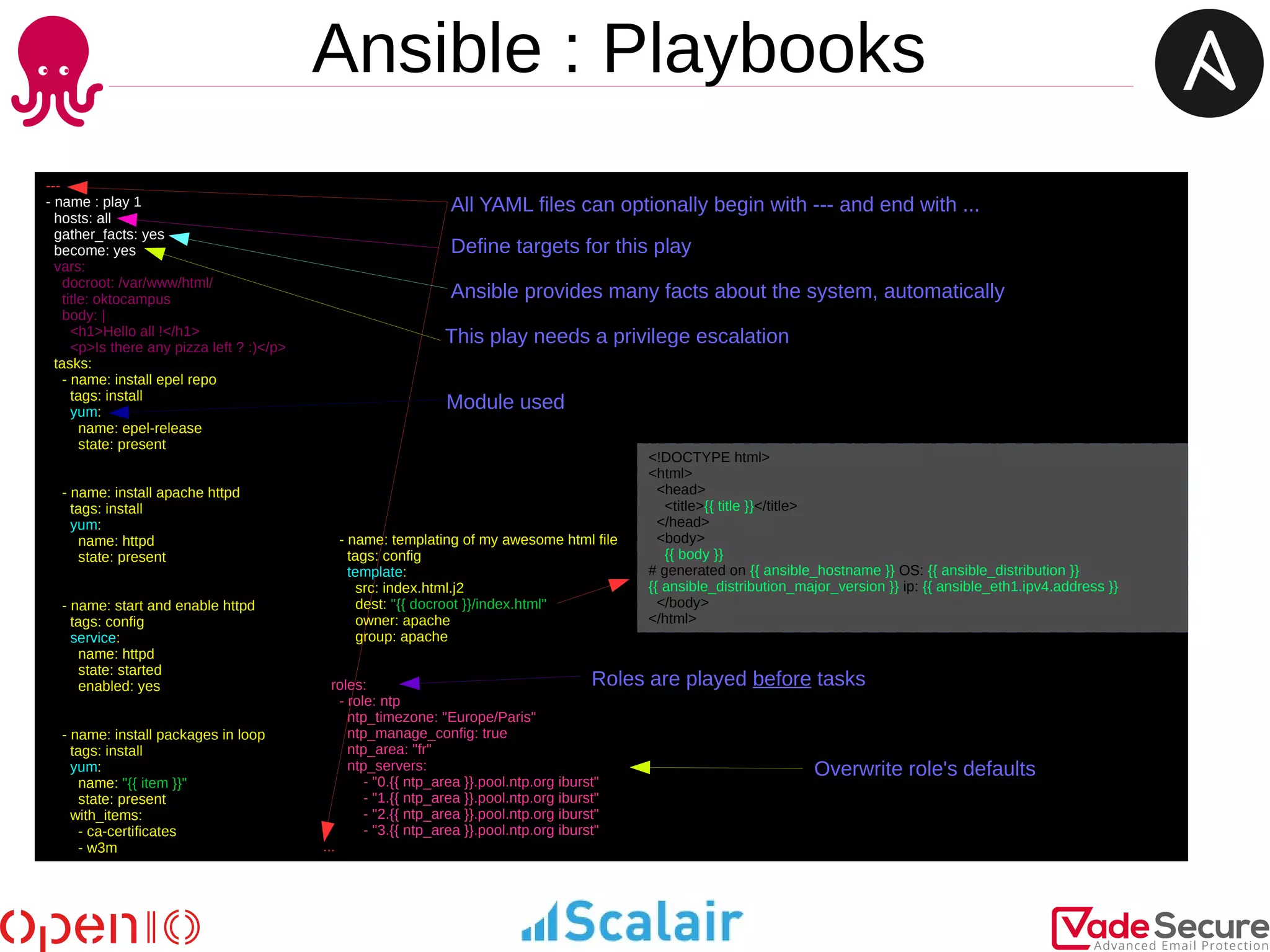
- A playbook is defined to check if a pattern is present in the content of a web page retrieved from localhost. The playbook registers the content and fails if the defined pattern is not found.
- The playbook is modified to define different patterns for different host groups - the groups "prod" and "recette" would each have their own unique pattern to check for.
- The playbook uses Ansible modules like uri to retrieve a web page, register to store the content, and fail if a registered pattern is not found in the content. Variables and conditionals allow defining patterns dynamically based on host groups.











![Ansible : Inventory
[prod]
prod1
10.0.15.21
[recette]
rec[1:2]
[jira]
{{ jira_ip }}
Inventory files are simple text files which describe
your servers
IP Addresses or DNS Names, grouped by names
Inventory files can take advantage of variables
and enumerations](https://image.slidesharecdn.com/oktocampusansible-170701164655/75/OktoCampus-Workshop-An-introduction-to-Ansible-19-2048.jpg)



![Ansible
LAB
Part 2
In a playbook only and with the manual
http://docs.ansible.com/ansible/list_of_all_modules.html
or with the ansible-doc commande
Try :
● To write a playbook which check if salt is in the uri http://locahost
● Same idea but the pattern have to be different for the groups [prod] and [recette]](https://image.slidesharecdn.com/oktocampusansible-170701164655/75/OktoCampus-Workshop-An-introduction-to-Ansible-25-2048.jpg)
![Ansible
LAB
Part 2
$> cat site.yml
---
- name : play 1
hosts: all
gather_facts: yes
become: yes
#vars:
# pattern: salt
Tasks:
- name: Get content page
uri:
url: http://localhost
return_content: yes
register: webpage
- name: Fail if {{ pattern }} is not in the page content
fail:
msg: "No >>> {{ pattern }} <<< in this page"
when: "pattern not in webpage.content"
#when: "ansible_hostname not in webpage.content"
...
$> cat inventory
[prod]
prod1
prod2
[recette]
rec[1:2]
[prod:vars]
pattern=pizza
[recette:vars]
pattern=salt](https://image.slidesharecdn.com/oktocampusansible-170701164655/75/OktoCampus-Workshop-An-introduction-to-Ansible-26-2048.jpg)