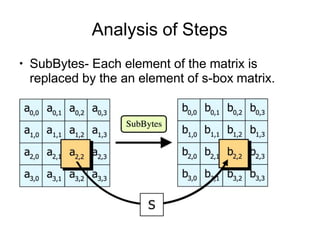
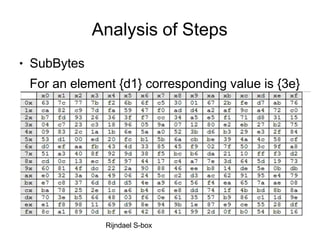
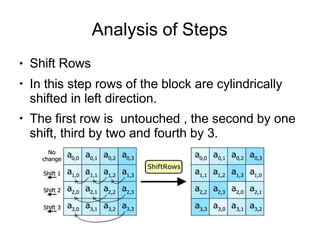
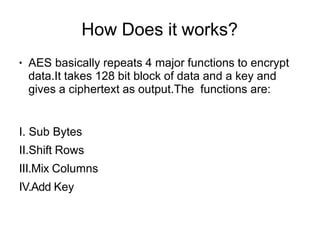
AES is an encryption standard chosen by the National Institute of Standards and Technology to protect classified information. It operates on 128-bit blocks using a variable key length of 128, 192, or 256 bits. AES became the replacement for the DES algorithm after it was cracked in 1997. The Rijndael cipher developed by two Belgian cryptographers was selected as the new AES algorithm due to its security, performance, and flexibility.




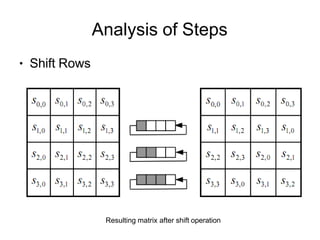
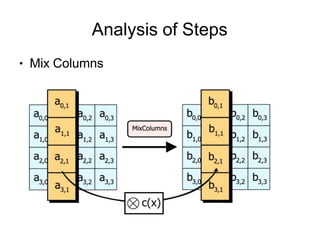
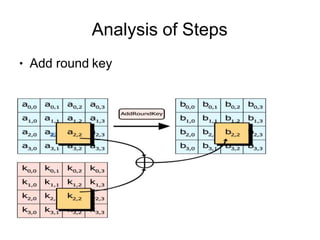
![Analysis of Steps
●
●
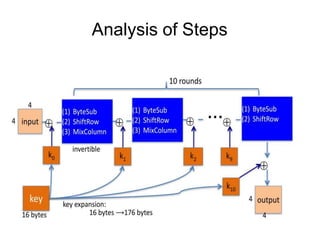
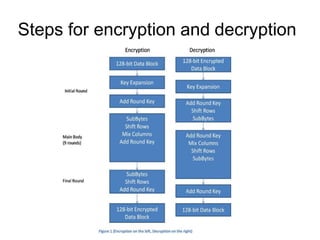
KeyExpansions- In the key Expansion process the given 128
bits cipher key is stored in [4]x[4] bytes matrix (16*8=128 bits)
and then the four column words of the key matrix is expanded
into a schedule of 44 words (44*4=176) resulting in 11 round
keys (176/11=16 bytes or 128 bits).
Number of round keys = Nr + 1. Where Nr is the number of
rounds (which is 10 in case of 128 bits key size) So here the
round keys = 11.](https://image.slidesharecdn.com/aes-240218152954-e11e4d5a/85/Advance-Encryption-Standard-A-E-S-pptx-8-320.jpg)