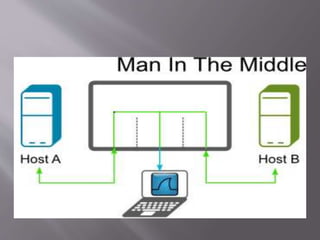
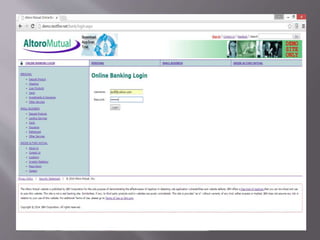
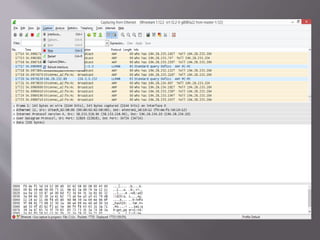
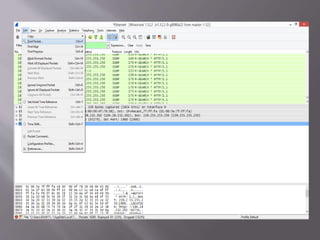
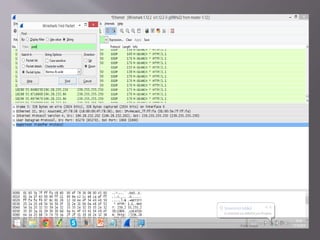
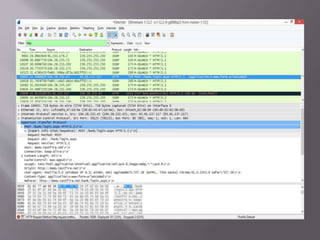
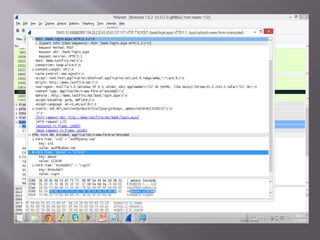
A man-in-the-middle attack intercepts communications between two systems by compromising the connection, such as the TCP connection between an HTTP client and server. Tools like Wireshark and tcpdump can be used to perform a man-in-the-middle attack on HTTP traffic in a LAN network by analyzing packets at the deepest level. Wireshark is used in this scenario to attack vulnerabilities between network nodes.