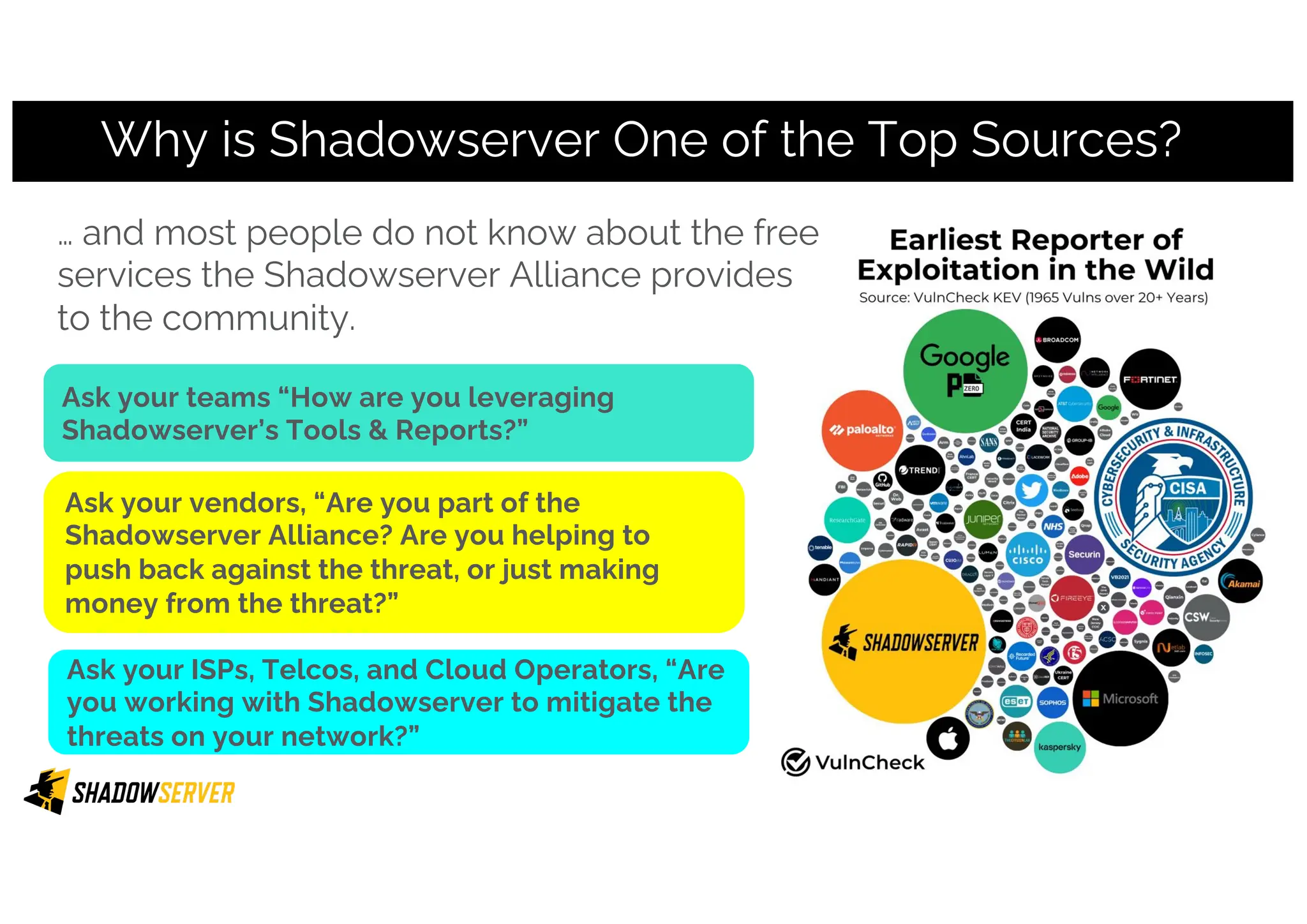
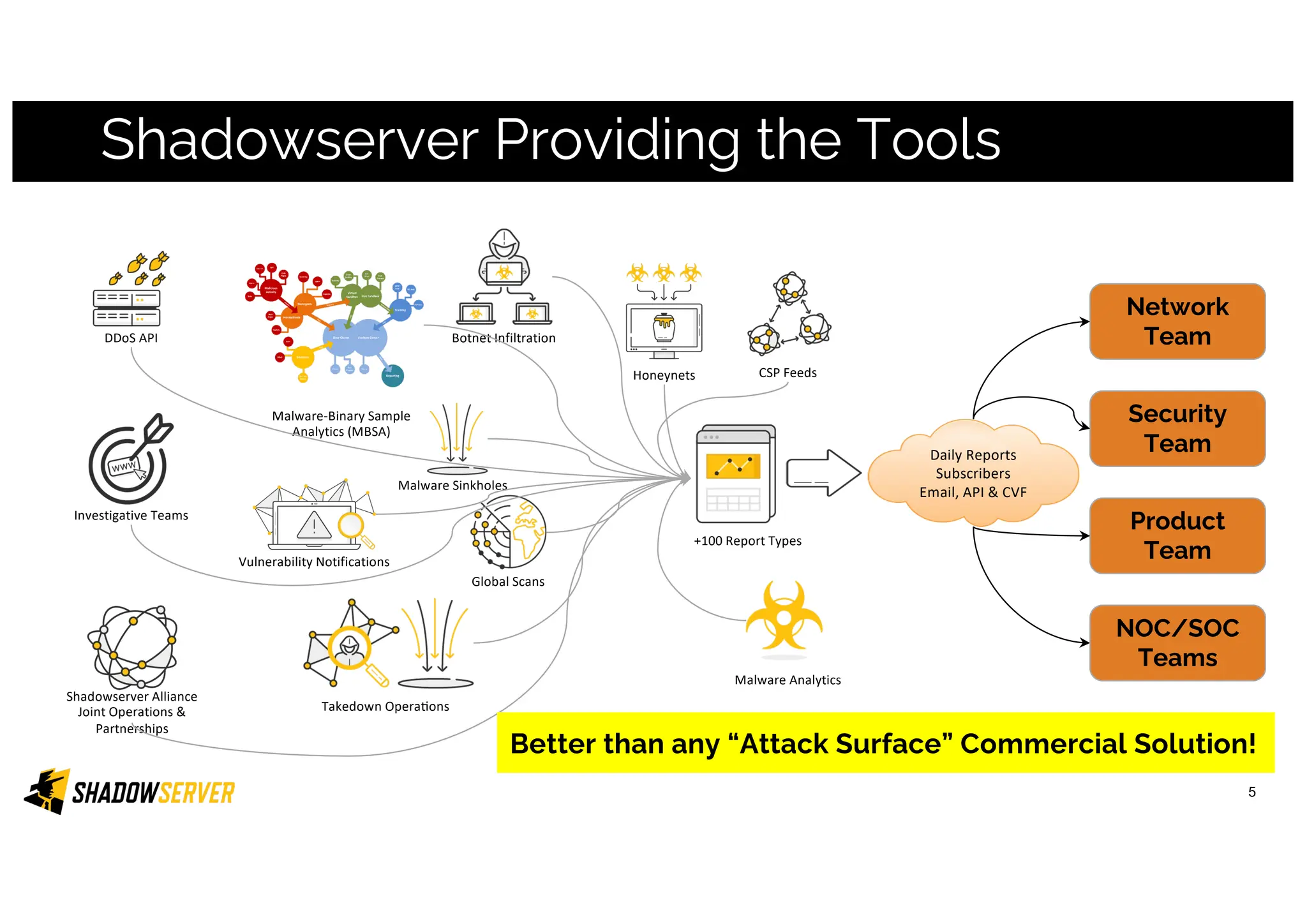
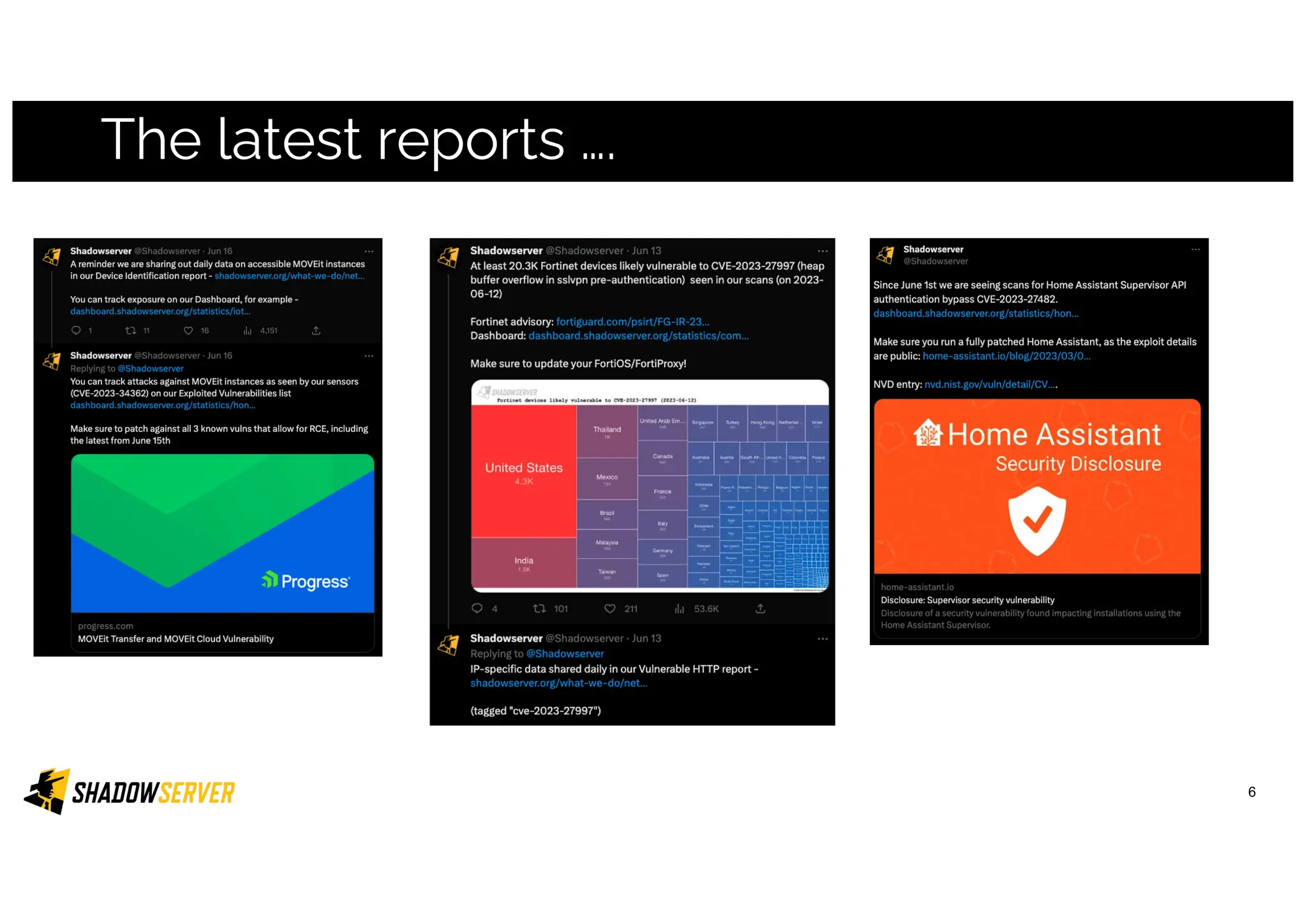
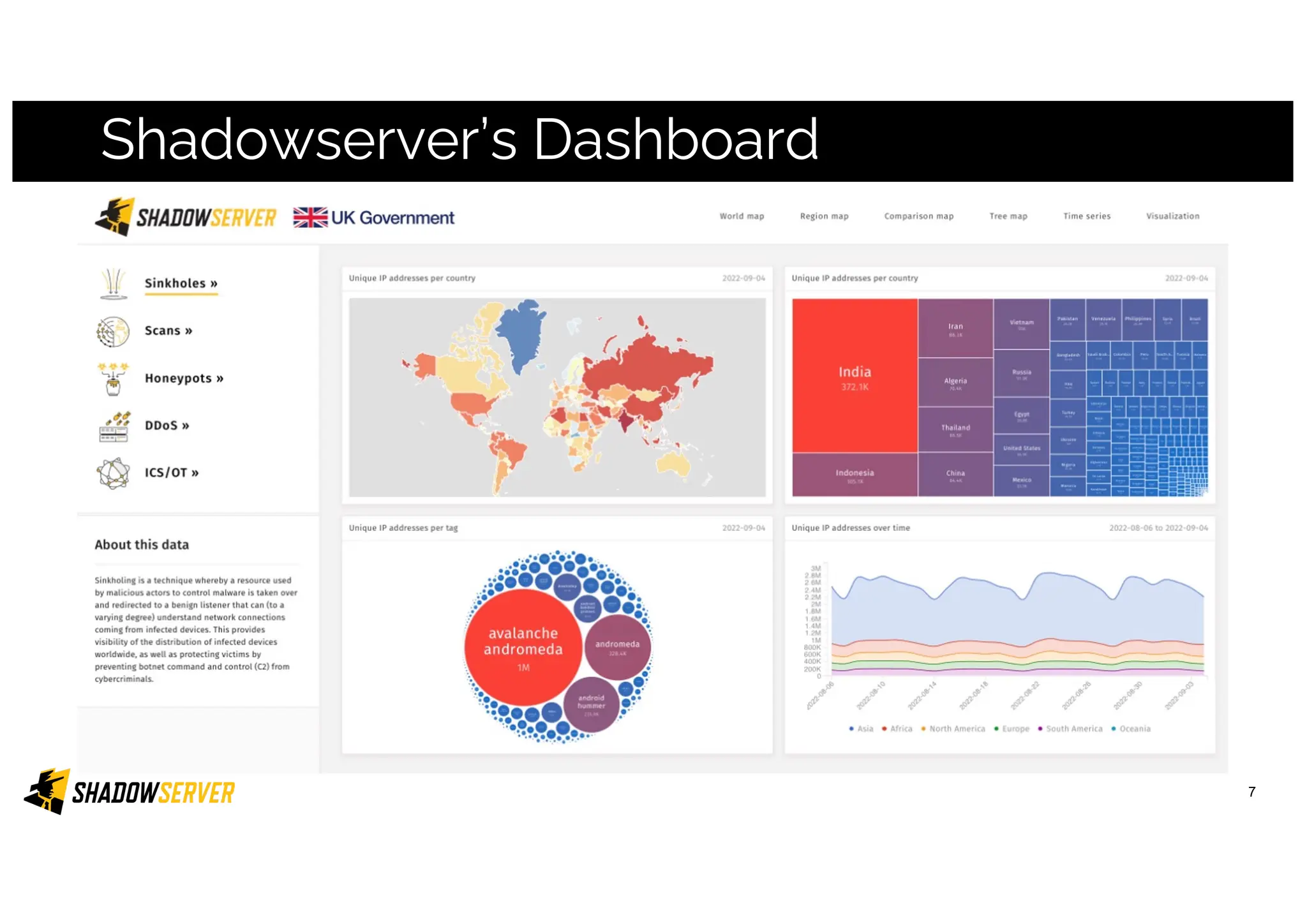
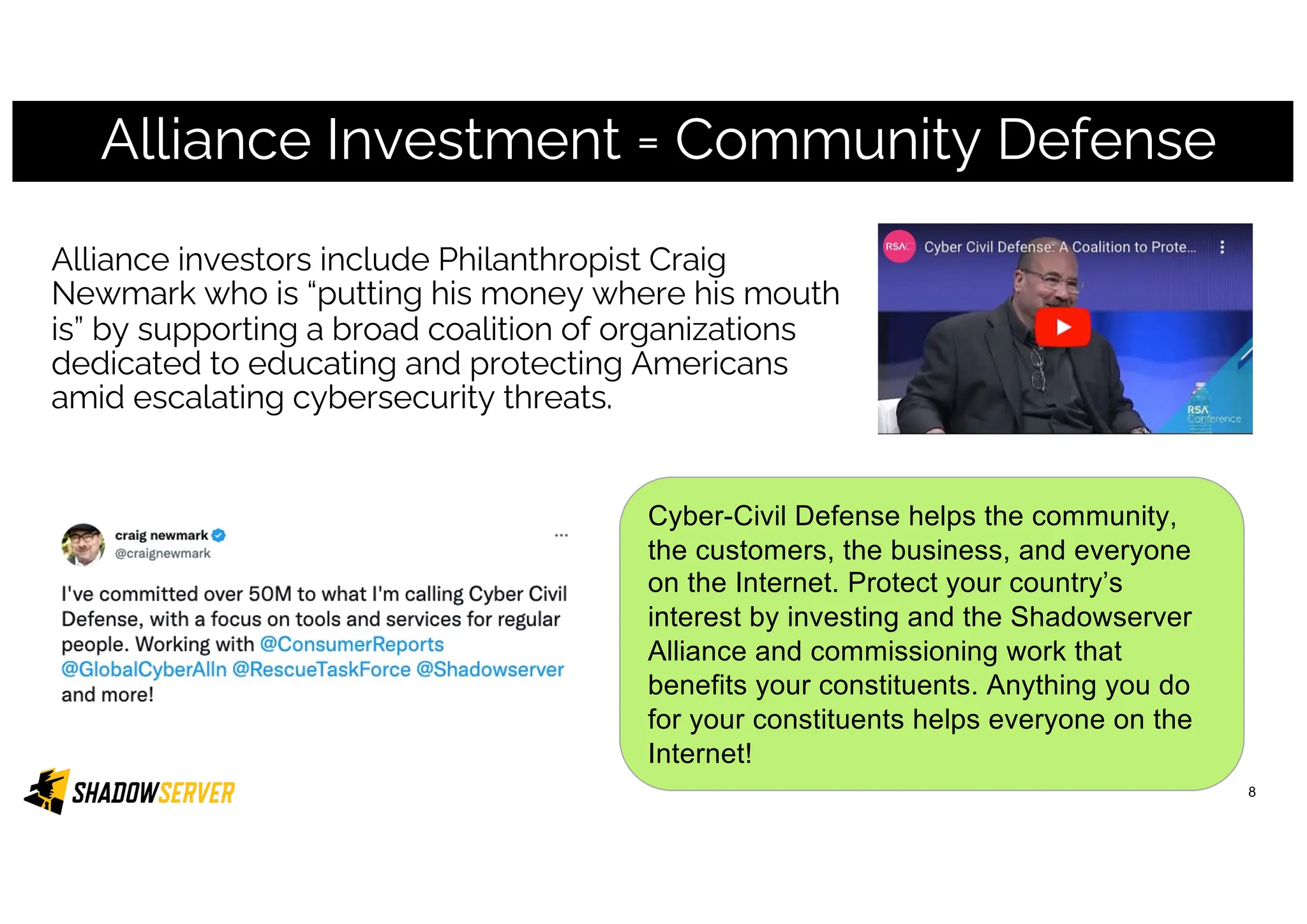
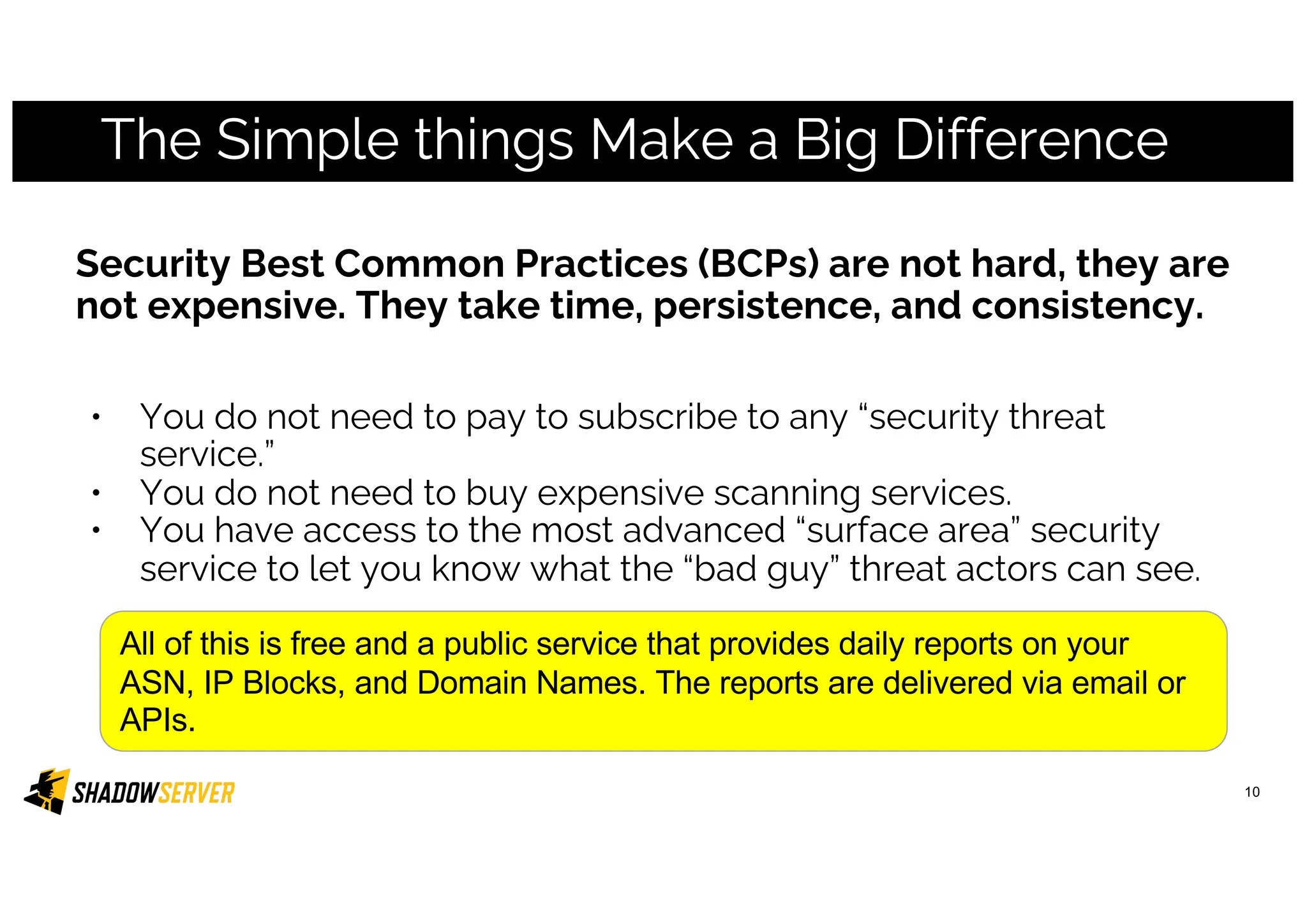
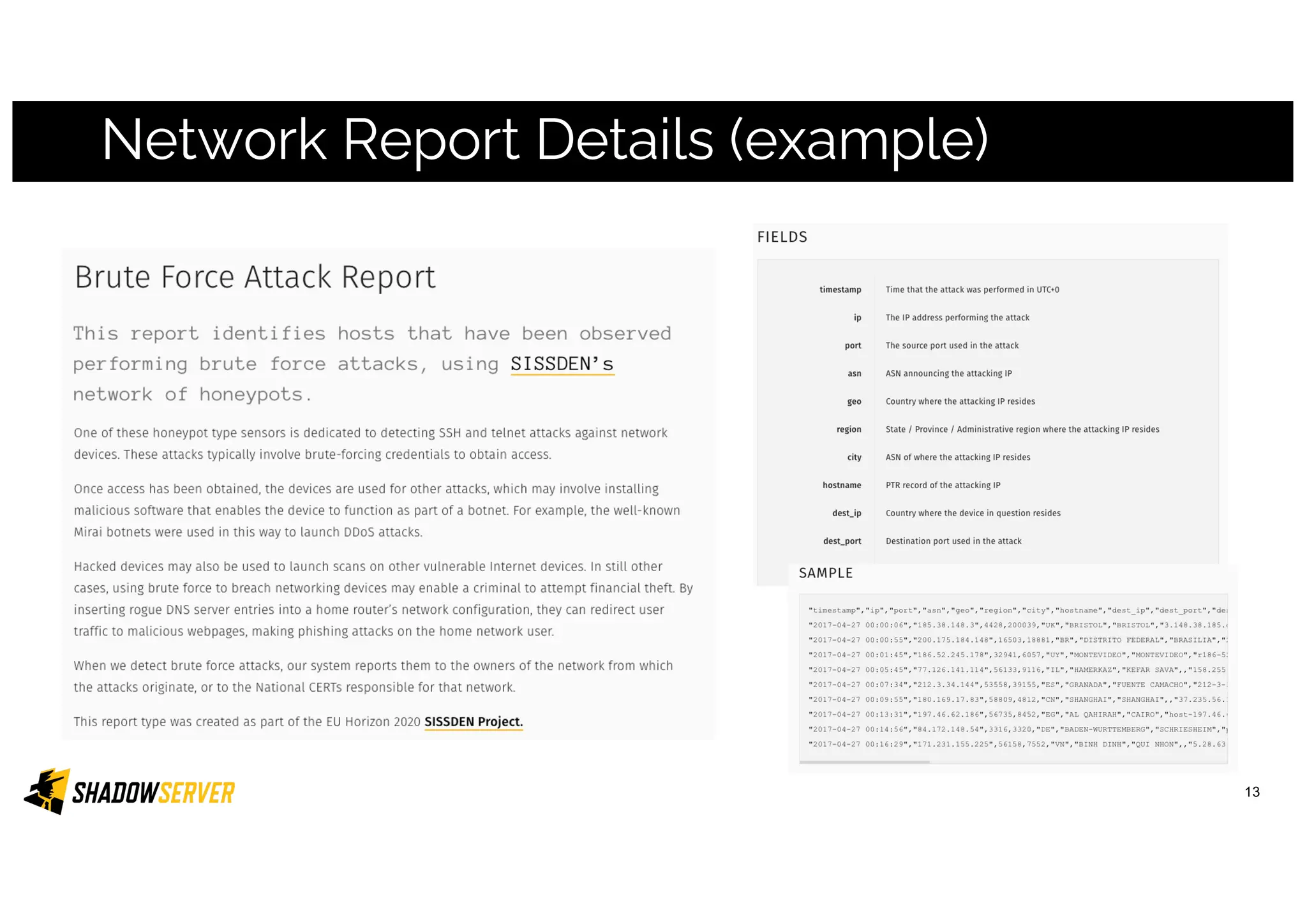
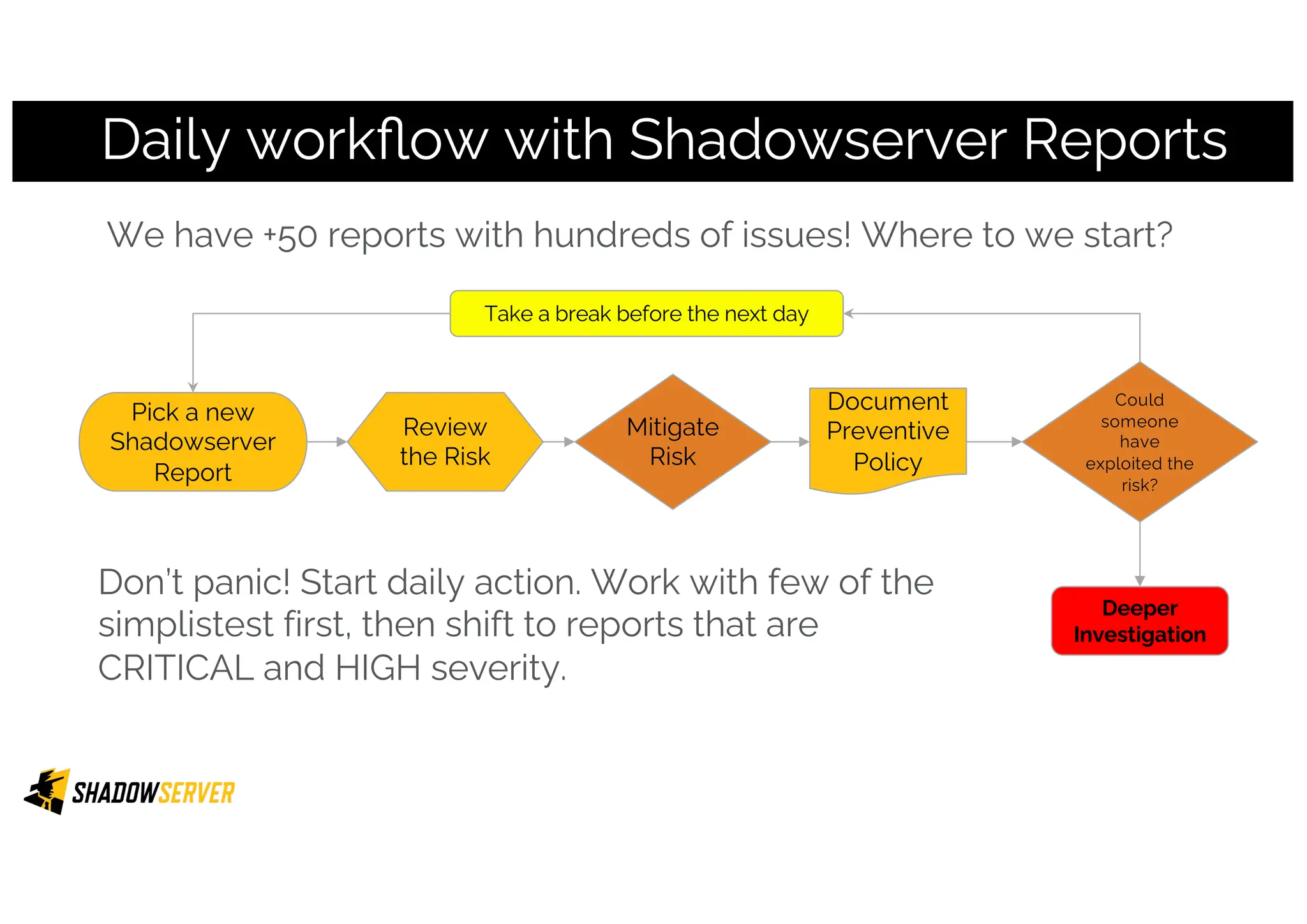
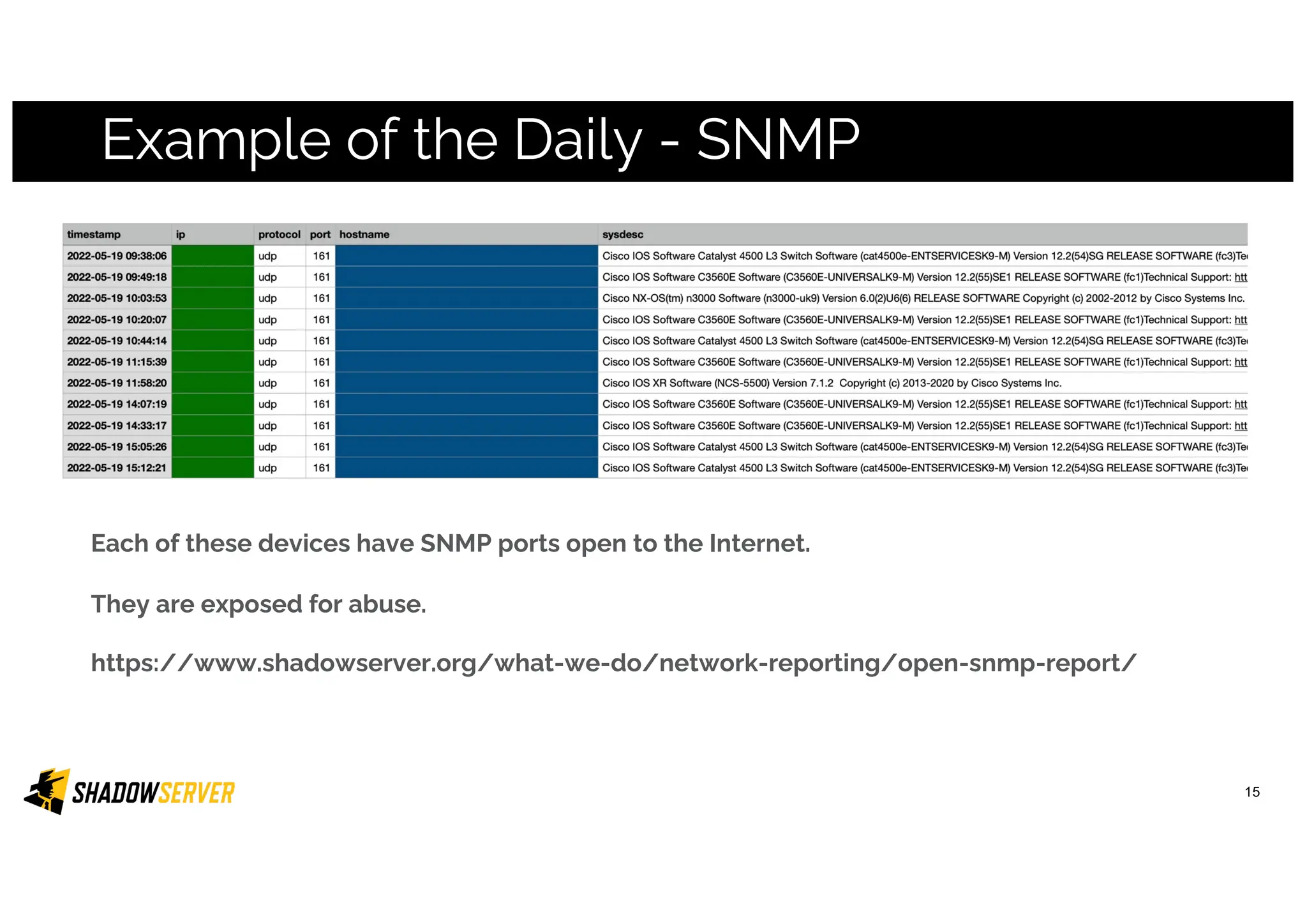
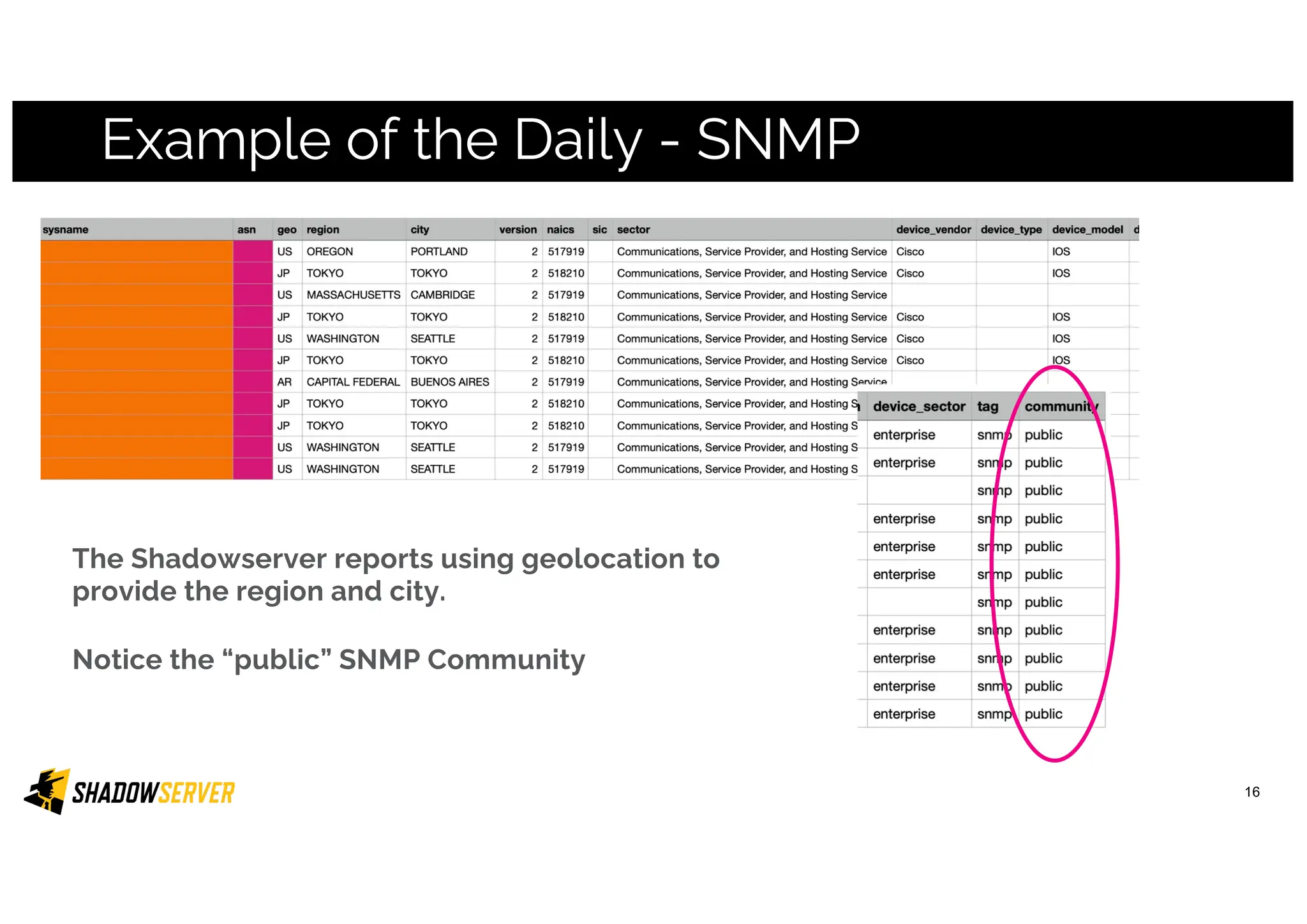
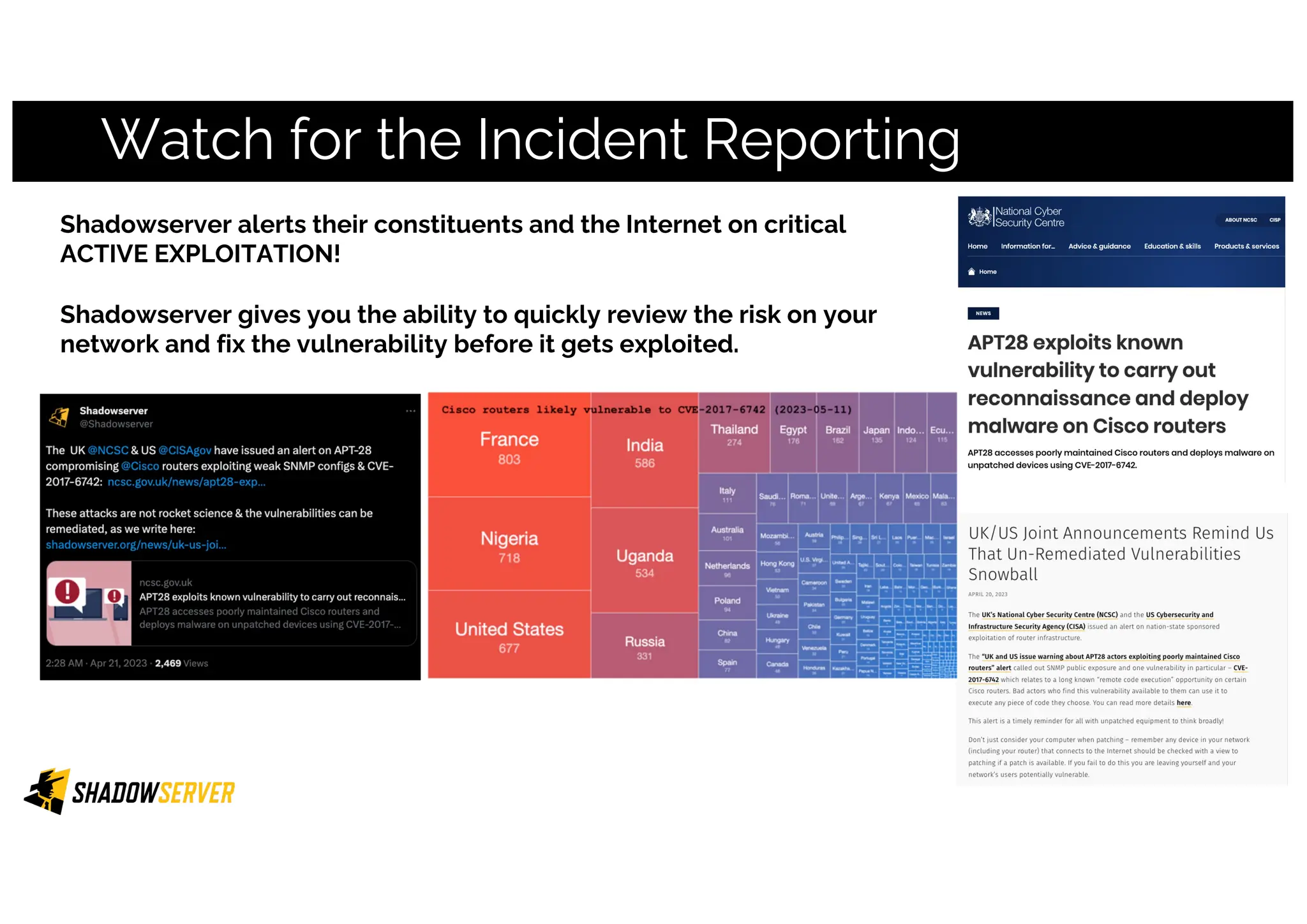
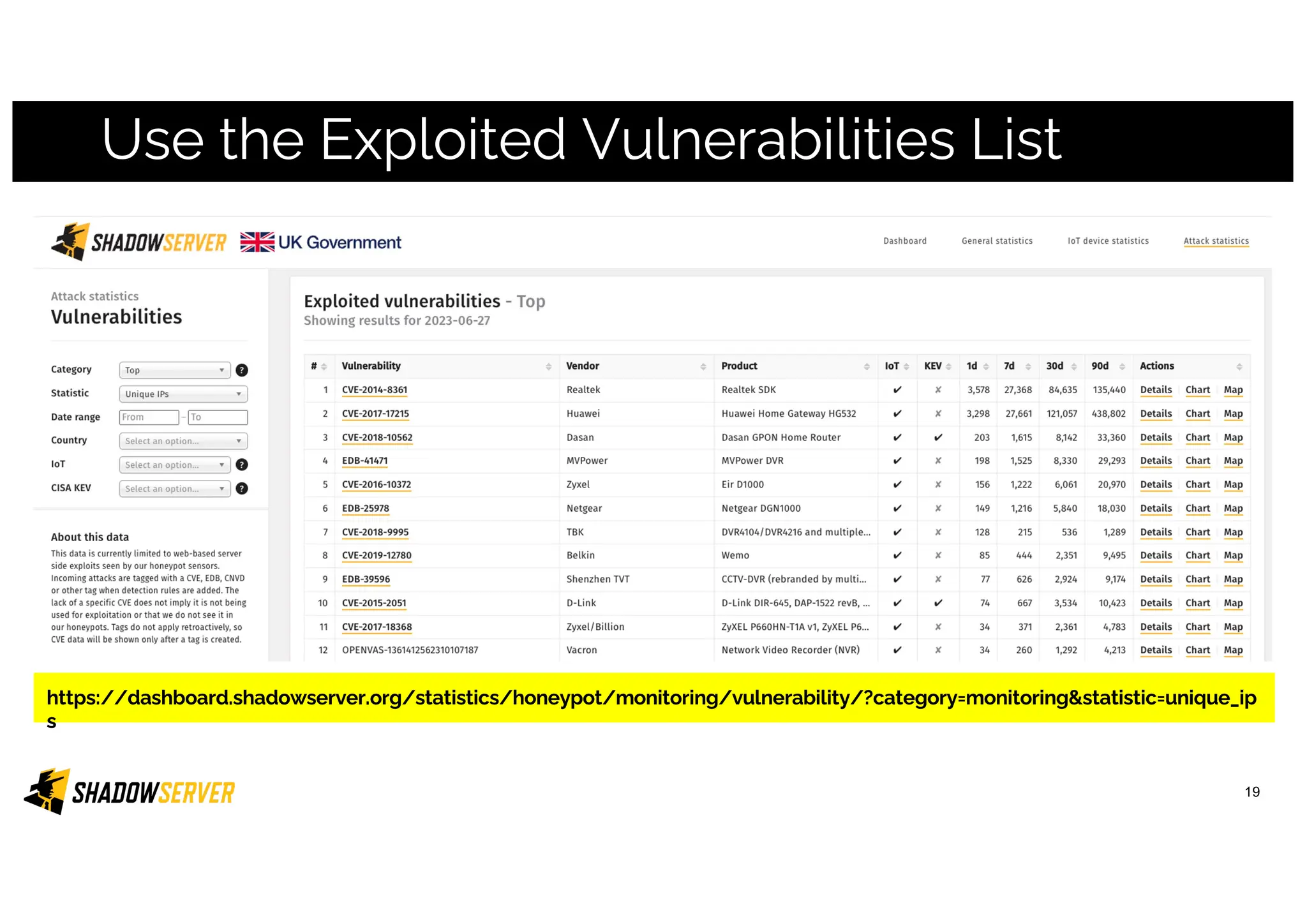
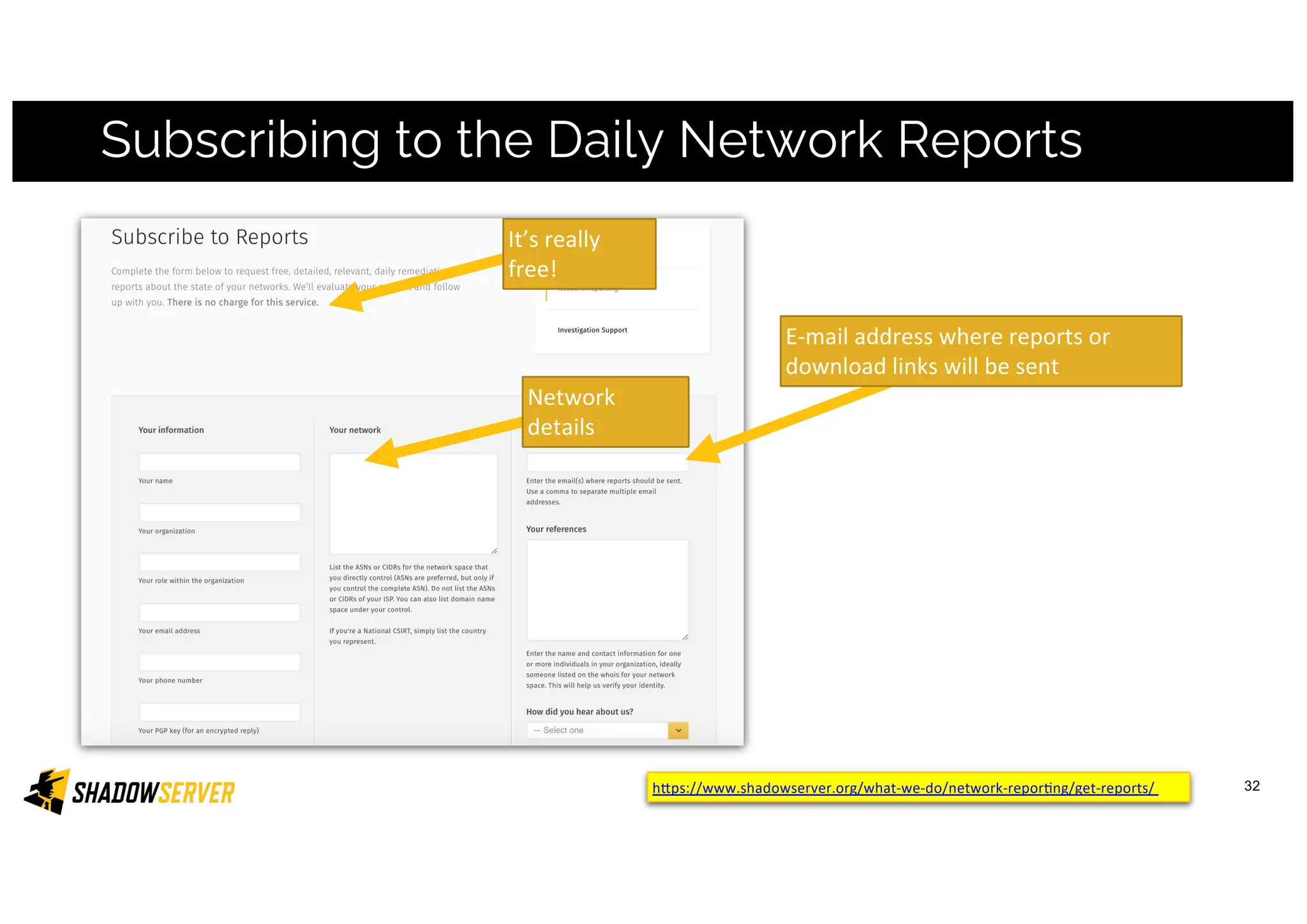
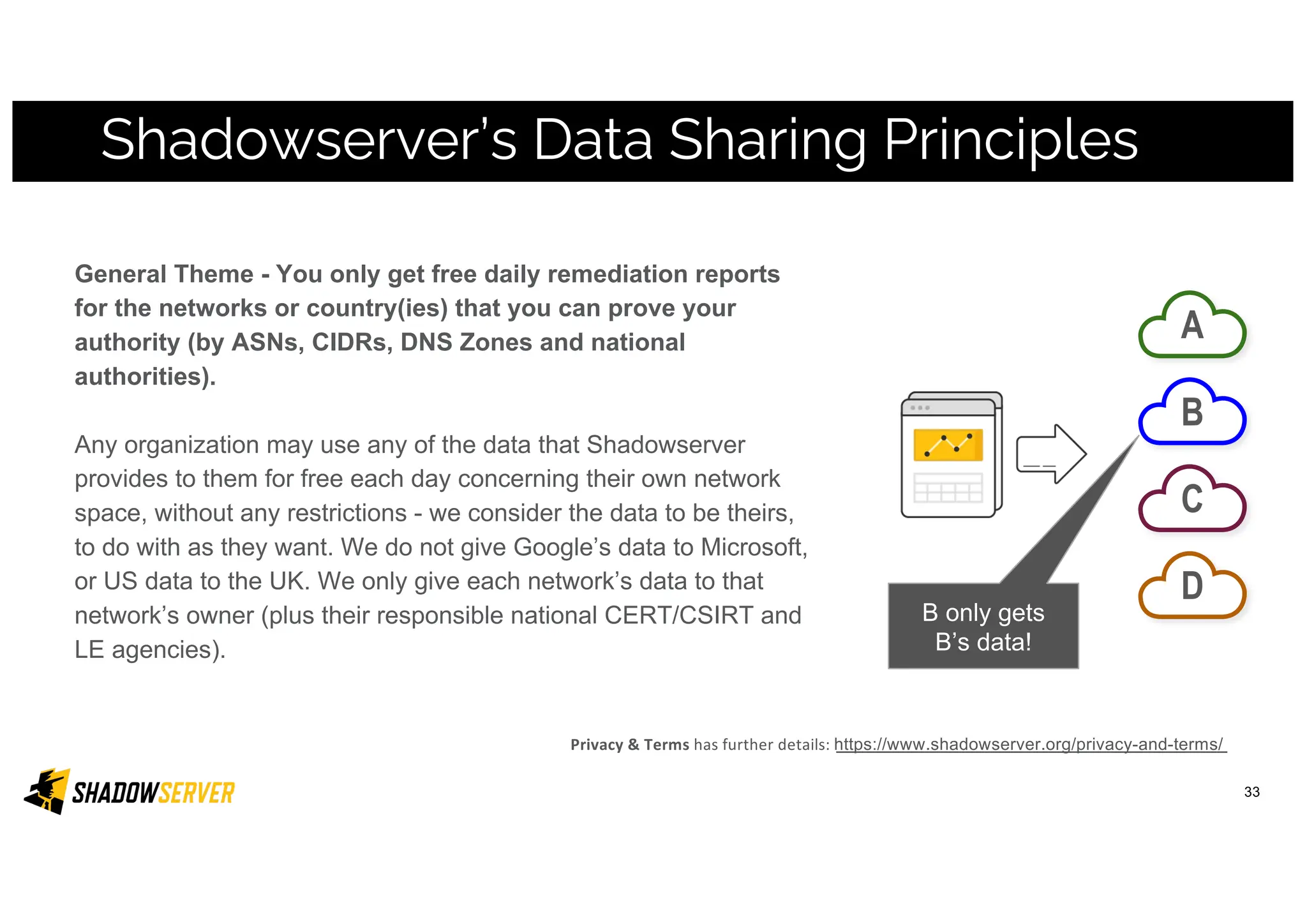
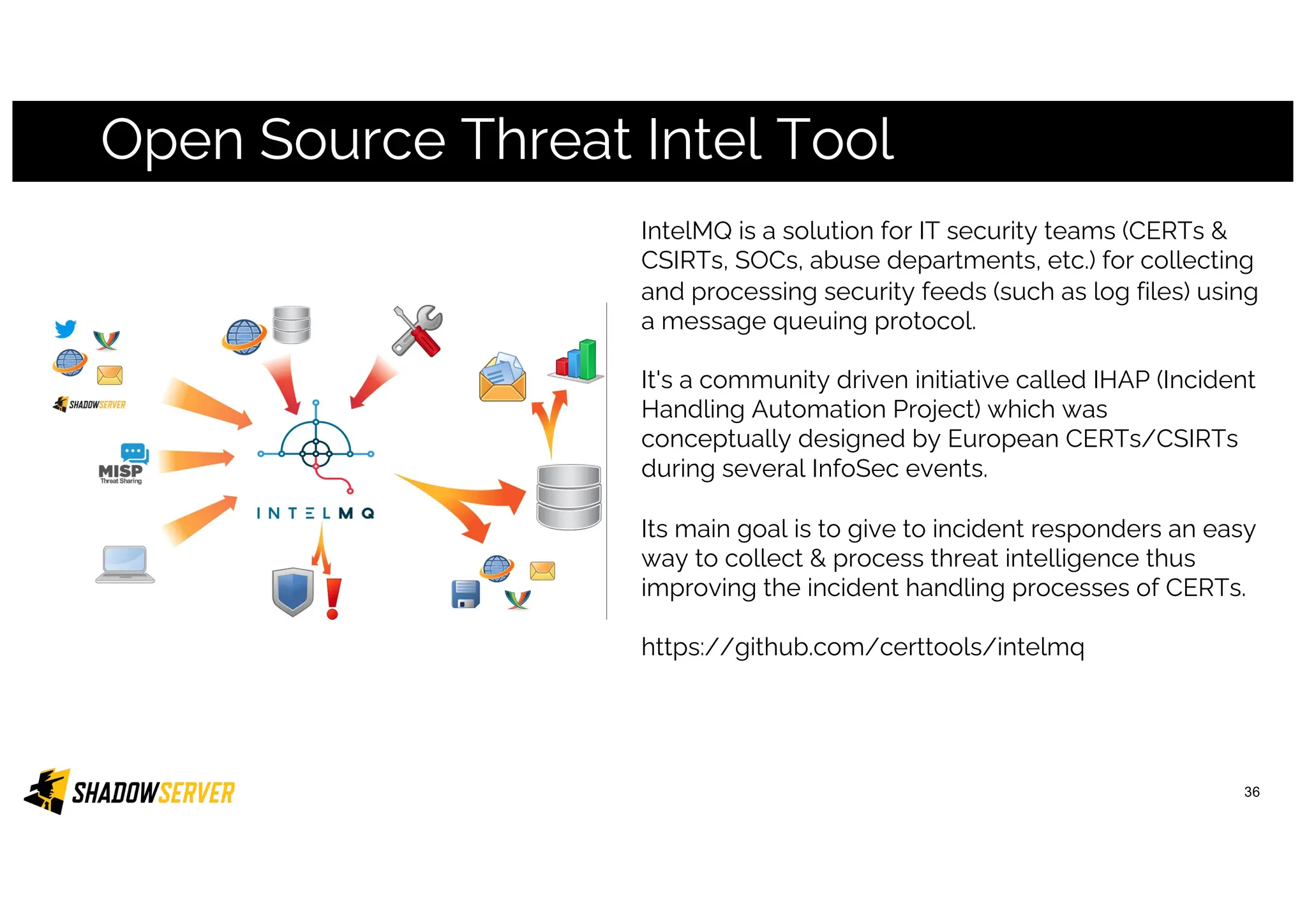
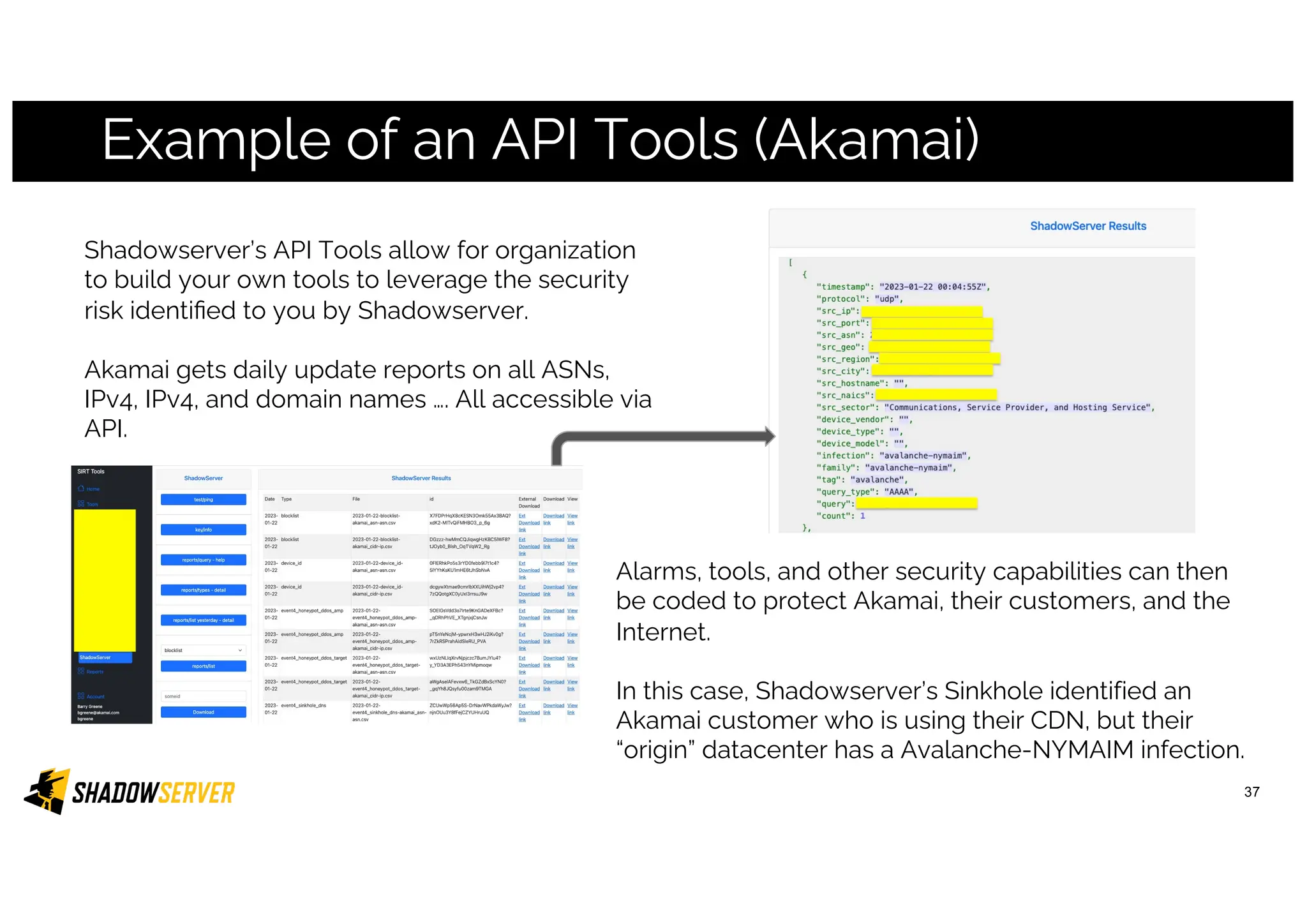
The Shadowserver Foundation is a non-profit organization dedicated to enhancing internet security by providing free cyber threat intelligence and tools to organizations worldwide. They collaborate with various stakeholders, including national response teams and law enforcement, to mitigate vulnerabilities and detect malicious activities. Shadowserver's daily network reports, accessible via email or APIs, help organizations identify and fix security risks without the need for costly paid services.