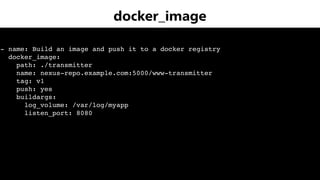
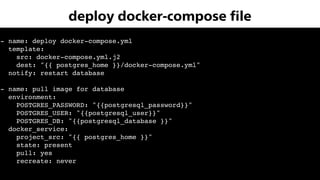
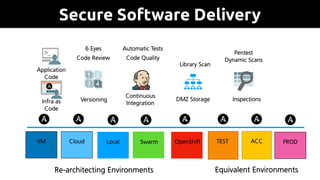
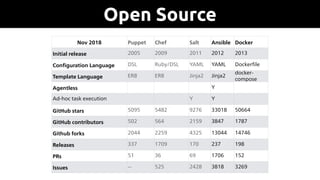
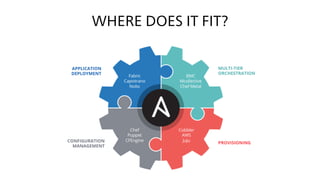
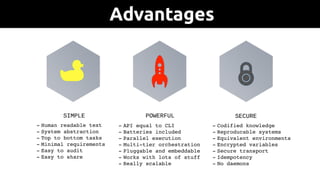
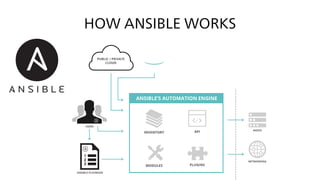
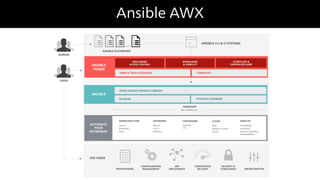
The document provides an overview of Ansible, an all-in-one IT automation tool, detailing its key features, benefits, and design principles. It highlights Ansible's agentless architecture, idempotency, and capability to manage and orchestrate complex IT environments efficiently. Additionally, it discusses various components like playbooks, roles, and integrations with other tools, emphasizing the importance of security and audibility in automation processes.











![[test:children]
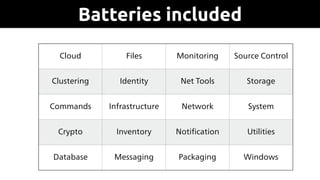
docker
frontend
backend
[test:vars]
ENV=test
ansible_user=ansible
[docker]
www-t.example.com
db-t.example.com
api-t.example.com
[frontend]
www-t.example.com
[backend]
db-t.example.com
api-t.example.com
Inventory of 'test'](https://image.slidesharecdn.com/ansibleatwork-190320192517/85/Ansible-at-work-19-320.jpg)


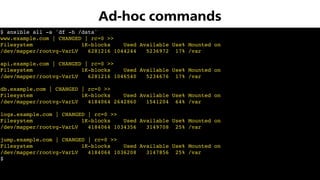
![$ ansible-playbook motd.yml
PLAY [server]
******************************************************************************
TASK [motd : create /etc/motd]
******************************************************************************
changed: [server]
PLAY RECAP
******************************************************************************
server : ok=1 changed=1 unreachable=0 failed=0
Idempotency](https://image.slidesharecdn.com/ansibleatwork-190320192517/85/Ansible-at-work-22-320.jpg)
![$ ansible-playbook motd.yml
PLAY [server]
******************************************************************************
TASK [motd : create /etc/motd]
******************************************************************************
ok: [server]
PLAY RECAP
******************************************************************************
server : ok=1 changed=0 unreachable=0 failed=0
Idempotency](https://image.slidesharecdn.com/ansibleatwork-190320192517/85/Ansible-at-work-23-320.jpg)



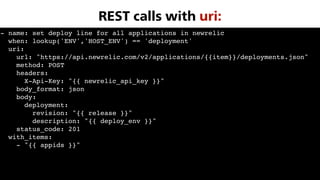


![BUILD_DIR=../build
SRC_DIR=../src
declare -A APP_DEPENDENCIES=
([“SRC"]=vendor ["DEST"]=vendor)
(["SRC"]=node_modules/app.js ["DEST"]=js)
# Clean old build(s)
clean:
rm -rf $(BUILD_DIR)
# Copy all app files
copy-app:
cp -R $(SRC_DIR) $(BUILD_DIR)
# Create local.xml symlink
symlink-localxml:
ln -fs /path/to/local.xml
$(BUILD_DIR)/local.xml
# Copy app dependencies (PHP & JS)
copy-dependencies:
for item in "$${!APP_DEPENDENCIES[@]}" ; do
cp -rT --preserve=mode,timestamp,links
”./$${item['SRC']}"
“${BUILD_DIR}/$${item['DEST']}" ;
done
vars:
- build_dir: ../build
- src_dir: ../src
- app_dependencies:
- { src: vendor, dest: vendor }
- { src: node_modules/app.js, dest: js }
tasks:
- name: Clean old build(s)
file:
path: "{{ build_dir }}"
state: absent
- name: Copy all app files
copy:
src: "{{ src_dir }}"
dest: "{{ build_dir }}"
- name: Create local.xml symlink
file:
src: /path/to/local.xml
dest: "{{ build_dir }}/local.xml”
state: link
- name: Copy app dependencies (PHP & JS)
copy:
src: "./{{ item.src }}"
dest: "{{ build_dir }}{{ item.dest }}"
follow: yes
with_items: app_dependencies
Makefile Ansible
Application Construction](https://image.slidesharecdn.com/ansibleatwork-190320192517/85/Ansible-at-work-33-320.jpg)
![FROM centos:centos7
MAINTAINER Bas Meijer <bas.meijer@me.com>
LABEL running="docker run -d -p 8080:8080 dockpack/tomcat:7"
ADD ansible /tmp/ansible
RUN yum update -y &&
yum install -y epel-release &&
yum install -y ansible tar &&
yum clean all &&
cd /tmp/ansible &&
ansible-galaxy install --force -r requirements.yml &&
ansible-playbook playbook.yml
ADD app /var/app
ENV DATABASE postgres
ENV PATH $APP_HOME/bin:$PATH
WORKDIR $APP_HOME
EXPOSE 8080
ENTRYPOINT ["/opt/apache-tomcat/bin/catalina.sh","run"]
Dockerfile?](https://image.slidesharecdn.com/ansibleatwork-190320192517/85/Ansible-at-work-34-320.jpg)