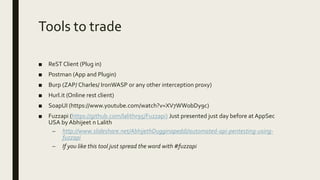
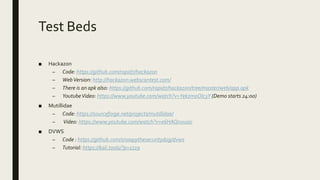
The document provides an overview of a presentation on pentesting REST APIs. The presentation will cover basic theory, personal experience, methodology, tools used, test beds, example vulnerabilities, common findings, and include hands-on demos. The presentation will discuss both SOAP and REST APIs, pentesting approaches, tools like Postman and Burp Suite, example test beds like Hackazon and Mutillidae, and common API vulnerabilities like information disclosure, IDOR, and token issues.