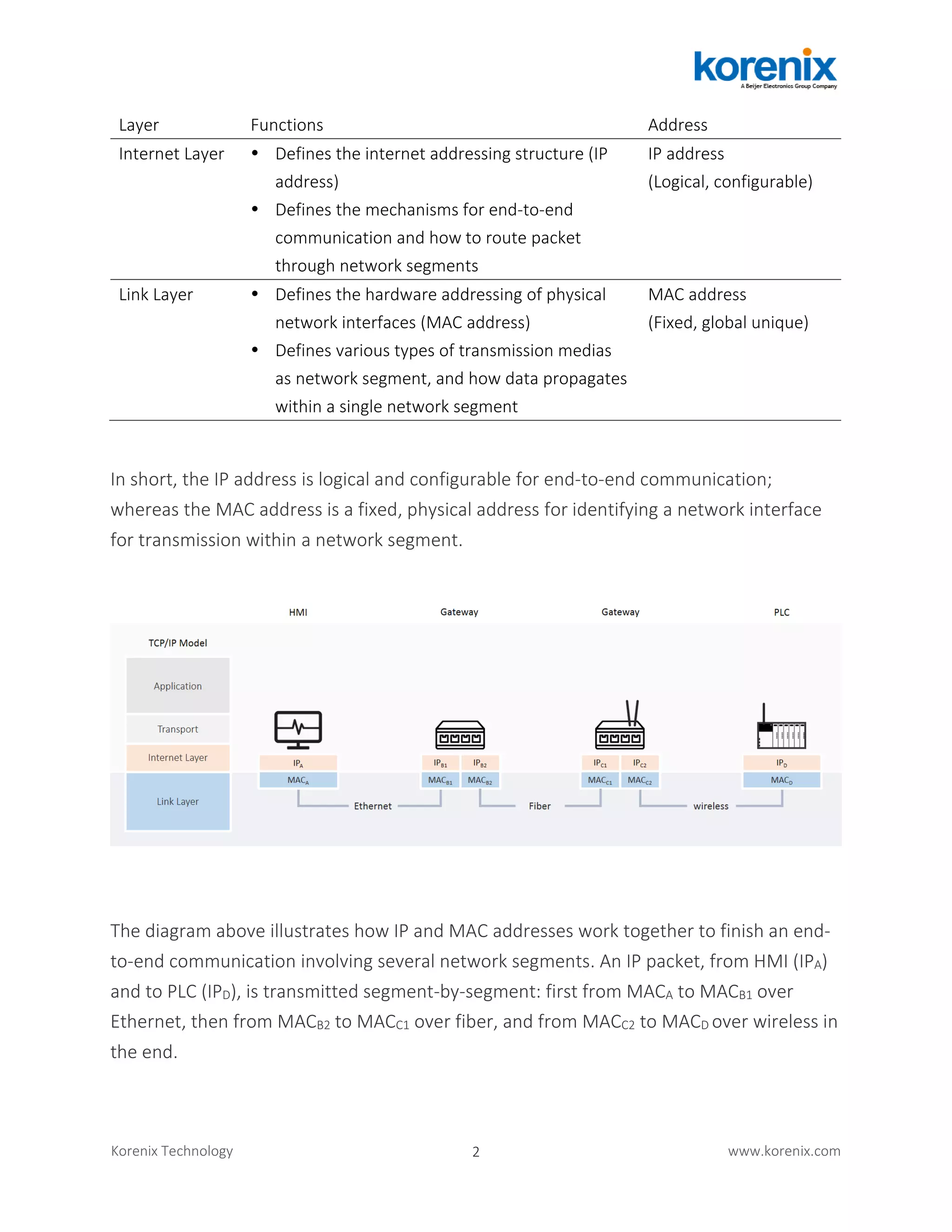
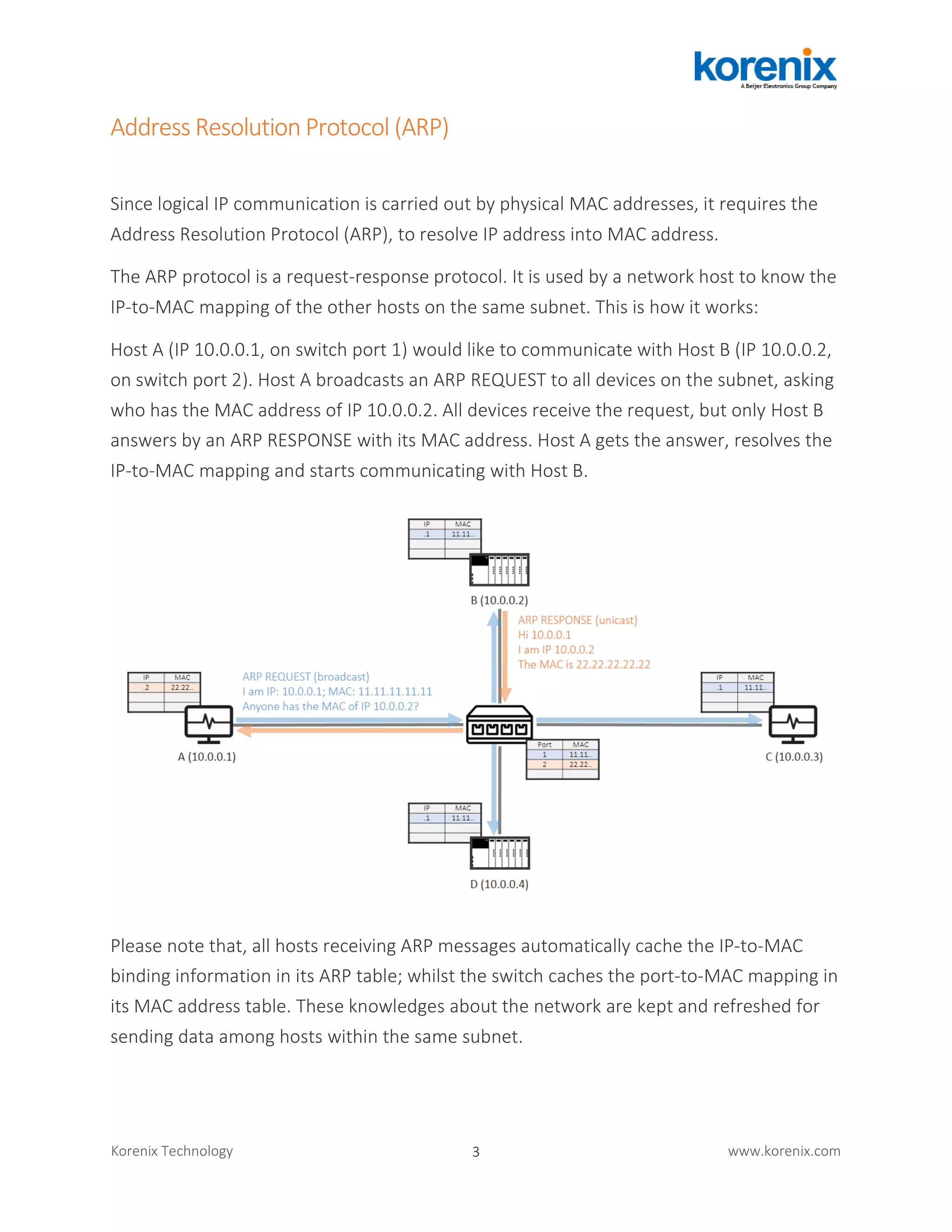
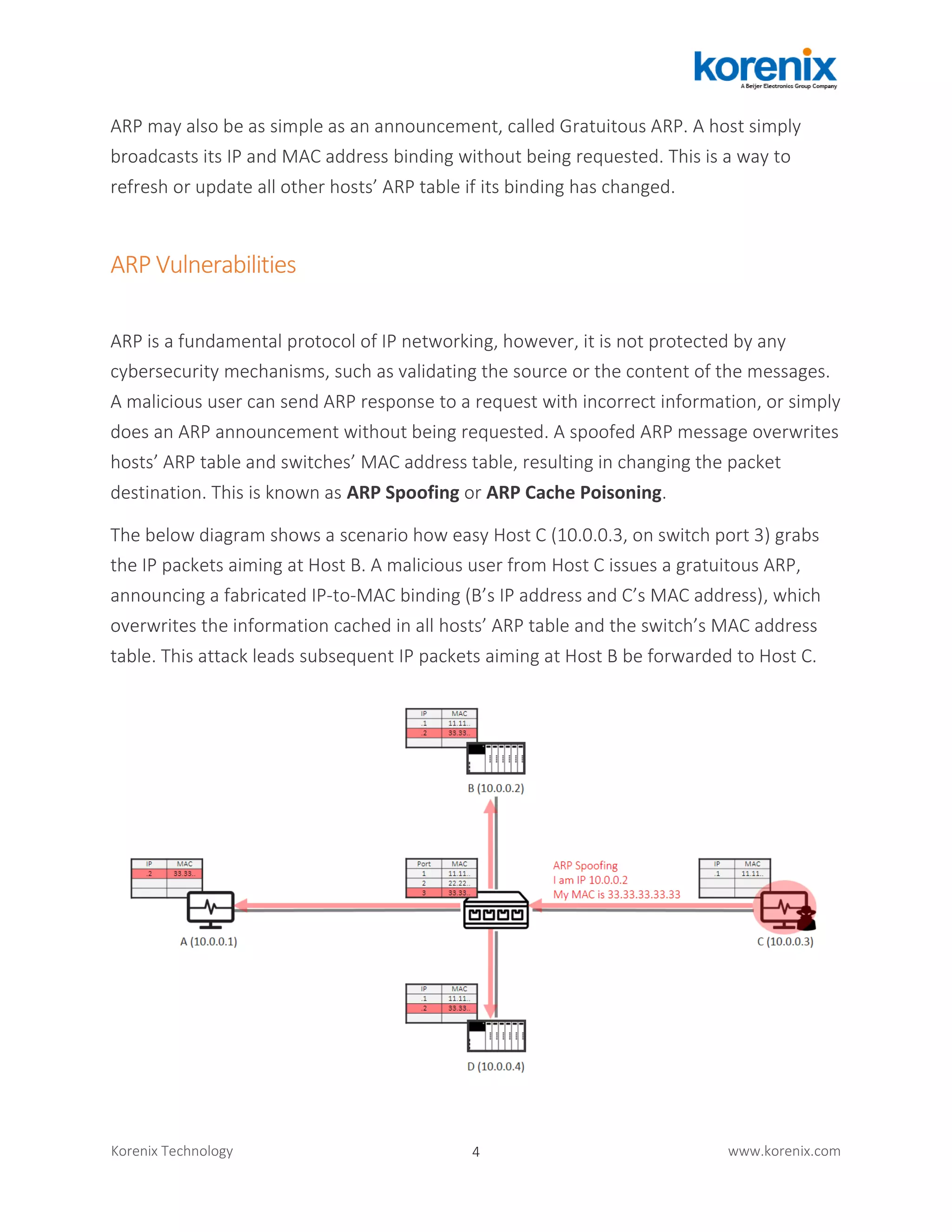
The document discusses how IP addresses are resolved to MAC addresses through the Address Resolution Protocol (ARP) and how ARP spoofing attacks threaten industrial network security. It describes how ARP works and how attackers can spoof ARP responses to redirect network traffic. The document advocates for using Dynamic ARP Inspection on industrial Ethernet switches to validate IP-MAC bindings and prevent ARP spoofing attacks from occurring. Securing ARP is important for protecting the basic operations of industrial IP networking.