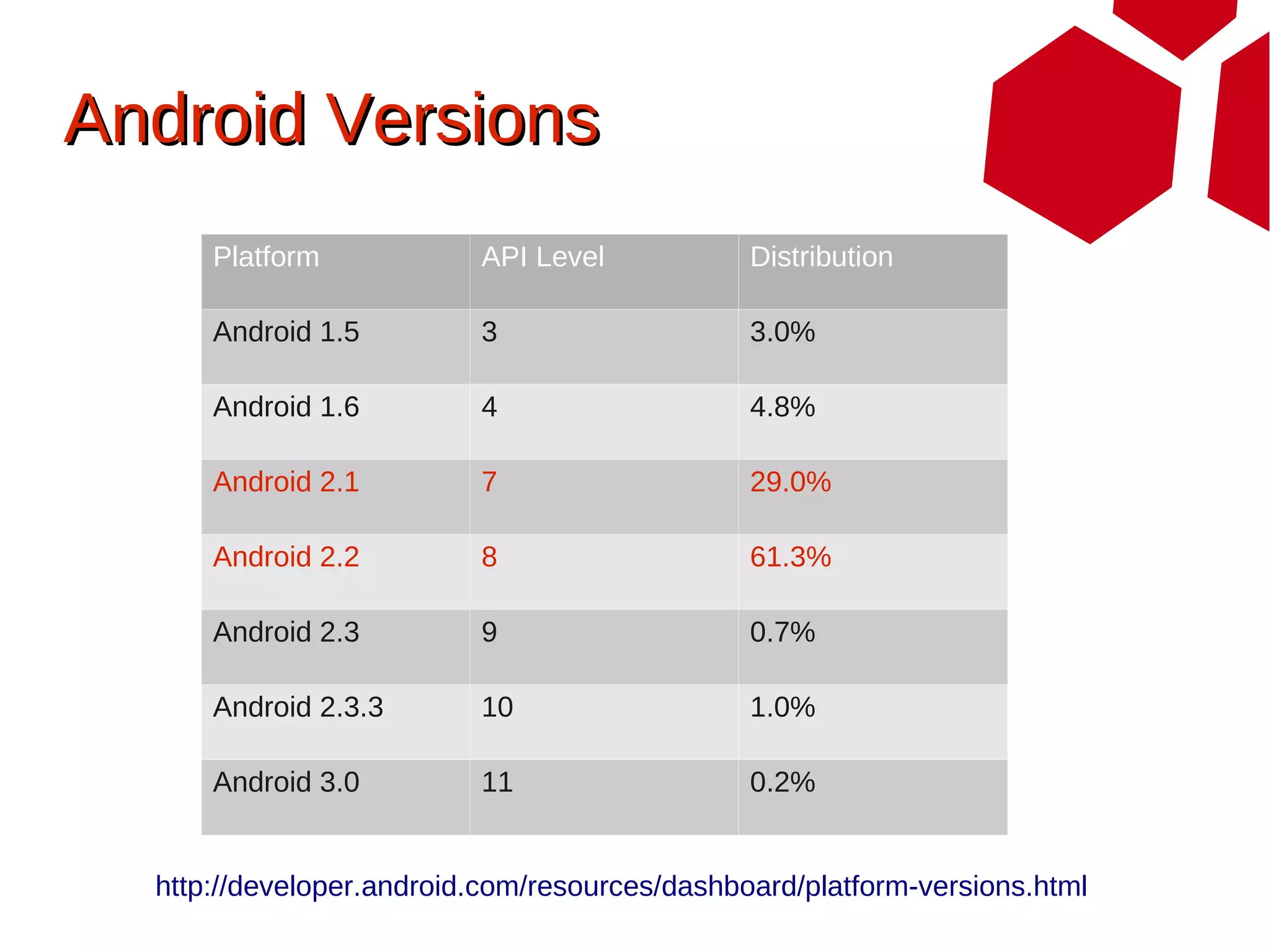
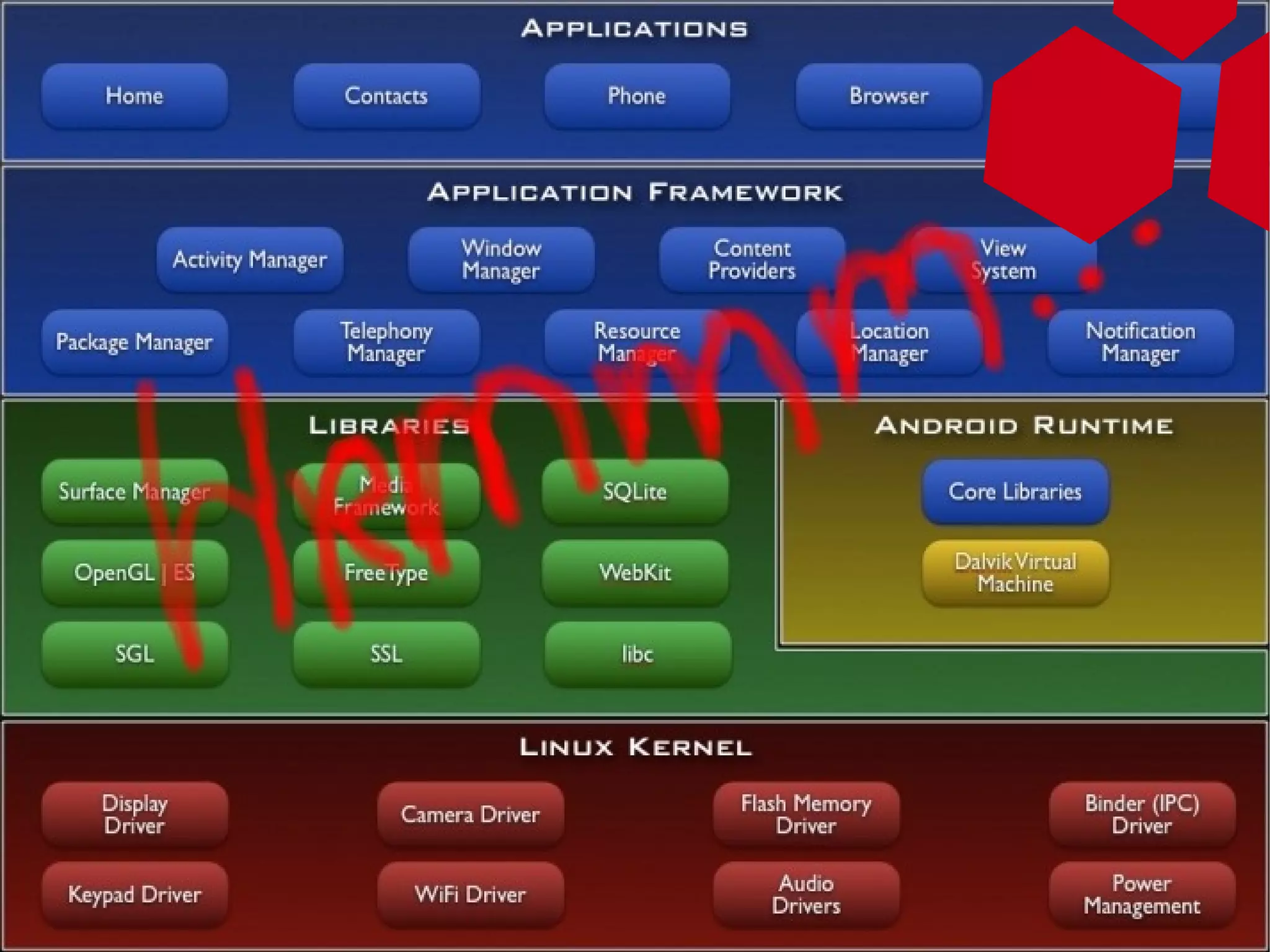
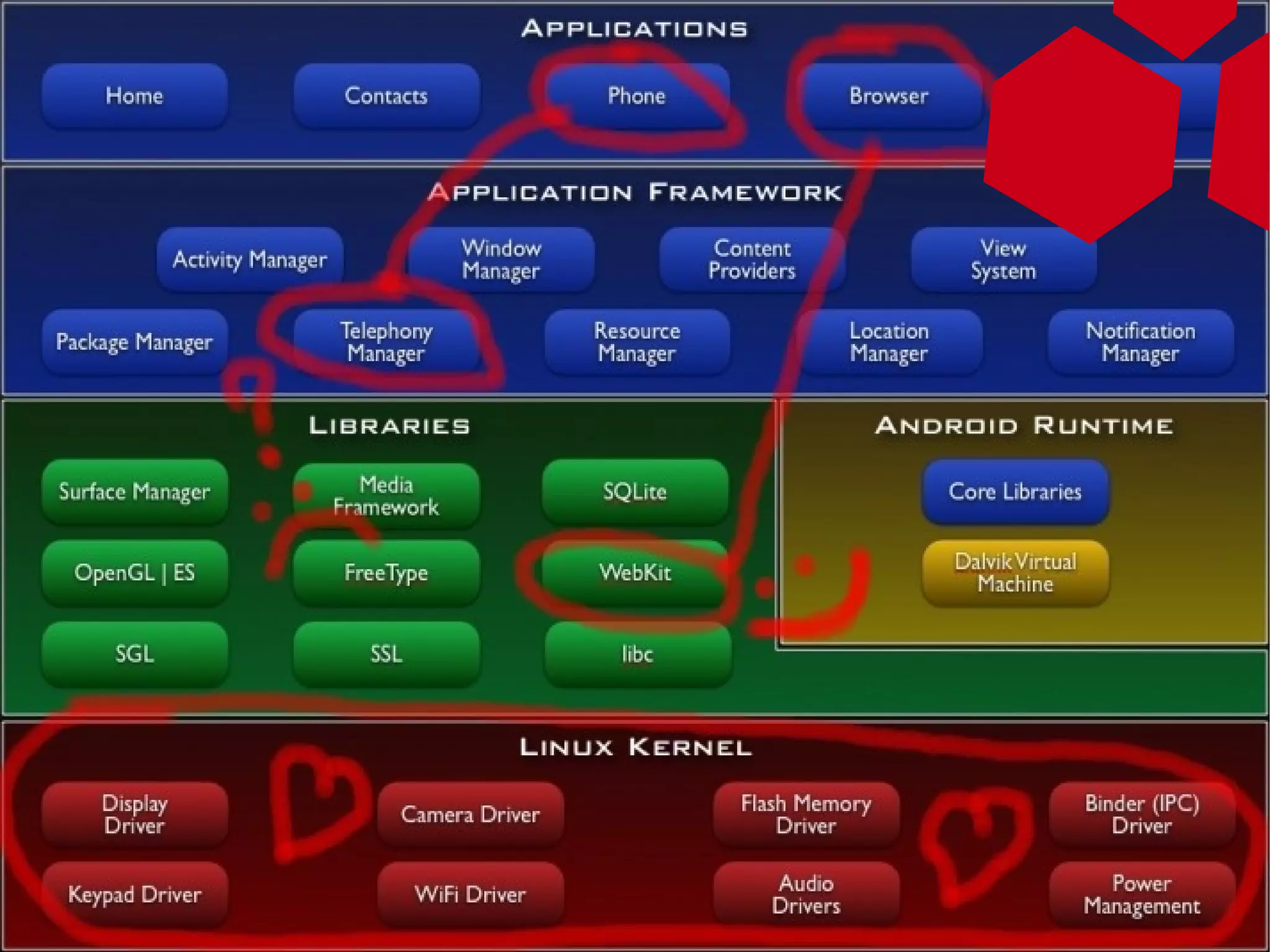
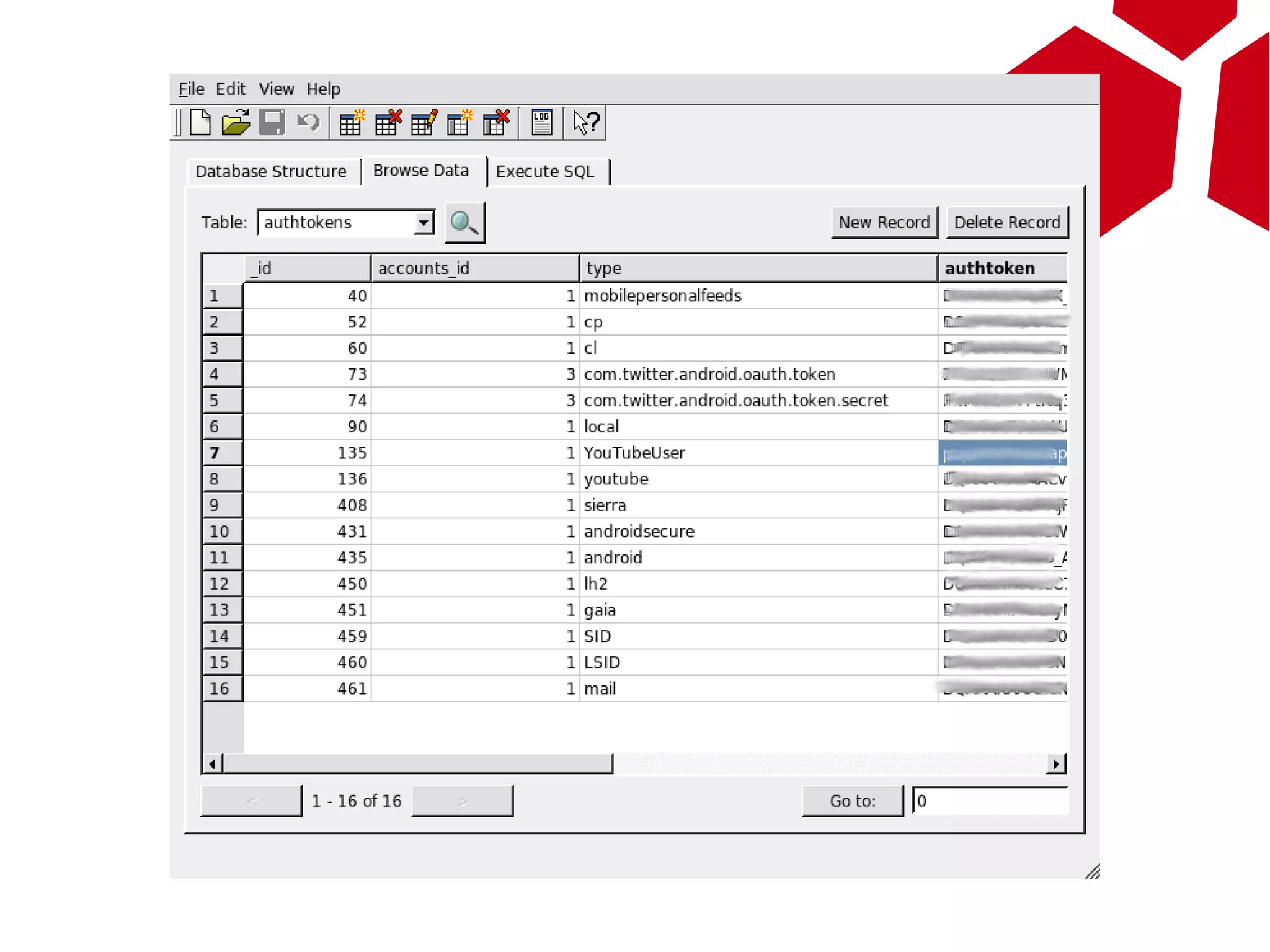
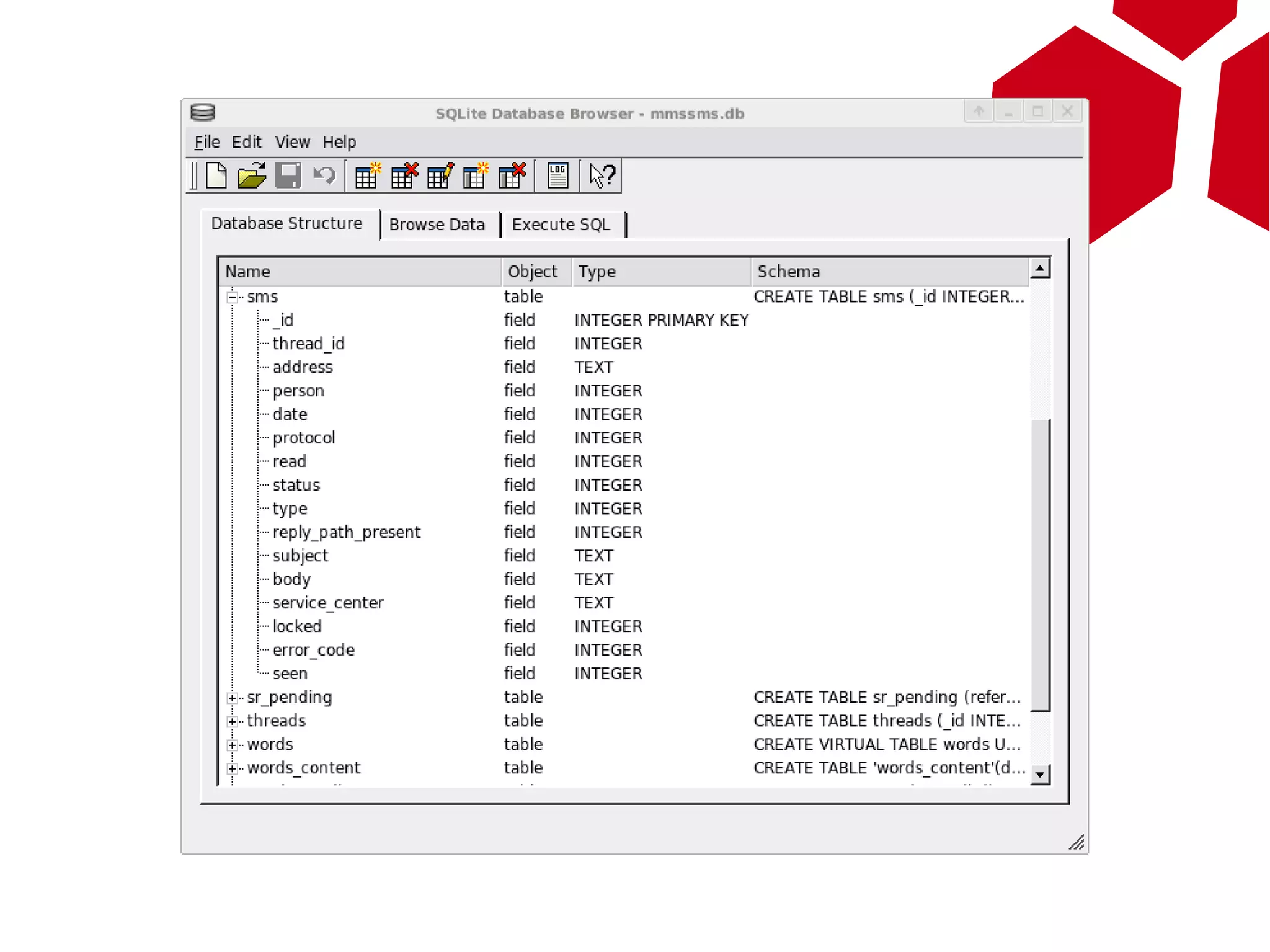
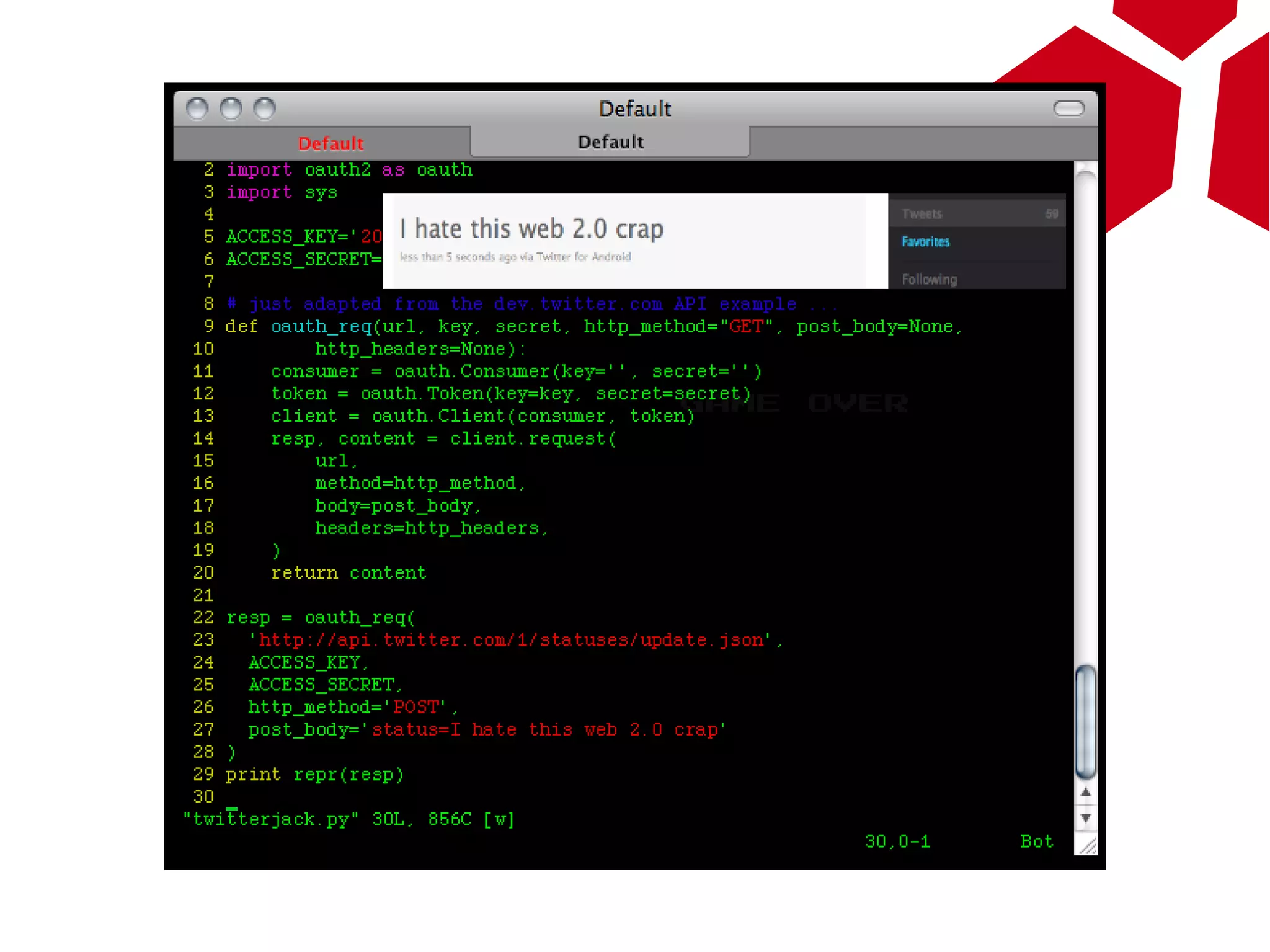
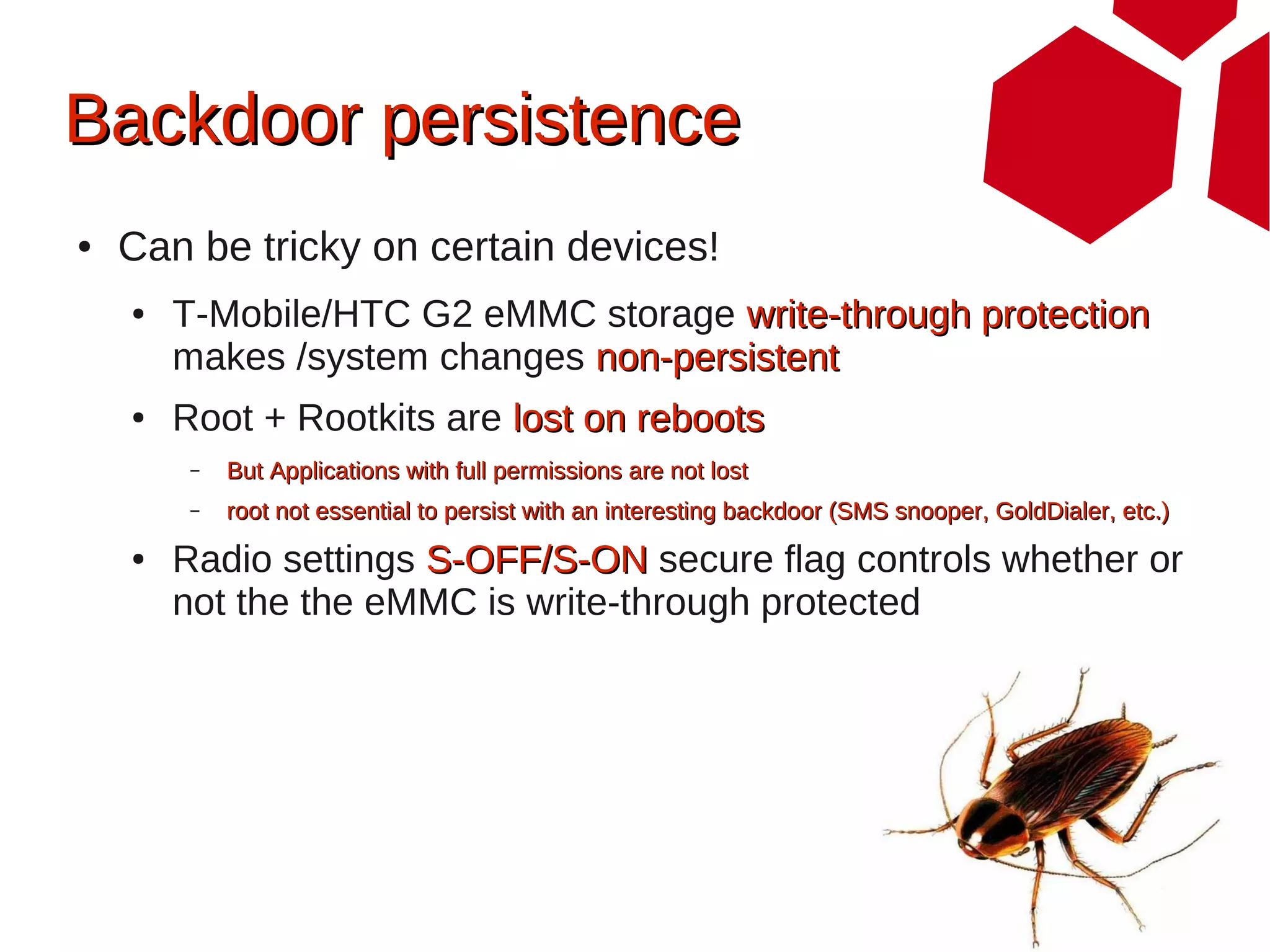
This document provides an overview of attacking Android devices. It discusses Android's architecture and security model, popular versions and their vulnerabilities, and methods for remotely accessing a device and elevating privileges. The presenters demonstrate gaining root access on an Android 2.1 device through a browser vulnerability and vendor kernel bug. They discuss options for backdooring devices at the application or system level for persistent remote access.
![Beating up on Android
[Practical Android Attacks]
Bas Alberts + Massimiliano Oldani
Immunity Inc.](https://image.slidesharecdn.com/androidattacks-odt-120115040005-phpapp01/75/Android-Attacks-1-2048.jpg)