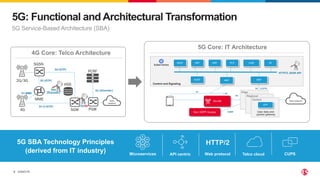
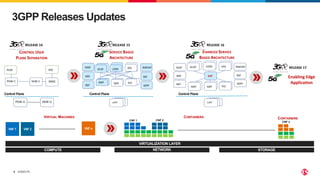
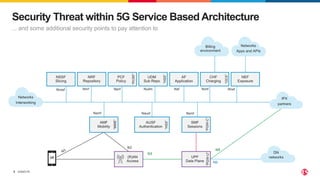
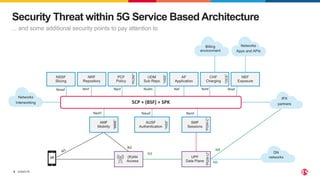
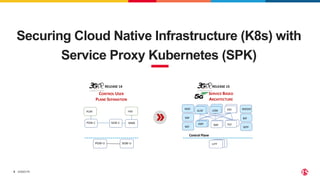
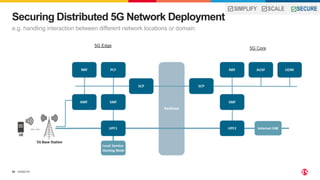
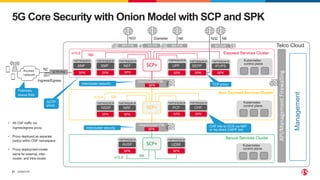
1) The document discusses securing 5G cloud native infrastructure using the Service Proxy for Kubernetes (SPK) and Secure Communication Proxy (SCP).
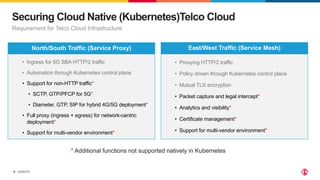
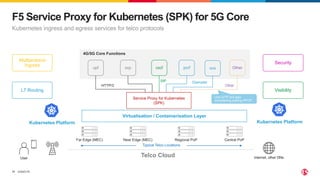
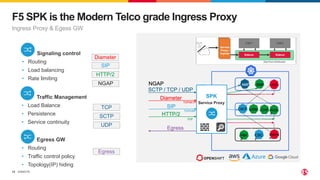
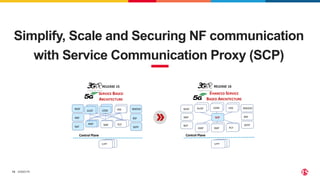
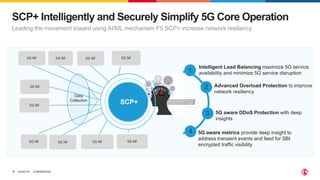
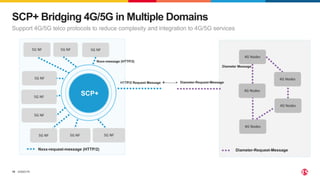
2) SPK provides ingress and egress services for telco protocols like HTTP/2, Diameter, and SIP to secure Kubernetes deployments. SCP simplifies and secures communications between network functions.
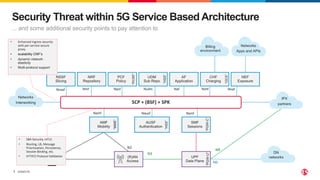
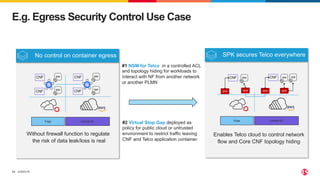
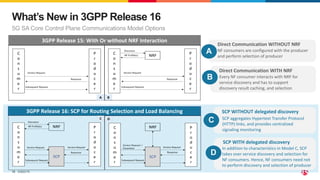
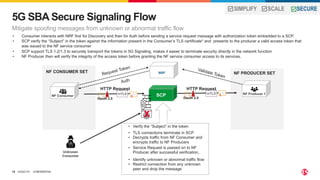
3) SCP and SPK work together to provide a secure "onion model" architecture for distributed 5G core deployments using mutual TLS and traffic management capabilities.