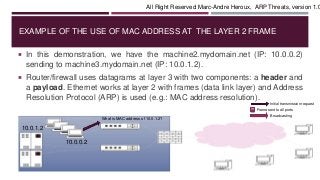
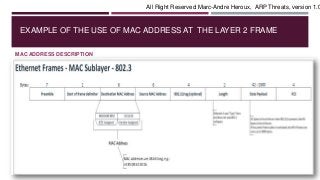
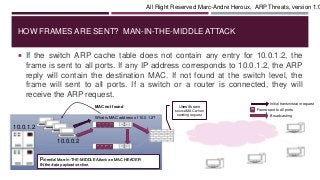
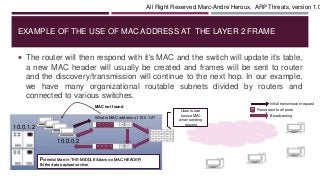
The document discusses MAC addresses and how they are used at the data link layer (layer 2) of the OSI model. It provides an example of how a machine with IP address 10.0.0.2 would use ARP requests to find the MAC address of 10.0.1.2, which could allow for a man-in-the-middle attack if a malicious actor was able to spoof responses. The document also describes how frames are broadcast at layer 2 when MAC addresses are unknown to switches, and stresses the importance of monitoring for abnormal network activity and securing network access to prevent ARP threats.