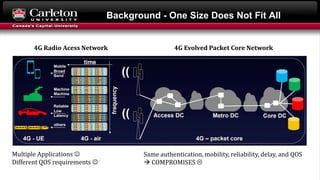
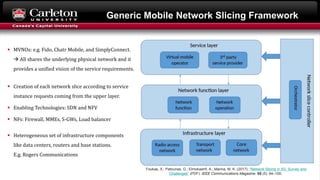
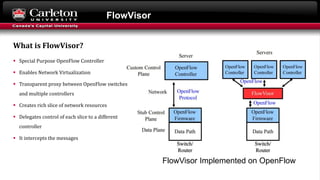
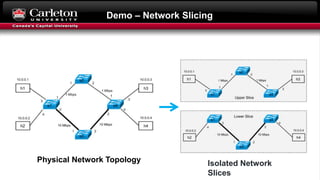
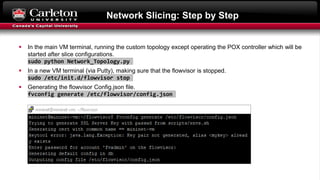
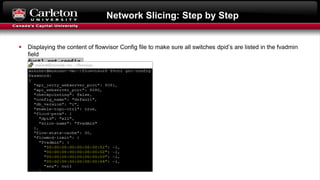
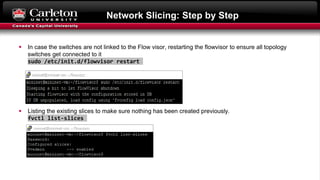
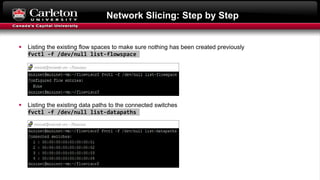
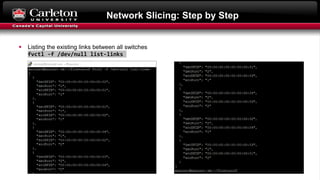
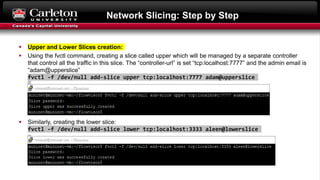
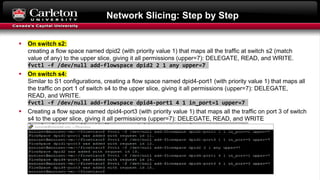
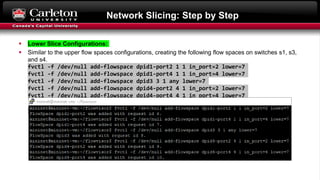
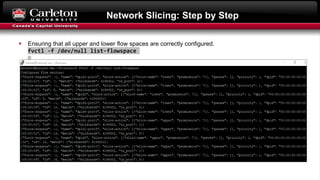
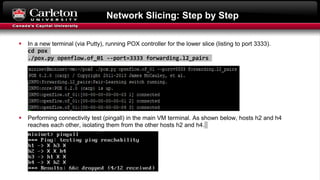
This document describes setting up network slicing on a Mininet testbed using FlowVisor. It outlines creating an upper and lower network slice managed by separate SDN controllers. Flow spaces are configured on switches to delegate traffic on certain ports to each slice. Connectivity tests show the slices isolate hosts from each other while intra-slice communication is maintained.