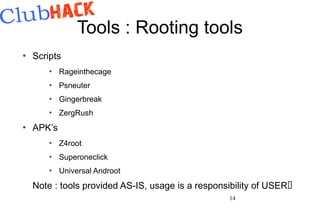
This document summarizes the Android Tamer virtual machine environment. It allows users to perform application penetration testing, malware analysis, ROM modification and analysis, and application/malware development. The VM is based on Ubuntu and contains tools like OWASP ZAP, DroidBox, and Eclipse. It provides an integrated solution for assessing Android security in a standardized way. The presenter aims to expand the toolset and keep the project maintained going forward.