Salt and Ansible are both popular tools for network orchestration and automation. Salt uses a centralized master-minion architecture where configuration files and templates are stored on the master. Ansible uses an agentless architecture where playbooks are run directly on managed nodes. Both tools support network device configuration through modules like NAPALM that provide a common API. Salt states and Ansible playbooks define the desired configuration through templates that are rendered and installed on devices. The tools detect configuration drift and make necessary changes.














![Ansible – Example
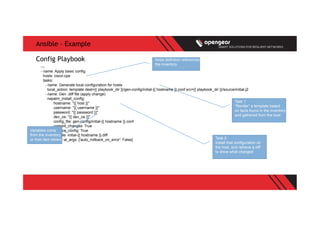
# Cisco CPE devices
[cisco-cpe]
r1 host=192.168.82.76 hostname=r1-cpe.opengear.com
r2 host=192.168.82.77 hostname=r2-cpe.opengear.com
# Default variables for Cisco devices managed via NAPALM
[cisco-cpe:vars]
username=admin
password=default
dev_os=ios
ansible_connection=local
Inventory hosts definitions, with
in-line variable definitions
Default variables for this
group of hosts](https://image.slidesharecdn.com/vincentboon-2018-network-automation-ansible-saltvincentboon-opengear-180724091801/85/Ansible-Salt-Vincent-Boon-16-320.jpg)
![Ansible – Example
test@test-srv:~/src/central-orchestration/ansible-napalm-ios$ ansible -playbook config.play -i inventory
PLAY [Apply basic config] ******************************************************
TASK [Gathering Facts] *********************************************************
ok: [r1]
ok: [r2]
TASK [Generate local configuration for hosts] **********************************
ok: [r2 -> localhost]
ok: [r1 -> localhost]
TASK [Gen .diff file (apply change)] *******************************************
ok: [r1]
ok: [r2]
PLAY RECAP *********************************************************************
r1 : ok=3 changed=0 unreachable=0 failed=0
r2 : ok=3 changed=0 unreachable=0 failed=0
Execution – test configuration compliance
Configuration matches the
generated template.](https://image.slidesharecdn.com/vincentboon-2018-network-automation-ansible-saltvincentboon-opengear-180724091801/85/Ansible-Salt-Vincent-Boon-17-320.jpg)

![Ansible – Example
test@test-srv:~/src/central-orchestration/ansible-napalm-ios$ ansible-playbook config.play -i inventory
PLAY [Apply basic config] **************************************************************************************************
TASK [Gathering Facts] *****************************************************************************************************
ok: [r1]
ok: [r2]
TASK [Generate local configuration for hosts] ******************************************************************************
ok: [r1 -> localhost]
ok: [r2 -> localhost]
TASK [Gen .diff file (apply change)] ***************************************************************************************
ok: [r1]
changed: [r2]
PLAY RECAP *****************************************************************************************************************
r1 : ok=3 changed=0 unreachable=0 failed=0
r2 : ok=3 changed=1 unreachable=0 failed=0
test@test-srv:~/src/central-orchestration/ansible-napalm-ios$ cat initial-r2-cpe.opengear.com.diff
+hostname r2-cpe.opengear.com
-hostname r2-cpe-modified.opengear.com
test@test-srv:~/src/central-orchestration/ansible-napalm-ios$ ssh admin@192.168.82.77
Password:
r2-cpe.opengear.com#exit
Execution – configuration fixups
Configuration change is
discovered and fixed
Diff shows the change](https://image.slidesharecdn.com/vincentboon-2018-network-automation-ansible-saltvincentboon-opengear-180724091801/85/Ansible-Salt-Vincent-Boon-19-320.jpg)







![Salt – Example
[test@test-srv pillar (master)]$ cat top.sls
base:
r1:
- r1
r2:
- r2
[test@test-srv pillar (master)]$ cat r1.sls
proxy:
proxytype: napalm
driver: ios
host: 192.168.82.76
username: admin
password: default
optional_args:
auto_rollback_on_error: False
#R1 specific variables
hostname: r1.cpe.opengear.com
[test@test-srv pillar (master)]$ cat r2.sls
<same proxy statement as r1.sls>
#R2 specific variables
hostname: r2.cpe.opengear.com
Salt Pillar
Restrict r1.sls to host r1,
and r2.sls to host r2
NAPALM configuration for R1
(same settings used for R2)
Host specific variable for R1](https://image.slidesharecdn.com/vincentboon-2018-network-automation-ansible-saltvincentboon-opengear-180724091801/85/Ansible-Salt-Vincent-Boon-27-320.jpg)
![Salt – Example
[test@test-srv states (master)]$ cat config.sls
full_config:
netconfig.managed:
- template_name: salt://router-config.j2
- replace: True
[test@test-srv states (master)]$ cat router-config.j2
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname {{ pillar.hostname }}
!
Salt State
Defines the template to be applied,
and if it should replace the existing config
Same templating engine as
Ansible
“pillar.hostname” instructs Salt to
Retrieve variable from the Pillar](https://image.slidesharecdn.com/vincentboon-2018-network-automation-ansible-saltvincentboon-opengear-180724091801/85/Ansible-Salt-Vincent-Boon-28-320.jpg)




